For companies with a complex organizational structure and many cloud computers, it is crucial to create sub-administrators to assist the main administrator with management tasks. However, according to the least privilege principle in information security best practices, it is not secure to simply grant each sub-administrator full feature and data permissions. This topic describes how to use the permission management module in Elastic Desktop Service (EDS) to isolate the feature and data permissions across sub-administrators.
Scenario
The Alibaba Cloud account that you use to log on to the EDS console has full permissions on EDS features and resources. If your company has a complex organizational structure, multiple departments, and a large number of employees and cloud computers, one administrator is not sufficient to manage all tasks. Additionally, having only one administrator does not meet the permission isolation requirements for business. In this scenario, the main administrator needs one or more sub-administrators to help manage tasks. In this situation, the following requirements must be met:
Different sub-administrators have varying levels of permissions. For example, Sub-administrator A can create and manage users but cannot create and manage cloud computers, while Sub-administrator B can only view data and cannot perform any other operations.
Access to different data is restricted to specific permissions. For example, Sub-administrator C has permissions to view and manage only cloud computers in the R&D department, while Sub-administrator D has permissions to view and manage only cloud computers in the design department.
Solution
The permission management module provided by EDS can meet the preceding requirements.

The permission management module enforces permission isolation across the following dimensions:
Employee dimension: Sub-administrators can be created, with their permissions on features determined by their roles and their permissions on data determined by the resource groups they manage.
Feature dimension: Default roles are available for use, and custom roles can also be created. A role is a set of permissions that define which feature modules that a user is allowed to access and which actions that a user is allowed to perform, which helps enforce feature permission control. EDS provides the following default roles:
Super administrator: a role with full permissions to access and manage all cloud resources and features. Only the super administrator can create and manage other administrator roles.
System administrator: a role with permissions to manage cloud resources, authorize access to resources, monitor system status, and execute O&M tasks. A system administrator cannot create or manage users.
Security audit administrator: a role with permissions to view data. A security audit administrator cannot access feature modules.
Security administrator: a role with permissions to create and manage users and monitor the status of security information processing. A security administrator cannot manage cloud resources.
Data dimension: Resource groups are supported as a way to isolate permissions. A resource group is a container for cloud computer resources, and helps enforce permission isolation.
The following table describes the solutions for meeting the preceding sample requirements.
Requirement | Solution |
|
|
|
|
Create a role
In addition to using a default role, you can also create custom roles that align with your business needs. Then, you can attach the custom roles to sub-administrators to enforce feature permission isolation.
Log on to the Elastic Desktop Service Enterprise console.
In the left-side navigation pane, choose . On the Administrator Permissions page, click the Role tab.
On the Role tab, click Create Role, configure the following parameters, and then click OK.
Name: Enter a name for the role.
Parent Role: Select a default role as the parent role for the role you want to create.
After you select the parent role, all the permissions of the parent role are loaded in the Configure Permission section, which helps you complete role authorization.
Description: Enter a description for the role to better distinguish it from other roles. This parameter is optional.
What to do next
A newly created role will be displayed on the Role tab.
If you want to modify a custom role, find the role on the Role tab and click Edit in the Actions column.
If you want to delete a custom role, find the role on the Role tab and click Delete in the Actions column.
Create a resource group
You can create resource groups and add cloud computers to the resource groups for management. Subsequently, you can grant the permissions on different resource groups to different sub-administrators, which helps enforce data permission isolation.
In the left-side navigation pane, choose
On the Resource Groups page, click Create Resource Group and enter a name for the resource group that you want to create.
NoteThe name must be 1 to 30 characters in length. It must start with a letter but cannot start with
http://orhttps://. It can contain letters, digits, colons (:), underscores (_), periods (.), and hyphens (-).In the Configure Resources and Authorize message, click Go Now.
On the Manage Resource tab, click Transfer In. In the Transfer In panel, select the cloud computers that you want to add to the group and click Confirm.
What to do next
A newly created resource group will be displayed on the Resource Groups page.
If you want to grant or reclaim permissions on a resource group to or from sub-administrators, find the resource group on the Resource Groups page and click Manage Authorization in the Actions column. On the Manage Authorization tab, click Authorize Administrator to grant or reclaim permissions based on your business requirements.
NoteIf you want to grant permissions on the resource group to a sub-administrator that does not exist, you can click Create Administrator in the lower part of the administrator list.
If you want to add or remove resources to or from a resource group, find the resource group on the Resource Groups page and click Manage Resource in the Actions column.
NoteOn the Manage Resource tab, click the icon in the User column, select Users Unassigned Resource, and then click OK. The idle resources are filtered out.
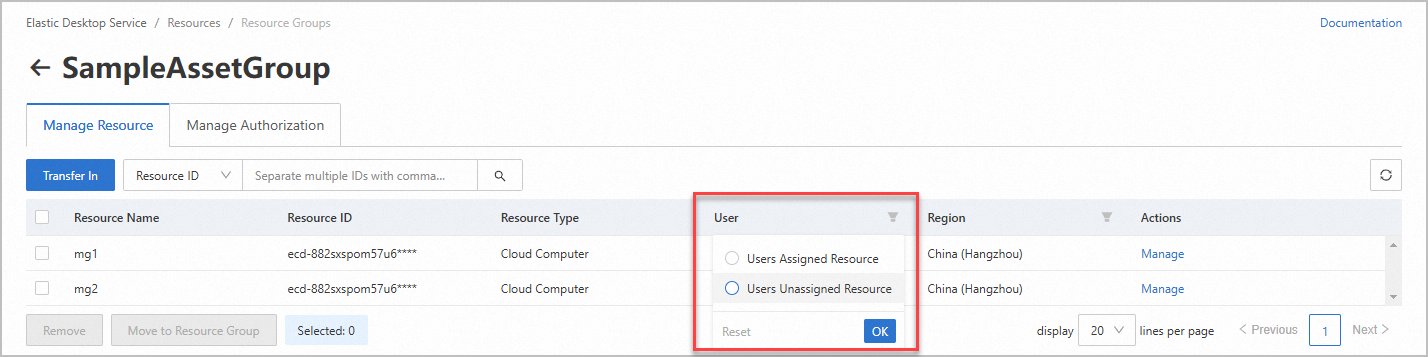
If you want to modify the name of a resource group, find the resource group on the Resource Groups page and click Edit in the Actions column.
If you want to delete a resource group, find the resource group on the Resource Groups page and click Delete in the Actions column.
Create a sub-administrator and configure the authorization scope
When you create a sub-administrator, you can enforce feature permission isolation by attaching a role to it, and enforce data permission isolation by granting resource group or resource type permissions to it.
In the left-side navigation pane, choose .
On the Administrator Permissions page, click Create Administrator, configure the following parameters, and then click OK.
Associate with RAM User: the Resource Access Management (RAM) user that the sub-administrator uses to log on to the EDS console to complete management tasks. Associate a RAM user with a sub-administrator by using one of the following methods:
Select a RAM user that exists in the current Alibaba Cloud account: Click Existing RAM Users and select a RAM role from the drop-down list.
Create a new RAM user: Click Create RAM User. On the RAM Quick Authorization page, click Authorize.
NoteThe name and initial password of the RAM user are sent to the sub-administrator by the specified email address or mobile number.
Nickname: the display name of the sub-administrator.
Role: the default or custom role that the sub-administrator plays. The role defines the permissions granted to the sub-administrator.
Email Address: the email address of the sub-administrator, which is used to receive the logon credentials of the RAM user.
Mobile Number: the mobile number of the sub-administrator, which is used to receive the logon credentials of the RAM user. This parameter is optional.
On the Administrator tab, find the newly created sub-administrator and click Manage Authorization in the Actions column.
In the Manage Authorization panel, configure the authorization scope and click Confirm. You can grant permissions based on resource types and resource groups. The final scope of authorization is the combination of the two dimensions.
Resource Type: You can select Cloud Computer or User.
ImportantAfter you select a specific type of resource for the sub-administrator, the sub-administrator will have full management permissions for that type of resource, including any future resources of the same type. For example, if you select Cloud Computer, the sub-administrator has management permissions for all cloud computers in the current Alibaba Cloud account, including cloud computers that will be purchased in the future.
Available Resource Group: In the Available Resource Group section, select the resource group whose permissions you want to grant to the sub-administrator and click the icon to move it to the Authorized Resource Group section.
EDS Enterprise and Cloud Phone use the same tiered access control module. Therefore, grant permissions in either product console and the change applies to both products.
What to do next
A newly created sub-administrator will be displayed on the Administrator tab of the Administrator Permissions page.
If you want to change the RAM role attached to a sub-administrator, find the sub-administrator on the Administrator tab and click Modify RAM User in the Actions column.
If you want to modify the authorization scope of a sub-administrator, find the sub-administrator on the Administrator tab and click Manage Authorization in the Actions column.
If you want to modify the basic information about a sub-administrator, such as the nickname, role, email address and mobile number, find the sub-administrator on the Administrator tab and click Edit in the Actions column.
If you want to delete a sub-administrator, find the sub-administrator on the Administrator tab and click Delete in the Actions column.
Log on to the EDS console as a sub-administrator
A sub-administrator can obtain the logon credentials to the EDS console by either email address or text message.
Go to the RAM User Logon page.
In the Username text box, enter the obtained username and click Next.
Sample username:
AU-492b4a18-****-****-****-****@1161219343******.onaliyun.comIn the Password text box, enter the obtained initial password and click Log On.
Sample password:
AP:269fa57f-34c6-4818-af98-bccb7fb6****(Conditional) The first time you visit the RAM User Logon page, reset the user password as prompted.
The new password is required for future logons.
Log on to the Elastic Desktop Service Enterprise console.