セキュリティグループは仮想ファイアウォールとして機能し、SPI (Stateful Packet Inspection) およびパケットフィルタリング機能を提供し、クラウド内のセキュリティドメインを定義します。 セキュリティグループルールを追加して、セキュリティグループ内のエラスティックコンテナインスタンスのインバウンドトラフィックとアウトバウンドトラフィックを制御できます。
セキュリティグループの概要
セキュリティグループの定義
セキュリティグループは、相互に信頼され、同じセキュリティ要件を共有する、同じリージョン内のインスタンスの論理的に分離されたグループです。 セキュリティグループルールは、セキュリティグループ内のエラスティックコンテナインスタンスのインターネットまたは内部ネットワークへのアクセスを制御します。
各セキュリティグループは、同じリージョン内の複数のエラスティックコンテナインスタンスを管理できます。
各弾性コンテナインスタンスは、単一のセキュリティグループに属している必要があります。
セキュリティグループの種類
セキュリティグループは、基本セキュリティグループと高度セキュリティグループに分類されます。 デフォルトでは、セキュリティグループの作成時に次のルールが追加されます。
ポート80、443、22、および3389でのアクセスを許可するインバウンドルール、およびすべてのポートでインターネット制御メッセージプロトコル (ICMP) を介したアクセスを許可するインバウンドルール。 これらのルールは変更できます。
すべてのポートですべてのアクセスを許可するアウトバウンドルール。
次の表に、基本セキュリティグループと高度セキュリティグループの機能の違いを示します。
機能 | ベーシックセキュリティグループ | アドバンストセキュリティグループ |
セキュリティグループにルールがない場合のアクセス制御ポリシー |
|
|
プライベートIPアドレスの最大数 | 2,000 | 65,536 |
同じセキュリティグループ内のインスタンス間の相互アクセス | デフォルトでは、同じセキュリティグループ内のインスタンスは、内部ネットワークを介して相互にアクセスできます。 | デフォルトでは、同じセキュリティグループ内のインスタンスは、内部ネットワークを介して相互に分離されます。 セキュリティグループルールを手動で追加して、インスタンスが内部ネットワークを介して相互にアクセスできるようにする必要があります。 |
他のセキュリティグループとのアクセスの制御 | ルールを追加して、他のセキュリティグループとのアクセスを制御できます。 | 他のセキュリティグループとのアクセスを制御するルールを追加することはできません。 |
ビジネスで多数の弾性コンテナインスタンスと高いO&M効率が必要な場合は、高度なセキュリティグループを使用することを推奨します。 基本的なセキュリティグループと比較して、高度なセキュリティグループはより柔軟なコンテナインスタンスに対応し、セキュリティグループルールの設定を容易にします。
セキュリティグループルール
セキュリティグループにルールを追加して、インバウンドトラフィックとアウトバウンドトラフィックを制御できます。 セキュリティグループルールは、方向、アクション、プロトコルタイプ、ポート範囲、許可オブジェクトなどの属性によって定義されます。 セキュリティグループルールに関する次の項目に注意してください。
各セキュリティグループのインバウンドルールとアウトバウンドルールの合計数は200を超えることはできません。
セキュリティグループルールを追加するときは、最小特権の原則に従います。 例:
ポート1 ~ 80のような80/80形式のポート範囲ではなく、ポート80などの1つのポートを1/80形式で指定します。
0.0.0.0/0 はすべての IP アドレスを示しています。 必要な場合を除き、認可オブジェクトとして設定しないでください。
詳細については、「概要」をご参照ください。
セキュリティグループの指定
エラスティックコンテナインスタンスを作成するときは、インスタンスのセキュリティグループを指定する必要があります。
エラスティックコンテナインスタンスのセキュリティグループは変更できません。 別のセキュリティグループ内でエラスティックコンテナインスタンスを使用するには、そのセキュリティグループ内に新しいエラスティックコンテナインスタンスを作成します。
Kubernetesクラスターのelasticコンテナインスタンスのセキュリティグループの指定
Kubernetesシナリオで仮想ノードに基づくElastic Container Instanceを使用すると、クラスター内のすべてのelastic container Instanceが、仮想ノードによって設定されたデフォルトのセキュリティグループに追加されます。 ビジネス要件に基づいて、エラスティックコンテナインスタンスのセキュリティグループを指定できます。
クラスター
kubectl editコマンドを実行して、クラスターのeci-profile ConfigMapを変更し、クラスター内のエラスティックコンテナインスタンスのdataセクションでデフォルトのセキュリティグループIDを変更できます。
説明仮想ノード2.0.0.90-15deb126e-aliyun以降では、ホットアップデート用にeci-profileを変更できます。 仮想ノードのバージョンが2.0.0.90-15deb126e-aliyunより前の場合は、仮想ノードをアップグレードすることを推奨します。
kubectl edit configmap eci-profile -n kube-systemdataセクションのsecurityGroupIdフィールドを変更します。 サンプルコード:
data: enableClusterIp: "true" enableHybridMode: "false" enablePrivateZone: "false" resourceGroupId: "" securityGroupId: sg-2ze0b9o8pjjzts4h**** # Specify a security group ID. selectors: "" vSwitchIds: vsw-2zeet2ksvw7f14ryz****,vsw-2ze94pjtfuj9vaymf**** vpcId: vpc-2zeghwzptn5zii0w7****elasticコンテナインスタンスのセキュリティグループの指定
ポッド設定のメタデータセクションにアノテーションを追加して、エラスティックコンテナインスタンスのセキュリティグループを指定できます。 サンプルコード:
apiVersion: apps/v1 kind: Deployment metadata: name: demo labels: app: nginx spec: replicas: 1 selector: matchLabels: app: nginx template: metadata: annotations: k8s.aliyun.com/eci-security-group: "sg-bp1dktddjsg5nktv****" # Specify a security group ID. labels: app: nginx spec: containers: - name: nginx image: nginx:latest
APIを呼び出してelasticコンテナインスタンスのセキュリティグループを指定する
CreateContainerGroup操作を呼び出してエラスティックコンテナインスタンスを作成する場合、SecurityGroupIdパラメーターを使用してセキュリティグループを指定できます。 次の表に、SecurityGroupIdパラメーターを示します。 詳細については、「CreateContainerGroup」をご参照ください。
パラメーター | データ型 | 例 | 説明 |
SecurityGroupId | String | sg-uf66jeqopgqa9hdn **** | セキュリティグループのID |
コンソールでelasticコンテナインスタンスのセキュリティグループを指定する
elastic container instanceコンソールのインスタンス購入ページでElastic Containerインスタンスを作成するときに、インスタンスのセキュリティグループを指定できます。
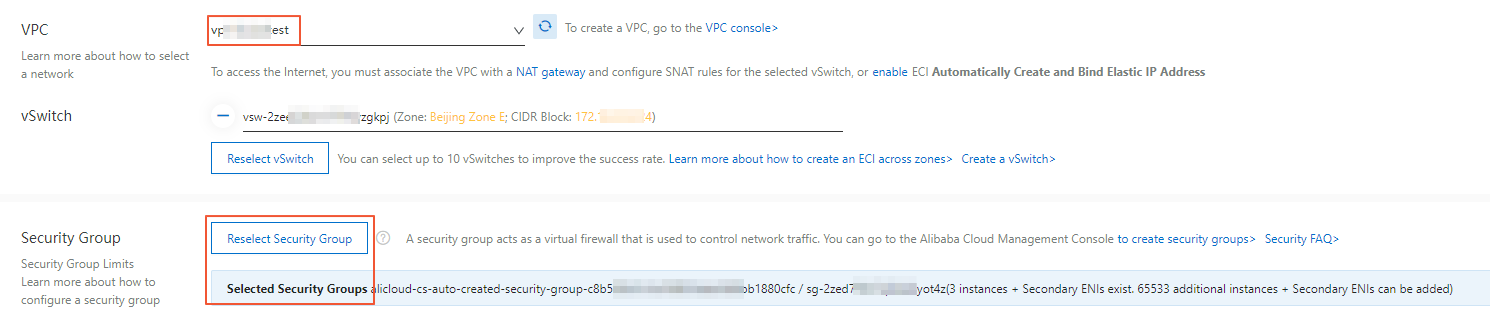
セキュリティグループルールの追加
セキュリティグループにルールを追加して、セキュリティグループ内のエラスティックコンテナインスタンスのインバウンドトラフィックとアウトバウンドトラフィックを制御できます。 例:
エラスティックコンテナインスタンスが属するセキュリティグループの外部のネットワークと通信する必要がある場合は、セキュリティグループルールを追加して、インスタンスがネットワークにアクセスできるようにする必要があります。
リクエストソースによる攻撃が検出された場合、セキュリティグループルールを追加して、リクエストソースからのアクセスをブロックできます。
セキュリティグループルールの追加方法の詳細については、「セキュリティグループルールの追加」をご参照ください。