本文介紹如何在本機資料中心IDC(Internet Data Center)和Virtual Private Cloud(Virtual Private Cloud)之間建立多條公網IPsec-VPN串連,組成ECMP(Equal-Cost Multipath Routing)鏈路實現本地IDC和VPC之間流量的負載分擔。
情境樣本
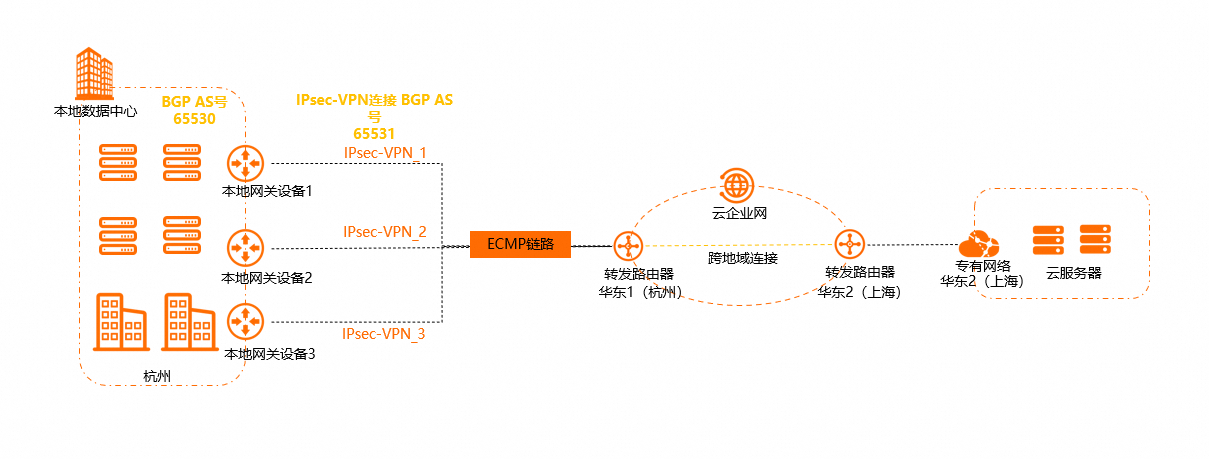
本文以上圖情境為例。某企業在中國杭州擁有一個本地IDC,在阿里雲華東2(上海)地區擁有一個VPC執行個體,VPC執行個體中已通過Elastic Compute Service(Elastic Compute Service)部署了相關業務。企業希望本地IDC可以通過VPN網關產品加密上雲,實現和VPC執行個體之間的相互連信,同時希望本地IDC和VPC執行個體之間可以通過多條加密隧道互相通訊,多條加密隧道組成ECMP鏈路,實現流量的負載分擔。
企業可以在本地IDC和阿里雲之間建立多條IPsec-VPN串連,實現本地IDC加密上雲,然後通過雲企業網產品將多條IPsec-VPN串連和VPC執行個體串連起來,多條IPsec-VPN串連加入雲企業網後可以自動組成ECMP鏈路,實現本地IDC和VPC執行個體之間的相互連信以及流量的負載分擔。
網路規劃
網路功能規劃
在本文情境中使用的網路功能如下:
通過互連網在本地IDC和阿里雲之間建立IPsec-VPN串連,即IPsec串連的網關類型為公網。
IPsec串連綁定的資源類型需為Cloud Enterprise Network,以實現多條IPsec-VPN串連組成ECMP鏈路。
IPsec串連和本地IDC之間使用BGP動態路由協議。
網段規劃
在您規劃網段時,請確保本地IDC和VPC之間要互連的網段沒有重疊。
資源 | 網段及IP地址 |
VPC | 主網段:10.0.0.0/16
|
IPsec串連 | BGP配置:
|
本地網關裝置 | 本地網關裝置公網IP地址:
|
本地網關裝置BGP配置:
| |
本地IDC | 待和VPC互連的網段:
|
準備工作
在開始配置前,請確保您已完成以下操作:
您已經在阿里雲華東2(上海)地區建立了一個VPC執行個體,並使用ECS部署了相關業務。具體操作,請參見搭建IPv4專用網路。
您已經建立了雲企業網執行個體,並在華東1(杭州)和華東2(上海)地區分別建立了企業版轉寄路由器。具體操作,請參見建立雲企業網執行個體和建立轉寄路由器執行個體。
重要建立轉寄路由器執行個體時,需為轉寄路由器執行個體配置轉寄路由器位址區段,否則IPsec串連無法成功綁定轉寄路由器執行個體。
如果您已經建立了轉寄路由器執行個體,您可以單獨為轉寄路由器執行個體添加轉寄路由器位址區段。具體操作,請參見添加轉寄路由器位址區段。
您已經瞭解VPC中ECS執行個體所應用的安全性群組規則,並確保安全性群組規則允許本地IDC和ECS執行個體互相通訊。具體操作,請參見查詢安全性群組規則和添加安全性群組規則。
配置流程

步驟一:建立使用者網關
在建立IPsec-VPN串連前,您需要先建立使用者網關,將本地網關裝置的資訊註冊至阿里雲上。
登入VPN網關管理主控台。
在左側導覽列,選擇。
在頂部功能表列,選擇使用者網關的地區。
選擇使用者網關所屬的地區時,需遵循就近原則,即選擇離您本地IDC最近的阿里雲地區。本文中選擇華東1(杭州)。
在使用者網關頁面,單擊建立使用者網關。
在建立使用者網關面板,根據以下資訊進行配置,然後單擊確定。
請根據以下配置在華東1(杭州)地區分別建立3個使用者網關,其餘配置項保持預設狀態。更多資訊,請參見建立和系統管理使用者網關。
配置項
配置項說明
使用者網關1
使用者網關2
使用者網關3
名稱
輸入使用者網關的名稱。
本文輸入Customer-Gateway1。
本文輸入Customer-Gateway2。
本文輸入Customer-Gateway3。
IP地址
輸入阿里雲側待串連的本地網關裝置的公網IP地址。
本文輸入本地網關裝置1的公網IP地址11.XX.XX.1。
本文輸入本地網關裝置2的公網IP地址11.XX.XX.2。
本文輸入本地網關裝置3的公網IP地址11.XX.XX.3。
自治系統號
輸入本地網關裝置使用的BGP AS號。
本文輸入65530。
步驟二:建立IPsec串連
建立使用者網關後,您需要在阿里雲側建立IPsec串連,以便本地IDC和阿里雲之間建立IPsec-VPN串連。
登入VPN網關管理主控台。
在左側導覽列,選擇。
在IPsec串連頁面,單擊綁定雲企業網。
在建立IPsec串連(CEN)頁面,根據以下資訊配置IPsec串連,然後單擊確定。
請根據以下配置資訊,在華東1(杭州)地區分別建立3個IPsec串連,其餘配置項保持預設狀態。更多資訊,請參見管理單隧道模式IPsec串連。
配置項
配置項說明
IPsec串連1
IPsec串連2
IPsec串連3
IPsec串連名稱
輸入IPsec串連的名稱。
本文輸入IPsec串連1。
本文輸入IPsec串連2。
本文輸入IPsec串連3。
地區
選擇待綁定的轉寄路由器所屬的地區。
IPsec串連建立完成後所屬地區與轉寄路由器地區相同。
選擇華東1(杭州)。
網關類型
選擇IPsec串連的網路類型。
本文選擇公網。
綁定雲企業網
選擇IPsec串連要綁定的轉寄路由器所屬帳號。
選擇本帳號綁定。
Cloud Enterprise Network執行個體ID
選擇雲企業網執行個體。
本文選擇在準備工作中已建立的雲企業網執行個體。
系統將會一併展示雲企業網執行個體在該地區建立的轉寄路由器執行個體ID和轉寄路由器位址區段,IPsec串連將會被綁定至該轉寄路由器。
可用區
在轉寄路由器支援的可用性區域中選擇部署IPsec串連的可用性區域。
本文選擇杭州可用性區域H。
路由模式
選擇路由模式。
本文選擇目的路由模式。
說明在使用BGP動態路由協議的情況下,推薦使用目的路由模式。
立即生效
選擇IPsec串連的配置是否立即生效。取值:
是,配置完成後立即進行協商
否,當有流量進入時進行協商
本文選擇是。
使用者網關
選擇IPsec串連關聯的使用者網關。
本文選擇Customer-Gateway1。
本文選擇Customer-Gateway2。
本文選擇Customer-Gateway3。
預先共用金鑰
輸入IPsec串連的認證密鑰,用於本地網關裝置和IPsec串連之間的身份認證。
密鑰長度為1~100個字元,支援數字、大小寫英文字母及右側字元
~`!@#$%^&*()_-+={}[]\|;:',.<>/?,不能包含空格。若您未指定預先共用金鑰,系統會隨機產生一個16位的字串作為預先共用金鑰。建立IPsec串連後,您可以通過隧道的編輯按鈕查看系統產生的預先共用金鑰。
重要IPsec串連及其對端網關裝置配置的預先共用金鑰需一致,否則系統無法正常建立IPsec-VPN串連。
本文輸入fddsFF123****。
本文輸入fddsFF456****。
本文輸入fddsFF789****。
啟用BGP
選擇是否開啟BGP功能。BGP功能預設為關閉狀態。
本文開啟BGP功能。
本端自治系統號
輸入IPsec串連的自治系統號。
本文輸入65531。
本文輸入65531。
本文輸入65531。
加密配置
添加IKE配置、IPsec配置等加密配置。
除以下參數外,其餘配置項保持預設值。
IKE配置的DH分組選擇group14。
IPsec配置的DH分組選擇group14。
說明您需要根據本地網關裝置的支援情況選擇加密配置參數,確保IPsec串連和本地網關裝置的加密配置保持一致。
BGP配置
隧道網段
輸入建立加密隧道時使用的網段。
隧道網段需要是在169.254.0.0/16內的子網路遮罩為30的網段,且不能是169.254.0.0/30、169.254.1.0/30、169.254.2.0/30、169.254.3.0/30、169.254.4.0/30、169.254.5.0/30、169.254.6.0/30和169.254.169.252/30。
本文輸入169.254.10.0/30。
本文輸入169.254.11.0/30。
本文輸入169.254.12.0/30。
本端BGP地址
輸入IPsec串連的BGP IP地址。
該地址為隧道網段內的一個IP地址。
本文輸入169.254.10.1。
本文輸入169.254.11.1。
本文輸入169.254.12.1。
進階配置
選擇是否啟用進階配置,實現IPsec連線路由的自動分發和學習。系統預設啟用進階配置。
本文保持預設值,即開啟所有進階配置。
IPsec串連建立成功後,系統將自動為每個IPsec串連分配一個網關IP地址,用於IPsec串連和本地網關裝置之間建立IPsec-VPN串連。您可以在IPsec串連詳情頁面查看網關IP地址,如下圖所示。

本文中,系統為IPsec串連1、IPsec串連2、IPsec串連3分配的網關IP地址如下表所示。
IPsec串連
網關IP地址
IPsec串連1
120.XX.XX.191
IPsec串連2
47.XX.XX.213
IPsec串連3
47.XX.XX.161
說明IPsec串連綁定轉寄路由器執行個體後系統才會為其分配網關IP地址。
返回到IPsec串連頁面,找到剛剛建立的IPsec串連,在操作列選擇產生對端配置。
請分別下載3個IPsec串連的配置並將配置儲存在您的本地電腦,用於後續在本地網關裝置中添加VPN配置。
步驟三:配置本地網關裝置
建立IPsec串連後,請依據下載的IPsec串連配置以及下述步驟,分別在本地網關裝置1、本地網關裝置2、本地網關裝置3中添加VPN配置和BGP配置,以便本地IDC和阿里雲之間建立IPsec-VPN串連。
本文以思科防火牆ASA(軟體版本9.19.1)作為配置樣本。不同軟體版本的配置命令可能會有所差異,操作時請根據您的實際環境查詢對應文檔或諮詢相關廠商。更多本地網關裝置配置樣本,請參見本地網關裝置配置樣本。
以下內容包含的第三方產品資訊僅供參考。阿里雲對第三方產品的效能、可靠性以及操作可能帶來的潛在影響,不做任何暗示或其他形式的承諾。
配置本地網關裝置。
本地網關裝置1配置樣本
登入思科防火牆的命令列視窗並進入配置模式。
ciscoasa> enable Password: ******** #輸入進入enable模式的密碼。 ciscoasa# configure terminal #進入配置模式。 ciscoasa(config)#查看介面配置。
請確保思科防火牆已完成了介面配置,並已開啟介面。以下為本文的介面配置樣本。
#查看本地網關裝置1的介面配置 ciscoasa(config)# show running-config interface ! interface GigabitEthernet0/0 #串連公網的介面。 nameif outside1 #GigabitEthernet0/0介面名稱。 security-level 0 ip address 11.XX.XX.1 255.255.255.255 #GigabitEthernet0/0介面配置的公網IP地址。 ! interface GigabitEthernet0/1 #串連本機資料中心的介面。 nameif private #GigabitEthernet0/1介面名稱。 security-level 100 #指定串連本機資料中心介面(私網介面)的security-level低於公網介面。 ip address 192.168.50.216 255.255.255.0 #GigabitEthernet0/1介面配置的IP地址。 !為公網介面開啟IKEv2功能。
#在本地網關裝置1上添加如下配置 crypto ikev2 enable outside1 #為本地網關裝置1的outside1介面(公網介面)開啟IKEv2功能。建立IKEv2 Policy,指定IKE階段認證演算法、密碼編譯演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置1上添加如下配置 crypto ikev2 policy 10 encryption aes #指定密碼編譯演算法。 integrity sha #指定認證演算法。 group 14 #指定DH分組。 prf sha #prf和integrity保持一致,阿里雲側prf與認證演算法預設保持一致。 lifetime seconds 86400 #指定SA生存周期。建立IPsec proposal和profile,指定思科防火牆側的IPsec階段密碼編譯演算法、認證演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置1上添加如下配置 crypto ipsec ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec proposal。 protocol esp encryption aes #指定密碼編譯演算法,協議使用ESP,阿里雲側固定使用ESP協議。 protocol esp integrity sha-1 #指定認證演算法,協議使用ESP,阿里雲側固定使用ESP協議。 crypto ipsec profile ALIYUN-PROFILE set ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec profile並應用已建立的proposal。 set ikev2 local-identity address #指定本端ID使用IP地址格式,與阿里雲側RemoteId格式保持一致。 set pfs group14 #指定pfs和DH分組。 set security-association lifetime seconds 86400 #指定基於時間的SA生存周期。 set security-association lifetime kilobytes unlimited #關閉基於流量的SA生存周期。建立tunnel group,指定隧道的預先共用金鑰,需和阿里雲側保持一致。
#在本地網關裝置1上添加如下配置 tunnel-group 120.XX.XX.191 type ipsec-l2l #指定隧道的封裝模式為l2l。 tunnel-group 120.XX.XX.191 ipsec-attributes ikev2 remote-authentication pre-shared-key fddsFF123**** #指定隧道對端的預先共用金鑰,即阿里雲側的預先共用金鑰。 ikev2 local-authentication pre-shared-key fddsFF123**** #指定隧道本端的預先共用金鑰,需和阿里雲側的保持一致。 !建立tunnel介面。
#在本地網關裝置1上添加如下配置 interface Tunnel1 #建立隧道介面。 nameif ALIYUN1 ip address 169.254.10.2 255.255.255.252 #指定介面的IP地址。 tunnel source interface outside1 #指定隧道源地址為公網介面GigabitEthernet0/0。 tunnel destination 120.XX.XX.191 #指定隧道目的地址為阿里雲側IPsec串連1的公網IP地址。 tunnel mode ipsec ipv4 tunnel protection ipsec profile ALIYUN-PROFILE #指定隧道應用ipsec profile ALIYUN-PROFILE。 no shutdown #開啟隧道介面。 !配置路由。
#在本地網關裝置1上添加如下配置 route outside1 120.XX.XX.191 255.255.255.255 192.XX.XX.172 #配置訪問阿里雲側IPsec串連1公網IP地址的路由,下一跳為外網地址。 route private 192.168.0.0 255.255.255.0 192.168.50.215 #配置去往本機資料中心的路由。 route private 192.168.1.0 255.255.255.0 192.168.50.215 route private 192.168.2.0 255.255.255.0 192.168.50.215 router bgp 65530 address-family ipv4 unicast neighbor 169.254.10.1 remote-as 65531 #指定BGP鄰居,即阿里雲側IPsec串連1的BGP IP地址。 neighbor 169.254.10.1 ebgp-multihop 255 neighbor 169.254.10.1 activate #啟用BGP鄰居。 network 192.168.0.0 mask 255.255.255.0 #宣告本機資料中心的網段。 network 192.168.1.0 mask 255.255.255.0 network 192.168.2.0 mask 255.255.255.0 exit-address-family
本地網關裝置2配置樣本
登入思科防火牆的命令列視窗並進入配置模式。
ciscoasa> enable Password: ******** #輸入進入enable模式的密碼。 ciscoasa# configure terminal #進入配置模式。 ciscoasa(config)#查看介面配置。
請確保思科防火牆已完成了介面配置,並已開啟介面。以下為本文的介面配置樣本。
#查看本地網關裝置2的介面配置 ciscoasa(config)# show running-config interface ! interface GigabitEthernet0/0 #串連公網的介面。 nameif outside1 #GigabitEthernet0/0介面名稱。 security-level 0 ip address 11.XX.XX.2 255.255.255.255 #GigabitEthernet0/0介面配置的公網IP地址。 ! interface GigabitEthernet0/1 #串連本機資料中心的介面。 nameif private #GigabitEthernet0/1介面名稱。 security-level 100 #指定串連本機資料中心介面(私網介面)的security-level低於公網介面。 ip address 192.168.50.218 255.255.255.0 #GigabitEthernet0/1介面配置的IP地址。 !為公網介面開啟IKEv2功能。
#在本地網關裝置2上添加如下配置 crypto ikev2 enable outside1 #為本地網關裝置2的outside1介面(公網介面)開啟IKEv2功能。建立IKEv2 Policy,指定IKE階段認證演算法、密碼編譯演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置2上添加如下配置 crypto ikev2 policy 10 encryption aes #指定密碼編譯演算法。 integrity sha #指定認證演算法。 group 14 #指定DH分組。 prf sha #prf和integrity保持一致,阿里雲側prf與認證演算法預設保持一致。 lifetime seconds 86400 #指定SA生存周期。建立IPsec proposal和profile,指定思科防火牆側的IPsec階段密碼編譯演算法、認證演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置2上添加如下配置 crypto ipsec ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec proposal。 protocol esp encryption aes #指定密碼編譯演算法,協議使用ESP,阿里雲側固定使用ESP協議。 protocol esp integrity sha-1 #指定認證演算法,協議使用ESP,阿里雲側固定使用ESP協議。 crypto ipsec profile ALIYUN-PROFILE set ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec profile並應用已建立的proposal。 set ikev2 local-identity address #指定本端ID使用IP地址格式,與阿里雲側RemoteId格式保持一致。 set pfs group14 #指定pfs和DH分組。 set security-association lifetime seconds 86400 #指定基於時間的SA生存周期。 set security-association lifetime kilobytes unlimited #關閉基於流量的SA生存周期。建立tunnel group,指定隧道的預先共用金鑰,需和阿里雲側保持一致。
#在本地網關裝置2上添加如下配置 tunnel-group 47.XX.XX.213 type ipsec-l2l #指定隧道的封裝模式為l2l。 tunnel-group 47.XX.XX.213 ipsec-attributes ikev2 remote-authentication pre-shared-key fddsFF456**** #指定隧道對端的預先共用金鑰,即阿里雲側的預先共用金鑰。 ikev2 local-authentication pre-shared-key fddsFF456**** #指定隧道本端的預先共用金鑰,需和阿里雲側的保持一致。 !建立tunnel介面。
#在本地網關裝置2上添加如下配置 interface Tunnel1 #建立隧道介面。 nameif ALIYUN1 ip address 169.254.11.2 255.255.255.252 #指定介面的IP地址。 tunnel source interface outside1 #指定隧道源地址為公網介面GigabitEthernet0/0。 tunnel destination 47.XX.XX.213 #指定隧道目的地址為阿里雲側IPsec串連2的公網IP地址。 tunnel mode ipsec ipv4 tunnel protection ipsec profile ALIYUN-PROFILE #指定隧道應用ipsec profile ALIYUN-PROFILE。 no shutdown #開啟隧道介面。 !配置路由。
#在本地網關裝置2上添加如下配置 route outside1 47.XX.XX.213 255.255.255.255 192.XX.XX.173 #配置訪問阿里雲側IPsec串連2公網IP地址的路由,下一跳為外網地址。 route private 192.168.0.0 255.255.255.0 192.168.50.217 #配置去往本機資料中心的路由。 route private 192.168.1.0 255.255.255.0 192.168.50.217 route private 192.168.2.0 255.255.255.0 192.168.50.217 router bgp 65530 address-family ipv4 unicast neighbor 169.254.11.1 remote-as 65531 #指定BGP鄰居,即阿里雲側IPsec串連2的BGP IP地址。 neighbor 169.254.11.1 ebgp-multihop 255 neighbor 169.254.11.1 activate #啟用BGP鄰居。 network 192.168.0.0 mask 255.255.255.0 #宣告本機資料中心的網段。 network 192.168.1.0 mask 255.255.255.0 network 192.168.2.0 mask 255.255.255.0 exit-address-family
本地網關裝置3配置樣本
登入思科防火牆的命令列視窗並進入配置模式。
ciscoasa> enable Password: ******** #輸入進入enable模式的密碼。 ciscoasa# configure terminal #進入配置模式。 ciscoasa(config)#查看介面配置。
請確保思科防火牆已完成了介面配置,並已開啟介面。以下為本文的介面配置樣本。
#查看本地網關裝置3的介面配置 ciscoasa(config)# show running-config interface ! interface GigabitEthernet0/0 #串連公網的介面。 nameif outside1 #GigabitEthernet0/0介面名稱。 security-level 0 ip address 11.XX.XX.3 255.255.255.255 #GigabitEthernet0/0介面配置的公網IP地址。 ! interface GigabitEthernet0/1 #串連本機資料中心的介面。 nameif private #GigabitEthernet0/1介面名稱。 security-level 100 #指定串連本機資料中心介面(私網介面)的security-level低於公網介面。 ip address 192.168.50.213 255.255.255.0 #GigabitEthernet0/1介面配置的IP地址。 !為公網介面開啟IKEv2功能。
#在本地網關裝置3上添加如下配置 crypto ikev2 enable outside1 #為本地網關裝置3的outside1介面(公網介面)開啟IKEv2功能。建立IKEv2 Policy,指定IKE階段認證演算法、密碼編譯演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置3上添加如下配置 crypto ikev2 policy 10 encryption aes #指定密碼編譯演算法。 integrity sha #指定認證演算法。 group 14 #指定DH分組。 prf sha #prf和integrity保持一致,阿里雲側prf與認證演算法預設保持一致。 lifetime seconds 86400 #指定SA生存周期。建立IPsec proposal和profile,指定思科防火牆側的IPsec階段密碼編譯演算法、認證演算法、DH分組和SA生存周期,需和阿里雲側保持一致。
#在本地網關裝置3上添加如下配置 crypto ipsec ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec proposal。 protocol esp encryption aes #指定密碼編譯演算法,協議使用ESP,阿里雲側固定使用ESP協議。 protocol esp integrity sha-1 #指定認證演算法,協議使用ESP,阿里雲側固定使用ESP協議。 crypto ipsec profile ALIYUN-PROFILE set ikev2 ipsec-proposal ALIYUN-PROPOSAL #建立ipsec profile並應用已建立的proposal。 set ikev2 local-identity address #指定本端ID使用IP地址格式,與阿里雲側RemoteId格式保持一致。 set pfs group14 #指定pfs和DH分組。 set security-association lifetime seconds 86400 #指定基於時間的SA生存周期。 set security-association lifetime kilobytes unlimited #關閉基於流量的SA生存周期。建立tunnel group,指定隧道的預先共用金鑰,需和阿里雲側保持一致。
#在本地網關裝置3上添加如下配置 tunnel-group 47.XX.XX.161 type ipsec-l2l #指定隧道的封裝模式為l2l。 tunnel-group 47.XX.XX.161 ipsec-attributes ikev2 remote-authentication pre-shared-key fddsFF789**** #指定隧道對端的預先共用金鑰,即阿里雲側的預先共用金鑰。 ikev2 local-authentication pre-shared-key fddsFF789**** #指定隧道本端的預先共用金鑰,需和阿里雲側的保持一致。 !建立tunnel介面。
#在本地網關裝置3上添加如下配置 interface Tunnel1 #建立隧道介面。 nameif ALIYUN1 ip address 169.254.12.2 255.255.255.252 #指定介面的IP地址。 tunnel source interface outside1 #指定隧道源地址為公網介面GigabitEthernet0/0。 tunnel destination 47.XX.XX.161 #指定隧道目的地址為阿里雲側IPsec串連3的公網IP地址。 tunnel mode ipsec ipv4 tunnel protection ipsec profile ALIYUN-PROFILE #指定隧道應用ipsec profile ALIYUN-PROFILE。 no shutdown #開啟隧道介面。 !配置路由。
#在本地網關裝置3上添加如下配置 route outside1 47.XX.XX.161 255.255.255.255 192.XX.XX.174 #配置訪問阿里雲側IPsec串連3公網IP地址的路由,下一跳為外網地址。 route private 192.168.0.0 255.255.255.0 192.168.50.214 #配置去往本機資料中心的路由。 route private 192.168.1.0 255.255.255.0 192.168.50.214 route private 192.168.2.0 255.255.255.0 192.168.50.214 router bgp 65530 address-family ipv4 unicast neighbor 169.254.12.1 remote-as 65531 #指定BGP鄰居,即阿里雲側IPsec串連3的BGP IP地址。 neighbor 169.254.12.1 ebgp-multihop 255 neighbor 169.254.12.1 activate #啟用BGP鄰居。 network 192.168.0.0 mask 255.255.255.0 #宣告本機資料中心的網段。 network 192.168.1.0 mask 255.255.255.0 network 192.168.2.0 mask 255.255.255.0 exit-address-family
完成上述配置後,本機資料中心和阿里雲之間可以成功建立IPsec-VPN串連,本機資料中心的路由將會通過BGP動態路由協議傳播至IPsec串連的BGP路由表中。
請根據您的實際網路環境按需在本機資料中心添加路由配置,使本機資料中心用戶端去往VPC的流量可以同時通過本地網關裝置1、本地網關裝置2和本地網關裝置3傳輸。具體命令,請諮詢相關裝置廠商。
步驟四:建立VPC串連
建立IPsec串連後,IPsec串連會自動綁定至轉寄路由器執行個體,您需要在雲企業網管理主控台建立VPC串連,將VPC執行個體也綁定至轉寄路由器執行個體上,用於實現本地IDC和VPC之間的相互連信。
登入雲企業網管理主控台。
在云企业网实例頁面,找到目標雲企業網執行個體,單擊目標執行個體ID。
在頁簽,找到華東2(上海)地區的轉寄路由器執行個體,在操作列單擊建立網路執行個體串連。
在串連網路執行個體頁面,根據以下資訊進行配置,然後單擊確定建立。
請根據以下資訊將華東2(上海)的VPC執行個體串連至轉寄路由器,其餘配置項保持預設狀態。更多資訊,請參見建立VPC串連。
配置項
配置項說明
VPC串連
執行個體類型
選擇網路執行個體類型。
本文選擇Virtual Private Cloud。
地區
選擇網路執行個體所屬的地區。
本文選擇華東2(上海)。
轉寄路由器
系統自動顯示當前地區已建立的轉寄路由器執行個體ID。
資源歸屬UID
選擇網路執行個體所屬的阿里雲帳號和當前登入的帳號是否為同一個帳號。
本文選擇同帳號。
付費方式
VPC串連的付費方式。預設值為隨用隨付。關於轉寄路由器的計費規則,請參見計費說明。
串連名稱
輸入VPC串連的名稱。
本文輸入VPC串連。
網路執行個體
選擇網路執行個體。
本文選擇華東2(上海)的VPC執行個體。
交換器
在轉寄路由器支援的可用性區域選擇交換器執行個體。
如果轉寄路由器在當前地區僅支援一個可用性區域,則您需要在當前可用性區域選擇一個交換器執行個體。
如果轉寄路由器在當前地區支援多個可用性區域,則您需要在至少2個可用性區域中各選擇一個交換器執行個體。在VPC和轉寄路由器流量互連的過程中,這2個交換器執行個體可以實現可用性區域層級的容災。
推薦您在每個可用性區域中都選擇一個交換器執行個體,以減少流量繞行,體驗更低傳輸時延以及更高效能。
請確保選擇的每個交換器執行個體下擁有一個閒置IP地址。如果VPC執行個體在轉寄路由器支援的可用性區域中並沒有交換器執行個體或者交換器執行個體下沒有閒置IP地址,您需要建立一個交換器執行個體。 具體操作,請參見建立和管理交換器。
本文在可用性區域F下選擇交換器1、在可用性區域G選擇交換器2。
進階配置
選擇是否開啟所有進階配置選項。系統預設選擇開啟所有進階配置選項。
保持預設配置,即開啟所有進階配置選項。
步驟五:建立跨地區串連
由於IPsec串連綁定的轉寄路由器執行個體和VPC執行個體綁定的轉寄路由器執行個體位於不同的地區,本地IDC和VPC執行個體之間預設無法通訊。您需要在華東1(杭州)和華東2(上海)地區的轉寄路由器執行個體之間建立跨地區串連,實現本地IDC和VPC執行個體之間的跨地區互連。
在雲企業網執行個體頁面,找到目標雲企業網執行個體,單擊雲企業網執行個體ID。
在頁簽,單擊設定跨地區頻寬。
在串連網路執行個體頁面,根據以下資訊配置跨地區串連,然後單擊確定建立。
請根據以下資訊建立跨地區串連,其餘配置項保持預設狀態。更多資訊,請參見建立跨地區串連。
配置項
說明
執行個體類型
選擇跨地區串連。
地區
選擇要互連的地區。
本文選擇華東1(杭州)。
轉寄路由器
系統自動顯示當前地區下轉寄路由器的執行個體ID。
串連名稱
輸入跨地區串連的名稱。
本文輸入跨地區串連。
對端地區
選擇要互連的對端地區。
本文選擇華東2(上海)。
轉寄路由器
系統自動顯示當前地區下轉寄路由器的執行個體ID。
頻寬分配方式
跨地區串連支援以下頻寬分配方式:
從頻寬包分配:從已經購買的頻寬包中分配頻寬。
按流量付費:按照跨地區串連實際使用的流量計費。
本文選擇按流量付費。
頻寬
輸入跨地區串連的頻寬值。單位:Mbps。
預設鏈路類型
使用預設鏈路類型。
進階配置
保持預設配置,即選中全部進階配置選項。
建立跨地區串連後,系統自動完成路由的分發和學習,IPsec串連會通過BGP動態路由協議將VPC執行個體的路由傳播至本機資料中心,同時也會將本機資料中心的路由傳播至轉寄路由器中,實現本地IDC和VPC執行個體間的網路互連。具體的路由資訊,請參見文末路由說明。
步驟六:驗證測試
建立跨地區串連後,本地IDC和VPC執行個體間已可以通過3條IPsec-VPN串連實現流量的負載分擔。以下內容介紹如何測試網路連通性以及如何驗證流量已通過3條IPsec-VPN串連實現負載分擔。
測試網路連通性。
登入VPC執行個體下的ECS執行個體。具體操作,請參見ECS遠端連線操作指南。
在ECS執行個體中執行ping命令,嘗試訪問本地IDC中的用戶端。
ping <本地IDC用戶端的IP地址>如果可以收到響應報文,則表示本地IDC和VPC執行個體之間的網路已連通,可以實現資源互訪。
驗證流量的負載分擔。
在本地IDC的多個用戶端中持續向ECS執行個體發送訪問請求,如果您可以分別在IPsec串連1、IPsec串連2、IPsec串連3的詳情頁面查看到流量監控資料,則證明本地IDC和VPC執行個體之間的流量已通過3條IPsec-VPN串連實現流量的負載分擔。
登入VPN網關管理主控台。
在頂部狀態列處,選擇IPsec串連所屬的地區。
在左側導覽列,選擇。
在IPsec串連頁面,找到目標IPsec串連,單擊IPsec串連ID。
進入IPsec串連詳情頁面在監控頁簽下查看流量監控資料。
路由說明
在本文中,建立IPsec串連、建立VPC串連、建立跨地區串連時均採用預設路由配置,預設路由配置下雲企業網會自動完成路由的分發和學習以實現本地IDC和VPC執行個體之間的相互連信。預設路由配置說明如下:
IPsec串連
在建立IPsec串連時直接綁定轉寄路由器執行個體,且啟用所有進階配置,系統會自動對IPsec串連進行以下路由配置:
IPsec串連預設被關聯至轉寄路由器執行個體的預設路由表,轉寄路由器執行個體將通過查詢預設路由錶轉發來自IPsec串連的流量。
您為IPsec串連添加的目的路由或者IPsec串連通過BGP動態路由協議學習到的雲下路由,均會被自動傳播至轉寄路由器執行個體的預設路由表。
轉寄路由器執行個體會將預設路由表下的其他路由條目自動傳播至IPsec串連的BGP路由表中。
IPsec串連會通過BGP動態路由協議將學習到的雲上路由自動傳播至本地IDC中。
VPC執行個體
建立VPC串連時如果開啟所有進階配置,則系統會自動對VPC執行個體進行以下路由配置:
自動關聯至轉寄路由器的預設路由表
開啟本功能後,VPC串連會自動關聯至轉寄路由器的預設路由表,轉寄路由器通過查詢預設路由錶轉發VPC執行個體的流量。
自動傳播系統路由至轉寄路由器的預設路由表
開啟本功能後,VPC執行個體會將自身的系統路由傳播至轉寄路由器的預設路由表中,用於網路執行個體的互連。
自動為VPC的所有路由表配置指向轉寄路由器的路由
開啟本功能後,系統將在VPC執行個體的所有路由表內自動設定10.0.0.0/8、172.16.0.0/12、192.168.0.0/16三條路由條目,其下一跳均指向VPC串連。
重要如果VPC的路由表中已經存在目標網段為10.0.0.0/8、172.16.0.0/12或192.168.0.0/16的路由條目,則系統無法再自動下發該路由條目,您需要在VPC路由表中手動添加指向VPC串連的路由條目以實現VPC和轉寄路由器之間的流量互連。
您可以單擊發起路由檢查查看網路執行個體內是否存在上述路由。
跨地區串連
建立跨地區串連時如果開啟所有進階配置,則系統會自動對跨地區串連進行以下路由配置:
自动关联至转发路由器的默认路由表
開啟本功能後,跨地區串連將與兩個地區的轉寄路由器的預設路由表建立關聯轉寄關係,兩個地區的轉寄路由器將會通過查詢預設路由錶轉發跨地區間的流量。
自动传播系统路由至转发路由器的默认路由表
開啟本功能後,跨地區串連將與兩個地區的轉寄路由器的預設路由表建立路由學習關係。
自动发布路由到对端地域
開啟本功能後,即允許跨地區串連將本端轉寄路由器路由表(指與跨地區串連建立關聯轉寄關係的路由表)下的路由自動傳播至對端轉寄路由器的路由表(指與跨地區串連建立路由學習關係的路由表)中,用於網路執行個體跨地區互連。
路由條目展示
以下內容為您展示本文中轉寄路由器執行個體、IPsec串連、VPC執行個體和本地網關裝置的路由條目資訊。您可以在阿里雲控制台查看對應執行個體的路由條目資訊:
查看轉寄路由器執行個體路由條目資訊,請參見查看企業版轉寄路由器路由條目。
查看VPC執行個體路由條目資訊,請參見建立和管理路由表。
查看IPsec串連的路由條目資訊,請進入IPsec串連詳情頁面:
登入VPN網關管理主控台。
在頂部狀態列處,選擇IPsec串連所屬的地區。
在左側導覽列,選擇。
在IPsec串連頁面,找到目標IPsec串連,單擊IPsec串連ID。
進入IPsec串連詳情頁面在BGP路由表頁簽下查看IPsec串連的路由條目資訊。