當業務應用中需要使用帳號口令、存取金鑰等憑據資訊時,您可以使用KMS的憑據管理功能,將憑據資訊儲存在KMS的憑據中,業務應用通過整合阿里雲SDK、KMS執行個體SDK或憑據SDK向KMS動態擷取憑據資訊,以避免明文儲存憑據資訊導致的資訊泄露或系統被惡意操作風險。本文介紹憑據的應用情境、組成、輪轉等基本資料。
為什麼使用憑據管理
資料庫帳號口令、伺服器帳號口令、SSH Key、存取金鑰等憑據的泄露,是當今資料安全面臨的主要威脅之一。為了降低資料泄露的安全風險,執行有效憑據保護和周期性輪轉非常關鍵。使用KMS的憑據管理功能可以為您帶來以下安全優勢:
KMS對憑據值使用高安全強度的密碼編譯演算法加密儲存,防止憑據寫入程式碼帶來的憑據泄露以及高價值資產泄露,提升資料安全性。
提供安全便捷的用戶端接入方式,應用程式以無代碼或者低代碼的方式,動態使用憑據。
具備應急處置能力,當您通過立即輪轉的方式更新憑據時,應用程式和業務不受影響。
說明僅對RAM憑據、資料庫憑據(雙帳號託管)、ECS憑據,並通過憑據SDK整合時有效。
支援高頻次輪轉的全動態憑據,縮小憑據的有效時間視窗,降低憑據被破解的風險。
支援通過API、阿里雲ROS或Terraform等營運編排工具,滿足中心化、規模化的安全管理需求。
應用情境
以託管您自建資料庫的使用者名稱和口令為例,為您介紹基本的憑據託管和使用情境。
如果您使用的是RDS資料庫,更推薦您使用RDS憑據,具體請參考RDS憑據。
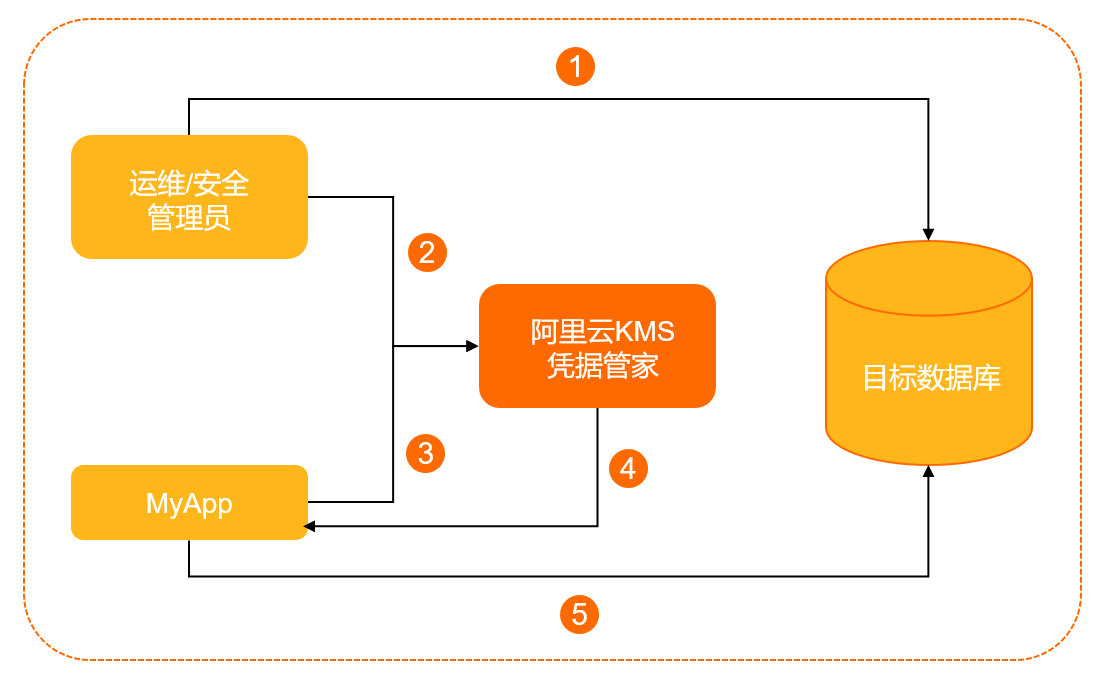
安全性系統管理員在目標資料庫配置MyApp訪問資料庫所需的使用者名稱和口令。
安全性系統管理員在KMS建立一個通用憑據,憑據名為“MyDbCreds”,用來託管上述使用者名稱和口令。
當MyApp需要訪問資料庫時,通過憑據用戶端SDK向KMS請求憑據MyDbCreds。
KMS讀取到儲存的憑據密文,解密後將明文通過HTTPS返回給MyApp。
MyApp讀取並解析KMS返回的憑據明文,擷取到使用者名稱和口令,使用該帳號可以訪問目標資料庫。
對應用MyApp而言,通過調用KMS的API來擷取訪問資料庫的使用者名稱和口令,避免了在程式中寫入程式碼憑據帶來的資訊泄露風險。寫入程式碼憑據和使用KMS的應用程式之間的差異,如下圖所示。
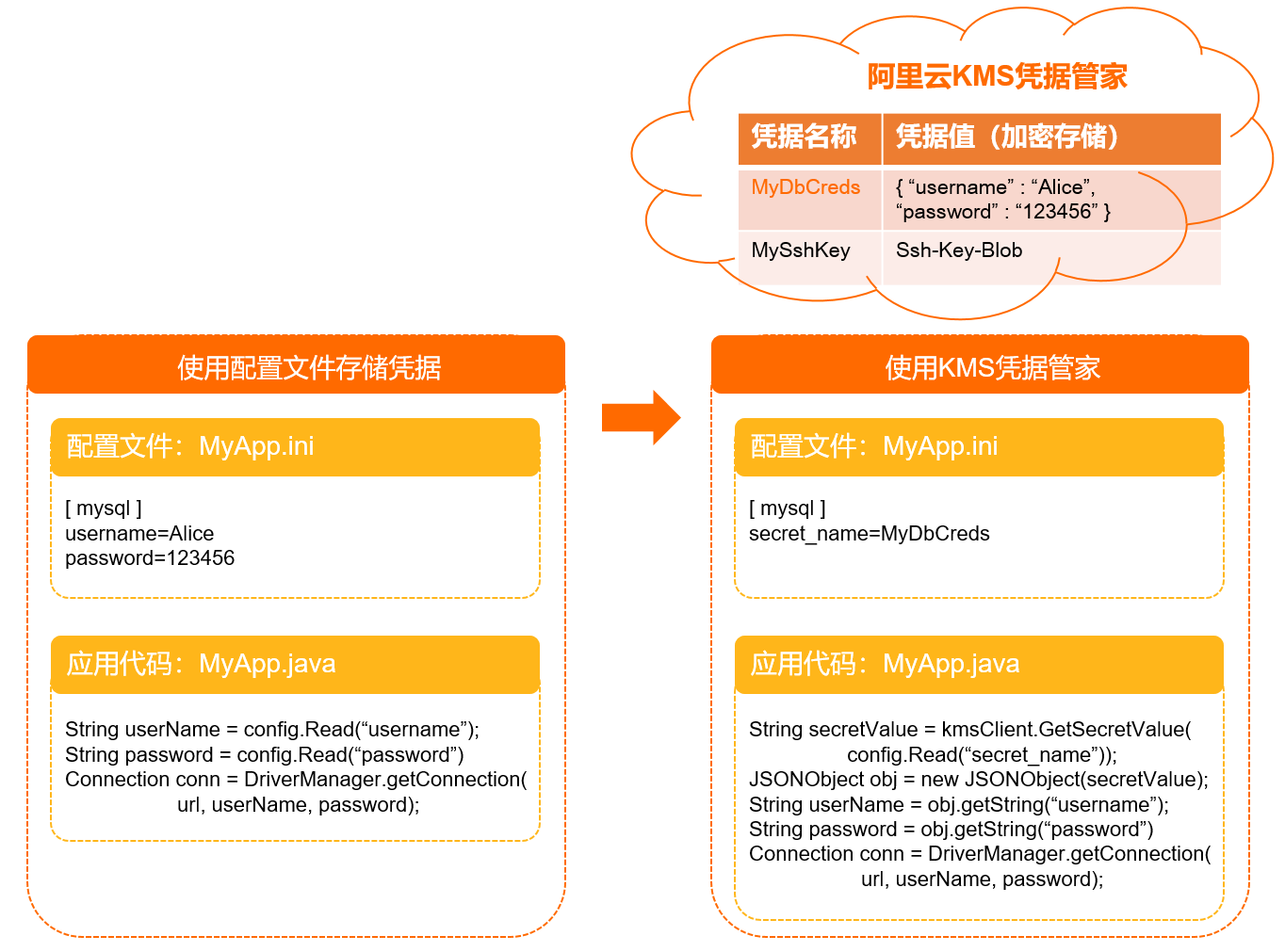
憑據的組成
憑據由中繼資料、一或多個憑據版本組成。您可以登入Key Management Service控制台,在凭据管理頁面查看憑據詳情。
中繼資料
包含憑據名稱、ARN、建立時間、憑據類型、加密金鑰、標籤等資訊。
重要加密金鑰僅用於加密憑據值,不加密憑據的中繼資料資訊。密鑰和憑據需要屬於同一個KMS執行個體,且密鑰必須為對稱金鑰。
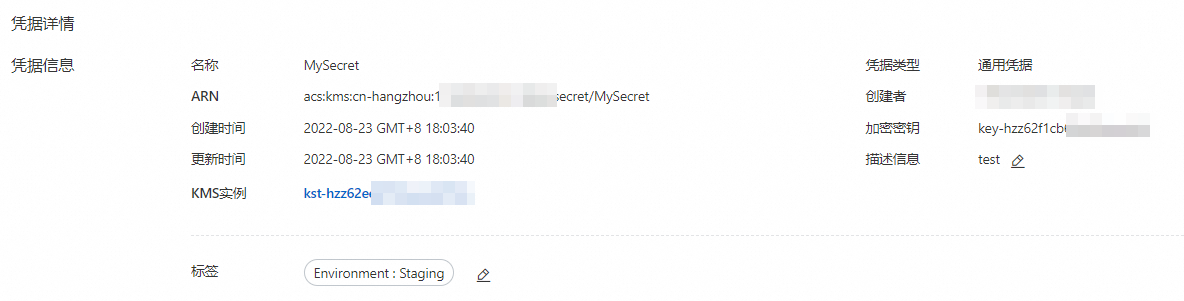
憑據版本
一個憑據可以有多個憑據版本。每個憑據版本包含版本號碼、版本狀態、憑據值。
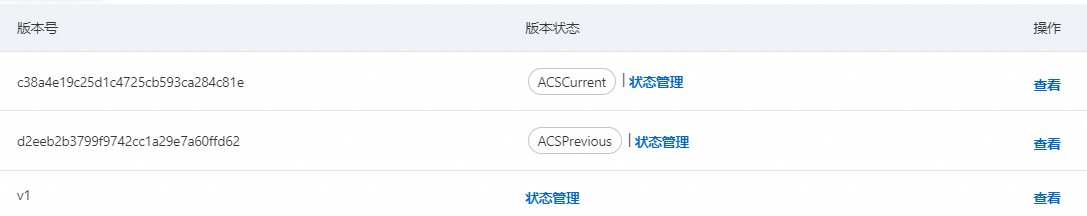
版本號碼:只能在存入憑據值時被寫入,在憑據內唯一且不支援修改。一個版本號碼可以關聯多個版本狀態,但每個版本狀態只能關聯一個版本號碼。
版本狀態:在憑據內唯一,包含內建版本狀態、自訂版本狀態。
內建版本狀態:
ACSCurrent:憑據的目前的版本,即最新存入的憑據值的狀態。
ACSPrevious:憑據的上一個版本。
ACSPending:待處理版本,輪轉過程中會產生該版本,輪轉完成後不會出現該狀態。
說明通過介面擷取憑據值時讀取ACSCurrent對應的憑據值。
內建版本狀態類似指標。例如,第一次存入一個憑據版本,版本號碼設定為v1,存入後內建版本狀態為ACSCurrent,此時繼續存入一個憑據版本,版本號碼設定為v2,則v2對應的內建版本狀態為ACSCurrent,v1對應的版本狀態會自動改為ACSPrevious。
自訂版本狀態:每個憑據版本可以自訂多個版本狀態。
重要僅通用憑據支援自訂版本狀態,其自訂版本狀態數量與內建版本狀態的總和不能超過8個。
憑據值:您存入的憑據資訊,可以是字串或二進位值。
說明當憑據的版本數超過上限時,最早的可回收版本(沒有關聯版本狀態的版本)會被刪除。
憑據輪轉
憑據輪轉即基於憑據支援多個版本的特徵,通過存入新的憑據版本來更新憑據,以提升憑據的安全性。新存入的憑據版本其狀態會設定為ACSCurrent,業務應用會動態讀取ACSCurrent對應的憑據值。
輪轉過程
輪轉方式
周期性自動輪轉:設定輪轉周期後,您無需關注輪轉的過程以及時間,到期後KMS自動完成輪轉。RAM憑據、資料庫憑據、ECS憑據支援您在KMS配置輪轉周期,通用憑據不支援在KMS配置輪轉周期,但您可以通過Function Compute編碼的方式設定輪轉周期。
立即輪轉:當您的憑據泄露時,可以通過立即輪轉進行應急處理。RAM憑據、資料庫憑據、ECS憑據,支援立即輪轉,通用憑據僅支援通過手動存入憑據值進行立即輪轉。
支援的憑據類型
KMS支援四種憑據類型:通用憑據、RAM憑據、資料庫憑據、ECS憑據,不同類型憑據的詳細說明見下表。
RAM憑據、資料庫憑據和ECS憑據為全託管式的憑據管理員模式。您在KMS託管這三類憑據後,您應僅在KMS對憑據進行輪轉,不能在對應產品中對憑據進行狀態、刪除等操作,否則KMS將無法對憑據進行輪轉,您應用程式從KMS擷取的憑據也無法正常使用。
如果您需要親自管理認證的輪轉(版本及狀態),可使用通用憑據。
憑據類型 | 說明 | 憑據輪轉方式 | 參考文檔 |
通用憑據 | 通用憑據(Generic Secret)是KMS支援的基礎類型憑據。您可以使用通用憑據儲存帳號口令、存取金鑰、OAuth密鑰和Token、API Key等任意的敏感性資料。 |
| |
RAM憑據 | RAM憑據是KMS支援的一種全託管類型的憑據。您可以使用RAM憑據託管RAM使用者的存取金鑰(AccessKey)。 |
| |
資料庫憑據 | 資料庫憑據是KMS支援的一種全託管類型的憑據,可用於託管ApsaraDB RDS執行個體、PolarDB執行個體等資料庫的帳號和密碼。 |
| |
ECS憑據 | ECS憑據是KMS支援的一種全託管式憑據,可用於託管用於登入ECS執行個體時使用的使用者名稱/口令和SSH密鑰。 |
|
如何計費
使用憑據前,您需要先購買KMS執行個體,購買時設定憑據配額。KMS執行個體的費用,請參見產品計費。關於如何購買KMS執行個體,請參見購買和啟用KMS執行個體。
存取控制與審計
基於Resource Access Management (RAM),限制使用者對憑據的訪問和操作許可權,以保護憑據的安全性。如何配置權限原則,請參見Key Management Service自訂權限原則參考。
基於ActionTrail,支援對憑據的建立、輪轉、讀取等操作進行記錄。具體操作,請參見查詢密鑰和憑據的使用記錄。