Security Center is a security management system that dynamically identifies and analyzes security threats, and generates alerts when threats are detected. You can use Security Center to ensure the security of your cloud resources and local servers in a centralized manner and meet regulatory compliance requirements. You can configure the alert ingestion system of Simple Log Service as a notification method in the Security Center console. This way, Security Center alerts can be ingested into Simple Log Service. Then, the alerting system of Simple Log Service denoises the alerts and sends alert notifications.
Prerequisites
An alert ingestion application is created. The Protocol parameter of the alert ingestion application is set to Security Center. For more information, see Configure webhook URLs for alert ingestion.
Security Center of the Enterprise edition is purchased. For more information, see Purchase Security Center.
Configure an alert notification method in the Security Center console
Log on to the Security Center console.
In the left-side navigation pane, click Settings.
In the DingTalk Chatbot Notification Settings section of the Notifications tab, click Add Chatbot.
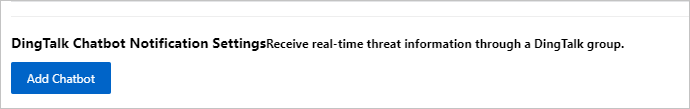
In the Add DingTalk Chatbot panel, set the parameters and click Add.
Set the Webhook URL parameter to the full path of the Internet webhook URL that is generated after you create an alert ingestion application. For more information, see Obtain webhook URLs. For information about other parameters, see Add a DingTalk chatbot.
Security Center alert parsing
Security Center generates alerts when vulnerabilities, baseline risks, security events, and AccessKey pair leaks are detected. The following tables describe the fields in different types of alerts.
Alerts for vulnerabilities
Field
Description
Mapping relationship with Simple Log Service
instanceName
The name of the instance that is protected by Security Center, for example, the name of an Elastic Compute Service (ECS) instance.
The instanceName field is mapped to the labels field in the alerts that are supported by Simple Log Service.
instanceId
The ID of the instance that is protected by Security Center, for example, the ID of an ECS instance.
The instanceId field is mapped to the labels field in the alerts that are supported by Simple Log Service.
alias_name
The alias of the vulnerability.
The alias_name field is mapped to the labels field in the alerts that are supported by Simple Log Service.
internetIp
The IP address.
The internetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
intranetIp
The internal IP address.
The intranetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
uuid
The universally unique identifier (UUID) of the server.
The uuid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
aliUid
The ID of the associated Alibaba Cloud account.
The aliUid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
time
The time when the alert is triggered.
The time field is mapped to the alert_time and fire_time fields in the alerts that are supported by Simple Log Service.
Alerts for baseline risks
Field
Description
Mapping relationship with Simple Log Service
instanceName
The name of the instance that is protected by Security Center, for example, the name of an ECS instance.
The instanceName field is mapped to the labels field in the alerts that are supported by Simple Log Service.
instanceId
The ID of the instance that is protected by Security Center, for example, the ID of an ECS instance.
The instanceId field is mapped to the labels field in the alerts that are supported by Simple Log Service.
type_alias
The alias of the check type in Chinese.
The type_alias field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
risk_name
The name of the risk.
The risk_name field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
internetIp
The IP address.
The internetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
intranetIp
The internal IP address.
The intranetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
uuid
The UUID of the server.
The uuid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
aliUid
The ID of the associated Alibaba Cloud account.
The aliUid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
time
The time when the alert is triggered.
The time field is mapped to the alert_time and fire_time fields in the alerts that are supported by Simple Log Service.
Alerts for security events
Field
Description
Mapping relationship with Simple Log Service
instanceName
The name of the instance that is protected by Security Center, for example, the name of an ECS instance.
The instanceName field is mapped to the labels field in the alerts that are supported by Simple Log Service.
instanceId
The ID of the instance that is protected by Security Center, for example, the ID of an ECS instance.
The instanceId field is mapped to the labels field in the alerts that are supported by Simple Log Service.
instanceId
machineIp
The IP address of the machine.
The machineIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
internetIp
The IP address.
The internetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
intranetIp
The internal IP address.
The intranetIp field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
uuid
The UUID of the server.
The uuid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
aliUid
The ID of the associated Alibaba Cloud account.
The aliUid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
groupId
The ID of the asset group.
The groupId field is mapped to the labels field in the alerts that are supported by Simple Log Service.
event_type
The type of the alert.
The event_type field is mapped to the alert_name field in the alerts that are supported by Simple Log Service.
event_name
The name of the alert.
The event_name field is mapped to the annotations and title fields in the alerts that are supported by Simple Log Service.
op
The action that is performed on a security event. Valid values:
new: detects a new security event.
fix: fixes a security event.
verify: verifies a security event.
The op field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
status
The status of the security event. For more information, see Security event status.
The status field is mapped to the annotations field in the alerts that are supported by Simple Log Service.
time
The time when the alert is triggered.
The time field is mapped to the alert_time and fire_time fields in the alerts that are supported by Simple Log Service.
The following table describes the status of security events.
Valid value of status
Description
Alert status in Simple Log Service
Pending
Pending
firing
Handled
Confirmed
firing
Dealing
Processing
firing
Auto Dealing
Automatic blocking
firing
Ignore
Ignored
resolved
Fault
Marked as false positives
resolved
Done
Processed
resolved
Expire
Expired
resolved
Deleted
Deleted
resolved
Auto Dealing Done
Automatic blocking completed
resolved
Alerts for AccessKey pair leaks
Field
Description
Mapping relationship with Simple Log Service
github_user
The GitHub account that is leaked.
The github_user field is mapped to the labels field in the alerts that are supported by Simple Log Service.
github_file
The GitHub file that is leaked.
The github_file field is mapped to the labels field in the alerts that are supported by Simple Log Service.
source
The source of the leak.
The source field is mapped to the labels field in the alerts that are supported by Simple Log Service.
github_repo
The GitHub repository that is leaked.
The github_repo field is mapped to the labels field in the alerts that are supported by Simple Log Service.
accesskey_id
The AccessKey pair that is leaked.
The accesskey_id field is mapped to the labels field in the alerts that are supported by Simple Log Service.
aliUid
The ID of the associated Alibaba Cloud account.
The aliUid field is mapped to the labels field in the alerts that are supported by Simple Log Service.
time
The time when the alert is triggered.
The time field is mapped to the alert_time and fire_time fields in the alerts that are supported by Simple Log Service.
Field mappings
The following table describes the mappings between the alert attributes of Simple Log Service and the alert fields of Security Center.
Simple Log Service | Security Center | Description |
aliuid | None | The ID of the Alibaba Cloud account to which the alert ingestion application belongs. |
alert_id | None | The ID of the alert monitoring rule. |
alert_type | None | The type of the alert. Valid value: sls_pub. |
alert_name | event_type | The name of the alert monitoring rule. |
status | status | The status of the alert. Valid values: firing and resolved. The status of each security event in Security Center is mapped to the status of the corresponding alert in Simple Log Service. For more information, see Security event status. |
next_eval_interval | None | The interval at which the alert is evaluated. Valid value: 0. |
alert_time | time | The time when the alert is evaluated. |
fire_time | time | The time when the first alert is triggered. |
resolve_time | None | The time when the alert is cleared.
|
labels | instanceName, instanceId, accountName, aliUid, and uuid | The labels of the alert. The following fields are included:
If you add a label on the Enrichment tab when you create the alert ingestion application, the label is added to the labels field. |
annotations | status, internetIp, intranetIp, machineIp, op, and event_name | The annotations of the alert. The following fields are included: status, internetIp, intranetIp, machineIp, op, and title. The title field is mapped to the event_name field. The following fields are also added to the annotations field:
If you add an annotation on the Enrichment tab when you create the alert ingestion application, the annotation is added to the annotations field. |
severity | event level | The severity of the alert.
|
policy | None | The alert policy that is specified for the alert ingestion application. For more information, see Description of the policy variable. |
project | None | The project to which Alert Center belongs. For more information, see Project. |
drill_down_query | None | The value is a link. The link contains the URL of a Security Center alert. You can click the link to go to the corresponding page that shows the Security Center alert. |