As the number of Elastic Compute Service (ECS) instances increases, it becomes more time-consuming and inefficient to configure a public IP address for each ECS instance. In addition, ECS instances are more vulnerable to attacks and malicious scanning. You can configure SNAT entries on an Internet NAT gateway so that specified ECS instances can access the Internet by using the same EIP. This simplifies ECS instance management and reduces the security risks caused by exposure to the Internet.
Scenario
You have a large number of ECS instances. Configuring a public IP address for each ECS instance is time-consuming and inefficient. In addition, ECS instances are more vulnerable to attacks and malicious scanning. As shown in the following figure, you can configure SNAT entries so that ECS instances in VPC-A can use the specified EIP to access the Internet. Some ECS instances created earlier can already access the Internet. Therefore, the following measures are taken:
Unified Internet egress: Use the EIP (39.XX.XX.35) to provide Internet access for all ECS instances in VPC-A.
Smooth transition: After you convert the public IP address of ECS-A to an EIP, you need to disassociate the EIP from the primary network interface controller (NIC) and associate the EIP with an elastic network interface (ENI). This ensures that the method of user access to ECS-A remains unchanged.
The preceding adjustments reduce the risks caused by exposure to the Internet and improve the efficiency of management and O&M.

Procedure
Step 1: Convert the public IP address to an EIP
Log on to the ECS console and find the ECS instance. Convert the public IP address of ECS-A to an EIP.
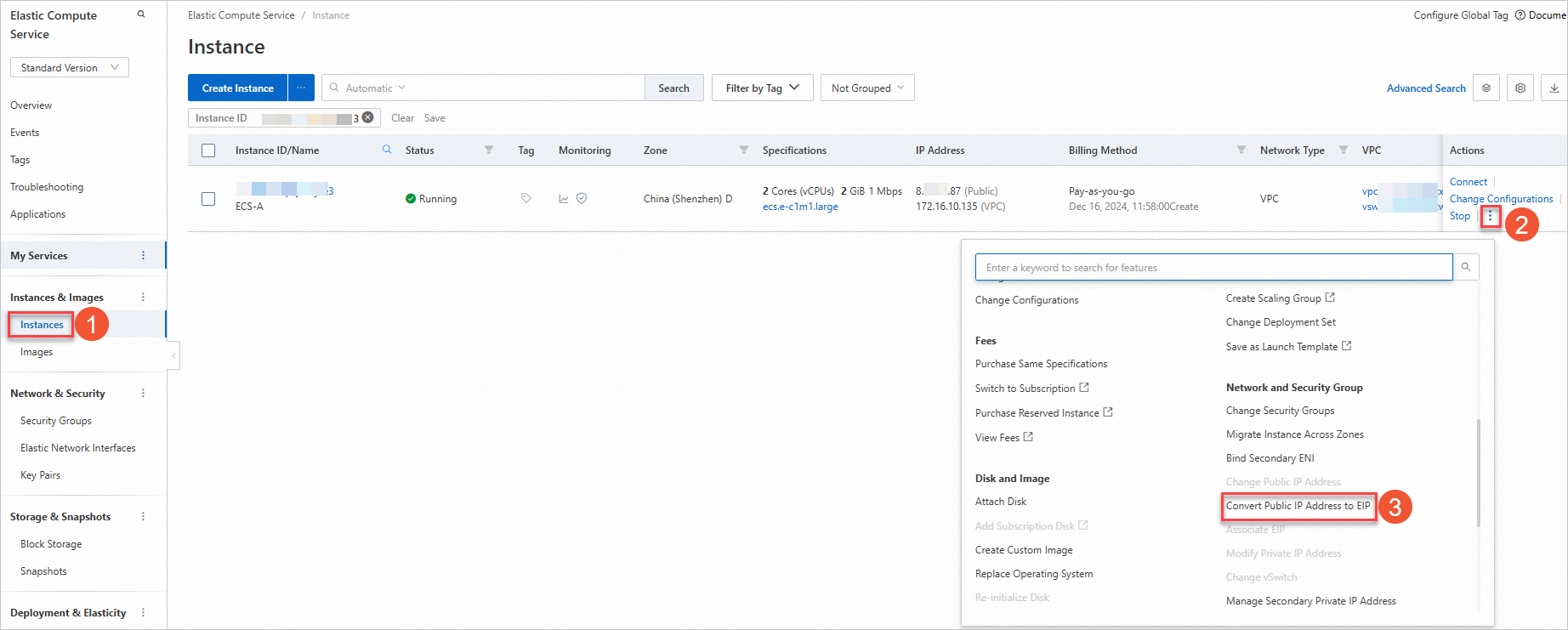
If the public IP address uses the subscription billing method, you cannot directly convert the public IP address to an EIP. You must switch the subscription billing method to pay-as-you-go before you can convert the public IP address to an EIP. For more information about how to convert a subscription public IP address to a pay-as-you-go public IP address, see Change from pay-by-bandwidth to pay-by-traffic.
Step 2: Configure an ENI
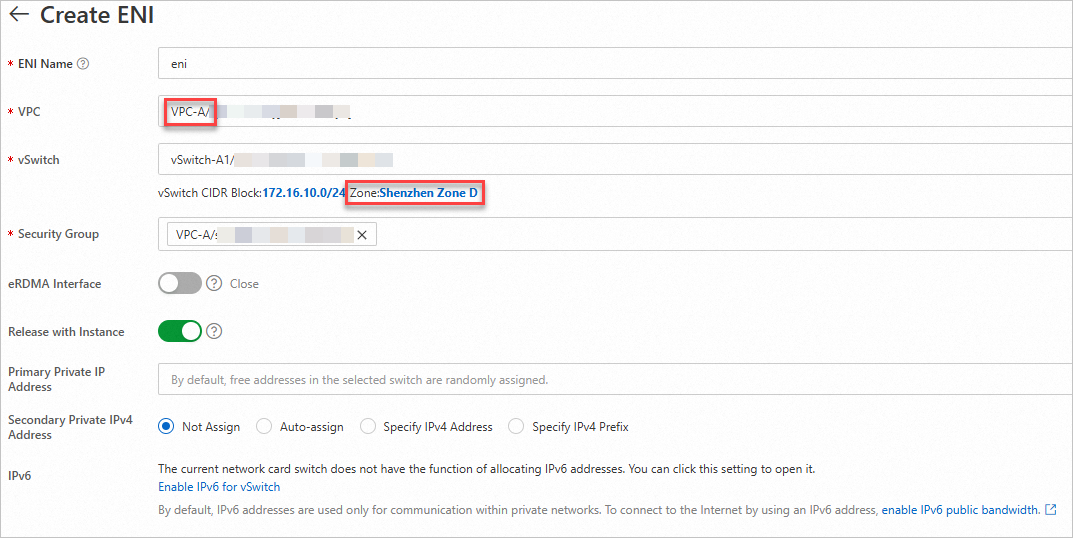
In the left-side navigation pane, choose and click Create ENI.
ImportantWhen you create an ENI, make sure that the VPC and vSwitch zone of the ENI are the same as those of ECS-A.
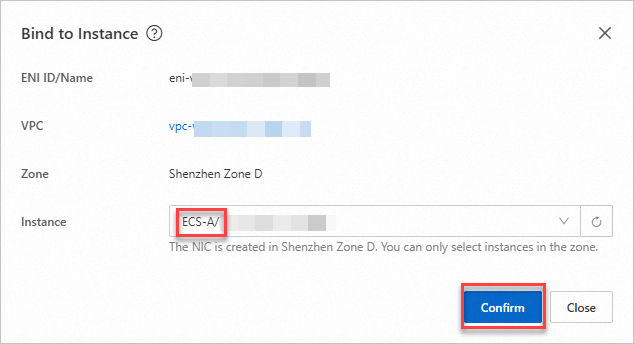
On the Elastic Network Interfaces page, find the ENI and click Bind to Instance in the Actions column to associate the ENI with ECS-A.
On the ECS-Workbench page, log on to ECS-A. In this example, the Alibaba Cloud Linux 3.2104 LTS 64-bit operating system is used to describe the ENI and route information, and how to configure policy-based routes.
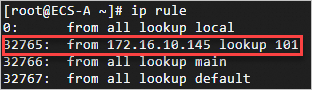
Run the
ifconfigandroute -ncommands to check the information about the ENI and route table.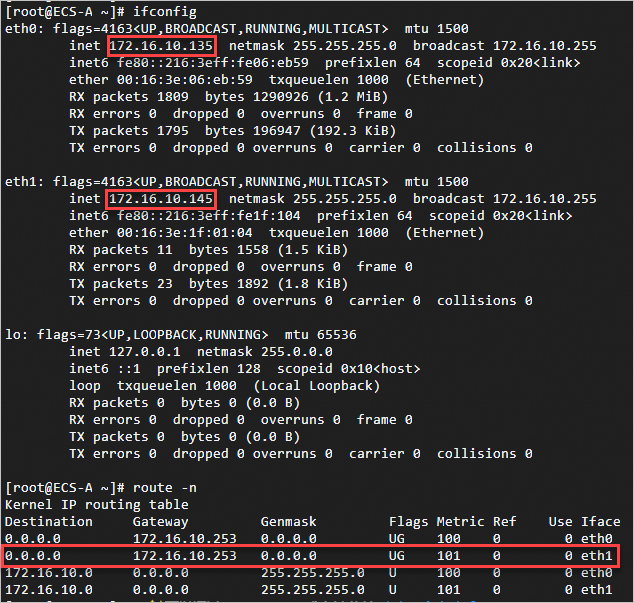
Configure policy-based routes
ImportantIf the associated ENI cannot be identified, you need to configure the ENI on the ECS instance.
Step 3: Configure an EIP
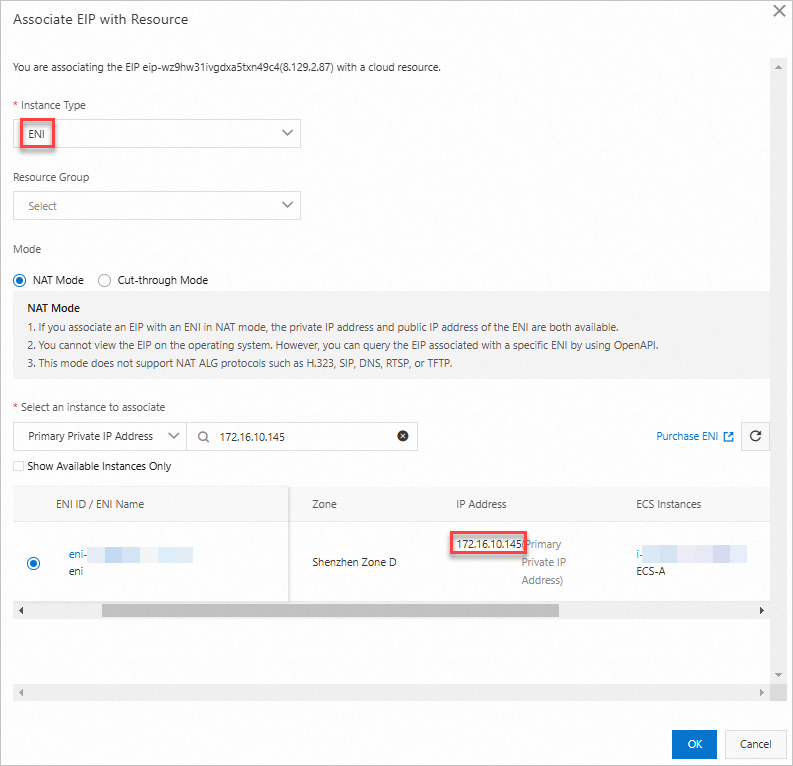
On the Elastic IP Addresses page, find the EIP 8.XX.XX.87 and click Disassociate from Resource in the Actions column. Click Associate with Resource in the Actions column.
Associate the EIP with the ENI whose private IP address is 172.16.10.145.
Step 4: Configure a NAT gateway
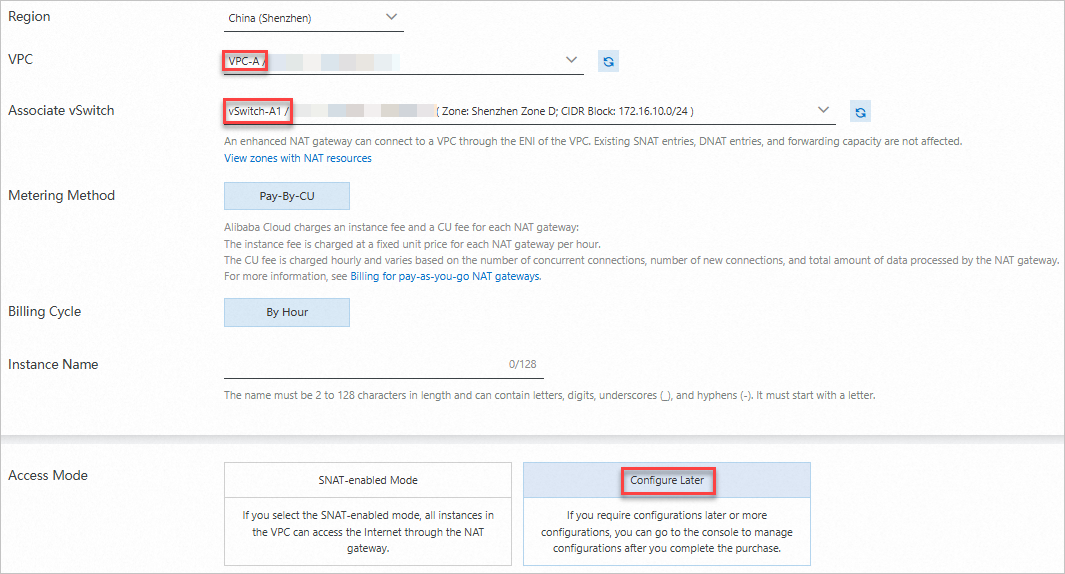
Create an Internet NAT gateway and associate the EIP with the Internet NAT gateway.
In the left-side navigation pane, choose . On the Internet NAT Gateway page, click Create Internet NAT Gateway.
On the Elastic IP Addresses page, find the EIP 39.XX.XX.35 associated with a CLB instance and click Disassociate from Resource in the Actions column.
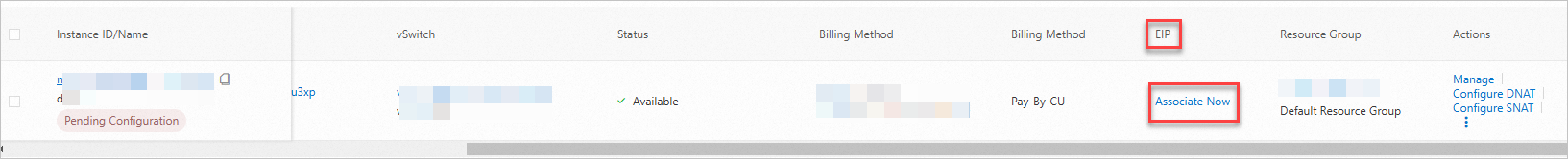
Return to the Internet NAT Gateway page, find the Internet NAT gateway, and click Associate Now in the EIP column. Associate the EIP 39.XX.XX.35 with the Internet NAT gateway.
Create a mapping between the Internet NAT gateway and the CLB instance.
Log on to the CLB console. On the Instances page, find the CLB instance and view the address in the VPC column.
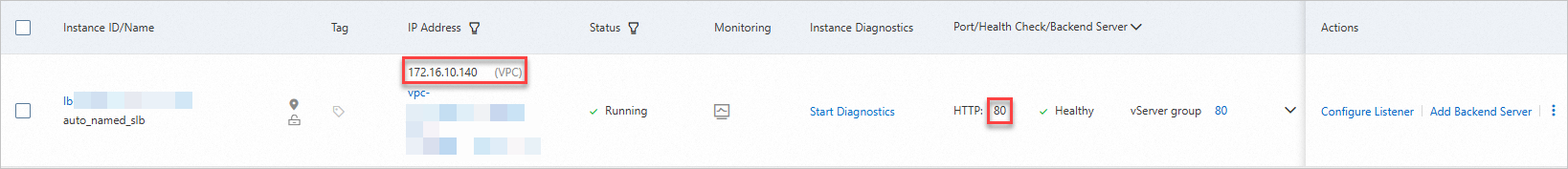
Return to the Internet NAT Gateway page, find the Internet NAT gateway and click Configure DNAT in the Actions column.
On the DNAT Management tab, click Create DNAT entry. Set Private Port to the port of the CLB listener.
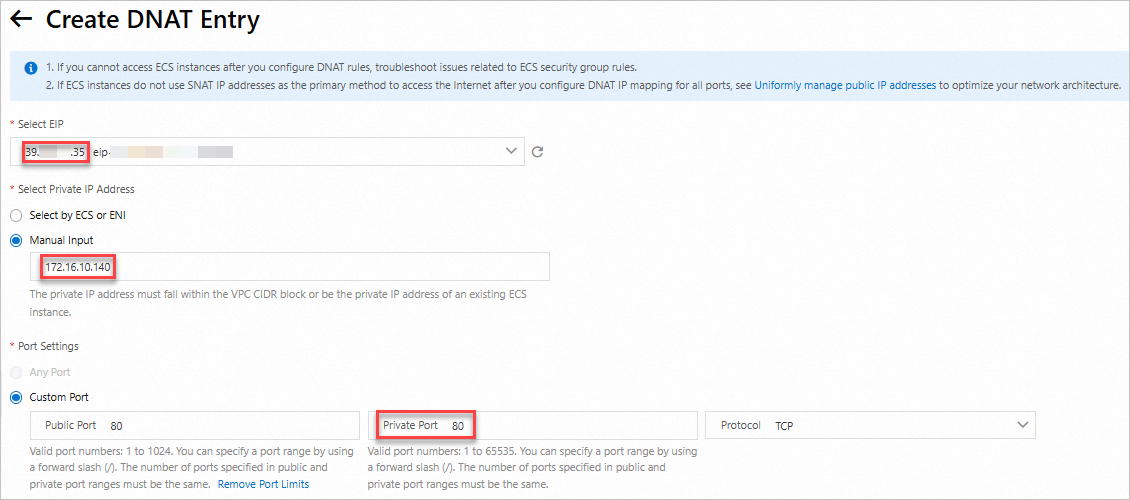 Note
NoteIf you set Port Settings to Any Port:
If IP mapping is configured for an EIP in a DNAT entry, the EIP cannot be used in another DNAT entry or SNAT entry.
If a NAT gateway is configured with an SNAT entry and a DNAT entry that uses IP mapping, the ECS instance preferentially uses IP mapping instead of SNAT to access the Internet.
Create a mapping between the Internet NAT gateway and the VPC. You can also modify the SNAT entry based on your requirements.
On the SNAT Management tab, click Create SNAT Entry.
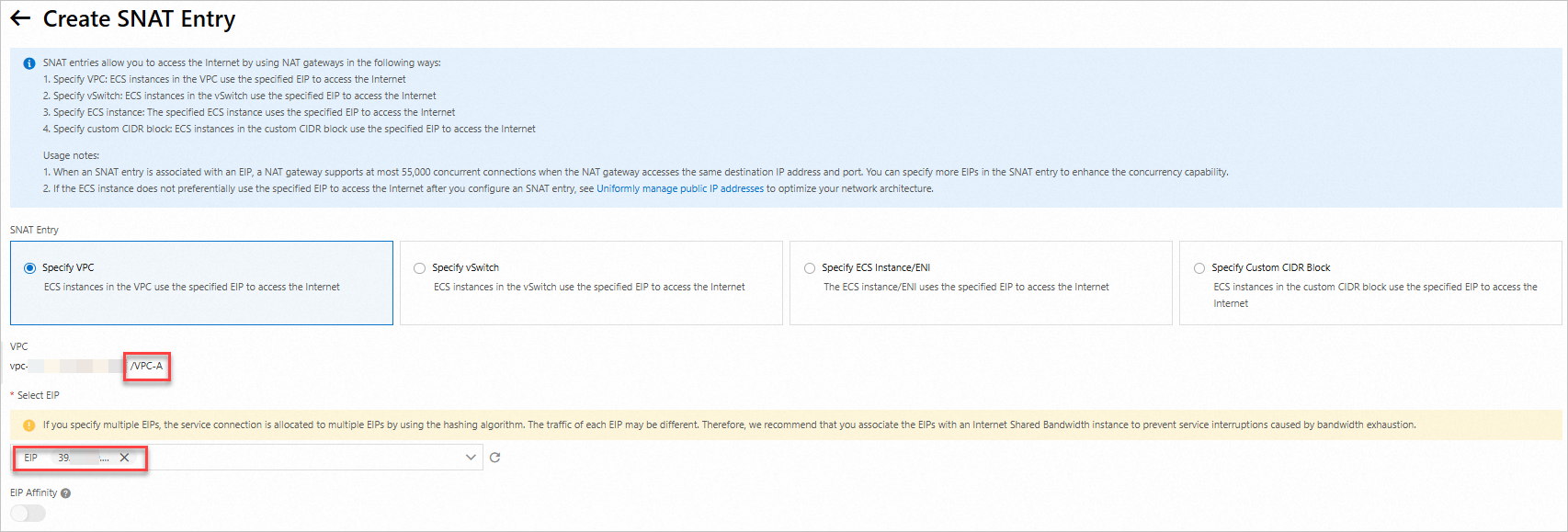 Important
ImportantIf the vSwitch is associated with a custom route table, you need to configure a 0.0.0.0/0 route whose next hop is the Internet NAT gateway on the custom route table.
Check the result
CLB
Enter
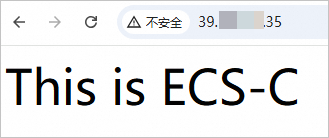
http://39.XX.XX.35in a browser to check whether the CLB instance works as expected.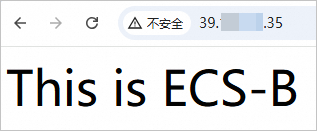
After you set the weight of ECS-B to 0, your access to ECS-B is redirected to ECS-C.
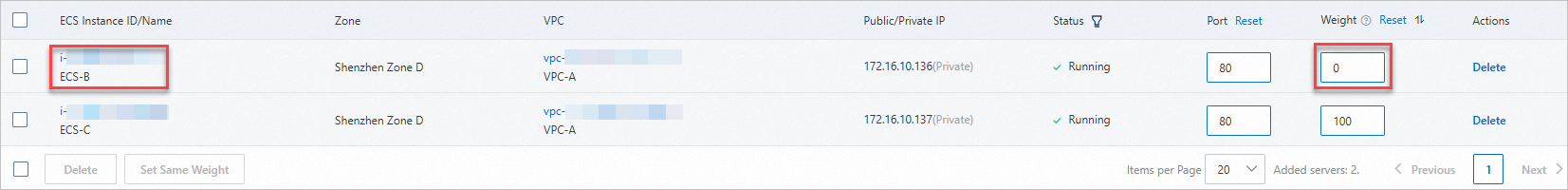
Internet egress
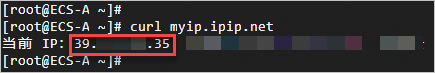
Log on to ECS-A and ECS-B on the ECS-Workbench page and run the curl myip.ipip.net command to check whether the same EIP is used for Internet access.
ECS-A
By default, outbound traffic is forwarded from eth0 through the EIP specified in the SNAT entry based on the priorities of internal NICs.
eth0: private IP address: 172.16.10.135. Metric :0. A smaller number indicates a high priority. EIP :39.XX.XX.XX. 35.
eth1: Private IP address: 172.16.10.145. Metric :101. EIP :8.XX.XX. 87.
ECS-B
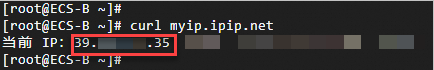
ECS-C
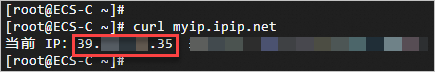
ECS-A access method
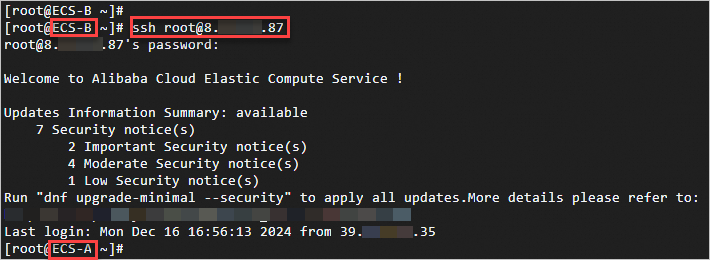
Log on to ECS-B and run the command ssh root@8.XX.XX. 87. Check whether you can access ECS-A by using the original method.
FAQ
How do I determine the priorities of public IP addresses, EIPs, SNAT entries, and DNAT entries (any port) when I configure Internet access for an ECS instance?
The following priority rule is applied: public IP address/EIP > DNAT IP mapping (any port) > EIP specified in SNAT.