Security Center提供了惡意主機行為防禦、防勒索、網站後門串連防禦等安全能力,您可以通過設定相應的安全能力為您的伺服器開啟安全防護。本文介紹主機防護設定支援的功能及如何設定相應功能。
主動防禦
功能介紹
Security Center的主動防禦能力為您自動攔截常見病毒、惡意網路連接和網站後門串連,並設定誘餌捕獲勒索病毒。以下表格是各功能的詳細介紹。
功能 | 支援的版本 | 描述 |
惡意主機行為防禦 | 防病毒版、高级版、企業版、旗艦版 | 惡意主機行為防禦功能能夠自動攔截並查殺常見網路病毒,包括主流勒索病毒、DDoS木馬、挖礦和木馬程式、惡意程式、後門程式和蠕蟲等。 購買Security Center防病毒版及以上版本後,Security Center預設開啟惡意主機行為防禦功能,並將您所有伺服器添加到該功能的檢測範圍內。 說明 感染型病毒是一類進階惡意程式,由病毒本體將惡意代碼寫入正常程式檔案執行,因此往往有大量原本正常程式被感染後作為宿體被檢出。感染型病毒可能會危害系統進程,終止系統進程會造成系統穩定性風險。因此Security Center不會自動隔離感染型病毒,您需要手動處理此類病毒。 |
防勒索(诱饵捕获) | 防病毒版、高级版、企業版、旗艦版 | 防勒索(誘餌捕獲)提供了捕捉新型勒索病毒的誘餌,並通過病毒行為分析,自動啟動新型勒索病毒的防禦。 Security Center在您伺服器中設定的勒索捕獲誘餌檔案僅用於捕獲新型勒索病毒,不會對您的業務產生任何影響,請您放心使用該功能。您可以在頁面雲工作負載保護平台(CWPP)頁簽,將警示類型設定為精準防禦,查看Security Center為您查殺的防勒索病毒。 |
网站后门连接防御 | 企業版、旗艦版 | 開啟該功能後,Security Center會自動攔截駭客通過已知網站後門進行的異常串連行為,並隔離相關檔案。您可以在頁面雲工作負載保護平台(CWPP)頁簽查看相應警示和被隔離的檔案。更多資訊,請參見評估及處理安全警示和評估及處理安全警示。 說明 您購買了企業版或旗艦版後,Security Center預設為您開啟网站后门连接防御功能,並將您的所有伺服器添加到網站後門串連防禦的檢測範圍內。 |
恶意网络行为防御 | 高级版、企業版、旗艦版 | 開啟該功能後,Security Center將攔截您的伺服器和已披露的惡意訪問源之間的網路行為,為您的伺服器增強安全防護。 |
主动防御体验优化 | 企業版、旗艦版 | 開啟該功能後,如果伺服器異常關機或安全防禦能力缺失時,Security Center將採集伺服器Kdump資料進行安全防護分析,不斷提升Security Center的安全防禦能力。 |
如果您主动防御地區的所有功能都為關閉狀態,Security Center將以安全警示的形式向您展示在您伺服器上檢測出的病毒,您需要在控制台手動處理病毒相關警示。建議您開啟主动防御地區所有的功能,加固伺服器安全防線。處理安全警示的具體操作,請參見評估及處理安全警示。
開啟防禦能力
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
選擇頁簽,在主动防御地區開啟惡意主機行為防禦、防勒索(诱饵捕获)、网站后门连接防御和恶意网络行为防御開關。
開啟主动防御地區的所有開關後,Security Center將從惡意主機防禦行為、防勒索、防網站後門異常串連和防惡意源訪問等多方位為您的伺服器提供安全防護。
單擊主動防禦類型右側的管理,選擇攔截病毒或惡意行為生效的伺服器範圍,然後單擊確定。
開啟惡意主機行為防禦、防勒索(诱饵捕获)、网站后门连接防御和恶意网络行为防御服務後,Security Center將自動攔截病毒啟動並執行相關程式、進程等,同時阻斷異常串連。
(可選)選中主动防御体验优化複選框。
選中主动防御体验优化有助於Security Center擷取伺服器異常情況下安全防護資料,為您提升安全防護能力。建議選中該項。
後續步驟
在頁面雲工作負載保護平台(CWPP)頁簽容器主動防禦類型警示列表中,查看被主動防禦功能自動攔截的病毒。您需要將搜尋條件置為已處理,並且警示類型選擇精準防禦。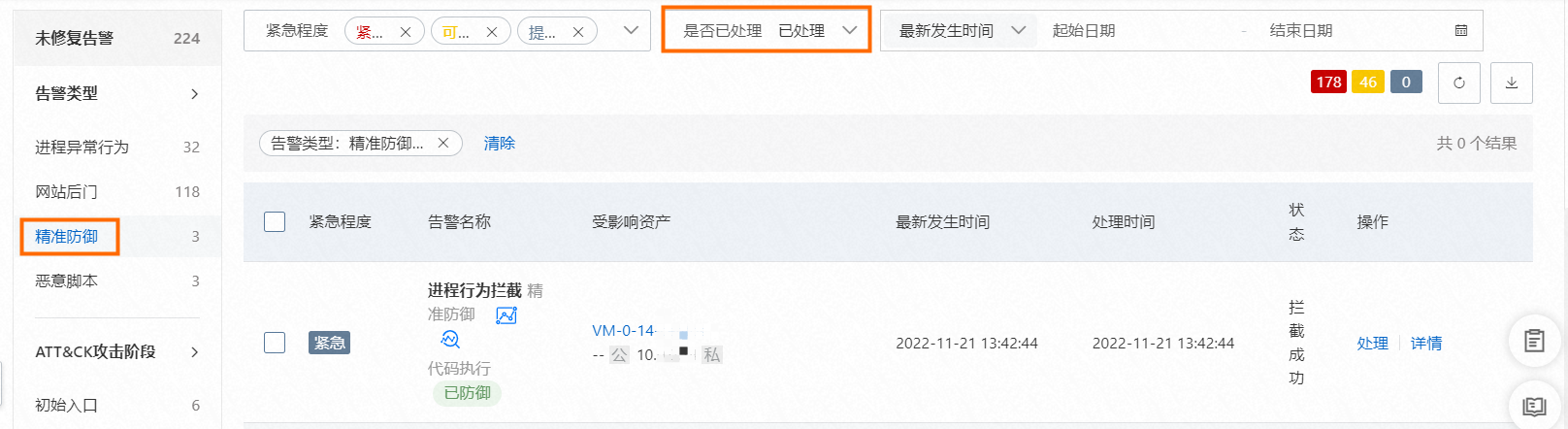
網站後門查殺
網站後門查殺功能使用自主查殺引擎檢測網站伺服器、網頁目錄中的網站後門及木馬程式,採用周期性靜態檢測和動態檢測相結合的檢測機制,並提供一鍵手動隔離功能。只有伺服器開啟網站後門查殺檢測後,Security Center用戶端才會執行網站後門檢測。以下是檢測和處理能力的說明:
每日執行Web目錄全量靜態掃描,Web目錄檔案變更時自動觸發動態掃描。
支援配置網站後門檢測的資產範圍置。
支援隔離、恢複和忽略發現的Webshell檔案。
免費版僅支援部分類型WebShell檢測,Security Center其他付費版本支援所有類型的WebShell檢測。如需較全面的WebShell檢測,建議您升級到防病毒版、高级版、企業版或旗艦版。升級的具體操作,請參見升級與降配。
配置網站後門查殺檢測開關
Security Center預設為所有已安裝Security Center用戶端的伺服器開啟網站後門查殺檢測。建議您為所有對外提供Web服務的伺服器開啟網站後門查殺檢測。如果您的伺服器處於完全封閉的內網,您可以參考下述步驟為對應伺服器關閉網站後門查殺。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
選擇頁簽,在網殼檢測地區單擊管理。
在佈建服務器以進行網殼檢測面板,取消選中需關閉網站後門查殺的伺服器,並單擊確定。
處理網站後門查殺警示
為伺服器開啟網站後門查殺後,當Security Center檢測到您的伺服器中存在後門Webshell檔案等安全威脅時,會在頁面無代理檢測頁簽為您展示相應警示。您可以前往雲工作負載保護平台(CWPP)頁簽查看並處理警示類型為網路外殼的警示。未處理的網站後門警示可能會對您的資產安全造成嚴重威脅,建議您及時處理此類警示。
不支援Security Center免費版使用者一鍵處理網站後門警示,防病毒版及以上版本使用者可在控制台一鍵隔離檢測出問題的Webshell檔案。具體操作,請參見評估及處理安全警示。
自適應威脅檢測能力
自適應威脅檢測能力預設為關閉狀態,您需要手動開啟該功能。開啟該功能後,如果Security Center在您的伺服器中檢測到高危風險(即高危警示),會自動為您的伺服器用戶端開啟期限為7天的嚴格警示模式。嚴格警示模式開啟所有安全防護規則和安全引擎,會對任何可疑的入侵行為和潛在的威脅進行警示,可以更全面地檢測駭客的入侵行為。
Security Center自動為您的伺服器開啟了期限為7天的嚴格警示模式,如果您在這7天中,手動設定了該伺服器的防護模式,7天到期後Security Center將不會自動為該伺服器關閉嚴格警示模式,該伺服器會一直保持您手動設定的防護模式。
版本限制
版本限制
開啟自適應威脅檢測能力
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
選擇頁簽,在自适应威胁检测能力地區開啟容器主動防禦開關。
說明如果您之前未授權Security Center訪問您的雲資源,您需要先根據頁面提示完成授權操作。該操作是授權Security Center訪問您的雲資源。授權成功後,存取控制服務會自動建立服務關聯Security Center服務關聯角色授權,Security Center使用此角色訪問您其他產品中的雲資源,為其他雲資源提供安全防護。更多資訊,請參見Security Center服務關聯角色。
警示設定
Security Center針對伺服器警示提供了不同的警示模式,可以滿足您不同應用情境下的安全需求。Security Center預設為所有已接入的伺服器開啟均衡模式,該模式下,經過阿里雲專家的綜合測試情況,會在保障較少誤判的情況下檢測出更多可疑風險。
修改警示模式
如果您需要對伺服器進行更嚴格檢測,您可以將伺服器警示模式修改為strict 模式。
在strict 模式下,阿里雲會檢測出更多的可疑行為警示,但會存在一定的誤判風險,建議在重保期間謹慎使用。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
選擇頁簽,在警示設定地區單擊strict 模式右側的管理。
選擇需要加入strict 模式的伺服器,然後單擊確定。