This topic describes troubleshooting methods and solutions for SSL certificates that are ineffective after deployment or websites that display as insecure.
Browser displays "Your connection to this site is not secure"
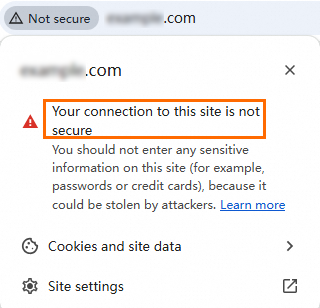
Possible causes: Browser cache not cleared, SSL certificate does not match the domain name, or the certificate has expired.
Solutions:
Clear the browser cache and then try to access your website again.
Check whether the SSL certificate matches the domain name.
Method 1: View through the digital certificate management service console
Log on to the Certificate Management Service console.
In the left-side navigation pane, choose Certificate Management > SSL Certificate Management.
On the SSL Certificate Management page, locate the certificate you deployed and check whether the domain name of the certificate matches the domain name of the site. If they do not match, re-upload the certificate that corresponds to the domain name.
Method 2: View through the browser
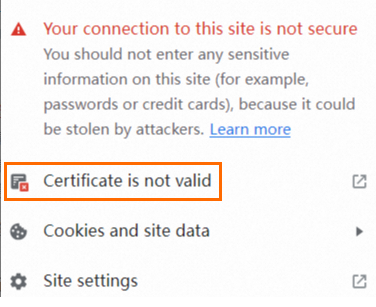
Access the domain name of the website and click the security lock in the address bar of the browser.
Click Certificate Invalid.
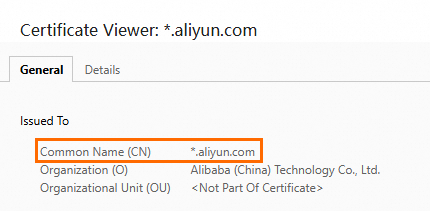
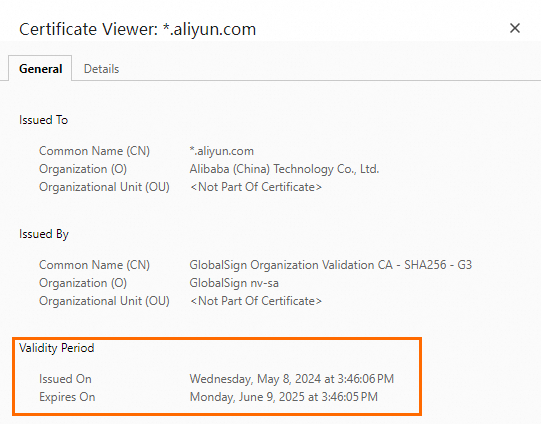
On the certificate page, check whether the Common Name (CN) of the certificate matches the domain name of the website.
Check whether the SSL certificate has expired.
The default validity period of a certificate is one year. If the certificate is not installed for the first time, check whether the certificate has expired when you access the website over HTTPS and an error occurs indicating that the connection is not secure. You can use one of the following methods to perform the check.
Method 1: View through the digital certificate management service console
Log on to the Certificate Management Service console.
In the left-side navigation pane, choose Certificate Management > SSL Certificate Management.
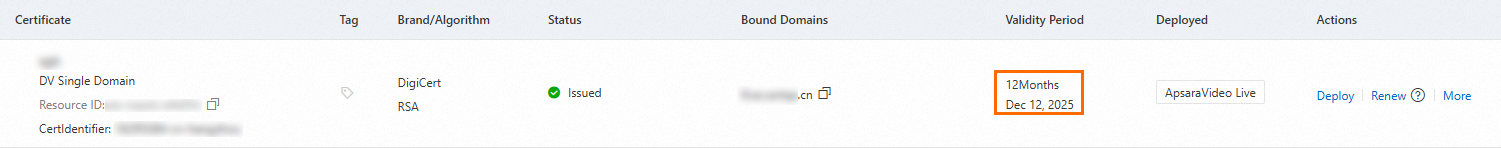
On the SSL Certificate Management page, locate the certificate you deployed and check whether it has expired.
If the certificate has expired, renew it in a timely manner. For specific operations, see Renewal of official SSL certificates.
Method 2: View through the browser
Access the domain name of the website and click the security lock icon in the address bar of the browser.
Click Certificate Invalid.

On the certificate page, view the expiration time of the certificate.
Check whether the format of the deployed SSL certificate is incorrect.
Different web servers support different certificate formats. For more information, see Deploy SSL certificates.
Possible cause: The certificate path or certificate file name in the configuration file is incorrect.
Solutions:
Check the SSL certificate settings in the web server configuration file to ensure that the certificate storage path and file name specified in the configuration file are exactly the same as the actual certificate path and file name on the server. The following is a configuration example for Nginx:
server {
listen 443 ssl;
server_name example.com;
# Please replace the following paths with your own SSL certificate and private key file paths
ssl_certificate /etc/nginx/ssl/example.com.crt;
ssl_certificate_key /etc/nginx/ssl/example.com.key;
# Other configurations...
}Possible cause: A new certificate was purchased, but the web server is still using the old certificate or the SSL certificate path in the configuration file was not updated in a timely manner.
Solutions:
By creating a deployment task, you can upload the issued certificate to the specified path of the cloud server or replace the certificate file in the specified path. For specific operations, see Manually deploy certificates to Alibaba Cloud Simple Application Server or ECS.
Browser displays "This page cannot be accessed"
Possible cause: Port 443 is not allowed.
Solutions:
If you are using an Alibaba Cloud ECS instance, go to the ECS console security group page to allow port 443. For more information about how to configure security groups, see Add security group rules.
NoteWhen you access a website by using the default port number, you can directly enter the domain name by using HTTP (default port 80) or HTTPS (default port 443). If you use a non-default port, you must append the port number to the domain name in the format of
http://domain name:port numberorhttps://domain name:port number.Ensure that the server allows connections over HTTPS on the default port 443. If you use a non-standard port, check whether the port is open and not occupied by other services.
If you have configured a firewall, check the firewall settings of the server itself to ensure that they do not block external access to port 443.
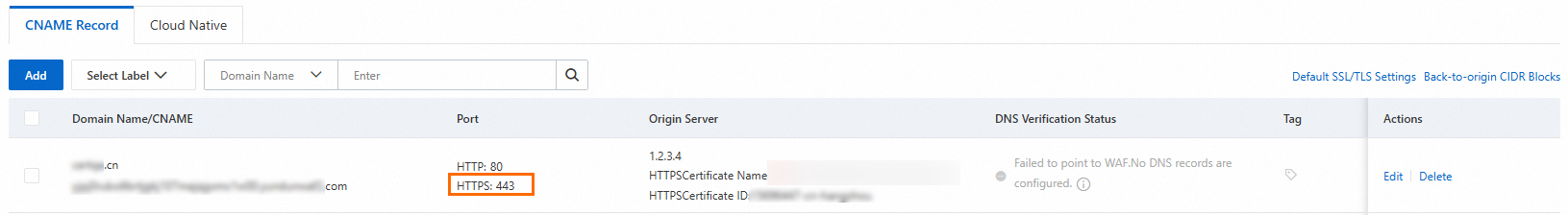
If your website is not hosted on an Alibaba Cloud ECS instance, refer to the documentation of the server that hosts the website and follow the related instructions to allow traffic over port 443.
Possible cause: Web server configuration error.
Solutions:
Check the configuration file of the web server to ensure that it correctly sets the SSL/TLS-related instructions and listens on port 443.
Check whether the configuration file contains syntax errors.
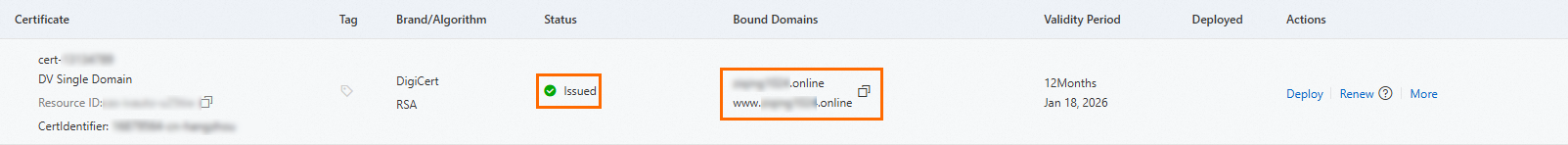
Possible cause: The SSL certificate has expired or was not correctly issued.
Solutions:
Check whether the certificate has expired. If the certificate has expired, renew it in a timely manner. For specific operations, see Renewal of official SSL certificates.

Check whether the certificate was correctly issued and matches your domain name.
Possible cause: DNS resolution issue.
Solutions:
Ensure that your domain name correctly points to the IP address of the server. You can use the
pingornslookupcommand to check whether the domain name can be correctly resolved to an IP address.If you are using a CDN service, ensure that the CDN settings are correct and do not block HTTPS traffic.
If the preceding steps cannot resolve the issue, we recommend that you carefully check the web server and application log files for more detailed information. Additionally, try accessing the website from different devices or locations to rule out issues specific to the local network or device. For further assistance, contact your business manager.
Browser displays "Unsupported protocol used"
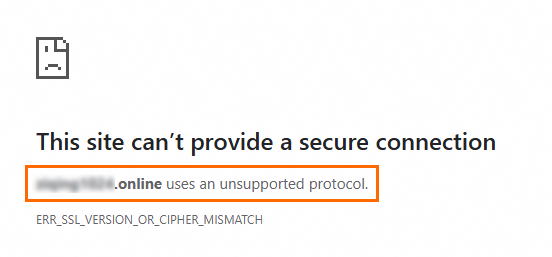
Possible cause: Your web server may be using an insecure protocol version (such as SSL 2.0, SSL 3.0, TLS 1.0, or TLS 1.1), or the TLS protocol configured on the web server is inconsistent with the TLS protocol supported by the operating system.
Solutions:
Use a more secure protocol version in the web server configuration file, such as TLS 1.2 or TLS 1.3. The following example demonstrates how to set the supported SSL/TLS protocol versions in the configuration file for Nginx. Make sure that your client supports the TLS versions that you want to specify. Otherwise, connection failures may occur.
server { listen 443 ssl; server_name yourdomain.com; # The paths to the certificate and private key files ssl_certificate /path/to/your_certificate.crt; ssl_certificate_key /path/to/your_private.key; # Specify the TLS versions that you want the certificate to support ssl_protocols TLSv1.2 TLSv1.3; # Optional. Specify a cipher suite that provides higher security ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256'; location / { root /var/www/html; index index.html index.htm; } }Ensure that the cipher suite used by the server is consistent with the TLS protocol supported by the operating system. You can configure the operating system accordingly. The method to set the TLS protocol varies based on the operating system. The following steps describe how to configure the TLS protocol on Windows operating systems.
Open the Control Panel and click Network And Internet.
In the Network And Internet panel, click Internet Options and then click Advanced.
Select to enable TLS 1.2 or TLS 1.3 to provide better security and compatibility.
Browser displays "Some content on this page is not secure (such as images)" or external resources (images, scripts, styles, etc.) cannot be loaded successfully
Possible cause: HTTP resources are referenced in the code of your website.
Solutions:
Update all HTTP resources to HTTPS to ensure that all external resources (images, scripts, styles, etc.) can be loaded over the HTTPS protocol.
If the resources are under the same domain name as your website, you can use relative URLs so that the browser automatically uses the protocol (HTTP or HTTPS) of the current page to load the resources.
Check whether third-party resources support HTTPS, or directly remove the references to related HTTP resources. After deployment and publication, access the website again.
The implementation logic varies based on the website code. Change the protocol based on your business requirements. For questions, contact your business manager.