Service MeshASM支援通過流量標籤功能將應用的相關版本(或者其他特徵)隔離成一個獨立的運行環境(即泳道),然後通過設定泳道規則,將滿足規則的請求流量路由到目標版本(或者其他特徵)的應用上。本文介紹如何在ASM中使用泳道模式下的流量管理功能。
前提條件
已建立ASM企業版或旗艦版執行個體,且版本為1.17.2.22及以上。具體操作,請參見建立ASM執行個體或升級ASM執行個體。
已添加叢集到ASM執行個體。具體操作,請參見添加叢集到ASM執行個體。
已建立名稱為ingressgateway的ASM網關。具體操作,請參見建立入口網關服務。
已建立名稱為ingressgateway且命名空間為istio-system的網關規則。具體操作,請參見管理網關規則。
功能介紹
灰階發布會根據請求內容或者請求流量的比例將線上流量的一小部分轉寄至新版本,待灰階驗證通過後,逐步調大新版本的請求流量,是一種循序漸進的發布方式。
全鏈路灰階治理策略主要專註於整個調用鏈,不關心鏈路上經過具體哪些微服務。流量控制視角從服務轉移至請求鏈路上。您僅需制定少量的治理規則,便可構建從網關到整個後端服務的多個流量隔離環境,有效保障多個服務順利安全發布以及服務多版本並行開發,進一步促進業務的快速發展。更多資訊,請參見流量標籤TrafficLabel說明。
本文樣本情境如下。圖中有三個泳道s1、s2、s3,分別包含三個服務mocka、mockb、mockc。在ASM控制台部署泳道後,您可以查看各個泳道的流量分布是否符合預期。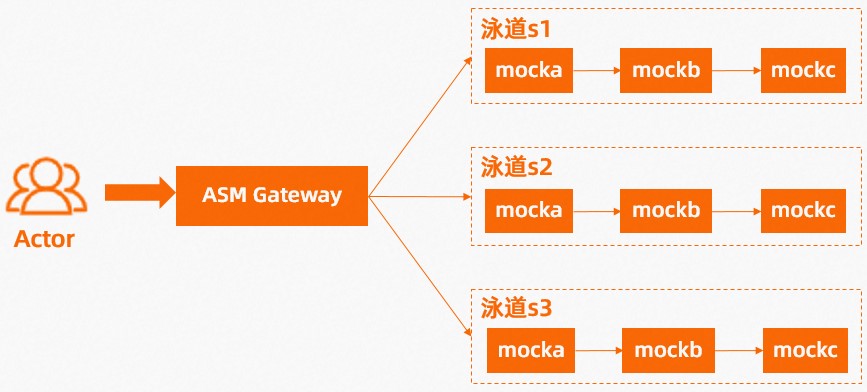
步驟一:部署樣本服務
為default命名空間啟用Sidecar網格代理自動注入。具體操作,請參見啟用自動注入。
關於自動注入的更多資訊,請參見配置Sidecar注入策略。
在ACK叢集中執行以下命令,部署樣本服務。
kubectl apply -f https://alibabacloudservicemesh.oss-cn-beijing.aliyuncs.com/asm-labs/swimlane/v1/application-v1.yaml kubectl apply -f https://alibabacloudservicemesh.oss-cn-beijing.aliyuncs.com/asm-labs/swimlane/v2/application-v2.yaml kubectl apply -f https://alibabacloudservicemesh.oss-cn-beijing.aliyuncs.com/asm-labs/swimlane/v3/application-v3.yaml
步驟二:建立泳道組和對應泳道
建立泳道組。
登入ASM控制台,在左側導覽列,選擇。
在網格管理頁面,單擊目標執行個體名稱,然後在左側導覽列,選擇。
在流量泳道頁面,單擊建立泳道組,在建立泳道組面板,配置相關資訊,然後單擊確定。
配置項
說明
泳道組名稱
本樣本配置為test。
入口網關
選擇ingressgateway。
泳道服務
選擇目標Kubernetes叢集和default命名空間,在下方列表中選中mocka、mockb和mockc服務,單擊
 表徵圖,添加目標服務到已選擇地區。
表徵圖,添加目標服務到已選擇地區。配置完成後,會自動產生對應的流量標籤TrafficLabel。
建立s1、s2、s3泳道,並分別綁定v1、v2、v3版本。
下文以建立s1泳道為例進行說明,請參照以下步驟建立s2和s3泳道。
在流量泳道頁面的流量規則定義地區,單擊建立泳道。
在建立泳道對話方塊,配置相關資訊,然後單擊確定。
配置項
說明
泳道名稱
本樣本配置為s1。
說明訪問服務時,帶上對應的Header請求(
'x-asm-prefer-tag: 泳道名稱')會路由到對應的版本。佈建服務標籤
本樣本配置為v1。
添加服務
選擇mocka(default)、mockb(default)和mockc(default)。

三個泳道建立完成後,樣本效果如下:

每建立一個泳道,會自動建立對應的目標規則DestinationRule。例如s1泳道建立完成後,會自動建立如下目標規則DestinationRule樣本。
建立各個泳道對應的引流規則。
下文以建立s1泳道的引流規則為例進行說明,請參照以下步驟建立s2和s3泳道的引流規則。
在流量泳道頁面的流量規則定義地區,單擊目標泳道右側操作列下的引流規則。
在添加引流規則對話方塊,配置相關資訊,然後單擊確定。
本文以泳道服務對應入口API均為
/mock為例,為每個泳道配置相同的引流規則。配置項
說明
入口服務
選擇mocka.default.svc.cluster.local。
引流規則
配置名稱為r1,網域名稱為*。
匹配請求的URI
配置匹配方式為精確,匹配內容為/mock。
三個泳道的引流規則建立成功後,樣本效果如下:
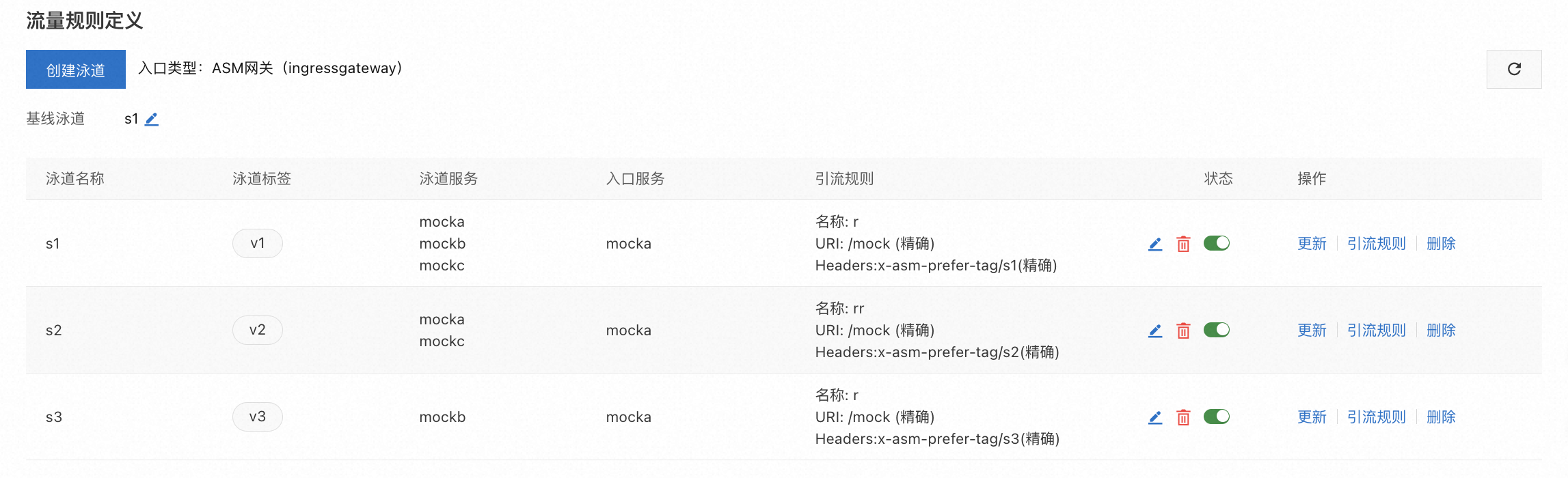
建立成功後,會自動產生如下虛擬服務VirtualService樣本。
步驟三:驗證全鏈路灰階功能是否生效
擷取ASM網關的公網IP。具體操作,請參見擷取ASM網關地址。
執行以下命令,設定環境變數。
xxx.xxx.xxx.xxx為上一步擷取的IP。export ASM_GATEWAY_IP=xxx.xxx.xxx.xxx驗證全鏈路灰階功能是否生效。
執行以下命令,查看s1泳道的訪問效果。
x-asm-prefer-tag對應的值s1為步驟2建立s1泳道時配置的泳道名稱。for i in {1..100}; do curl -H 'x-asm-prefer-tag: s1' http://${ASM_GATEWAY_IP}/mock ; echo ''; sleep 1; done;預期輸出:
-> mocka(version: v1, ip: 172.17.0.54)-> mockb(version: v1, ip: 172.17.0.129)-> mockc(version: v1, ip: 172.17.0.130)由預期輸出得到,通過設定HTTP標題
x-asm-prefer-tag: s1聲明的流量流向s1泳道下的相關服務,符合預期。執行以下命令,查看s2泳道的訪問效果。
x-asm-prefer-tag對應的值s2為步驟2建立s2泳道時配置的泳道名稱。for i in {1..100}; do curl -H 'x-asm-prefer-tag: s2' http://${ASM_GATEWAY_IP}/mock ; echo ''; sleep 1; done;預期輸出:
-> mocka(version: v2, ip: 172.17.0.9)-> mockb(version: v2, ip: 172.17.0.126)-> mockc(version: v2, ip: 172.17.0.128)由預期輸出得到,通過設定HTTP標題
x-asm-prefer-tag: s2聲明的流量流向s2泳道下的相關服務,符合預期。執行以下命令,查看s3泳道的訪問效果。
x-asm-prefer-tag對應的值s3為步驟2建立s3泳道時配置的泳道名稱。for i in {1..100}; do curl -H 'x-asm-prefer-tag: s3' http://${ASM_GATEWAY_IP}/mock ; echo ''; sleep 1; done;預期輸出:
-> mocka(version: v3, ip: 172.17.0.132)-> mockb(version: v3, ip: 172.17.0.127)-> mockc(version: v3, ip: 172.17.0.69)由預期輸出得到,通過設定HTTP標題
x-asm-prefer-tag: s3聲明的流量流向s3泳道下的相關服務,符合預期。
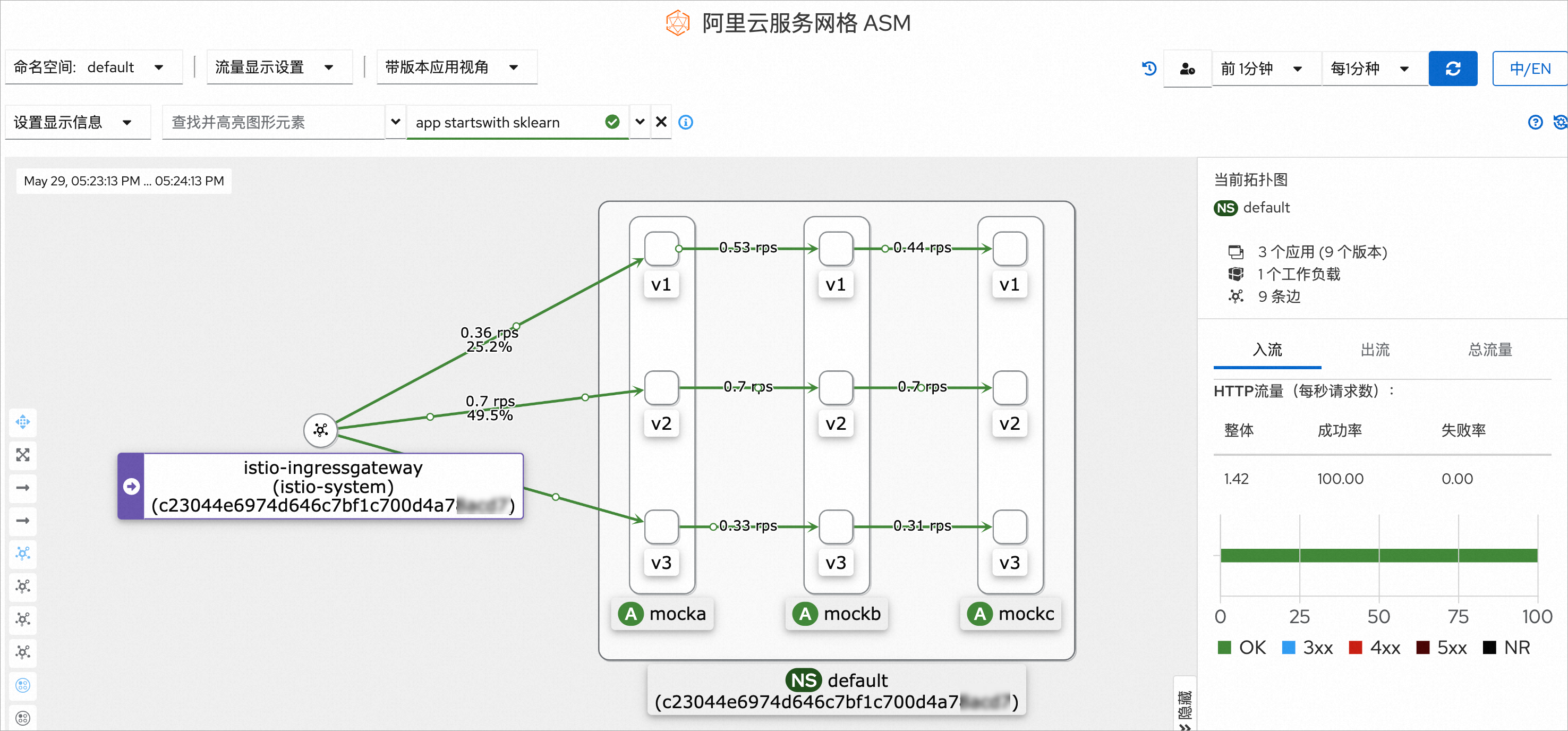
(可選)步驟四:查看網格拓撲
若您已通過ASM控制台開啟網格拓撲的可觀測性,可以查看在上述請求下的網格拓撲。具體操作,請參見開啟網格拓撲提高可觀測性。