If the Security Center agent installed on your server is in the Offline state, the server is not protected by Security Center, and the server may be attacked. We recommend that you refer to this topic to troubleshoot why the Security Center agent is offline at the earliest opportunity.
Background information
Security Center provides the agent troubleshooting feature. If the Security Center agent on your server is offline, we recommend that you use this feature to troubleshoot the issue. For more information, see Use the agent troubleshooting feature.
Procedure
Log on to your server and check whether the
AliYunDunandAliYunDunUpdateprocesses of the Security Center agent run as expected on your server.NoteIf a process does not run as expected, we recommend that you restart the server or reinstall the Security Center agent on the server. For more information, see Install the Security Center agent.
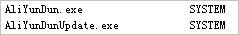
Windows server
Open Task Manager and check whether the processes run as expected.
Linux server
Run the
ps aux | grep AliYunDuncommand and check whether the processes run as expected.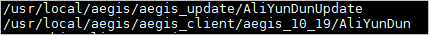
If the protection status of your server is Unprotected the first time that you install the Security Center agent on your server, perform the following operations to restart the agent:
If your server is a Linux server, run the following commands:
killall AliYunDun killall AliYunDunUpdate /usr/local/aegis/aegis_client/aegis_10_xx/AliYunDunNoteIn the third command, replace
xxwith the greatest number among the numbers at the end of the files whose names are in the aegis_10_xx format. The greatest number indicates the latest version of the Security Center agent. You can view the files whose names are in the aegis_10_xx format in the /usr/local/aegis/aegis_client directory. For example, if the directory contains aegis_10_70, aegis_10_73, and aegis_10_75, you must replacexxin the third command with75.If your server is a Windows server, find and select the
Alibaba Security Aegis Detect ServiceandAlibaba Security Aegis Update Serviceservices of Security Center in the service list, right-click the services, and then select Restart.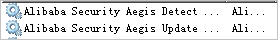
Run a ping command on your server to check whether the network connection on your server is normal. If the IP address of your server is returned after you run a ping command on your server, the network connection is normal. The command that you can run varies based on the operating system of the server and whether the server has a public IP address.
The server has a public IP address such as a classic network IP address or an elastic IP address (EIP).
For a Windows server, run the
ping jsrv.aegis.aliyun.com -l 1000command.For a Linux server, run the
ping jsrv.aegis.aliyun.com -s 1000command.
The server does not have a public IP address. For example, the server is deployed on a virtual private cloud (VPC) or Alibaba Finance Cloud.
For a Windows server, run the
ping jsrv2.aegis.aliyun.com -l 1000command.For a Linux server, run the
ping jsrv2.aegis.aliyun.com -s 1000command.
If the ping command fails to run, perform the following operations to check whether the network connection on your server is normal:
Check whether the Domain Name System (DNS) service runs as expected on your server. If the DNS service does not run as expected, restart your server or check whether an error occurred on the DNS service.
Check whether access control policies in Cloud Firewall or security group rules are configured for your server. If an access control policy or a security group rule is configured for your server, make sure that an outbound policy is created to allow access from the IP address of Security Center to the Internet. You do not need to create an inbound policy. For more information about how to configure a security group rule, see Create a secueity group. For more information about how to configure an access control policy in Cloud Firewall, see Create inbound and outbound access control policies for the Internet firewall.
NoteAllow inbound and outbound traffic of the CIDR blocks that contain 100.100, 106.11, and 100.103 on all ports or on ports 80 and 443.
If a valid IP address is returned, run a telnet command to connect to the IP address on port 80. If the connection fails, check whether the connection request is blocked by a firewall.
Check whether the CPU utilization or memory usage of your server remains high for a long period of time. For example, the CPU utilization of 95% or the memory usage of 100% is considered high. High CPU utilization or memory usage may cause the Security Center agent to fail to work.
Check whether third-party security software is installed on your server. Third-party security software may prevent the Security Center agent from establishing network connections.
If third-party security software is installed, we recommend that you stop the software and reinstall the Security Center agent.