您可以使用KMS輕鬆地建立密鑰,使用祕密金鑰加密、解密業務資料,保護您的資料安全。本文介紹如何建立及使用密鑰。
概述
KMS提供預設密鑰、軟體密鑰和硬體密鑰三種密鑰管理類型,以滿足不同業務情境、安全與合規要求。更多詳細資料,請參見密鑰服務概述、密鑰管理類型和密鑰規格。
預設密鑰是KMS免費為使用者提供的功能,可供雲產品服務端加密,比如和ECS結合使用。預設密鑰只提供對稱解密這一種加密方式,並且不支援用戶端資料加密。
軟體密鑰和預設密鑰一樣提供雲產品服務端加密功能,除此之外也可用於構建應用程式層密碼技術方案,提供介面API用於用戶端資料加解密、數位簽章計算和驗證,支援對稱金鑰和非對稱金鑰,同時支援通行金鑰輪轉(自動更新密鑰),減少密鑰泄漏風險。
硬體密鑰和軟體密鑰一樣提供雲產品服務端加密功能和構建應用程式層密碼技術方案,提供介面API用於用戶端資料加解密、數位簽章計算和驗證,支援對稱金鑰和非對稱金鑰,相對軟體密鑰支援的密鑰規格更多,同時會把金鑰儲存區在密碼機中,滿足密碼法和FIPS國際的合規要求,但不支援通行金鑰輪轉。
密鑰管理為雲產品加密
密鑰管理可供雲產品服務端加密,比如和ECS結合使用,解決服務端資料明文傳輸的安全問題。支援該功能的密鑰類型:預設密鑰、軟體密鑰、硬體密鑰
使用樣本
本文以ECS整合KMS預設主要金鑰為例。關於雲產品整合KMS的更多資訊,請參見雲產品整合KMS加密概述、支援整合KMS加密的雲產品。
步驟一:啟用預設主要金鑰
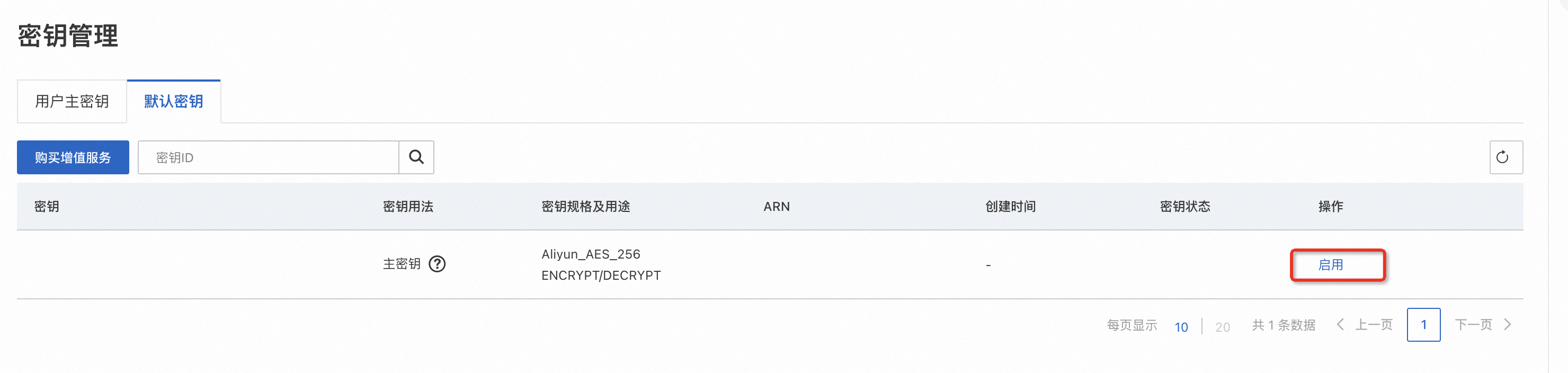
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊资源 > 密钥管理。
在密鑰管理頁單擊默认密钥,點擊主要金鑰操作欄的啟用按鈕。為主要金鑰取名alias/main。
您的預設密鑰中的主要金鑰只能用於雲產品服務端加密,不能用於您的用戶端資料加密。如果您有用戶端資料加密的訴求,請通過建立執行個體購買主要金鑰(軟體)或者主要金鑰(硬體)。
步驟二:ECS整合KMS預設密鑰
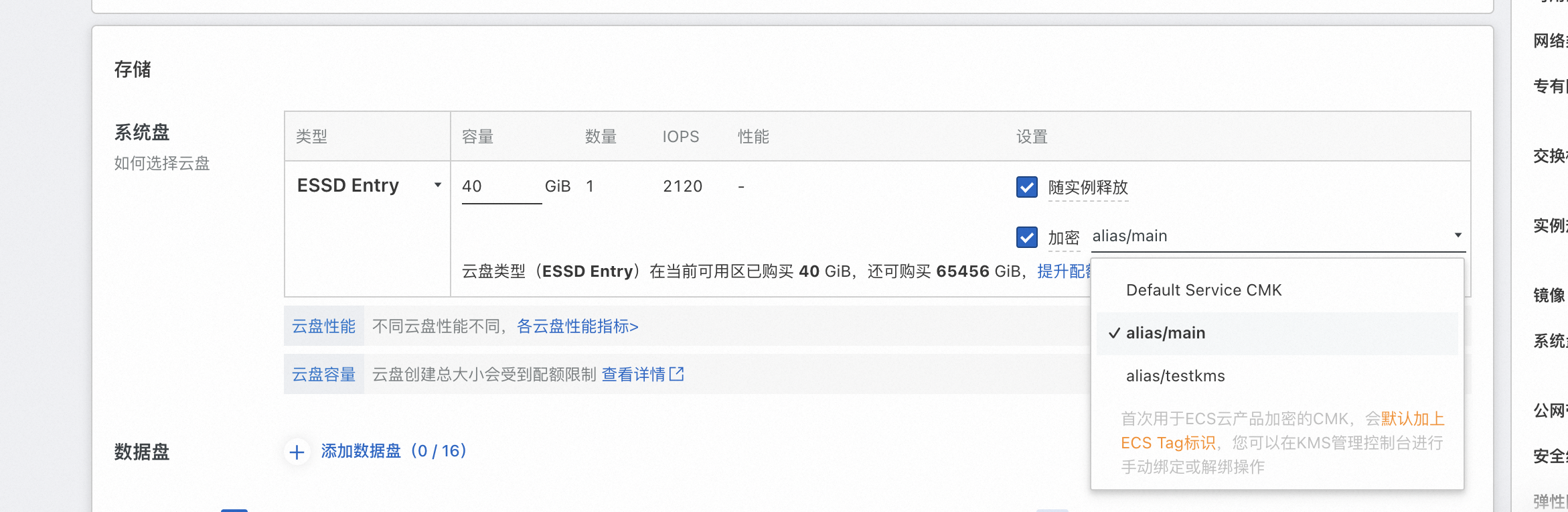
購買ECS產品時,在購買頁選擇使用建立的主要金鑰alias/mainData Encryption Service端資料
步驟三:ECS使用KMS對資料進行密文傳輸
當有資料在ECS上傳輸時,ECS會預設調用KMS API對資料進行加解密處理,無需人工處理資料。通常雲產品採用信封加密的機制實現對資料的加密,詳情請參見使用KMS密鑰進行信封加密。
密鑰管理構建應用程式層密碼技術方案
密鑰管理可用於構建應用程式層密碼技術方案,提供介面API用於用戶端資料加解密、數位簽章計算和驗證。支援該功能的密鑰類型:軟體密鑰、硬體密鑰。
前提條件
已購買並啟用KMS軟體/硬體密鑰管理執行個體。具體操作,請參見購買和啟用KMS執行個體。
使用樣本
本文以使用軟體執行個體金鑰組應用程式層資料進行加密(Encrypt)和解密(Decrypt)為例。更多操作請參見使用KMS密鑰線上加密和解密資料。
步驟一:建立軟體密鑰
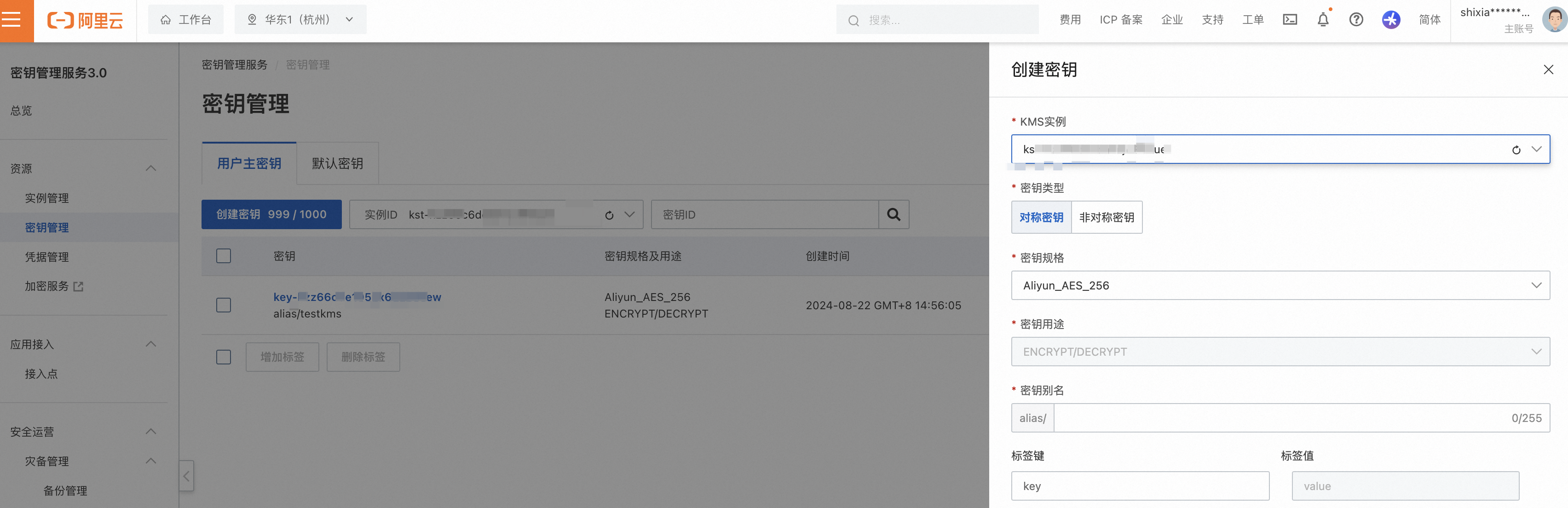
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊资源 > 密钥管理。
進入用户主密钥頁簽,單擊创建密钥,根據提示完成配置。
KMS執行個體選擇之前購買的KMS軟體密鑰管理執行個體。
密鑰類型選擇對稱式加密。
密鑰規格選擇Aliyun_AES_256。
步驟二:升級KMS執行個體鏡像版本
本文樣本為通過KMS專屬網關調用OpenAPI進行密碼運算,鏡像版本需要為3.0.0及以上。
如果KMS執行個體的鏡像版本已經是3.0.0及以上版本,請跳過此步驟。
請在实例管理頁面的執行個體詳情中查看鏡像版本,如果鏡像版本為3.0.0以下,請單擊升级版本升級KMS執行個體的鏡像版本。詳細介紹,請參見升級KMS執行個體的鏡像版本。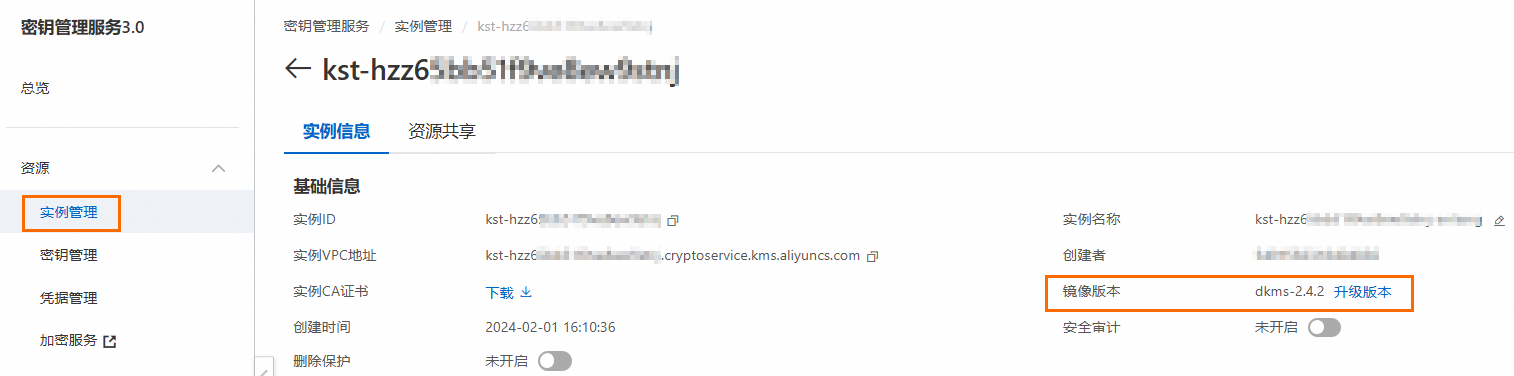
步驟三:依賴安裝
環境準備
環境要求
已下載並安裝Java 8或以上版本。
驗證版本
開啟終端,輸入
java -version,查看Java(JDK)版本。安裝SDK
在專案中添加Maven依賴,從Maven倉庫中自動下載Java安裝包。請使用阿里雲SDK(V2.0)。
<dependency> <groupId>com.aliyun</groupId> <artifactId>kms20160120</artifactId> <version>1.2.3</version> </dependency> <dependency> <groupId>com.aliyun</groupId> <artifactId>tea</artifactId> <version>1.3.2</version> </dependency> <dependency> <groupId>com.aliyun</groupId> <artifactId>tea-openapi</artifactId> <version>0.3.6</version> </dependency>
步驟四:建立介面調用憑證
阿里雲SDK支援基於RAM的多種認證方式,本文以使用RAM使用者的AccessKey為例。更多認證方式的介紹,請參見管理訪問憑據。
在RAM控制台建立RAM使用者的AccessKey。具體操作,請參見建立AccessKey。
如果您已有AccessKey,請跳過該步驟。
為RAM使用者佈建合適的存取權限。
例如,您希望該RAM使用者僅能執行密碼運算操作,可以授予其系統權限原則AliyunKMSCryptoUserAccess。具體操作,請參見為RAM使用者授權。
 說明
說明KMS提供了兩種設定存取權限的途徑:
基於身份的策略:上述樣本即該方式,通過關聯身份與相應的許可權來控制訪問。詳細介紹,請參見使用RAM進行存取控制。
基於資源的策略:包含密鑰策略、憑據策略,這些策略直接與資源相關聯,用於定義對特定資源的訪問規則。詳細介紹,請參見密鑰策略、憑據策略。
步驟五:擷取KMS執行個體的CA認證
在執行個體的詳情頁面,擷取執行個體CA認證。

步驟六:擷取執行個體VPC地址
在執行個體的詳情頁面,擷取執行個體VPC地址。

步驟七:用戶端調用
初始化阿里雲SDK。
重要請使用阿里雲SDK(V2.0),Endpoint請填寫執行個體VPC地址,同時需要設定執行個體CA認證。
public static com.aliyun.kms20160120.Client createClient() throws Exception { // 工程代碼泄露可能會導致 AccessKey 泄露,並威脅帳號下所有資源的安全性。以下程式碼範例僅供參考。 // 建議使用更安全的 STS 方式,更多鑒權訪問方式請參見:https://www.alibabacloud.com/help/document_detail/378657.html。 com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config() // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_ID。 .setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID")) // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_SECRET。 .setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET")); // Endpoint請輸入執行個體VPC地址,例如kst-hzz65f176a0ogplgq****.cryptoservice.kms.aliyuncs.com config.endpoint = "<執行個體VPC地址>"; // 請填寫執行個體ca認證的內容 config.ca = "<執行個體CA認證>"; return new com.aliyun.kms20160120.Client(config); }調用Encrypt加密資料。
package com.aliyun.sample; import com.aliyun.tea.*; public class Sample { public static com.aliyun.kms20160120.Client createClient() throws Exception { // 工程代碼泄露可能會導致 AccessKey 泄露,並威脅帳號下所有資源的安全性。以下程式碼範例僅供參考。 // 建議使用更安全的 STS 方式,更多鑒權訪問方式請參見:https://www.alibabacloud.com/help/document_detail/378657.html。 com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config() // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_ID。 .setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID")) // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_SECRET。 .setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET")); // Endpoint請輸入執行個體VPC地址,例如kst-hzz65f176a0ogplgq****.cryptoservice.kms.aliyuncs.com config.endpoint = "<執行個體VPC地址>"; // 請填寫執行個體ca認證的內容 config.ca = "<執行個體CA認證>"; return new com.aliyun.kms20160120.Client(config); } public static void main(String[] args_) throws Exception { java.util.List<String> args = java.util.Arrays.asList(args_); com.aliyun.kms20160120.Client client = Sample.createClient(); com.aliyun.kms20160120.models.EncryptRequest encryptRequest = new com.aliyun.kms20160120.models.EncryptRequest() .setKeyId("<keyID>") .setPlaintext("<PlaintText>"); com.aliyun.teautil.models.RuntimeOptions runtime = new com.aliyun.teautil.models.RuntimeOptions(); try { // 複製代碼運行請自行列印 API 的傳回值 client.encryptWithOptions(encryptRequest, runtime); } catch (TeaException error) { // 此處僅做列印展示,請謹慎對待異常處理,在工程專案中切勿直接忽略異常。 // 錯誤 message System.out.println(error.getMessage()); // 診斷地址 System.out.println(error.getData().get("Recommend")); com.aliyun.teautil.Common.assertAsString(error.message); } catch (Exception _error) { TeaException error = new TeaException(_error.getMessage(), _error); // 此處僅做列印展示,請謹慎對待異常處理,在工程專案中切勿直接忽略異常。 // 錯誤 message System.out.println(error.getMessage()); // 診斷地址 System.out.println(error.getData().get("Recommend")); com.aliyun.teautil.Common.assertAsString(error.message); } } }調用Decrypt解密資料。
package com.aliyun.sample; import com.aliyun.tea.*; public class Sample { public static com.aliyun.kms20160120.Client createClient() throws Exception { // 工程代碼泄露可能會導致 AccessKey 泄露,並威脅帳號下所有資源的安全性。以下程式碼範例僅供參考。 // 建議使用更安全的 STS 方式,更多鑒權訪問方式請參見:https://www.alibabacloud.com/help/document_detail/378657.html。 com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config() // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_ID。 .setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID")) // 必填,請確保代碼運行環境設定了環境變數 ALIBABA_CLOUD_ACCESS_KEY_SECRET。 .setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET")); // Endpoint請輸入執行個體VPC地址,例如kst-hzz65f176a0ogplgq****.cryptoservice.kms.aliyuncs.com config.endpoint = "<執行個體VPC地址>"; // 請填寫執行個體ca認證的內容 config.ca = "<執行個體CA認證>"; return new com.aliyun.kms20160120.Client(config); } public static void main(String[] args_) throws Exception { java.util.List<String> args = java.util.Arrays.asList(args_); com.aliyun.kms20160120.Client client = Sample.createClient(); com.aliyun.kms20160120.models.DecryptRequest decryptRequest = new com.aliyun.kms20160120.models.DecryptRequest() .setCiphertextBlob("<CiphertextBlob>"); com.aliyun.teautil.models.RuntimeOptions runtime = new com.aliyun.teautil.models.RuntimeOptions(); try { // 複製代碼運行請自行列印 API 的傳回值 client.decryptWithOptions(decryptRequest, runtime); } catch (TeaException error) { // 此處僅做列印展示,請謹慎對待異常處理,在工程專案中切勿直接忽略異常。 // 錯誤 message System.out.println(error.getMessage()); // 診斷地址 System.out.println(error.getData().get("Recommend")); com.aliyun.teautil.Common.assertAsString(error.message); } catch (Exception _error) { TeaException error = new TeaException(_error.getMessage(), _error); // 此處僅做列印展示,請謹慎對待異常處理,在工程專案中切勿直接忽略異常。 // 錯誤 message System.out.println(error.getMessage()); // 診斷地址 System.out.println(error.getData().get("Recommend")); com.aliyun.teautil.Common.assertAsString(error.message); } } }
相關文檔
如果您想瞭解密鑰的應用情境、演算法類型、密鑰規格等資訊,請參見密鑰服務概述。
如果您想瞭解SDK接入的詳細資料,請參見阿里雲SDK(Java)。
如果您有對少量資料進行加解密的需求時,可採用直接加密的方式。具體操作,請參見使用KMS密鑰線上加密和解密資料。
如果您有對大量資料進行加解密的需求時,可採用信封加密的方式。具體操作,請參見使用KMS密鑰進行信封加密