By Yili (Xiao Yi) from Alibaba Cloud Storage
It has been a common practice for many users to use Log Service to collect Kubernetes container logs. Users can enable Log Service when creating a cluster to quickly collect container logs of a Kubernetes cluster, including the standard output of containers and text files in containers.
In scenarios where a user has multiple ACK clusters in multiple regions, if the users want to centrally audit and query the Kubernetes logs of multiple ACK clusters in each region, they need to perform additional operations.
For example, users can manually create a data transformation job to deliver logs from each Logstore to the same destination database. However, this operation has the following limits:
Log Audit has introduced the Kubernetes log centralized audit function to solve the problems, which means that log audit will automatically perform a centralized audit and query on Kubernetes event logs, audit logs, and Ingress logs that meet the automation conditions.
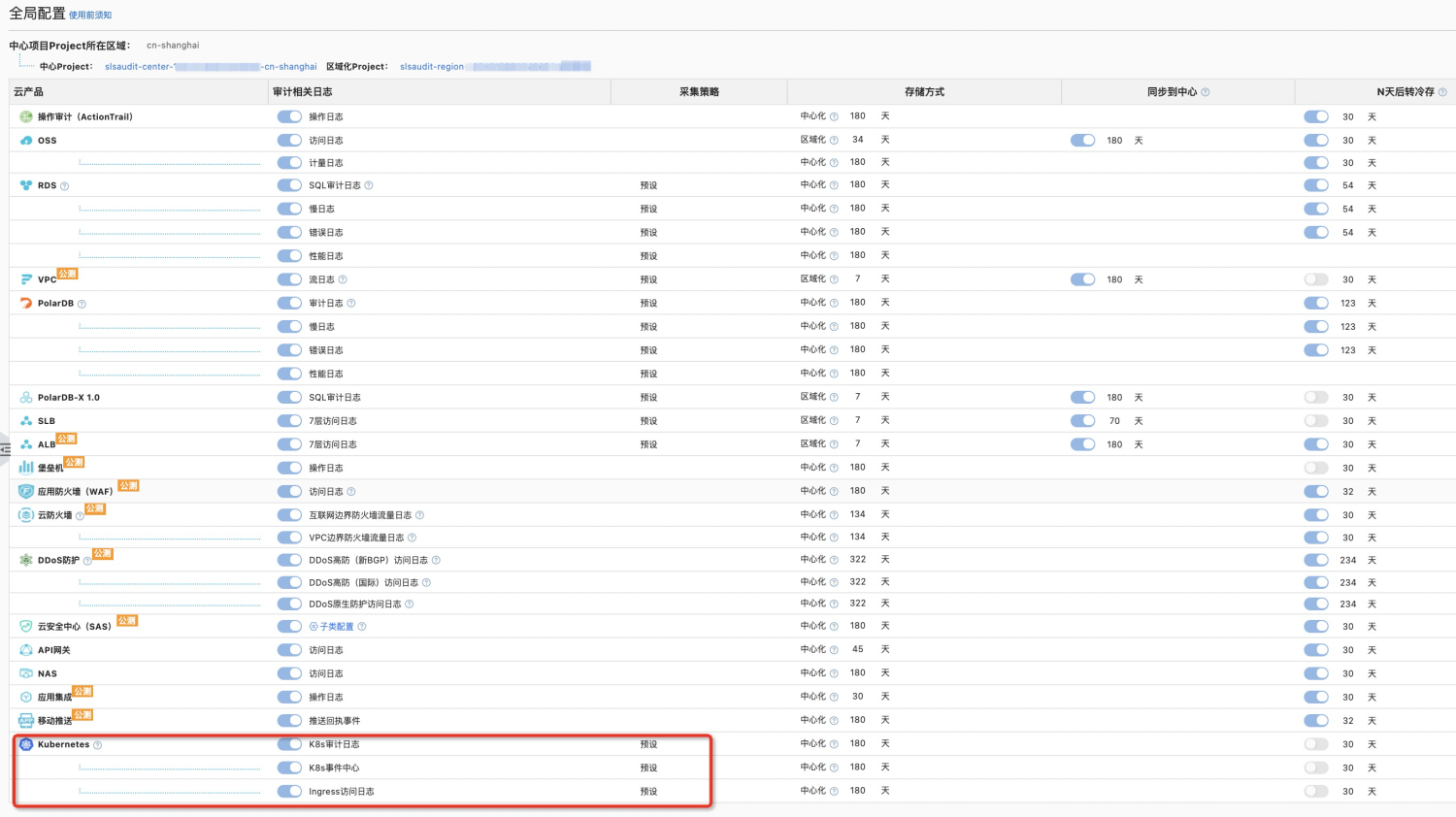
However, the use of Log Audit (before upgrade) (even if the central account has upgraded the service-linked role AliyunServiceRoleForSLSAudit) to perform a centralized audit on Kubernetes logs still requires complicated separated authentication. The following three operations are required to perform a centralized audit and centralized query of Kubernetes logs:
{
"Version": "1",
"Statement": [
{
"Action": "log:*",
"Resource": [
"acs:log:*:*:project/k8s-log-*"
],
"Effect": "Allow"
}
]
}Log audit (before upgrade) solves the problems of limits 1 and 2, but due to the complexity of its separated custom authentication operations, it brings some inconvenience to users. Users cannot truly enjoy the out-of-the-box feature, centralized audit and centralized query. In addition, custom roles can be deleted and tampered with by users easily, which will affect the user experience.
With the upgrade of Log Audit Central account authentication from the custom role sls-audit-service-monitor required by users to the one-click authorization of service-linked role AliyunServiceRoleForSLSAudit, Kubernetes log collection separated authentication under Log Audit is also on the agenda.
After the log audit has carried out in-depth cooperation with SLS data processing, it can automatically create and run data to process jobs and consume and write logs based on the role through the service-linked role AliyunServiceRoleForSLSAudit. This enables centralized audit, query, and storage of Kubernetes logs in multiple out-of-the-box clusters. Now, the user can enjoy such conveniences by clicking Authorize to authorize the service-linked role AliyunServiceRoleForSLSAudit at the first time of use.
| Centralized Audit of Kubernetes Logs | Raw Mode | Log Audit Enabled Kubernetes (Before Upgrade) | Log Audit Enabled Kubernetes (After Upgrade) |
| Manually Create Related Jobs | Yes | None | None |
| Real-Time Automated Updates | No | Yes | Yes |
| Complex Custom Authentication | None | Yes | None |
The following example shows how to enable a centralized audit of Kubernetes logs in a multi-ACK cluster. Please see Cloud service resource coverage for more information.
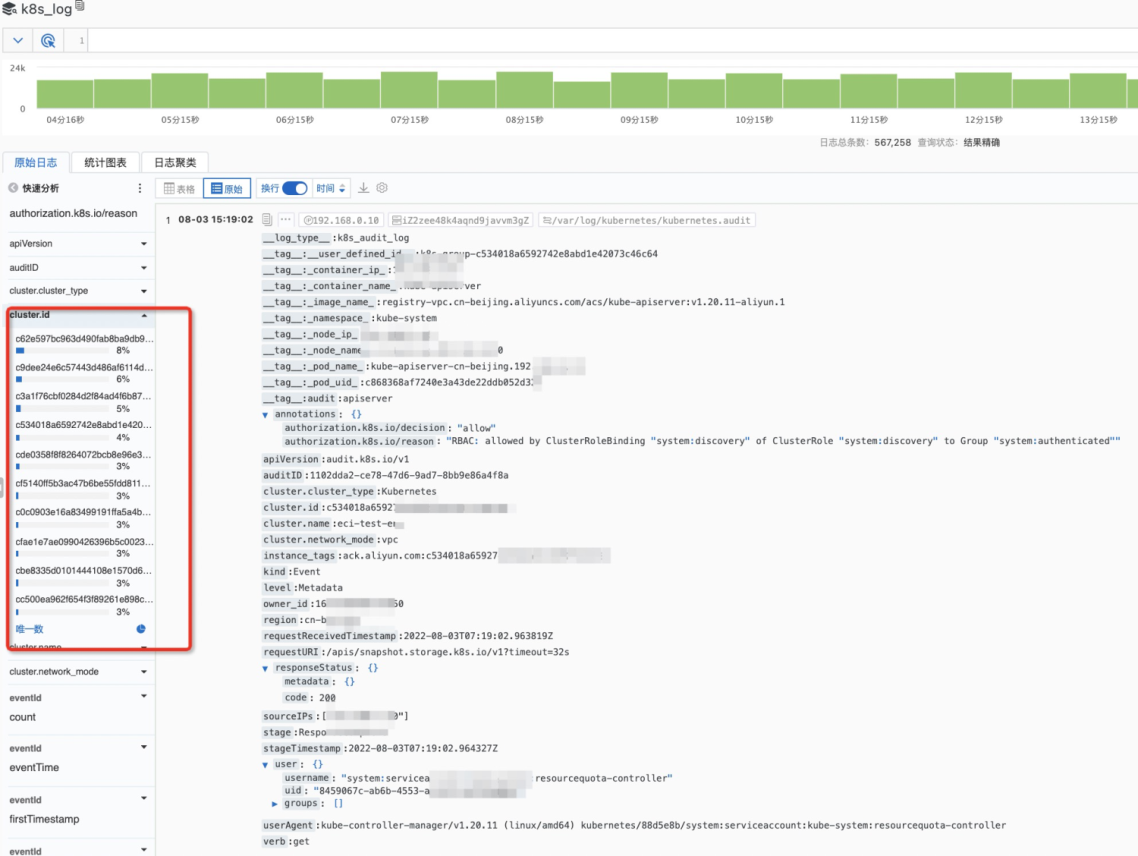
An Example of Centralized Audit of Kubernetes Logs in Multiple Clusters
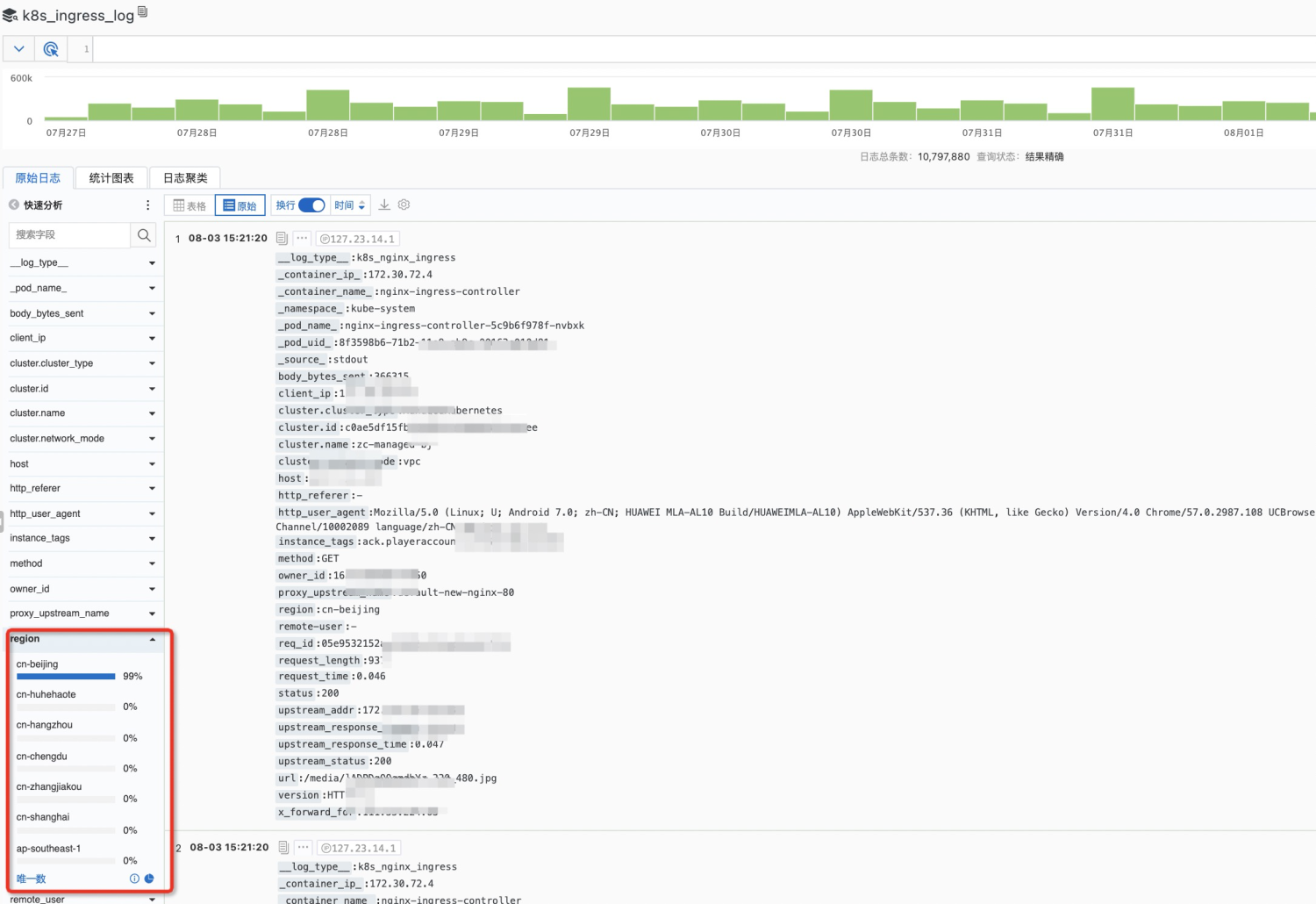
An Example of Centralized Query of Kubernetes Logs in Multiple Regions
Pandas + SLS SQL: Data Pivot with Flexibility and High Performance

1,092 posts | 302 followers
FollowAlibaba Cloud Native - November 3, 2022
Alibaba Developer - April 22, 2021
Alibaba Cloud Community - October 19, 2021
Alibaba Container Service - November 13, 2019
Xi Ning Wang(王夕宁) - July 21, 2023
Alibaba Clouder - December 30, 2020

1,092 posts | 302 followers
Follow Simple Log Service
Simple Log Service
An all-in-one service for log-type data
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More Log Management for AIOps Solution
Log Management for AIOps Solution
Log into an artificial intelligence for IT operations (AIOps) environment with an intelligent, all-in-one, and out-of-the-box log management solution
Learn MoreMore Posts by Alibaba Cloud Community