Sensitive information leaks may cause significant business loss. To prevent users from leaking sensitive information in special office scenarios, such as screen snapshot capture, screen photo taking, and printing, we recommend that you use the data loss prevention (DLP) feature of Secure Access Service Edge (SASE) to enable screen watermarks and application watermarks. This allows you to use visible watermarks as a deterrent against sensitive information leaks and use invisible watermarks to trace the source of leaks. This topic describes how to configure a watermark policy, view the detection results of sensitive behaviors, and configure a watermark whitelist.
Prerequisites
Internet Access DLP of SASE is purchased. For more information, see Billing overview.
Users and user groups are added. For more information, see Connect an LDAP IdP to SASE and Configure a user group.
Configure policies for screen watermarks and application watermarks
Log on to the SASE console.
In the left-side navigation pane, choose .
Click the Watermark Management tab. On the Screen Watermark or Application Watermark tab, click Create Policy.
In the Create Policy panel, configure parameters. The following table describes the parameters.
Parameter
Description
Basic Information
Policy Name
The name of the policy.
The name must be 2 to 32 characters in length and can contain letters, digits, hyphens (-), and underscores (_).
Status
The status of the policy. Valid values: Enabled or Disabled.
The policy takes effect only when it is enabled.
Priority
The priority of the policy.
Valid values: 1 to 100. A smaller value indicates a higher priority.
User Group
The users or user groups to which the policy is applied.
If you specify a user or user group in a screen watermark policy and a printer watermark policy, both policies are applied to the user or user group.
Applicable Application
The applications to which the policy is applied. You must specify this parameter when you create an application watermark policy.
Before you configure applicable applications, you must enable the web application access reinforcement feature for corresponding office applications.
Watermark Settings
Visible Watermark
The settings of the visible watermark. Configure the settings based on your business requirements. You can turn on Preview to preview the settings of the visible watermark.
We recommend that you increase the opacity to the maximum value to ensure that the watermark is clearly visible.
Invisible Watermark
The settings of the invisible watermark. Configure the settings based on your business requirements.
Click OK.
After the policy is created, the policy is displayed in the policy list.
Extract invisible watermark information
If you configured an invisible watermark, you can perform the following operations to extract the information about the invisible watermark.
Go to the tab and select a watermark type.
Upload the file that contains the invisible watermark as prompted.
After the file is uploaded, the invisible watermark is automatically extracted.
To export the extraction results, click Export on the right side of the page.
View the results of sensitive behavior detection
If a user performs a print operation, sensitive behavior detection is triggered. DLP automatically detects files printed by users and analyzes the data in the last 30 days, 7 days, and 24 hours based on the detection results.
In the left-side navigation pane, choose .
On the Sensitive Behavior Detection page, view the statistics of files printed by users within the specified time range.
In the list in the lower part of the page, find the user that you want to query and click Details in the Actions column to view the details of the printed files.
Find the file that you want to query, click Details in the Actions column, and then view the sensitive message, hit policy, office terminal, and outbound transfer channel of the file.
Configure a watermark whitelist
If you want SASE not to audit and manage the sensitive behaviors of specific users, you can configure a watermark whitelist to allow specific users to perform sensitive operations.
On the Watermark Management tab, click Watermark Whitelist.
On the tab, add users to the screen watermark whitelist and the application watermark whitelist.
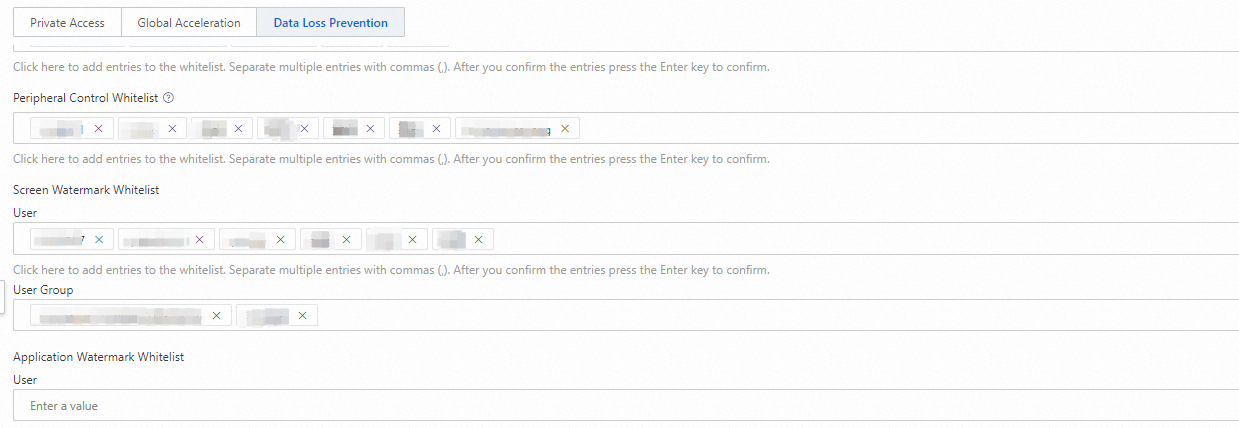
Click Submit.
Adjust the priority of a policy
If you want to adjust the priority of a watermark policy, click the  icon on the Watermark Management page to change the priority value. Valid values: 1 to 100. A smaller value indicates a higher priority.
icon on the Watermark Management page to change the priority value. Valid values: 1 to 100. A smaller value indicates a higher priority.

Disable a policy
If you do not require a watermark policy, you can find the policy and turn off the switch in the Policy Status column to disable the policy. After the policy is disabled, the policy is retained. You can turn on the switch in the Policy Status column to enable the policy again.
Delete a policy
If you no longer require a watermark policy, you can find the policy and click Delete in the Actions column.
After a policy is deleted, it cannot be restored. Proceed with caution.
References
For information about how to view and trace the logs of outbound transfers of sensitive files, see Sensitive file detection.
For information about how to detect files transferred outbound, see Monitor outbound file transfers to ensure data security.
For information about how to manage peripherals of users to ensure data security, see Manage peripherals to ensure data security.