Overview
Alibaba Cloud commits to guide you throughout your digital transformation journey in China. We understand the importance of security compliance and the common challenges faced by MNCs entering and expanding in China. On top of assuring Alibaba Cloud's compliance, this solution provides cloud security compliance capabilities and guidance for you to leverage and stay compliant with the key regulatory requirements, such as MLPS 2.0.
As a pioneer practitioner in MLPS 2.0 implementation, Alibaba Cloud ensures that its cloud platforms meet the MLPS 2.0 baseline. The platform intends to use the technical advantages of its cloud platforms and cloud security services to help implement the classified protection system for cybersecurity quickly, efficiently, and continuously, and improve the overall security protection capabilities of business systems on the cloud.
Download WhitepaperLearn more about Alibaba Cloud MLPS 2.0 Compliance
Contact SalesWhat is Classified Protection of Cybersecurity (CCSP or MLPS)
Classified Protection of Cybersecurity (CCSP), also known as Multi-Level Protection Scheme (MLPS), is a regulatory scheme designed to protect the cybersecurity of networks and systems in China. Under China Cybersecurity Law, it is required that the network operator in China must protect the network and the system components from interruption, damage, unauthorized access with a tiered concept to avoid any data leakage, manipulation, and eavesdropping. It is compulsory for all companies and individuals that own, operate, or provide services relating to network and corresponding system components in China to follow the national standards under the MLPS scheme. MLPS was first introduced in 2008 and subsequently updated to MLPS 2.0 in 2019.
What's New in MLPS 2.0?
There are several new technical and managerial requirement domains raised in MLPS 2.0. There is an emphasis on the concept of "one center, three layers of defense". The adoption of advanced, secure mechanisms is also required under MLPS 2.0, such as the trusted techniques and security management center. On top of the general requirements, a set of additional security requirements are extended to five types of emerging technologies. A corporation is required to have its security defense, risk management, and contingency management established, implemented, and monitored more comprehensively compared to those under MLPS 1.0.
Learn more about Alibaba Cloud MLPS 2.0 Compliance
Contact SalesSolution Highlights

A Comprehensive End-to-End Process
This is a one-stop solution that covers every stage of the MLPS 2.0 process from the classification to inspection. This solution provides you with expert consulting services and the capabilities of implementing a robust, fully compliant MLPS 2.0 infrastructure on the cloud.

Recognized Infrastructure-Level Evaluation Results
You can apply the latest evaluation report on the cloud services of Alibaba Cloud through the Alibaba Cloud ticket system. It can be used as the infrastructure part to form your own classified protection evaluation conclusions to speed up your evaluation process with an excellent result cost-efficiently.
How It Works
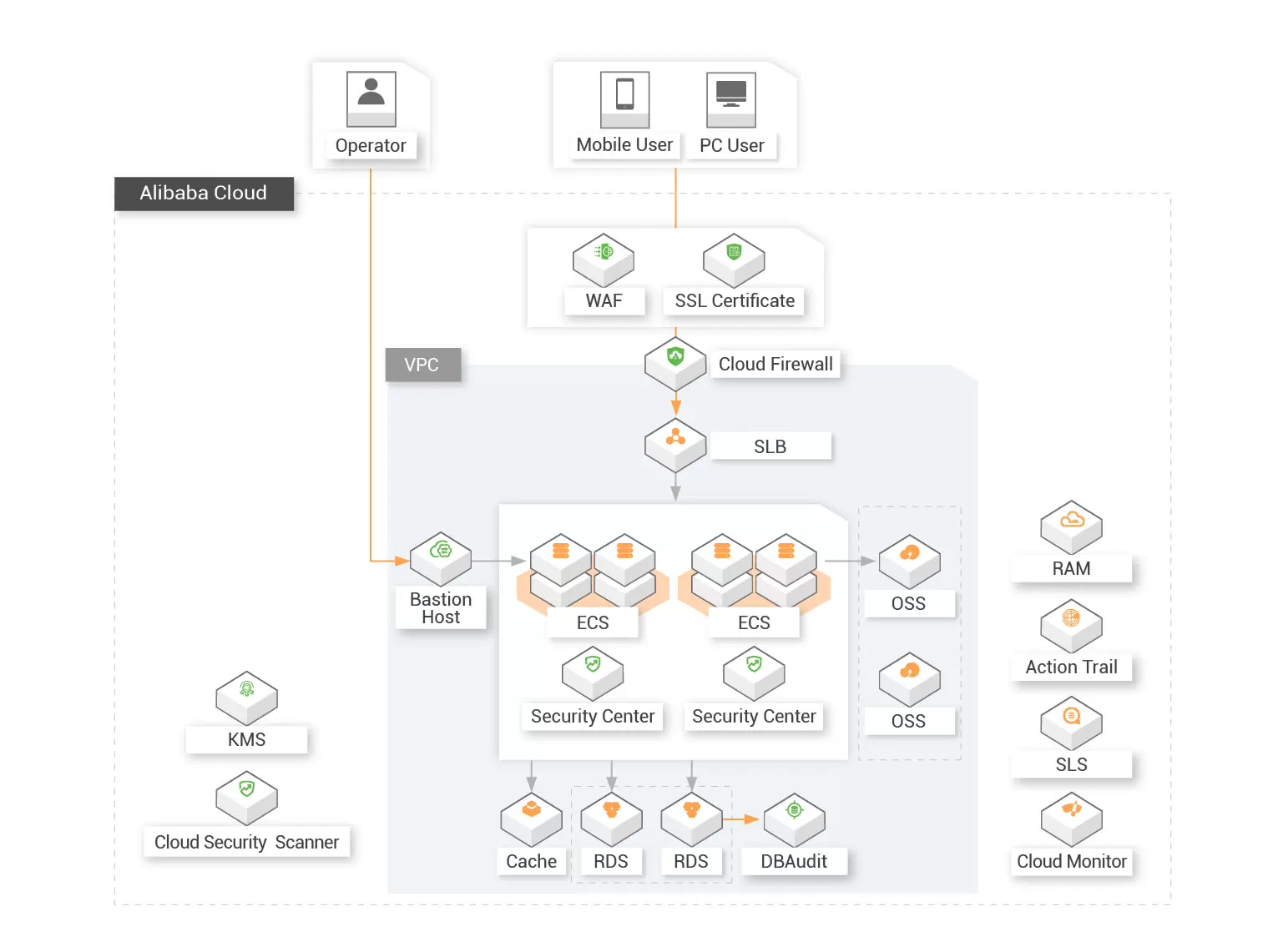
![]() Secured Physical Environment
Secured Physical Environment
Alibaba Cloud services are provided in an MLPS 2.0 compliant physical environment. Our cloud customers can enjoy the secured physical environment with physical access control, anti-theft, anti-sabotage, anti-lighting, fireproof, waterproof, damp-proof, temperature and humidity control, power supply management, and electromagnetic protection.
![]() Secured Communication Network
Secured Communication Network
Alibaba Cloud services are provided based on a secured communication network. Our cloud customers can leverage Alibaba Cloud's network product and security product to build secured network architecture for secured communication and transmission. On top of the measures mentioned above, our cloud customer can also benefit from the trusted authentication mechanisms provided by Alibaba Cloud.
![]() Secured Zone Boundary
Secured Zone Boundary
Alibaba Cloud provides our customers with the capability to protect the security boundaries with access control, intrusion prevention, malicious code prevention and security audit.
![]() Secured Computing Environment
Secured Computing Environment
Alibaba Cloud provides our customers with the capability to secure their computing environment with identity authentication and management, access control, security audit, intrusion prevention, personal and important data protection.
![]() Security Management Center
Security Management Center
Alibaba Cloud provides our customers with a unified security management system that identifies, analyzes, and notifies you of security threats in real time.
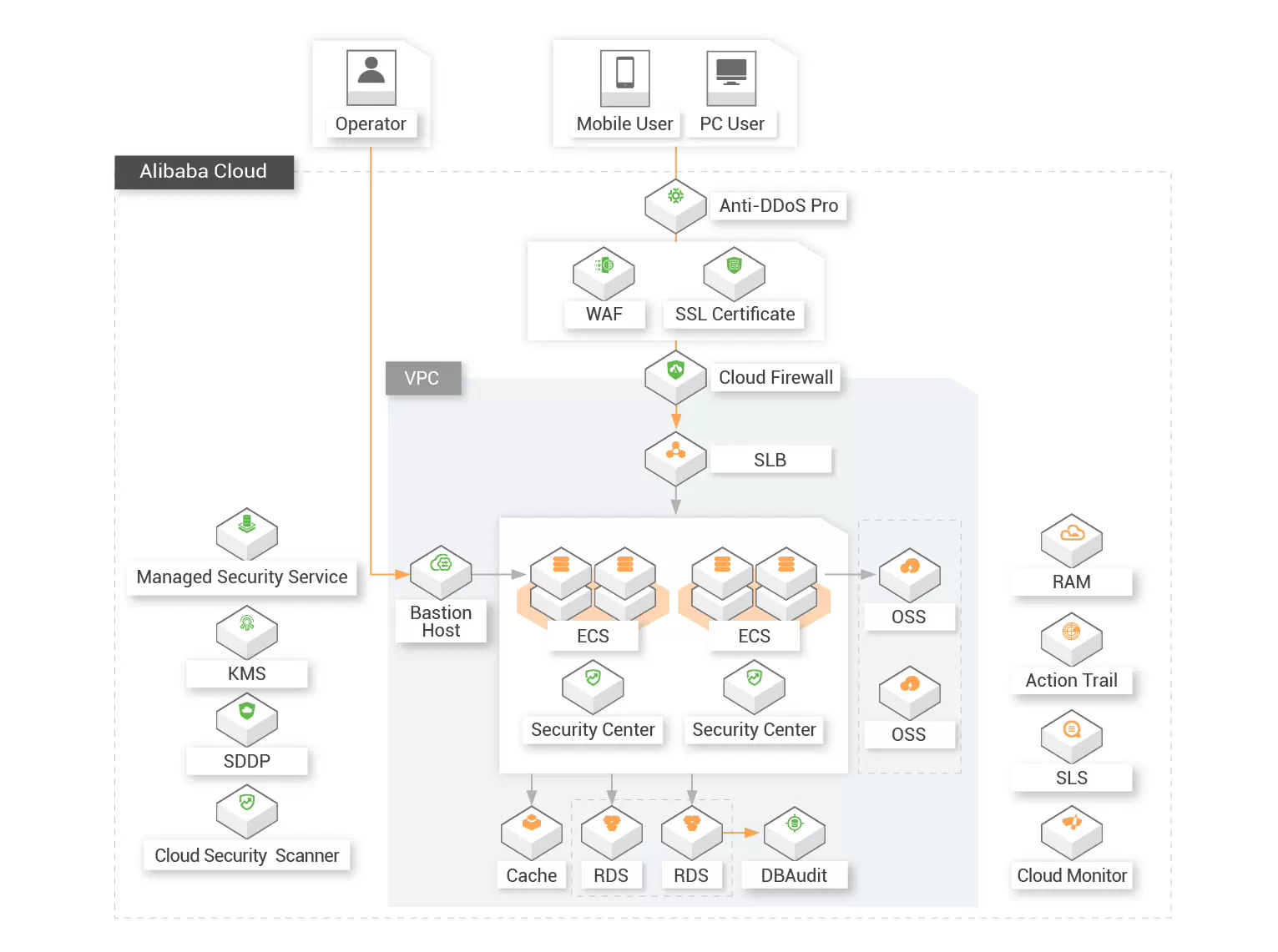
![]() Secured Physical Environment
Secured Physical Environment
Alibaba Cloud services are provided in an MLPS 2.0 compliant physical environment. Our cloud customers can enjoy the secured physical environment with physical access control, anti-theft, anti-sabotage, anti-lighting, fireproof, waterproof, damp-proof, temperature and humidity control, power supply management and electromagnetic protection.
![]() Secured Communication Network
Secured Communication Network
Alibaba Cloud services are provided based on a secured communication network. Our cloud customers can leverage Alibaba Cloud's network product and security product to build secured network architecture for secured communication and transmission. Our customers can flexibly manage the bandwidth on the cloud to deal with peak business needs, encrypt the important data before the transmission, and manage the key with our KMS services. On top of the measures mentioned above, our cloud customers can also benefit from the trusted authentication mechanisms provided by Alibaba Cloud.
![]() Secured Zone Boundary
Secured Zone Boundary
Alibaba Cloud provides our customers with the capability to protect the security boundaries with access control, intrusion prevention, malicious code prevention and security audit. With the incorporation of the Anti-DDoS Pro, comprehensive DDoS protection to intelligently defend sophisticated DDoS attacks with over 1.6Tbps mitigation capacity and mitigates potential security threats.
![]() Secured Computing Environment
Secured Computing Environment
Alibaba Cloud provides our customers with the capability to secure their computing environment with identity authentication and management, access control, security audit, intrusion prevention, encryption, key management, data integrity protection, vulnerability management, and personal and important data protection.
![]() Security Management Center
Security Management Center
Alibaba Cloud provides our customers with a unified security management system that identifies, analyzes, and notifies you of security threats in real-time.
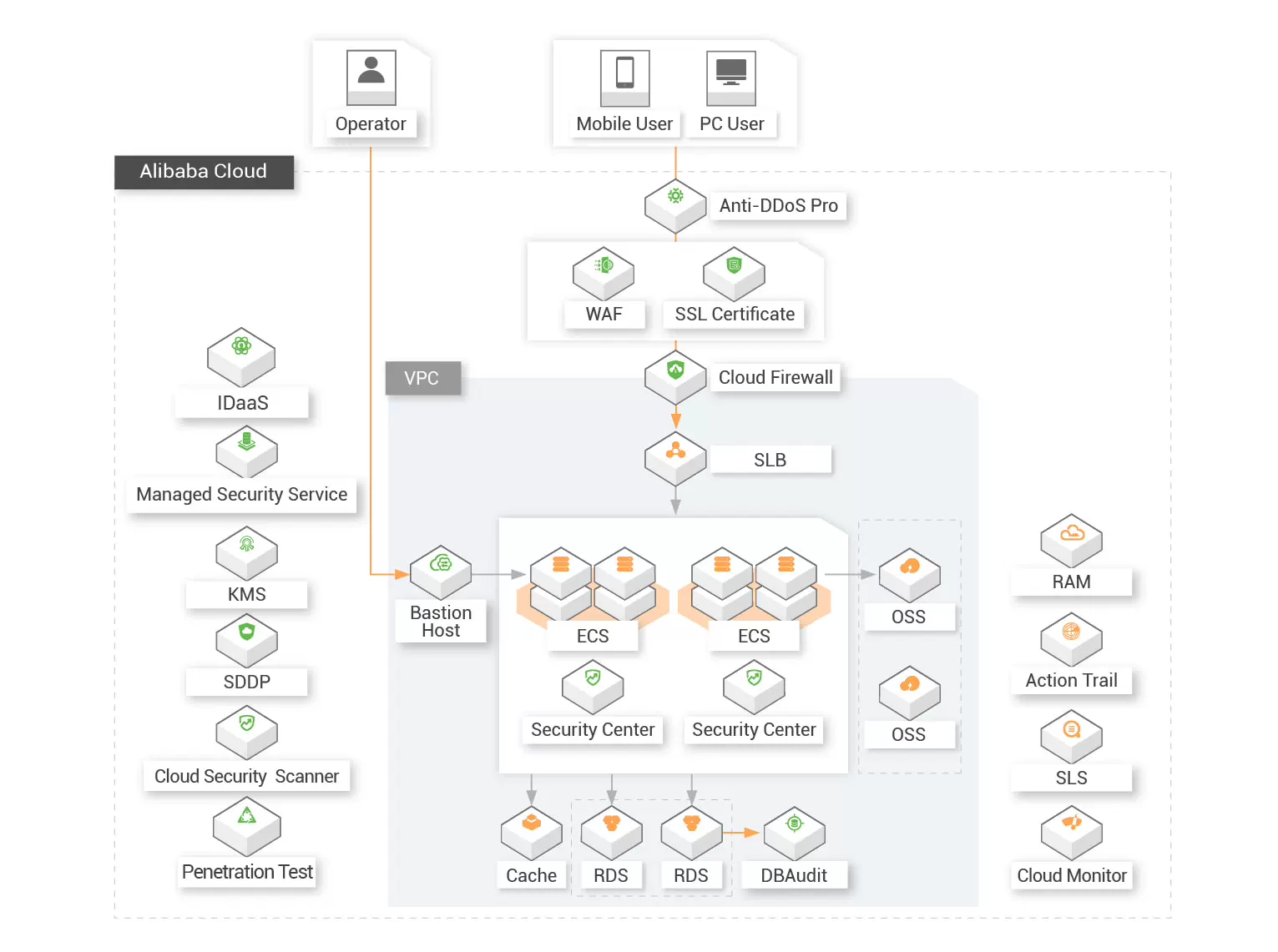
![]() Secured Physical Environment
Secured Physical Environment
Alibaba Cloud services are provided in an MLPS 2.0 compliant physical environment. Our cloud customers can enjoy the secured physical environment with physical access control, anti-theft, anti-sabotage, anti-lighting, fireproof, waterproof, damp-proof, temperature and humidity control, power supply management, and electromagnetic protection.
![]() Secured Communication Network
Secured Communication Network
Alibaba Cloud services are provided based on a secured communication network. Our cloud customers can leverage Alibaba Cloud's network product and security product to build secured network architecture for secured communication and transmission. Our customers can flexibly manage the bandwidth on the cloud to deal with the peak business needs, encrypt the important data before the transmission, and manage the key with our KMS services. On top of the measures mentioned above, our cloud customer can also benefit from the trusted authentication mechanisms provided by Alibaba Cloud.
![]() Secured Zone Boundary
Secured Zone Boundary
Alibaba Cloud provides our customers with the capability to protect the security boundaries with access control, intrusion prevention, malicious code prevention and security audit. With the incorporation of the Anti-DDoS Pro, comprehensive DDoS protection to intelligently defend sophisticated DDoS attacks with over 1.6Tbps mitigation capacity and mitigates potential security threats.
![]() Secured Computing Environment
Secured Computing Environment
Alibaba Cloud provides our customers with the capability to secure their computing environment with identity authentication and management, access control, security audit, intrusion prevention, encryption, key management, data integrity protection, vulnerability management, and personal and important data protection. Our customers can manage multiple identities across applications on a central platform through our IDaaS offering.
![]() Security Management Center
Security Management Center
Alibaba Cloud provides our customers with a unified security management system that identifies, analyzes, and notifies you of security threats in real-time.
Learn more about Alibaba Cloud MLPS 2.0 Compliance
Contact SalesMLPS Evaluation Process
MLPS is a holistic regulatory requirement system supported by a comprehensive end-to-end process that has five stages: Classification, Filing, Implementation and Rectification, Evaluation, and Authority Inspection. The classified object (i.e., the object to pass MLPS evaluation) is recommended to be assessed regarding the requirements for the corresponding classified level and implemented with the rectification measures to close the gaps before the evaluation process. The evaluation can only be conducted by the qualified evaluation agency in China according to the relevant requirements in "Baseline for classified protection of cybersecurity". The evaluation report issued by the qualified evaluation agency shall be submitted to the corresponding local agency of the Office of Cyber Security of the Ministry of Public Security (local government authority) for inspection and endorsement.
-
Compliance Process
-
Corporate Customer
-
Alibaba Cloud
-
Advisory Agency
-
Evaluation Agency
-
Government Authority
-
Classification
-
Determine the classified level of the object, prepare classification endorsement report.
-
Assist corporate customers in classification process.
-
Advise customers in preparing the classification report and organize the review with expert personnel.
-
Filing
-
Endorse the classification report and filing documents to the local government agency for filing.
-
Provide guidance for filing.
-
Advise customers in preparing the filing documents and complete the filing process.
-
Verify the filing documents.
-
Implementation and Rectification
-
Assess regarding the MLPS baseline requirements to identify and rectify the gaps.
-
Advise the security products to fulfill the relevant requirements of MLPS 2.0.
-
Advise customers in security hardening and assist customers in implementing the security management system.
-
Evaluation
-
Appoint external qualified evaluation agency to have the object evaluated and obtain the evaluation report.
-
On top of providing the certificate and compliance reports of Alibaba Cloud, Alibaba Cloud provides a one-stop evaluation service to corporate customer.
-
Advise customers in assessment and rectification.
-
Evaluate the object and issue the evaluation report.
-
Authority Inspection
-
Submit the evaluation report to the local government authority and cooperate with government officers for authority inspection.
-
Assist customers in completing the inspection and rectification.
-
Inspect the security mechanisms and measures to protect the object.
-
Corporate Customer
Determine the classified level of the object, prepare classification endorsement report.
-
Alibaba Cloud
Assist corporate customers in classification process.
-
Advisory Agency
Advise customers in preparing the classification report and organize the review with expert personnel.
-
Evaluation Agency
-
Government Authority
-
Corporate Customer
Endorse the classification report and filing documents to the local government agency for filing.
-
Alibaba Cloud
Provide guidance for filing.
-
Advisory Agency
Advise customers in preparing the filing documents and complete the filing process.
-
Evaluation Agency
-
Government Authority
Verify the filing documents.
-
Corporate Customer
Assess regarding the MLPS baseline requirements to identify and rectify the gaps.
-
Alibaba Cloud
Advise the security products to fulfill the relevant requirements of MLPS 2.0.
-
Advisory Agency
Advise customers in security hardening and assist customers in implementing the security management system.
-
Evaluation Agency
-
Government Authority
-
Corporate Customer
Appoint external qualified evaluation agency to have the object evaluated and obtain the evaluation report.
-
Alibaba Cloud
On top of providing the certificate and compliance reports of Alibaba Cloud, Alibaba Cloud provides a one-stop evaluation service to corporate customer.
-
Advisory Agency
Advise customers in assessment and rectification.
-
Evaluation Agency
Evaluate the object and issue the evaluation report.
-
Government Authority
-
Corporate Customer
Submit the evaluation report to the local government authority and cooperate with government officers for authority inspection.
-
Alibaba Cloud
-
Advisory Agency
Assist customers in completing the inspection and rectification.
-
Evaluation Agency
-
Government Authority
Inspect the security mechanisms and measures to protect the object.
Related Resources
Webinar
MLPS 2.0 Insight and Alibaba Cloud's Solutions
Watch this webinar to learn about MLPS 2.0 and how Alibaba Cloud can help your business comply with MLPS 2.0.
Whitepaper
Alibaba Cloud Security Compliance Whitepaper for MLPS 2.0 Baseline
It's designed to help our cloud customers establish a security system on the cloud that is compliant with MLPS 2.0 in an easier way.
Whitepaper
2020 Alibaba Cloud Security Whitepaper - The China Gateway Version
Introduces the public cloud security system of Alibaba Cloud, specifically for security capabilities and offerings in the Chinese mainland.






