By Sunny Jovita, Solution Architect Intern
Data security has now become major concern for companies, organizations, government authorities, and even individuals alike. Its primary objective is to prevent unauthorized parties from misusing sensitive data for fraudulent purposes. Essentially, data security entails the safekeeping of personal, financial, and confidential information of users to ensure that it remains inaccessible to unauthorized individuals.
Furthermore, data assets are vulnerable to breaches caused by accidental hacking or system failures, which can potentially expose sensitive information like email addresses, passwords, and ID card numbers. To mitigate the risk of such unauthorized access, it is crucial to implement techniques such as masking, hashing, or encryption to protect our data assets. By employing these measures, we can enhance the security and integrity of our valuable information.
In this blog, we will delve into the specific data security measures that Alibaba Cloud’s Data Security Center (DSC) can undertake to ensure continuous protection in the ever-evolving cyber world. By exploring these comprehensive strategies and solutions, we aim to shed light on the robust security practices that can be implemented to effectively safeguarding valuable data assets.
The exponential growth of data creation is unprecedented in history. According to a study, 90% of the data has been generated within the past two years signifies a remarkable acceleration in data creation compared to the cumulative data accumulated throughout human civilization prior to this period [1].
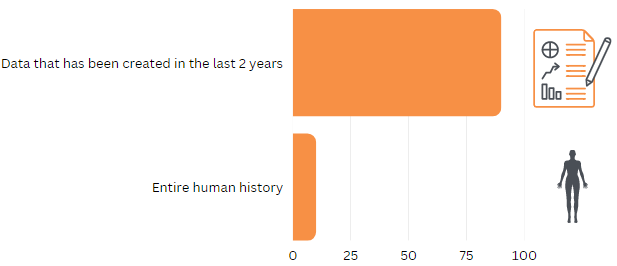
In 2021, about 2.5 quintillion bytes of data is produced daily [2], equating to 1.7 MB per second for every individual. This vast amount of data holds immense value for both business and individuals, making it an enticing target for attackers. As cyberattacks continue to rise, it becomes crucial for users to understand how these attacks work and how to safeguard their data from potential breaches and misuse.
The advancement of information technology and the increasing focus on privacy have amplified the importance of securely storing sensitive information such as contact details, financial data, payment information, and personal information. It is imperative for individuals and businesses to adopt proper security measures to protect their data.
As advancing digitalization leads many businesses to adopt a cloud-based solution, traditional data isolation techniques alone will not protect your corporate information. A more flexible and advanced approach is now required. But this comes with its own set of issues, and today’s organizations are typically faced with two main data security challenges on the cloud:
1) Meeting business demands: Migrating services to the cloud requires maintaining high availability and effectively managing data assets across different regions, platforms, and products, even when stored in separate data warehouse.
2) Identifying sensitive data: with massive and disparate datasets, organizations must swiftly and accurately identify sensitive data to implement appropriate safeguards.
In this blog, we present a comprehensive overview of Data Security Center solution and its ability to effectively tackle the security challenges encountered by organizations operating in the cloud. We highlight the unique advantages that set our solution apart as a prominent choice across various scenarios, through the implementation of advanced security measures such as encryption, decryption, hashing, and many more to detect sensitive data stored in Alibaba Cloud products.
Data security center offers a range of features designed to enhance data security, such sensitive data detection and de-identification. With these capabilities, the DSC provides a comprehensive and integrated data security solution.
Platforms
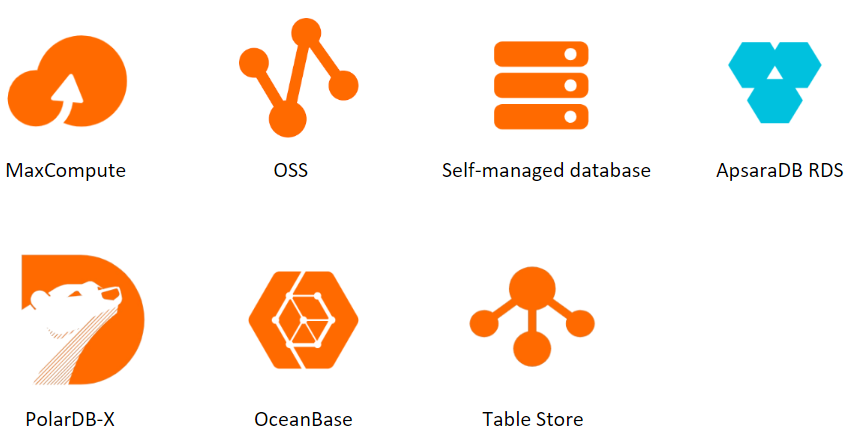
To ensure thorough scanning, the DSC examines your data stored in various platforms such as:
Sensitivity Evaluation
The DSC evaluates the sensitivity of your data by checking the number of items that the data matches the sensitive data detection rules. This assessment helps determine whether the data is sensitive or not.
Importantly, it is essential to note that Data Security Center (DSC) does not store your data. Instead, it scans your data assets for sensitive information and classifies it according to different risk levels, providing you with valuable insights while maintaining data privacy and confidentiality.
Our Data Security Center (DSC) offers real-time scanning of large data volumes to identify sensitive information, enabling you to assess the security status of your data assets. By scanning vast amounts of data, DSC keeps you informed about the security of your data assets, empowering you to implement effective protection measures regardless of the data’s location.
Our Data Security Center also offers several benefits to address the challenges faced by organizations today:
Compliance
Data Security Center helps you meet the compliance requirements for protecting personal information and undergoing security audits in cloud computing.
Intelligence
Leveraging big data technologies, machine learning capabilities, and intelligent algorithms, the Data Security Center detects and monitors sensitive data, identifies high-risk activities like anomalous data access, and alerts you about potential data leaks. It also provides actionable suggestions to resolve detected issues.
Visualization
The DSC visualizes the results of sensitive data detection, providing a clear overview of the security status of your data assets. It presents data assets in dynamic and visual manner, allowing you to query and identify sensitive data quickly with just few clicks.
Cloud-Native
Designed to fully utilize cloud-native capabilities, the Data Security Center offers an integrated data protection and defense mechanism for cloud data assets. The Data Security Center operates within the cloud environment, which means eliminating the need for installing or running any agents. This simplifies deployment and management, ensuring seamless integration with your existing cloud infrastructure.
Wide Range of Data Types
The Data Security Center supports various data types, including image files, compressed packages, databases, structured data, unstructured data. It is designed to accommodate diverse data formats, making it flexible and adaptable to different data sources.
Integration with Big Data Platforms
Our Data Security Center seamlessly integrates with big data platforms, allowing you to secure and protect large-scale data environments, whether you are dealing with structured or unstructured data.
Closed-Loop Data Protection
Offering a closed loop solution that covers the entire data lifecycle, from identification to desensitization, The DSC facilitates:
These techniques are offered to protect sensitive data, ensuring end-to-end security. Additionally, it enables auditing capabilities to monitor data access and ensure compliance.
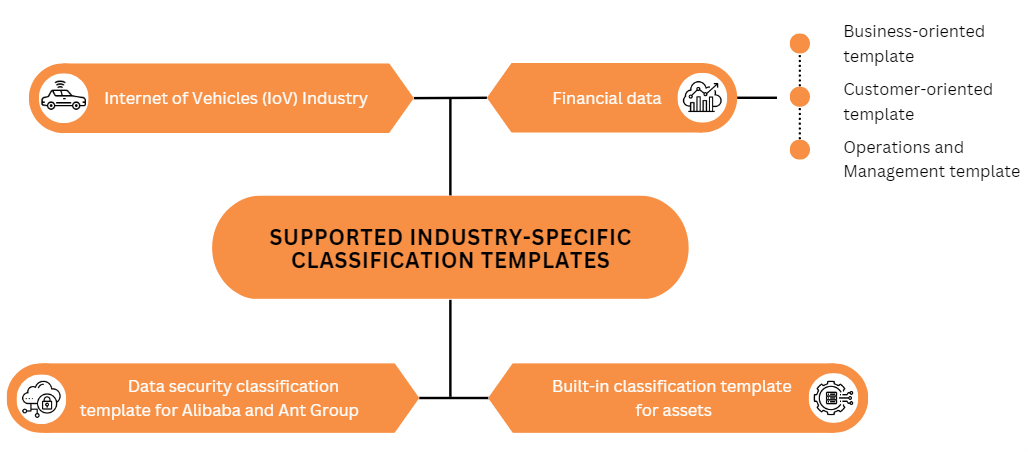
DSC provides classification templates for detecting sensitive data. The classification templates are customized to classify the sensitive data based on the requirements of different industries. DSC can detect sensitive data based on the classification template that you specify. This ensures data security compliance.
The Alibaba Cloud Data Security Center (DSC) provides a comprehensive suite of features to protect and de-identify sensitive data within your organization. With DSC, you have access to a range of powerful tools and algorithms designed to enhance data security and ensure compliance with privacy regulations.
Let’s delve deeper into each of these features to understand how they contribute to robust data protection and privacy measures offered by the Alibaba Cloud Data Security Center.
DSC allows you to set a salt value for each encryption algorithm such as MD5, SHA1, SHA256, and HMAC. They provide irreversible transformations that generate fixed-size hash values, ensuring data integrity.
With masking, you can set parameters for the redaction algorithm. It redacts specified text in sensitive data with asterisks (*) or number signs (#).
Replacement involves replacing sensitive data with predefined values or patterns. This technique is useful when you want to maintain the overall structure and format of the data while concealing the actual sensitive information.
This technique is commonly used to protect sensitive numerical data while preserving statistical integrity and ensuring privacy compliance.
This type of algorithm is used to encrypt sensitive fields that need to be retrieved after encryption.
Similar to encryption, DSC allows you to set a key for each decryption. By setting decryption keys, you can securely retrieve and access the original data when needed.
Shuffling involves reordering or rearranging the elements within a dataset to remove any identifiable patterns or sequences. This technique helps in anonymizing data by making it difficult to link specific records to individuals.
In the unfortunate event of an unauthorized intruder gaining access to your sensitive data, several challenges and risks may arise. Firstly, the intruder can exploit the sensitive data for malicious purposes, leading to financial losses, reputational damage, or legal implications. Additionally, unauthorized access can result in data leakage, compromising the privacy and confidentiality of sensitive information. Such incidents can also violate compliance regulations and industry standards, leading to severe penalties.
However, there’s no need to worry. Alibaba Cloud offers a powerful solution to mitigate theses risks through its RAM authorization features within the Data Security Center. By leveraging RAM, you can establish granular access controls and define custom policies that restrict data visibility to only authorized individuals. This ensures that even if an intruder gains unauthorized access, they will encounter substantial barriers and limitations, minimizing the potential damage they can inflict.
Alibaba Cloud’s SDDP RAM authorization empowers you to proactively safeguard your data, fortifying your defense against unauthorized access and potential intrusions. With this robust security measure in place, you can confidently protect your sensitive assets and ensure compliance with data protection regulations.
In the table below, you will find a comparison of regions that support various features of data security center. China (Hong Kong) is a region that offers support for data masking and data detection. Singapore, Malaysia, and Indonesia also provide the same features as China (Hong Kong), including data masking and data detection. However, it is important to note that these regions do not offer support for security audit and data risk detection.
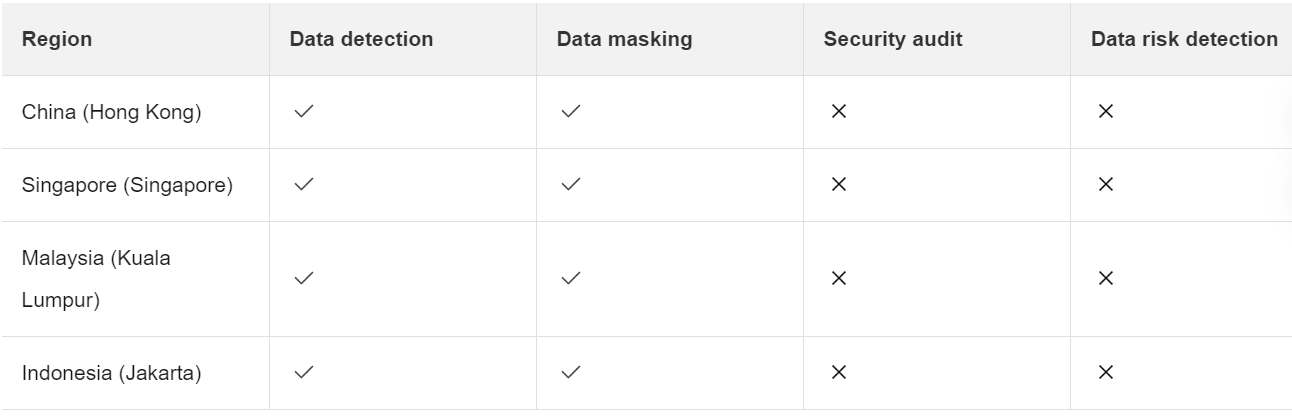
Image source: https://www.alibabacloud.com/help/en/data-security-center/latest/supported-regions
Alibaba Cloud Data Security Center (DSC) is designed to instill confidence in organizations as they navigate the digital landscape. In a rapidly evolving sector, we understand the challenges businesses face in responding to the evolving cyber world. DSC equips organizations with robust data security solutions to address the increasing threats, protect sensitive information, ensure regulatory compliance, and adapt to the dynamic nature of the cybersecurity landscape.
Alibaba Cloud Data Security Center (DSC) offers a comprehensive suite of tools for sensitive data discovery, identification, classification, data leak prevention, security audit, data masking, risk detection, and protection. With DSC, organizations gain enhanced visibility, manageability, and control over their sensitive data assets. DSC efficiently detects sensitive data within vast datasets in the cloud, performs data behavior analysis and auditing, and provides data masking capabilities. This empowers enterprise customers to effectively manage data classification, identify anomalous data behaviors, and prevent data leakage through proactive anomaly detection and auditing.
We also have the expertise and experience to design custom security solutions to tailor your specific needs.
Reach us out at: https://id.alibabacloud.com/id
[1] B. P. Patil, K. G. Kharade, and R. K. Kamat, ‘Investigation on data security threats & solutions’, International Journal of Innovative Science and Research Technology, vol. 5, no. 1, pp. 79–83, 2020.
[2] Domo Resource – Data Never Sleeps 5.0. [Online]. Available: https://www.domo.com/learn/infographic/data-never-sleeps-5
Alibaba Cloud Elasticsearch: An Overview of Data Search and Visualization
Leverage your CI/CD pipeline by Autoscaling Jenkins Agent with Alibaba Cloud
115 posts | 21 followers
FollowAlibaba Cloud Community - May 19, 2023
Maya Enda - June 16, 2023
Amuthan Nallathambi - August 24, 2023
Amuthan Nallathambi - July 12, 2024
Data Geek - December 2, 2024
Nick Patrocky - March 4, 2024
115 posts | 21 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More Data Lake Formation
Data Lake Formation
An end-to-end solution to efficiently build a secure data lake
Learn MoreMore Posts by Alibaba Cloud Indonesia