您可以將線下安全廠商的日誌(例如長亭WAF、飛塔防火牆)接入威脅分析與響應CTDR(Cloud Threat Detection and Response)中,在Security Center進行風險的統一管理,從而提高風險的可見度和響應效率。本文介紹如何將安全廠商日誌接入CTDR。
方案概覽
將安全廠商日誌接入威脅分析與響應,只需4步:
建立CTDR專屬Logstore:在Security Center控制台為指定日誌類型建立專屬Logstore,該Logstore用於儲存待接入CTDR的日誌資料。
將安全廠商日誌採集至專屬Logstore:將安全廠商的日誌採集至Log Service中的CTDR專屬Logstore。如果原始日誌都在一個欄位中,需在日誌分析控制台使用資料擷取處理外掛程式,將原始日誌進一步解析為結構化資料,即拆分為索引值對儲存到專屬Logstore中。
配置解析規則:定義專屬Logstore中儲存的安全廠商日誌到CTDR日誌標準欄位的映射關係,即標準化需要接入CTDR的日誌。
配置資料來源綁定解析規則:在Security Center控制台配置資料來源將專屬Logstore與解析規則綁定,完成日誌接入CTDR。
支援接入的安全廠商
廠商名稱 | 支援的日誌類型 |
飛塔防火牆 |
|
長亭WAF |
|
微軟Active Directory | 微軟AD日誌 |
F5 BIG-IP本地流量管理員(LTM) | F5 BIG-IP LTM警示日誌 |
其他 |
|
如果您需要接入的安全廠商未在上述列表中,您可以先將日誌接入其他廠商。如需諮詢日誌採集、解析規則配置等資訊,您可以提交工單聯絡Security Center技術支援人員。
計費說明
將安全廠商日誌接入Security Center會涉及以下三部分的費用說明如下:
費用專案 | 費用承擔者 | 說明 | |
CTDR日誌接入流量 | 已購買CTDR的阿里雲賬戶 | 根據從CTDR專屬Logstore接入到CTDR的日誌流量大小,按天計費。 | |
CTDR日誌儲存容量 | 已購買CTDR的阿里雲賬戶 | 根據投遞到CTDR日誌管理功能中的標準化日誌儲存容量收取費用。 | |
CTDR專屬Logstore |
| 阿里雲Security Center |
|
| 已購買CTDR的阿里雲賬戶 |
| |
前提條件
已購買威脅分析與響應服務的日誌接入流量並開通該服務。具體操作,請參見什麼是威脅分析與響應。
1. 建立CTDR專屬Logstore
執行下述步驟自動建立CTDR專屬Logstore,該Logstore用於接收和臨時儲存安全廠商日誌。
登入Security Center控制台。在控制台左上方,選擇需防護資產所在的地區:中國或全球(不含中國)。
在左側導覽列,選擇。
在產品接入頁面,找到需要接入的安全產品,單擊操作列的接入設定。
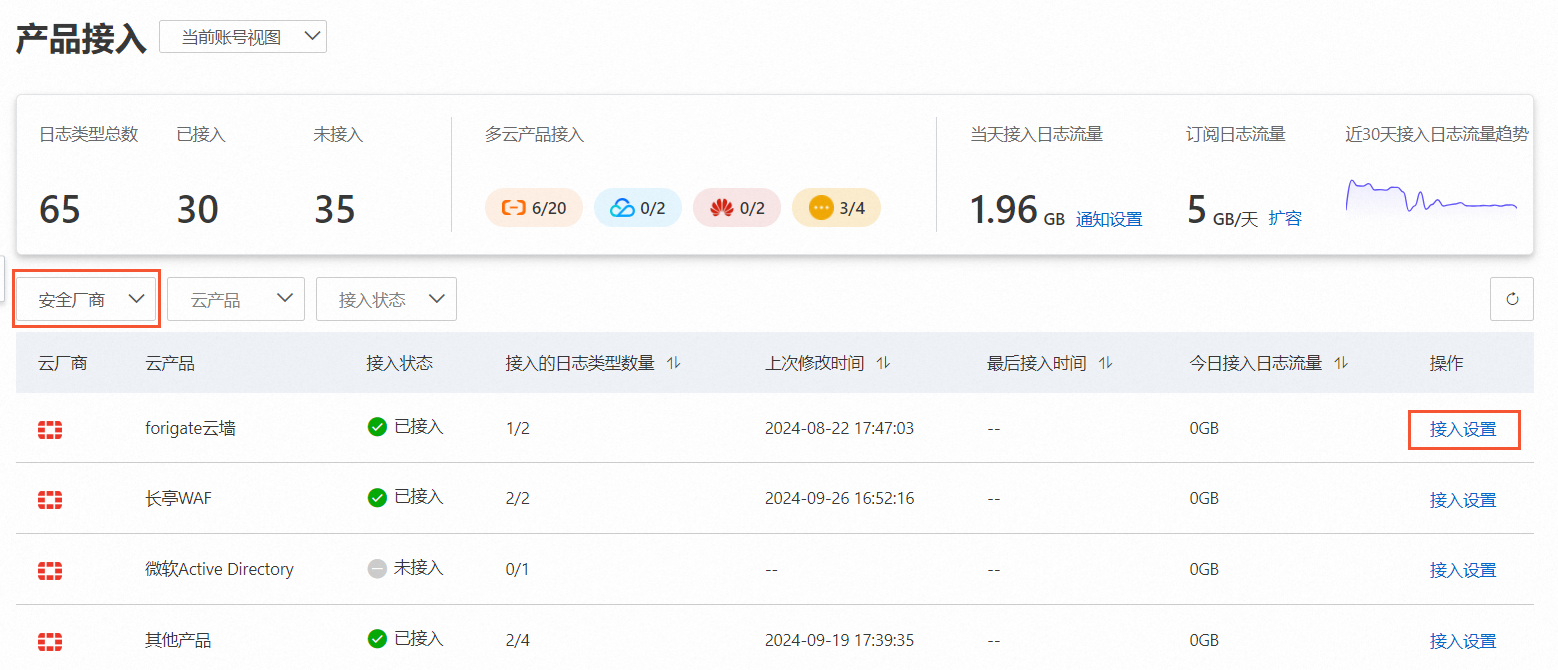
在雲產品接入設定面板,找到需要接入的日誌類型,單擊已接入帳號列下的數字。
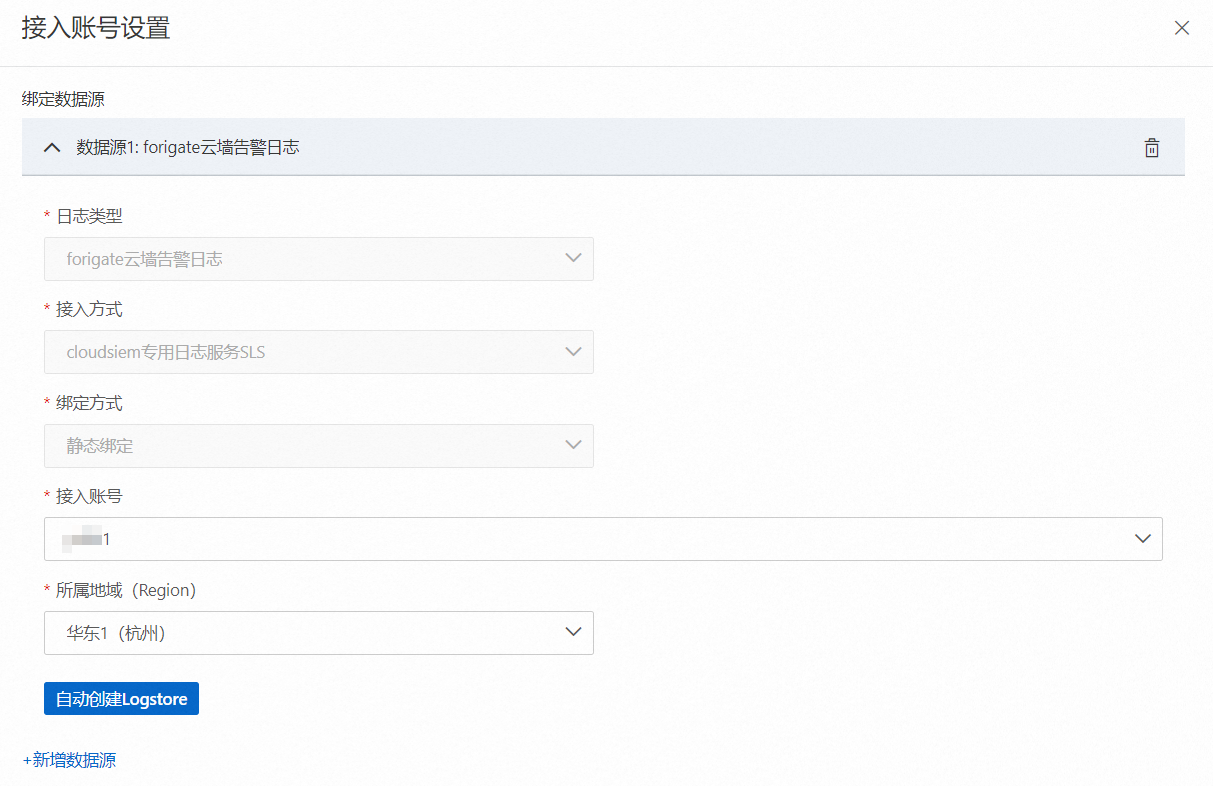
在接入帳號設定面板,選擇接入帳號和所屬地區(Region),並單擊自動建立logstore。
 說明
說明執行該步驟完成自動建立Logstore即可,以獲得CTDR專屬Logstore的專案和日誌庫名稱,為安全廠商日誌採集到阿里雲上做準備。
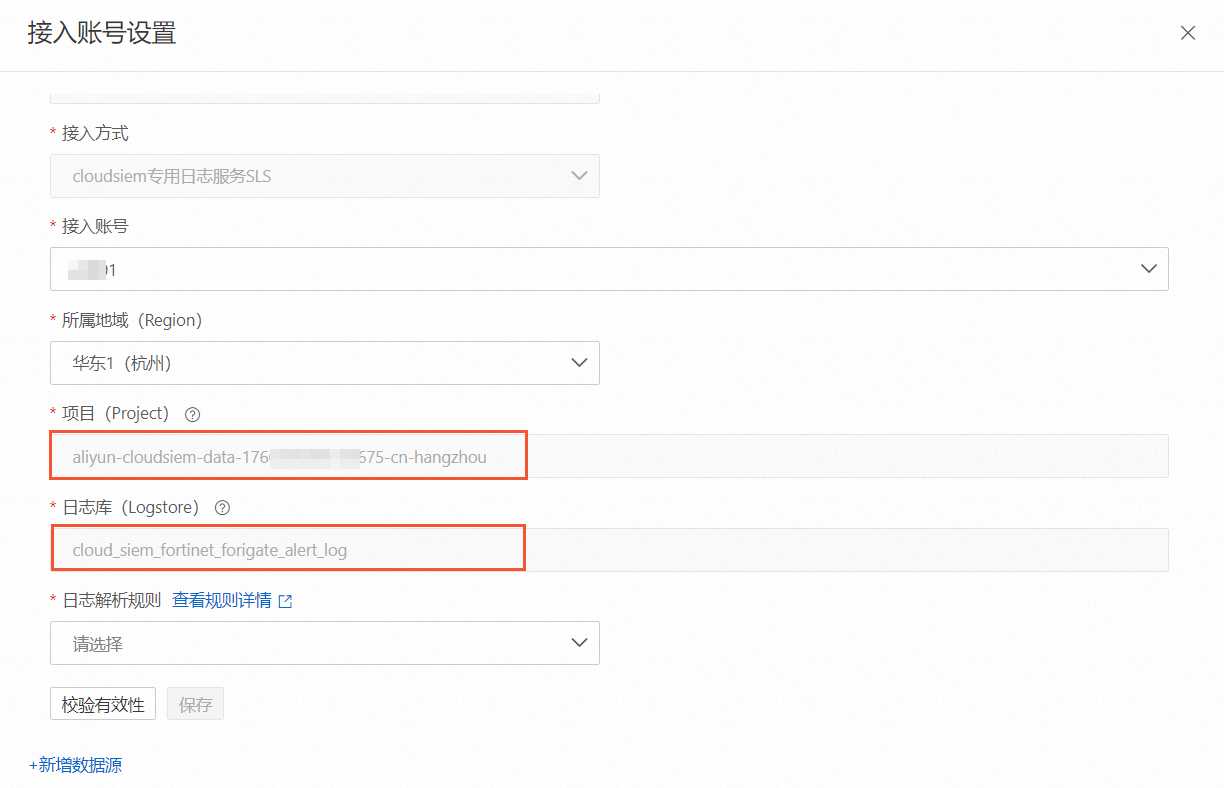
記錄接入帳號設定面板中顯示的專案(Project)和日誌庫(Logstore)名稱。
2. 採集日誌至專屬LogStore
在此步驟中,您需要將安全廠商的原始日誌樣本,通過SLS提供的資料擷取方式,解析成索引值對形式,儲存到CTDR專屬Logstore中,才能在CTDR控制台進行下一步的日誌解析規則映射,即對日誌進行標準化處理。
如果將日誌採集到專屬LogStore的過程中有任何問題,您可提交工單聯絡技術支援人員,提交工單時產品分類需選擇為Log Service。
選擇採集方式
Log Service支援採集伺服器與應用、開源軟體、物聯網、移動端、標準協議、阿里雲產品等多種來源的資料。您可以使用Logtail採集或其他採集方式(Kafka協議、Syslog協議)將日誌上傳到自動建立的Logstore中。關於採集方式的更多資訊,請參見資料擷取概述。
如果您選擇了Logtail採集的方式,在執行下述操作前,您需要先選擇網路類型。更多資訊,請參見Logtail網路類型,啟動參數與設定檔。
配置Logtail採集
該步驟以長亭WAF為例介紹具體的操作步驟,其他線下安全產品如飛塔防火牆可參考附錄中的說明。
需要接入長亭WAF日誌時,由於無法在部署長亭WAF的伺服器中安裝Logtail,您需要使用代理服務器完成日誌採集。
準備一台代理服務器,先將長亭WAF的日誌通過長亭內建的syslog發信功能轉寄到代理服務器。
在代理服務器中安裝Logtail。具體操作,請參見安裝Logtail(Linux系統)、安裝Logtail(Windows系統)。
如實際情況允許,您也可以直接在安全廠商日誌儲存的伺服器上安裝Logtail。
為已安裝Logtail的伺服器配置使用者標識,授權您的阿里雲帳號通過Logtail採集伺服器日誌。具體操作,請參見配置使用者標識。
在自動建立的日誌庫(Logstore)中建立機器組。
如何建立IP地址類型的機器組,請參見建立IP地址機器組。
如何建立使用者自訂標識類型的機器組,請參見建立使用者自訂標識機器組。
完成資料接入配置。
在快速接入資料地區,單擊接入資料,並在接入資料對話方塊中選擇Syslog-外掛程式。
在選擇日誌空間嚮導頁,選擇步驟6中記錄的專案Project和日誌庫Logstore,單擊下一步。
在建立機器組嚮導頁,單擊使用現有機器組。
在機器組配置嚮導頁,選擇使用情境、安裝環境和已建立的機器組,單擊下一步。
在資料來源設定嚮導頁,參考下述樣本設定外掛程式配置,並單擊下一步。
重要配置時,需去掉下面樣本中的注釋。
下述樣本中的Logtail處理外掛程式可將長亭WAF日誌中_content_的JSON欄位內容展開成索引值對形式,以便CTDR可以解析對應欄位。您也可以按需調整Logtail處理外掛程式以滿足將日誌解析為索引值對格式的需求。更多資訊,請參見擴充外掛程式:展開JSON欄位、處理外掛程式概述。
{ "inputs": [{ "type": "service_syslog", "detail": { "Address": "udp://0.0.0.0:9001", #如果一台伺服器轉寄多種日誌類型,需根據不同日誌類型,調整連接埠 "ParseProtocol": "rfc3164" } }], "processors": [{ "detail": { "ExpandArray": false, "ExpandConnector": ".", #按需配置 "ExpandDepth": 0, "IgnoreFirstConnector": true, "KeepSource": false, #是否保留原欄位, 按需 "KeepSourceIfParseError": true, "NoKeyError": true, "Prefix": "", #按需配置 "SourceKey": "_content_", #需要Json展開的欄位名 "UseSourceKeyAsPrefix": false # 按需配置 }, "type": "processor_json" }] }預覽資料及建立索引,單擊下一步。
在Log Service控制台查看日誌是否已正常接入自動建立的Logstore中。
其他採集方式
除了使用Logtail採集外,您還可以通過Kafka協議、Syslog協議上傳日誌到CTDR專屬Logstore中。具體操作如下:
3. 配置日誌解析規則
登入Security Center控制台。在控制台左上方,選擇需防護資產所在的地區:中國或全球(不含中國)。
在左側導覽列,選擇。
在產品接入頁面,將滑鼠移動至
 表徵圖處,單擊安全廠商下方的日誌解析規則。
表徵圖處,單擊安全廠商下方的日誌解析規則。
在日誌解析規則頁面,單擊新增規則。
在新增日誌解析規則頁面,按照介面導航完成規則設定。
配置類別
配置項
說明
基本資料設定
规则名称
設定日誌解析規則的名稱。
活動分類
選擇需接入日誌的類別。常見日誌類型的對應關係如下:
防火牆警示日誌:安全日誌 > 防火牆警示日誌。
防火牆流日誌:部落格 > 五元組日誌。
WAF警示日誌:安全日誌 > Web Application Firewall警示日誌。
WAF流日誌:部落格 > HTTP日誌。
備忘
設定日誌解析規則的備忘資訊。
日誌樣本查看
地區(RegionId)
選擇自動建立的Logstore所在地區。
项目(Project)
輸入自動建立的Logstore所在Project。
日誌庫(Logstore)
輸入自動建立的Logstore的名稱。
載入樣本
您可以單擊載入樣本,將已採集到的安全廠商日誌欄位,載入到規則配置列表中。載入後,您無需手動填寫欄位做映射,可以直接選擇已匯入的日誌欄位做映射。您也可以單擊查看更多日誌樣本,前往Log Service控制台查看已接入的安全廠商日誌欄位的詳細資料。
日誌解析映射設定
配置解析規則
您需要在此地區,配置日誌解析映射規則,將已採集到的日誌欄位對應到CTDR的標準欄位中。不支援修改目標標准欄位的欄位為您必須要配置的欄位,其餘欄位您可以按需選擇是否配置。
4. 綁定資料來源
在產品接入頁面,找到需要接入的安全產品,單擊操作列的接入設定。

在雲產品接入設定面板,找到需要接入的日誌類型,單擊已接入帳號列下的數字。
在接入帳號設定面板,選擇接入帳號和所屬地區(Region),並單擊自動建立logstore。
 說明
說明如果所選地區下,已建立過該日誌類型對應的Logstore,即使您執行了自動建立Logstore,也不會重複建立。
選擇3. 配置日誌解析規則中建立的日誌解析規則,並單擊校正有效性,然後單擊儲存。
後續步驟
配置自訂檢測規則,以深入檢測並分析安全廠商的日誌。具體操作,請參見新增自訂規則。
說明暫不支援安全廠商日誌使用預定義規則。
如需查看CTDR標準化後的日誌資料,您可以使用日誌管理功能。使用日誌管理功能查看對應日誌前,您需要購買日誌儲存容量並開通對應日誌的投遞。具體操作,請參見步驟一:開啟投遞。
附錄
CTDR專屬Logstore說明
執行完1. 建立CTDR專屬Logstore後,Security Center會自動在Log Service建立CTDR專屬Project和Logstore,該Logstore用於儲存安全廠商日誌,不建議作為其他用途使用。您受限使用CTDR專屬Logstore中的資料,不具備修改該Logstore內資料或在其中建立索引的許可權。您可以在Logstore中執行消費、加工、投遞日誌等操作。
一個地區下只會建立一個Project,即使您重新執行自動建立操作,僅有第一次操作會自動建立對應的Project和Logstore。
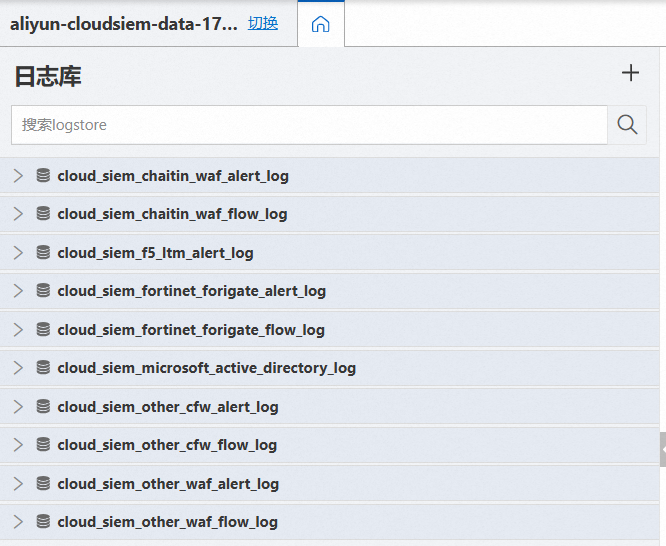
在杭州地區下建立的Project的名稱為aliyun-cloudsiem-data-阿里雲帳號ID-cn-hangzhou。根據您接入的日誌類型不同,Security Center會建立不同的Logstore。日誌庫的名稱和具體用途說明如下。在Log Service控制台進行接入配置時,您需要在安全廠商對應的日誌庫下操作。
日誌庫名稱 | 用途說明 |
cloud_siem_chaitin_waf_alert_log | 採集長亭WAF警示日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_chaitin_waf_flow_log | 採集長亭WAF流日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_f5_ltm_alert_log | 採集F5 BIG-IP LTM警示日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_fortinet_forigate_alert_log | 採集飛塔防火牆警示日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_fortinet_forigate_flow_log | 採集飛塔防火牆流日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_microsoft_active_directory_log | 採集微軟Active Directory日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_other_cfw_alert_log | 採集其他廠商的防火牆警示日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_other_cfw_flow_log | 採集其他廠商的防火牆流日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_other_waf_alert_log | 採集其他廠商的WAF警示日誌,採集解析為索引值對進行結構化日誌儲存。 |
cloud_siem_other_waf_flow_log | 採集其他廠商的WAF流日誌,採集解析為索引值對進行結構化日誌儲存。 |
飛塔防火牆日誌採集處置外掛程式樣本
採集飛塔防火牆日誌到CTDR專屬Logstore時,可以使用Logtail採集的方法(和長亭WAF日誌類似)。對應的Logtail外掛程式配置樣本如下:
下述樣本中的Logtail處理外掛程式可將飛塔防火牆日誌中_content_的欄位內容展開成索引值對形式,以便CTDR解析對應欄位。您也可以按需調整Logtail處理外掛程式以滿足將日誌解析為索引值對格式的需求。更多資訊,請參見擴充外掛程式:提取欄位、處理外掛程式概述。
{
"inputs": [
{
"type": "service_syslog",
"detail": {
"Address": "udp://0.0.0.0:9002",
"ParseProtocol": "rfc5424"
}
}
],
"processors": [
{
"detail": {
"Delimiter": " ",
"Separator": "=",
"KeepSource": true,
"SourceKey": "_content_",
"UseSourceKeyAsPrefix": false
},
"type": "processor_split_key_value"
}
]
}通過一台伺服器採集多個安全廠商的日誌
如需將多個安全廠商的日誌接入CTDR,您可以通過將多個日誌源的日誌發送到指定伺服器的IP地址和不同連接埠,在該伺服器上安裝Logtail,並在Log Service控制台不同的Logstore下進行不同的資料來源設定,實現將不同類型的日誌採集到CTDR專屬Logstore中。
例如,需要將長亭WAF警示日誌、飛塔防火牆警示日誌接入CTDR,您可以通過rsyslog等syslog agent將日誌的syslog資料轉寄到指定伺服器IP地址和連接埠上。例如長亭WAF警示日誌發送到指定伺服器的9001連接埠,飛塔防火牆警示日誌發送到指定伺服器的9003連接埠。在指定伺服器上安裝Logtail後,在Log Service控制台對應的Logstore中完成Logtail配置:
長亭WAF警示日誌:在名稱為cloud_siem_chaitin_waf_alert_log的Logstore中,外掛程式配置inputs部分如下:
{ "inputs": [ { "type": "service_syslog", "detail": { "Address": "udp://0.0.0.0:9001", "ParseProtocol": "rfc3164" } } ] }飛塔防火牆警示日誌:在名稱為cloud_siem_fortinet_forigate_alert_log的Logstore中,外掛程式配置inputs部分如下:
{ "inputs": [ { "type": "service_syslog", "detail": { "Address": "udp://0.0.0.0:9003", "ParseProtocol": "rfc3164" } } ] }
日誌採集說明
除了本文介紹的Logtail採集方法外,您也可以根據實際情況選擇其他採集方法,將安全日誌採集到Log Service中。更多資訊,請參見資料擷取概述。
使用Logtail機器組採集時機器組無心跳的處理方法,請參見Logtail機器組問題排查思路(主機情境)。