Cloud Firewall的入侵防禦IPS(Intrusion Prevention System)能力可以即時主動式偵測和攔截駭客惡意攻擊、漏洞利用、暴力破解、蠕蟲、挖礦程式、後門木馬、DoS等惡意流量,保護雲上公司資訊系統和網路架構免受侵害,防止業務被未授權訪問或資料泄露、業務系統和應用程式損壞或宕機等。
使用限制
Cloud Firewall入侵防禦不支援對TLS、SSL加密的流量進行解密檢測和防禦,但支援部分基於加密指紋的IPS檢測規則。
由於資料彙總,Cloud Firewall的入侵防禦資料統計存在一定延時。如果需要查詢即時資料,建議您通過日誌審計或日誌分析查詢,具體操作,請參見日誌審計或查詢及分析日誌。
查詢最近1小時內的防禦資料時,統計資料會存在10分鐘的延時,即查詢結果中不包含最近10分鐘內發生的防禦事件。
查詢超過1小時且包含當前30分鐘內的防禦資料時,統計資料會存在30分鐘延時,即查詢結果中不包含最近30分鐘內發生的防禦事件。
例如,目前時間為15:00:00,如果您查詢當日12:00:00~15:00:00的資料時,14:30:00~15:00:00之間的資料將無法查到;如果您查詢當日12:00:00~14:30:00的資料,您將可以查詢到該時間段內的完整資料。
查看或者修改入侵防禦規則
開通Cloud Firewall服務後,防護配置的威脅引擎預設啟用攔截模式,即Cloud Firewall會自動攔截攻擊行為。同時,Cloud Firewall會根據業務流量的實際情況判斷,自動選擇需要開啟的攔截模式等級(寬鬆、中等、嚴格)。此外,Cloud Firewall會預設開啟威脅情報、基礎防禦和虛擬補丁。
您可以通過以下任意一種方式進入IPS配置頁面管理防護策略:
入侵防御頁面中,通過防護明細列表右上方連結入口直達。

在左側導覽列,選擇。

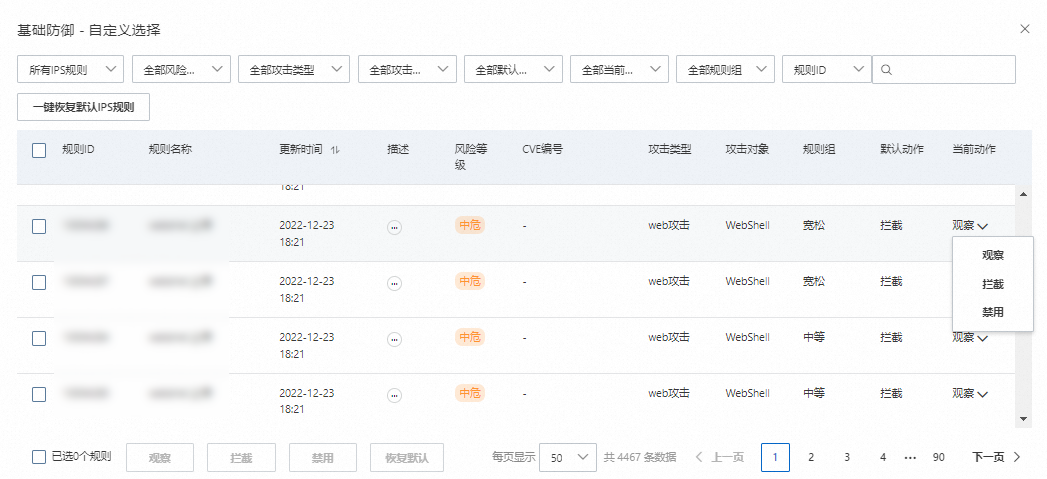
進入頁面後,在基礎防禦卡片中單擊自訂選擇,查看預設的入侵防禦規則。如果您業務需要修改某條入侵防禦的規則,定位到該規則,在當前動作列,修改該規則的執行動作。更多資訊,請參見IPS配置。
開啟IPS私網溯源
查看互連網阻斷事件
Cloud Firewall提供了雲資產的互連網入向和出向流量防護統計資料,便於您瞭解Cloud Firewall對資產流量的防禦情況,確保資產安全。您可以查詢過去90天內的互連網流量阻斷資料,單次查詢時間最長範圍為31天。
進入頁面,在互聯網攔截頁簽,設定查詢時間後,查看防護資料統計和防護明細列表。
防护数据模組包含攻擊總數、攻擊類型分布、攔截資料。
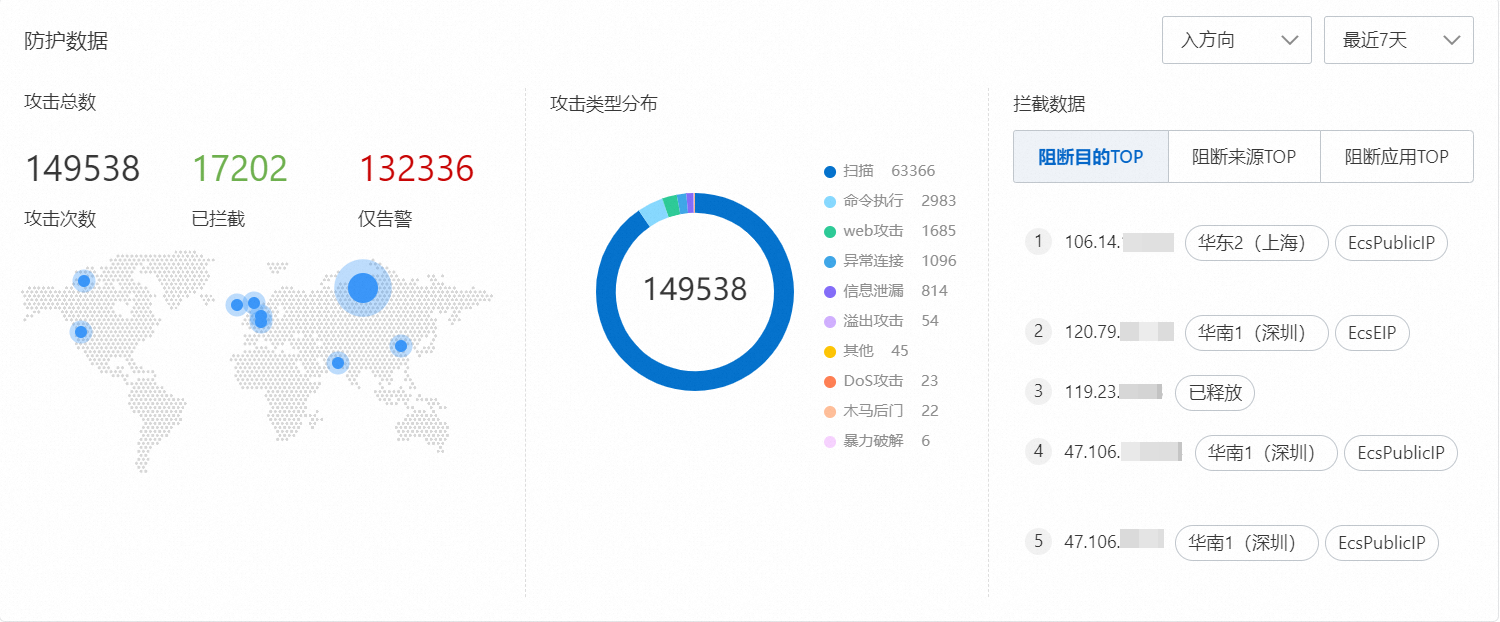
其中,攔截資料指標說明如下:
阻断目的IP TOP:展示被Cloud Firewall阻斷的流量中,佔比Top 5的目的IP地址。
滑鼠懸浮在阻斷目的IP上,單擊
 表徵圖,可進入日誌審計頁面查看該目的IP地址對應的流量的目的連接埠、應用類型、動作等詳細資料。
表徵圖,可進入日誌審計頁面查看該目的IP地址對應的流量的目的連接埠、應用類型、動作等詳細資料。阻斷來源TOP:展示被Cloud Firewall阻斷的流量中,佔比Top 3的來源類型。
被阻斷的應用TOP:展示被Cloud Firewall阻斷的流量中,佔比Top 5的應用類型。
防護明細列表:根據查詢條件,展示Cloud Firewall對攻擊流量的防護明細,包括事件的風險層級、事件數目量、源IP地址、目的IP地址等資訊。
 說明
說明如果源IP是WAF或者DDoS的回源地址,Cloud Firewall會識別出此類回源地址,並顯示WAF回源IP、DDoS回源IP。
在該模組地區,您可以執行以下操作:
查詢目標事件:選擇風險層級、防禦狀態、攻擊類型、判斷來源、方向和時間範圍等條件後,單擊搜尋,查看符合設定條件的事件資訊。
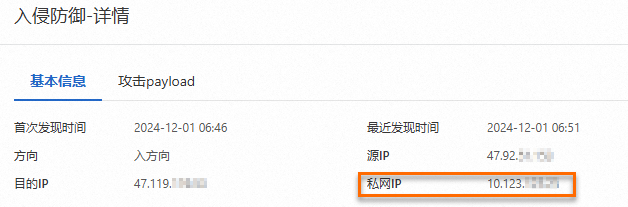
查看事件詳情:在操作列單擊詳情,開啟阻斷事件的詳情頁面,查看基本信息、攻擊payload等詳細資料。攻擊payload展示了攻擊流量的五元組資訊、載荷內容等,方便您進行攻擊溯源,降低安全風險。
下載阻斷事件:在搜尋欄右側,單擊
 表徵圖,在右上方的下载任务管理中下載阻斷事件。
表徵圖,在右上方的下载任务管理中下載阻斷事件。AI輔助分析事件:單擊AI分析列下的
 表徵圖,即可利用安全AI助手快速輔助事件分析。
表徵圖,即可利用安全AI助手快速輔助事件分析。內容包含:
Payload內容分析:包含關於請求的簡要描述和AI對其請求動作的分析。

威脅情報:目的地址與情報庫的比對結果。
說明Cloud Firewall進階版和隨用隨付版不支援此項內容。
攻擊者意圖:AI分析得出的攻擊者行為預測。
防禦建議:提供雲牆防護配置(ACL策略、IPS配置等)和資產排查的建議。
查看VPC攔截事件
Cloud Firewall為您提供了VPC網路之間的流量防護統計情況,您可以查看VPC的流量通行和阻斷情況。您可以查詢過去90天內的VPC流量阻斷資料,單次查詢時間最長範圍為31天。
Cloud Firewall進階版不支援VPC邊界防火牆,不會顯示VPC防護頁簽。
進入頁面,在VPC攔截頁簽,查看指定時間段內VPC攔截事件的名稱、風險層級、攻擊類型等詳細資料。

您可以執行以下操作:
查詢目標事件:選擇風險層級、防禦狀態、攻擊類型和時間等條件後,單擊搜尋,查看符合設定條件的事件資訊。
查看事件詳情:在操作列單擊詳情,開啟阻斷事件的詳情頁面,查看基本信息、攻擊payload等詳細資料。攻擊payload展示了攻擊流量的五元組資訊、載荷內容等,方便您進行攻擊溯源,降低安全風險。
下載防護事件:在搜尋欄右側,單擊
 表徵圖,在右上方的下载任务管理中下載防護事件。
表徵圖,在右上方的下载任务管理中下載防護事件。AI輔助分析事件:單擊AI分析列下的
 表徵圖,即可利用安全AI助手快速輔助事件分析。
表徵圖,即可利用安全AI助手快速輔助事件分析。內容包含:
Payload內容分析:包含關於請求的簡要描述和AI對其請求動作的分析。

威脅情報:目的地址與情報庫的比對結果。
說明Cloud Firewall進階版和隨用隨付版不支援此項內容。
攻擊者意圖:AI分析得出的攻擊者行為預測。
防禦建議:提供雲牆防護配置(ACL策略、IPS配置等)和資產排查的建議。