Problem description
After my service is added to an Anti-DDoS Pro or Anti-DDoS Premium instance, issues such as slow response, high latency, and access failures occur.
Causes
- Collect the affected IP addresses and test connectivity by using tools such as traceroute
or MTR to identify the cause.
Note
The MTR tool is used in this step to describe how to check latency in network links.
mtr --no-dns [$IP]Note [$IP] indicates the affected IP address that you collect. - Check whether the Host value of the node is the IP address of your origin server or the IP address of the Anti-DDoS Pro or Anti-DDoS Premium instance.
Solutions
If you want to immediately access your service, we recommend that you bypass Anti-DDoS Pro or Anti-DDoS Premium and directly access the origin server. This ensures normal access to your service. Then, troubleshoot the issue based on the following sections.
Troubleshooting for the exceptions on origin servers
Troubleshoot the exceptions based on the type of your origin server.
| Type of origin server | Troubleshooting |
|---|---|
| Server Load Balancer (SLB) instance |
|
| Elastic Compute Service (ECS) instance |
|
| Server not deployed on Alibaba Cloud |
|
Troubleshooting for an Anti-DDoS Pro and Anti-DDoS Premium instance
- Scrubbing
If network traffic exceeds the traffic scrubbing threshold, the instance scrubs traffic. Traffic scrubbing events may cause slow response or latency.
- Blackholing
If volumetric attacks are launched to your server and blackholing filtering is triggered for your server, the server is accessible only from Alibaba Cloud and services in the same region as the server. Traffic from other sources is denied.
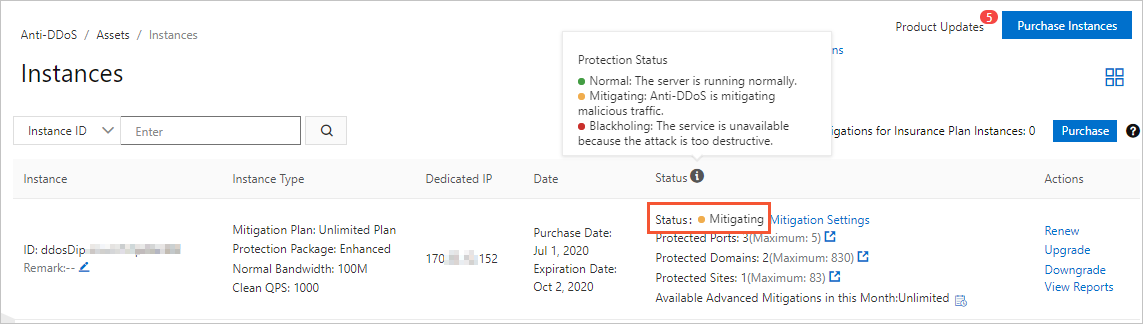
| Latency and packet loss on affected ports
|
Latency and packet loss on unaffected ports
|
Solution |
|---|---|---|
| Yes | No | The traffic scrubbing policy does not cause high latency and packet loss.
We recommend that you check the status and attack mitigation capabilities of the backend
server. If the backend server does not have sufficient capabilities to mitigate attacks,
adjust the mitigation policies of your Anti-DDoS Pro or Anti-DDoS Premium instance
to harden the security of the server. You can analyze the attack mitigation capabilities
of your server and adjust the mitigation policies based on the following details:
|
| Yes | Yes | The traffic scrubbing policy causes latency and packet loss. |
| No | No | The traffic scrubbing policy does not cause latency or packet loss. |
| No | Yes | This case does not exist. |
- The following figure shows that blackhole filtering events occurred. In this case,
check the IP address that is in the blackholing state and check whether the affected
service used the IP address.
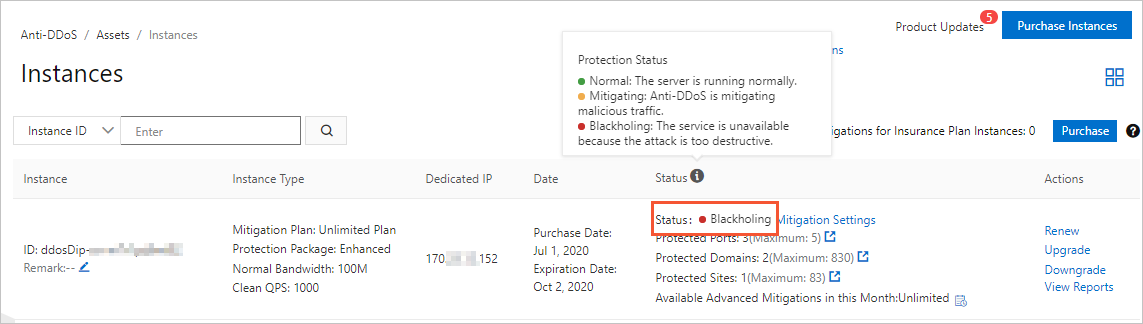
- We recommend that you deactivate blackhole filtering. Each Alibaba Cloud account can deactivate blackhole filtering up to five times per day. For more information, see Deactivate blackhole filtering.
Additional information
- Use TCPing in Windows
Copy the TCPing tool to the specified directory in Windows and run the
tcping [$Domain_Name] [$Port]command.Note- [$Domain_Name] indicates the domain name or IP address for which you want to test connectivity.
- [$Port] indicates the port for which you want to test connectivity.
The following output is returned:Probing 192.168.XX.XX:80/tcp - Port is open - time=19.550ms Probing 140.XXX.XXX.8:80/tcp - Port is open - time=8.761ms Probing 192.168.XX.XX:80/tcp - Port is open - time=10.899ms Probing 192.168.XX.XX:80/tcp - Port is open - time=13.013ms Ping statistics for 192.168.XX.XX:80 4 probes sent. 4 successful, 0 failed. Approximate trip times in milli-seconds: Minimum = 8.761ms, Maximum = 19.550ms, Average = 13.056ms - Use TCPing in Linux
- Run the following commands in sequence to install TCPing:
tar zxvf tcping-1.3.5.tar.gz cd tcping-1.3.5 make tcping.linux - Run the following command to test connectivity:
for ((i=0; i<10; ++i)) ; do ./tcping www.example.com 80;doneThe following output is returned:www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open. www.example.com port 80 open.
- Run the following commands in sequence to install TCPing:
Applicable scope
Anti-DDoS Pro and Anti-DDoS Premium