Communication between client applications and OSS is encrypted by using the transport layer security (TLS) protocol. TLS is a standard cryptographic protocol that ensures privacy and data integrity between clients and servers that communicate over the Internet. You can use an OSS server to configure the TLS version and the cipher suite. After you configure the TLS version and the cipher suite, clients can use only the configured TLS version and cipher suite to send requests to and receive requests from OSS to meet the security requirements of the communication link.
Prerequisite
A RAM user is granted the following permissions: oss:PutTLSVersion and oss:GetTLSVersion. For more information, see Attach a custom policy to a RAM user.
TLS versions
The TLS protocol supports the following versions: TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3. The following table describes the usage scenarios of each version and the mainstream browsers that support each version.
Protocol | Description | Scenario | Supported browser |
TLS 1.0 | The main encryption algorithms that are used include RSA, DES, and 3DES. TLS 1.0 has specific security vulnerabilities and is vulnerable to various attacks, such as BEAST and POODLE attacks. TLS 1.0 cannot ensure strong security for network connections and does not meet the compliance requirements of Payment Card Industry Data Security Standard (PCI DSS). | TLS 1.0 is no longer recommended for network protection due to security vulnerabilities. In most cases, we recommend that you update TLS 1.0 to a secure version at the earliest opportunity. |
|
TLS 1.1 | TLS 1.1 improves security for network connections, fixes some known vulnerabilities, and supports more powerful encryption algorithms, such as AES, RSA, and SHA-256. | TLS 1.1 is suitable for environments that require a relatively high level of security but do not require the latest TLS features. |
|
TLS 1.2 | TLS 1.2 further enhances security for network connections, and launches new features, such as Server Name Indication (SNI) and handshake protocols. TLS 1.2 supports more encryption algorithms, including AES-GCM, AES-CBC, and ECDHE. | TLS 1.2 is suitable for most common secure communication scenarios, including web applications, e-commerce websites, emails, and virtual private networks (VPNs). |
|
TLS 1.3 | TLS 1.3 significantly improves security, performance, and privacy. TLS 1.3 no longer supports some insecure encryption algorithms. It supports more powerful key exchange algorithms and encryption algorithms that reduce the delay of the handshake process, and also provides better forward secrecy and authentication mechanisms. | TLS 1.3 is suitable for scenarios in which high security, better performance, and privacy protection are required, such as in financial institutions, large Internet companies, and government agencies. |
|
Usage notes
We recommend that you do not set the allowed TLS version to only TLS 1.0 or TLS 1.1 for a bucket. We recommend that you include at least TLS 1.2.
If you disable TLS version management, TLS 1.0, 1.1, and 1.2 are supported by default. If you enable TLS version management, you can select TLS 1.0, 1.1, 1.2, or 1.3. When you specify the TLS version for the first time in the OSS console, TLS 1.2 is selected by default because this is the current mainstream version. If you do not select TLS 1.2, some mainstream clients cannot access OSS.
Downgrading the TLS version, such as changing the TLS version from TLS 1.2 to TLS 1.1 or TLS 1.0, or disabling TLS version management may cause security and compliance issues. Proceed with caution when you perform the operation.
Before you disable a TLS version, make sure that clients do not use only the TLS version that you want to disable.
Methods
Use the OSS API
If your business requires a high level of customization, you can directly call the RESTful APIs. To directly call a RESTful API, you must include the signature calculation in your code. For more information, see PutBucketHttpsConfig and GetBucketHttpsConfig.
FAQ
How do I determine the current TLS version of a bucket?
If the client does not specify a TLS version, you can run the following command to determine the current TLS version that is used between the client and the server:
openssl s_client -connect <Bucket>.<Endpoint>:443 -servername <Bucket>.<Endpoint>The following table describes the parameters in the command.
Parameter | Description |
Bucket | The name of the bucket. |
Endpoint | The public endpoint, internal endpoint, or custom domain name of the bucket. |
You can obtain the TLS version from the response.
How do I determine whether the TLS version is successfully configured?
If the allowed TLS version is set to only TLS 1.2 for a bucket, the following scenarios may occur:
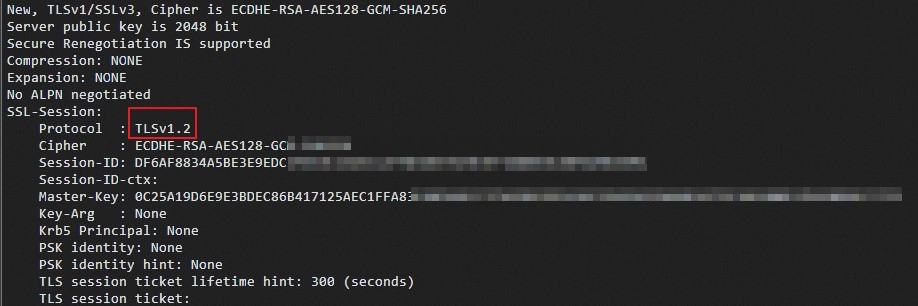
If the client specifies that TLS 1.2 is allowed, you can successfully access the server when you run the following command:
openssl s_client -connect <Bucket>.<Endpoint>:443 -servername <Bucket>.<Endpoint> -tls1_2The following table describes the parameters in the command.
Parameter
Description
Bucket
The name of the OSS bucket.
Endpoint
The public endpoint, internal endpoint, or custom domain name of the bucket.
Sample response:
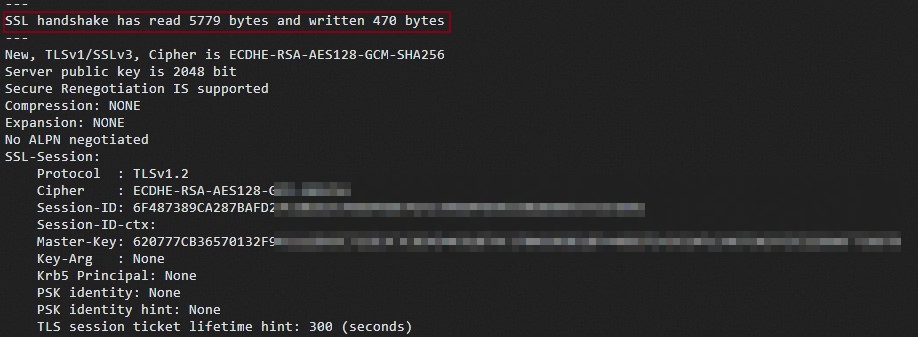
If the client does not specify the TLS version but the client supports TLS 1.2, you can successfully access the server when you run the following command:
openssl s_client -connect <Bucket>.<Endpoint>:443 -servername <Bucket>.<Endpoint>Sample response:

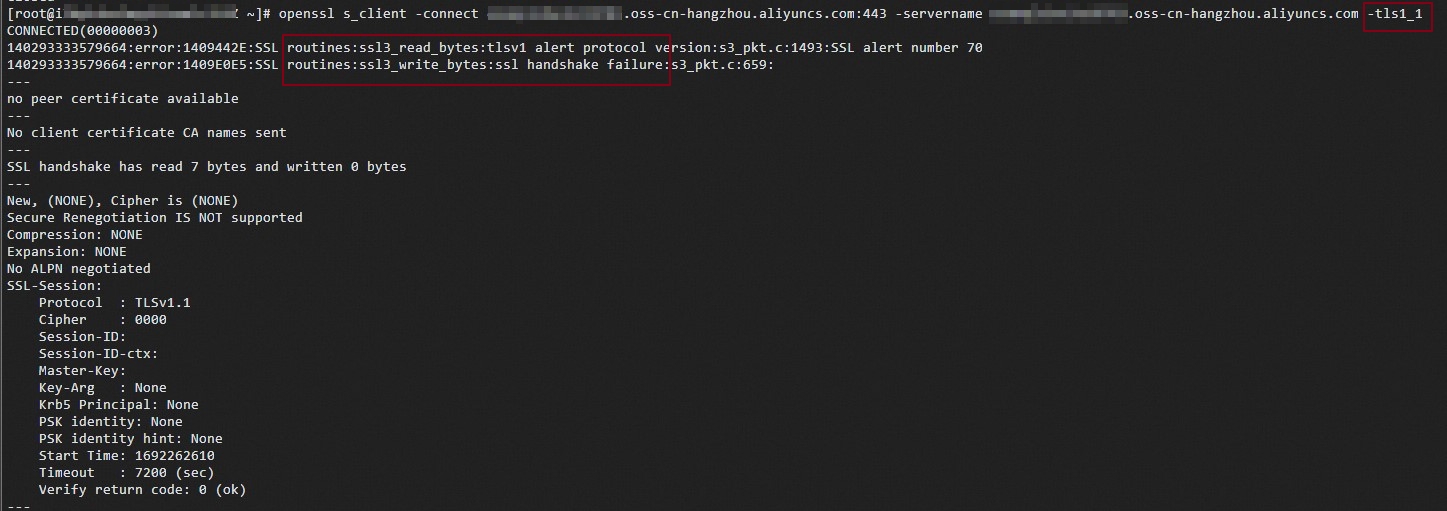
If the client specifies a TLS version other than TLS 1.2, such as TLS 1.1, you cannot access the server when you run the following command:
openssl s_client -connect <Bucket>.<Endpoint>:443 -servername <Bucket>.<Endpoint> -tls1_1Sample response: