Data Management (DMS)支援整合RDS憑據,當DMS需要對RDS資料庫遠端存取時,DMS會即時從KMS擷取憑據值用於登入。本文介紹如何配置DMS使用RDS憑據方式登入RDS資料庫。
功能介紹
當您使用Data Management (DMS)服務對ApsaraDB RDS進行資料資產管理、資料庫開發等操作前,您需要先將RDS資料庫錄入DMS,錄入時需要在DMS配置RDS登入憑證,用於DMS遠端連線RDS資料庫。
除了手動在DMS輸入RDS帳號口令外,DMS還支援整合KMS的憑據功能,即將RDS帳號口令在KMS中儲存為RDS憑據,DMS中配置使用RDS憑據來登入RDS資料庫。當DMS遠端連線RDS資料庫時,會即時從KMS擷取憑據值用於登入。具體流程如下:

憑據管理員在KMS中建立RDS憑據。
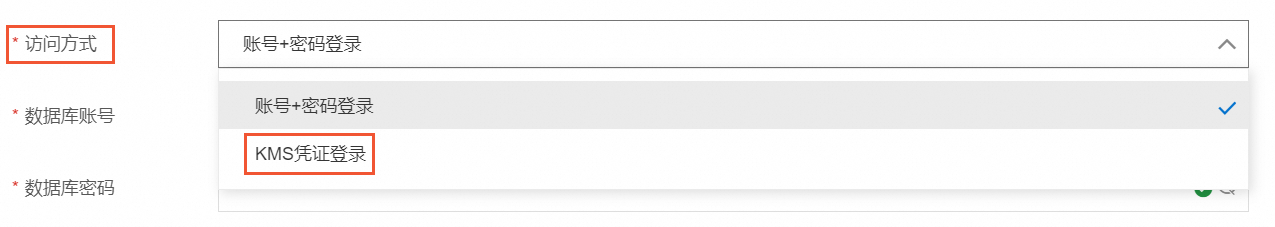
DMS管理員在DMS中錄入RDS資料庫時,設定訪問方式為使用KMS中的RDS憑據。
DMS管理員發起遠端連線RDS資料庫的請求。
DMS調用KMS的ListSecrets、GetSecretValue介面,即時從KMS擷取對應的RDS憑據值。
DMS使用RDS憑據值登入RDS資料庫。
DMS整合RDS憑據的優勢
DMS整合RDS憑據,可以提升資料庫的安全性,確保資料庫憑證的安全存取。
RDS憑據加密儲存在KMS中,減少人工接觸明文資料庫帳號口令,提高了安全性。
您可以在KMS配置RDS憑據定期自動輪轉以更新資料庫口令,降低因長期未更換而帶來的安全風險。
KMS支援Action Trail,可以記錄所有對RDS憑據的訪問請求,方便後續審計和回溯,以及及時發現異常行為。
注意事項
支援的RDS資料庫為:RDS MySQL、RDS MariaDB、RDS SQL Server(2017叢集版除外)和RDS PostgreSQL。
如果您已在KMS託管了RDS憑據,由於RDS憑據支援輪轉,輪轉時會更新口令,因此建議您在DMS中配置使用RDS憑據來登入RDS資料庫,不要手動輸入RDS帳號口令,以避免口令變更導致無法登入RDS資料庫。
在KMS刪除RDS憑據前,請確保DMS已不再訪問該RDS憑據。如何查詢訪問記錄,請參見查詢密鑰和憑據的使用記錄。
前提條件
已購買和啟用KMS執行個體。具體操作,請參見購買和啟用KMS執行個體。
由於建立RDS憑據時需要指定用於加密RDS憑據的對稱金鑰,請先在KMS執行個體中建立對稱金鑰。具體操作,請參見建立密鑰。
步驟一:在KMS建立RDS憑據
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
在凭据管理頁面單擊数据库凭据,選擇实例ID後,單擊,完成各項配置後單擊確定。
配置項
說明
数据库类型
選擇RDS凭据。
凭据名称
自訂的憑據名稱。
RDS实例
選擇阿里雲帳號下已有的RDS執行個體。
账号托管
長度不超過30720位元組(30KB)。
双账号托管(推薦):適用於程式化訪問資料庫情境。託管兩個相同許可權的帳號,保證口令重設切換的瞬間,程式訪問資料庫不被中斷。
單擊新建账号,配置帳號名、選擇資料庫並指定許可權。
說明一鍵建立和授權不會立即為您配置新的帳號,而是在您審核確認憑據資訊之後進行配置。
單擊导入已有账号,選擇使用者名稱、配置口令。
說明建議您將口令配置為建立RDS執行個體使用者帳號時對應的密碼。如果匯入的帳號和口令不匹配,您可以在憑據首次輪轉之後,擷取正確的帳號和口令。
单账号托管:適用於高許可權帳號或者人工營運帳號託管情境。口令重設切換的瞬間,憑據的目前的版本可能暫時無法使用。
單擊新建账号,配置帳號名、選擇帳號類型。
您可以選擇普通账号和高权限账号兩種帳號類型。當您選擇普通账号時,還需選擇資料庫並指定許可權。
單擊导入已有账号頁簽,選擇使用者名稱、配置口令。
加密主密钥
選擇用於加密憑據值的密鑰。
重要密鑰和憑據需要屬於同一個KMS執行個體,且密鑰必須為對稱金鑰。關於KMS支援哪些對稱金鑰,請參見密鑰管理類型和密鑰規格。
如果是RAM使用者、RAM角色,需要具備使用加密主要金鑰執行GenerateDataKey操作的許可權。
標籤
憑據的標籤,方便您對憑據進行分類管理。每個標籤由一個索引值對(Key:Value)組成,包含標籤鍵(Key)、標籤值(Value)。
說明標籤鍵和標籤值的格式:最多支援128個字元,可以包含英文大小寫字母、數字、正斜線(/)、反斜線(\)、底線(_)、短劃線(-)、半形句號(.)、加號(+)、等號(=)、半形冒號(:)、字元at(@)。
標籤鍵不能以aliyun或acs:開頭。
每個憑據最多可以設定20個標籤索引值對。
自动轮转
選擇開啟或關閉憑據的周期性自動輪轉。
轮转周期
僅當开启自动轮转時需要設定。支援設定為6小時~365天。
表示輪轉的周期,設定後KMS將定期為您更新憑據值。
描述信息
憑據的描述資訊。
策略配置
憑據的策略配置。詳細介紹,請參見憑據策略概述。
您可以先選擇預設策略,建立憑據後根據業務需要再修改策略。
步驟二:將RDS資料庫錄入DMS
在控制台首頁左側的資料庫執行個體地區,單擊新增執行個體
 表徵圖。說明
表徵圖。說明您還可以在功能表列中選擇,單擊新增,進行新增執行個體操作。
在新增執行個體頁面,錄入RDS執行個體資訊。
訪問方式選擇KMS憑證登入。其他參數如何配置,請參見雲資料庫錄入。
相關文檔
已經在DMS中通過帳號密碼方式錄入的RDS資料庫, 支援將訪問方式修改為KMS憑據登入。具體操作,請參見編輯執行個體資訊。
將資料庫錄入DMS後,您可能需要進行如下操作:
建立資料庫、建立表、查詢表資料、變更表資料等操作。具體操作,請參見SQL Console初體驗。
需要在不鎖表的前提下變更大量表資料,您可使用DMS的無鎖資料變更。具體操作,請參見DML無鎖變更。
匯出表資料。具體操作,請參見匯出資料。