This topic describes the cause of the cross-site request forgery (CSRF) vulnerability in Redis and the security policies of Tair (Redis OSS-compatible).
CSRF introduction
CSRF (or XSRF), also known as One Click Attack or Session Riding, refers to a malicious exploitation of websites.
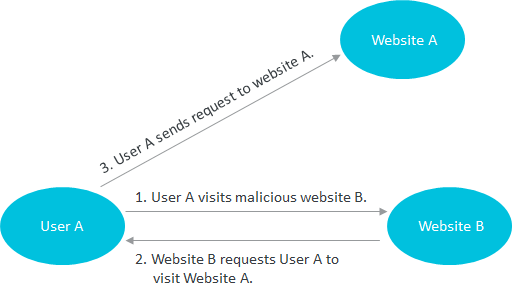
The preceding figure shows a simplified model of a CSRF attack. A user visits malicious website B (Website B), and malicious website A (Website A) replies to the user with an HTTP message that requires the user to visit Website B. If the user maintained a trust relationship with Website B, the system assumes that the user personally sent the request to visit Website B and processes the request.
Redis CSRF attack model
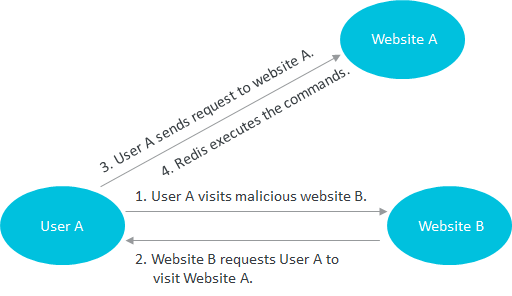
Based on the preceding principle of CSRF, a malicious website can require a user to send an HTTP request to Redis. Due to the support for a text-based protocol, Redis does not automatically disconnect after encountering malformed protocol data during protocol parsing. In this case, an attacker can append Redis commands to a normal HTTP request to allow the commands to be run on the Redis server. If no password authentication is configured between the user and Redis, the Redis commands can be directly run. Attackers can exploit this vulnerability to encrypt the data stored in Redis and then demand a ransom for decryption. This attack method is similar to previous ransomware attacks that targeted MongoDB databases.
Kernel fixes
Redis 3.2.7 provides a solution to this issue, which is to log statements that contain the POST and Host: keywords and then close the connection to prevent Redis from running subsequent legitimate commands.
Redis security risks
Earlier versions of Redis are exposed to a security vulnerability that allows hackers to obtain the root privileges of the Redis service when specific conditions are met. The main reason for this security vulnerability is that users do not have sufficient knowledge about the security mechanism of Redis and are inexperienced in Redis operations and maintenance. In addition, Redis does not provide robust security protection mechanisms. Tair (Redis OSS-compatible) provides a more secure service. We recommend that you use Tair (Redis OSS-compatible) as the Redis service in the cloud.
Security policies of Tair (Redis OSS-compatible)
Connections over an internal network instead of the Internet
Tair (Redis OSS-compatible) provides trusted internal access. If you do not apply for a public endpoint, you cannot directly access Tair instances from the Internet.
Physical network isolation
The network in which Tair (Redis OSS-compatible) instances are deployed is physically isolated from the network from which you want to access the instances. You cannot directly access the network of backend servers.
VPC for network isolation
If you are an Alibaba Cloud user and deploy a virtual private cloud (VPC) to connect your services, only the services in the same VPC can access each other.
Whitelists
Tair (Redis OSS-compatible) allows you to configure whitelists. You can configure a whitelist of IP addresses that can be used to access a Tair instance in the console.
Password authentication
Tair (Redis OSS-compatible) requires password authentication for instances deployed in the classic network. You can configure a complex password to prevent password cracking.
Permission isolation
Tair (Redis OSS-compatible) isolates permissions and accessible directories for each backend instance. The instances can access resources only by using their own paths to the resources to avoid mutual interference.
Disabling of high-risk commands
Tair (Redis OSS-compatible) disables specific high-risk system management commands such as config and save. To modify parameters, you must perform two-factor authentication in the console. This avoids direct operations on backend configuration files and management commands.
Security monitoring
Tair (Redis OSS-compatible) features comprehensive security monitoring for physical machines, regular scans, and updates to security monitoring policies to detect security risks at the earliest opportunity.
Password authentication for cluster instances
Native Redis 3.0 clusters do not support password authentication. Tair (Redis OSS-compatible) cluster instances support password authentication for enhanced security.