Interested to learn more about Alibaba Cloud? Check out our course on Cloud Platform Security Overview course and get certified today!
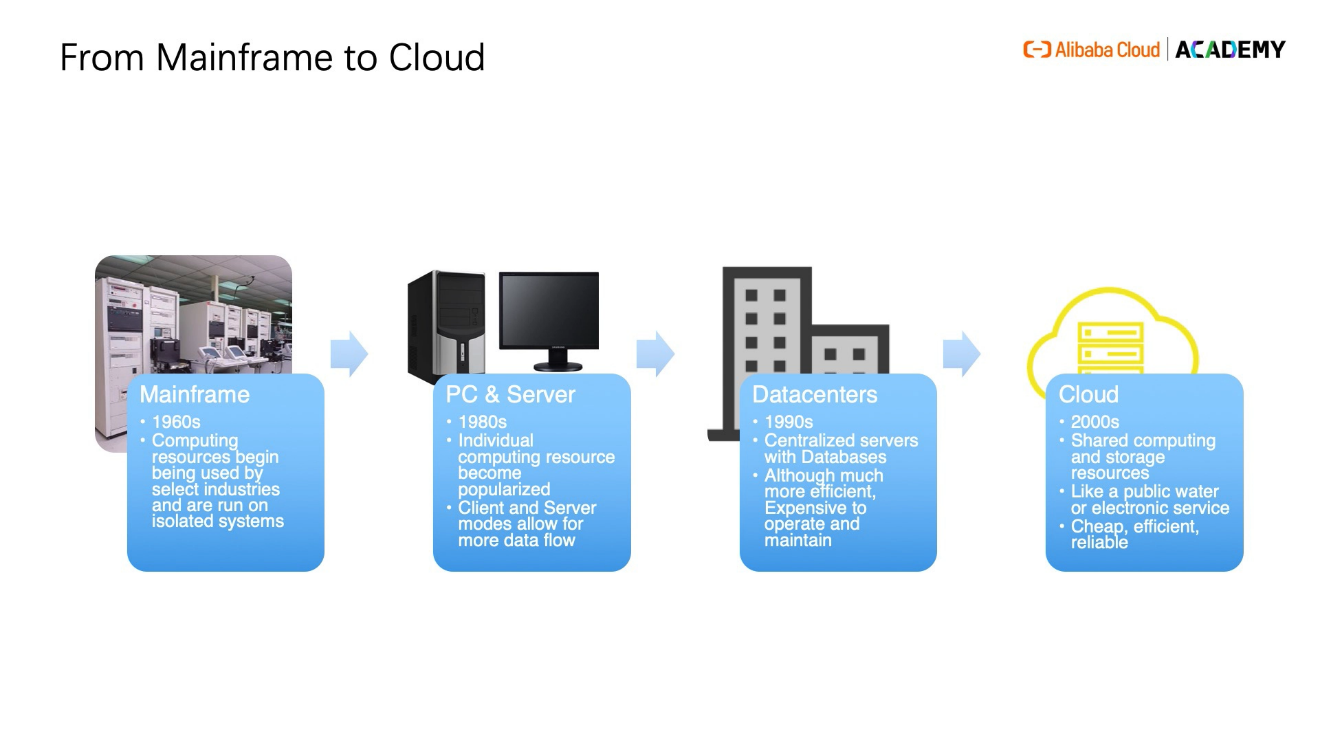
Ever wondered how data stored online can remain secure despite being publicly accessible? Well, before we start, let's have a quick recap on the history and evolution of the IT infrastructure. In the 1960s, the mainframe is recorded on the memory of its on making a very powerful but very isolated kind of device. At that time, those devices can only be owned by rich individuals or big companies, especially banks. They use this kind of device to do major financial transactions or for other kinds of heavy load computing. But as the internet developed further, we saw a shift from physical mainframes to a powerful and empowering tool called the virtual server, all thanks to cloud computing.
The problem of the mainframe is that it's very isolated and can only be controlled by large enterprises with a lot of resources and technical expertise. This type of setup is not shareable and is also very expensive to develop. Eventually, companies like Intel and AMD began to provide cheaper and cheaper chips, and rebuild these powerful devices into personal computers and small servers. This innovation gave consumers and individuals the ability to carry out their own computational tasks.
For smaller enterprises, such as SMEs, they started to buy cheaper servers to build up a network of servers. Companies can now have their own computing capability to compete with larger enterprises, building their own centralized, small database center. This trend caught on in the late 80s and early 90s, and at the same time, many companies spun off to provide specialized products, such as Cisco to provide dedicated network devices.
It was a golden time for the architecture and the market and this model worked very well in the 1990s, and even at the beginning of the 21st century. But as technology is becoming more and more commonplace, scaling such systems became expensive due to physical constraints. For instance, you have to maintain the temperature and humidity o f a data center to ensure service availability is not affected.
Some companies, namely IBM, had a concept that we should treat computing similar to a water service or power service. This concept, also known as cloud computing, was slow to gather momentum at the beginning due to many constraints. Although cloud computing solves many financial and physical challenges for customers, having data stored in a public location with other customers does not seem like a safe option at first glance.
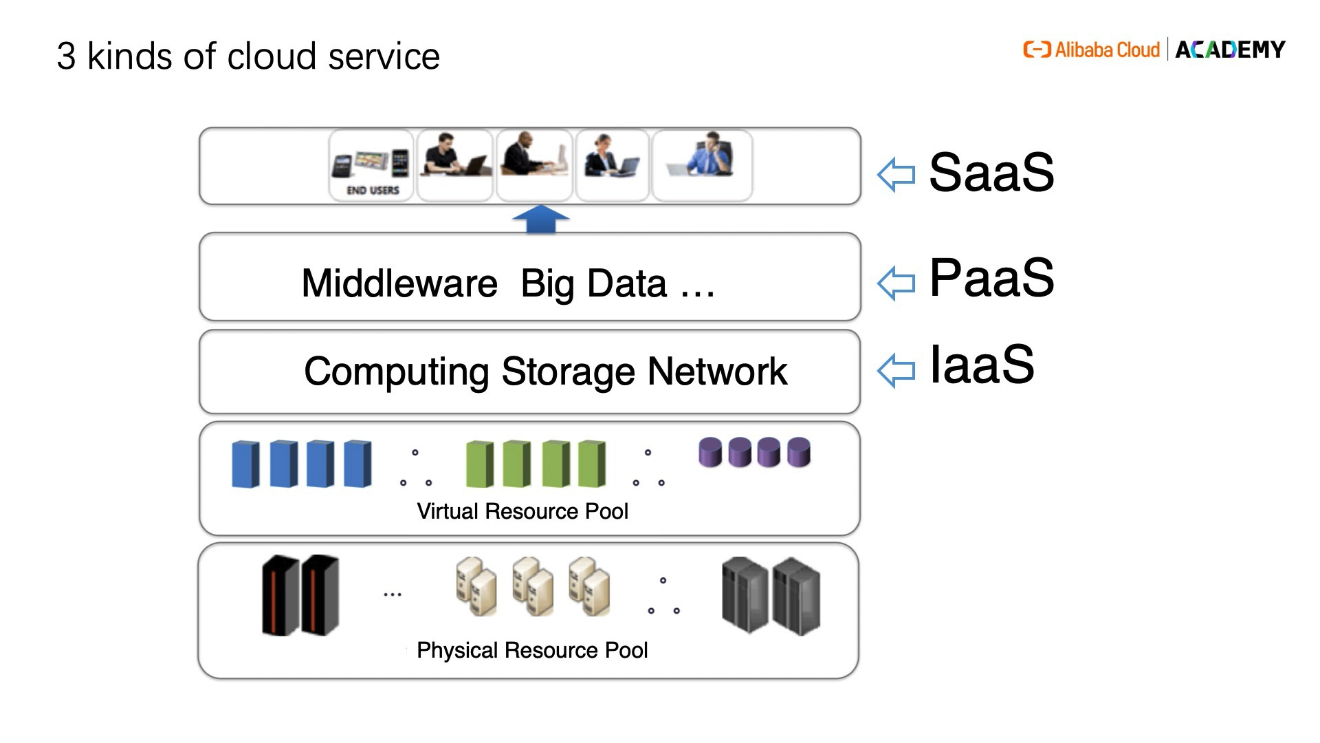
In cloud computing, you only need to manage the parts that are important to your business. Physical aspects, such as server management and updates are taken care of by cloud service providers. From a user's perspective, resources such as networking and storage are virtual resources, which can be created or destroyed (released) rather easily.
They have no sense about any existing infrastructure. They only focus on their business convenience, Easy to use features, and the service staff.
By virtualizing these resources, customers will not be able to access resources created and managed by other users because from their perspective, such resources do not exist. In addition, services like virtual private cloud (VPC) lets customers build an isolated network environment based on Alibaba Cloud, including customizing the IP address range, network segment, route table, and gateway. This gives an additional layer of data security from a software level.
In terms of data storage, services like Alibaba Cloud Object Storage Service (OSS) provides hierarchical security protection and encryption for enterprises, including features such as server-side encryption, client-side encryption, hotlink protection, IP address blacklist or whitelist, fine-grained permission control, log audit, and Write Once Read Many (WORM) policies.
Additionally, data stored in the cloud is not only protected against cyber-attacks, but is also reliable. OSS uses a data redundant storage mechanism to store copies of each object on multiple devices of different facilities in the same region, ensuring data reliability and availability in case of hardware failure. Backing up data on the cloud is more convenient and faster than that of traditional systems.
Another concept that helps ensure data security on the cloud is the shared security responsibilities model. In this model, Alibaba Cloud and its customers are jointly responsible for the security of customers' applications built on Alibaba Cloud. With security responsibilities shared between Alibaba Cloud and its customers, Alibaba Cloud provides a secure infrastructure to decrease the enterprise security burden of customers. As such, customers can configure and use cloud products in a secure manner, thus relieving much of the underlying security burdens while allowing customers to focus more on their core business needs.
You can learn more about our security capabilities and compliances in the Alibaba Cloud Security Whitepaper - The International Version
Ready to test your knowledge? Take the Cloud Platform Security Overview course and get certified today!
Alibaba's POLARDB Powered 11.11, and Now It's Bringing You Games with Zero Latency

64 posts | 54 followers
FollowAlibaba Developer - February 26, 2020
Alex - July 9, 2020
ApsaraDB - December 5, 2018
Alibaba Clouder - July 23, 2018
ApsaraDB - December 5, 2018
Hiteshjethva - April 5, 2023

64 posts | 54 followers
Follow Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)
Industry-standard hardware security modules (HSMs) deployed on Alibaba Cloud.
Learn MoreMore Posts by Alibaba Cloud_Academy