オープンソースのKubernetesでkubeletが使用する安全でない読み取り専用ポート10255は、ポッドとコンテナーを悪意のある攻撃にさらします。 セキュリティリスクを軽減するために、Container Service for Kubernetes (ACK) は、Kubernetes 1.26以降を実行するACKクラスターで、デフォルトでkubeletの読み取り専用ポート10255を開きません。 代わりに、認証ポート10250が開かれ、kubeletによって使用される。
リスク免責事項
攻撃者はノードに侵入し、kubeletの読み取り専用ポート10255を利用して、ノード上のアプリケーションに関する情報を取得できます。 この結果、情報が漏洩する。 この問題を解決するために、Kubernetes 1.26以降を実行するACKクラスターでは、デフォルトでkubeletの読み取り専用ポート10255は開きません。 代わりに、認証ポート10250が開かれ、kubeletによって使用される。
クラスターが1.26より前のバージョンのKubernetesを実行している場合は、このトピックの手順に従って、関連するモニタリングコンポーネントを更新し、kubeletの読み取り専用ポート10255を手動で閉じることを推奨します。 詳細については、「関連するモニタリングコンポーネントを更新し、kubeletの読み取り専用ポート10255を手動で閉じる」をご参照ください。
ポート10255が使用中の場合、またはアプリケーションで使用される場合は、潜在的なセキュリティリスクを評価することを推奨します。 Kubernetes 1.26以降では、kubeletパラメーターを変更してポート10255を開くことができます。 詳細については、「kubeletの読み取り専用ポート10255を手動で開く」をご参照ください。
影響範囲
1.26より前のバージョンのKubernetesを実行するACKクラスターは、クラスター内のkubeletがポート10255を使用するか、またはポート10255を使用する場合に影響を受けます。
kubeletの読み取り専用ポート10255を更新し、手動で閉じます。
クラスターの元のKubernetesバージョンが1.26より前の場合、関連するモニタリングコンポーネントを更新し、クラスター内のkubeletの読み取り専用ポート10255を手動で閉じることを推奨します。
注意事項
クラスターに仮想ノード (ack-virtual-node) が含まれている場合、または1.26より前のバージョンのKubernetesを実行するACKサーバーレスクラスターを使用している場合、チケットを起票するを起票し、テクニカルサポートに連絡してポート10255を終了します。
手順
にログインします。ACKコンソールをクリックし、クラスター左側のナビゲーションウィンドウに表示されます。
On theクラスターページで、管理するクラスターの名前をクリックし、左側のナビゲーションウィンドウに表示されます。
関連するコンポーネントを見つけて更新します。
メトリクス-serverを0.3.9.4-ff225cd-aliyun以降に更新します。 metrics-serverがクラスターにインストールされていない場合、操作は必要ありません。
ack-arms-prometheusがインストールされている場合は、コンポーネントを1.1.15以降に更新します。 ack-arms-prometheusがクラスターにインストールされていない場合、操作は必要ありません。
説明この更新により、クラスターのモニタリングパフォーマンスが低下したり、アプリケーションに影響したりすることはありません。
左側のナビゲーションウィンドウで、 を選択します。 ノードプールリストで、次の手順を実行して、すべてのクラスターノードのポート10255を閉じます。
ノードプールの [操作] 列で、 を選択します。
[カスタムパラメーター] セクションで、readOnlyPortを
0に設定し、[送信] をクリックしてポート10255を閉じます。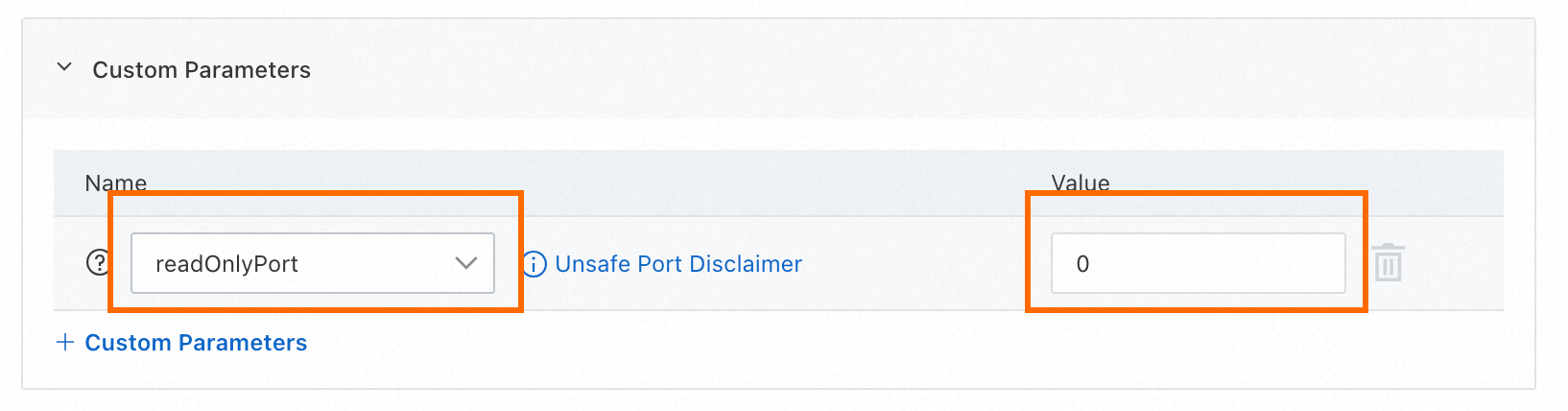
重要ポート10255を閉じるときは、ノード上のkubelet構成ファイル
/etc/kubernetes/kubelet-customized-args.confを手動で変更しないでください。 ACKコンソールのkubelet設定は、kubelet設定ファイルを自動的に上書きします。
kubeletの読み取り専用ポート10255を手動で開く
ポート10255が使用中の場合、またはアプリケーションで使用される場合は、潜在的なセキュリティリスクを評価することを推奨します。 Kubernetes 1.26以降では、kubeletパラメーターを変更してポート10255を開くことができます。
手順
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
On theクラスターページで、管理するクラスターの名前をクリックし、左側のナビゲーションウィンドウに表示されます。
ノードプールの [操作] 列で、次の手順を実行して、すべてのクラスターノードでポート10255を開きます。
ノードプールの を選択します。
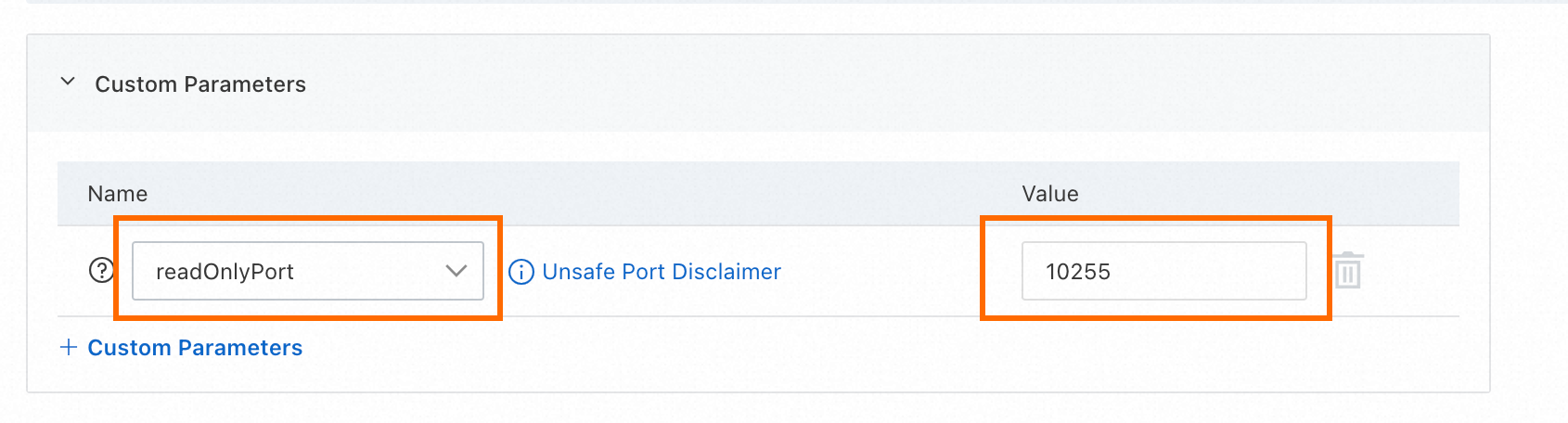
[カスタムパラメーター] セクションで、readOnlyPortを
10255に設定し、[送信] をクリックしてポート10255を開きます。