Alibaba Cloud Elasticsearch clusters are deployed in logically isolated virtual private clouds (VPCs). Access control, authentication and authorization, encryption, and the advanced security features provided by X-Pack are used for the clusters. This ensures the high security of the clusters. This topic describes the access control methods that can be used for Alibaba Cloud Elasticsearch clusters.
Specify a cluster access password or reset the password
When you create an Elasticsearch cluster, you must specify a password for the default user elastic. The password is used to authenticate your identity when you use a client to access the cluster or when you log on to the Kibana console of the cluster. For more information, see Parameters on the buy page.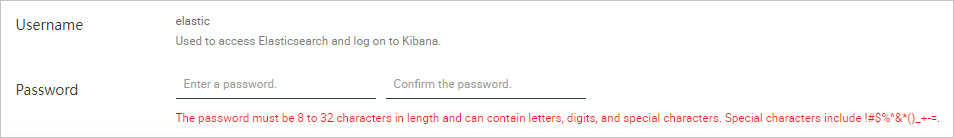
If you want to change the password, you can reset the password. For more information, see Reset the access password for an Elasticsearch cluster.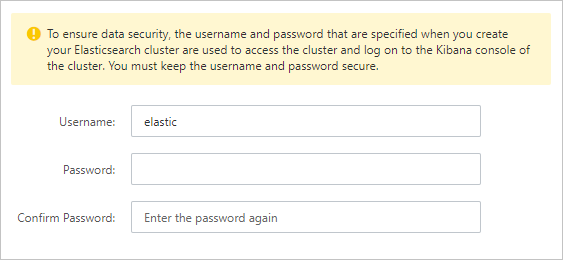
Configure IP address whitelists for cluster access
Public IP address whitelists: For security purposes, the Public Network Access feature is disabled for Elasticsearch clusters by default. If you want to access your Elasticsearch cluster over the Internet, you must enable the feature and add the IP address of the host that you use to access the cluster to a public IP address whitelist of the cluster. For more information, see Configure a public or private IP address whitelist for an Elasticsearch cluster.

Private IP address whitelists: By default, Elasticsearch allows you to access your cluster over an internal network and modify the private IP address whitelists of the cluster. If you want to use a host to access your Elasticsearch cluster over an internal network, you must add the IP address of the host to a private IP address whitelist of the cluster. For more information, see Configure a public or private IP address whitelist for an Elasticsearch cluster.
Configure IP address whitelists for Kibana access
Public IP access whitelists: The Public Network Access feature is enabled for Kibana by default. However, for security purposes, Elasticsearch adds 127.0.0.1,::1 to the default public IP address whitelist of Kibana to deny requests from all IPv4 and IPv6 addresses. The first time you log on to the Kibana console, the system prompts you to configure a public IP address whitelist. You must add the IP address of your host to a public IP address whitelist of Kibana before you log on to the Kibana console by using the host. For more information, see Configure a public or private IP address whitelist for Kibana.

Private IP address whitelists: The Private Network Access feature is disabled for Kibana by default. If you want to use a host to log on to the Kibana console over an internal network, you must enable the feature and add the IP address of the host to a private IP address whitelist of Kibana. For more information, see Configure a public or private IP address whitelist for Kibana.
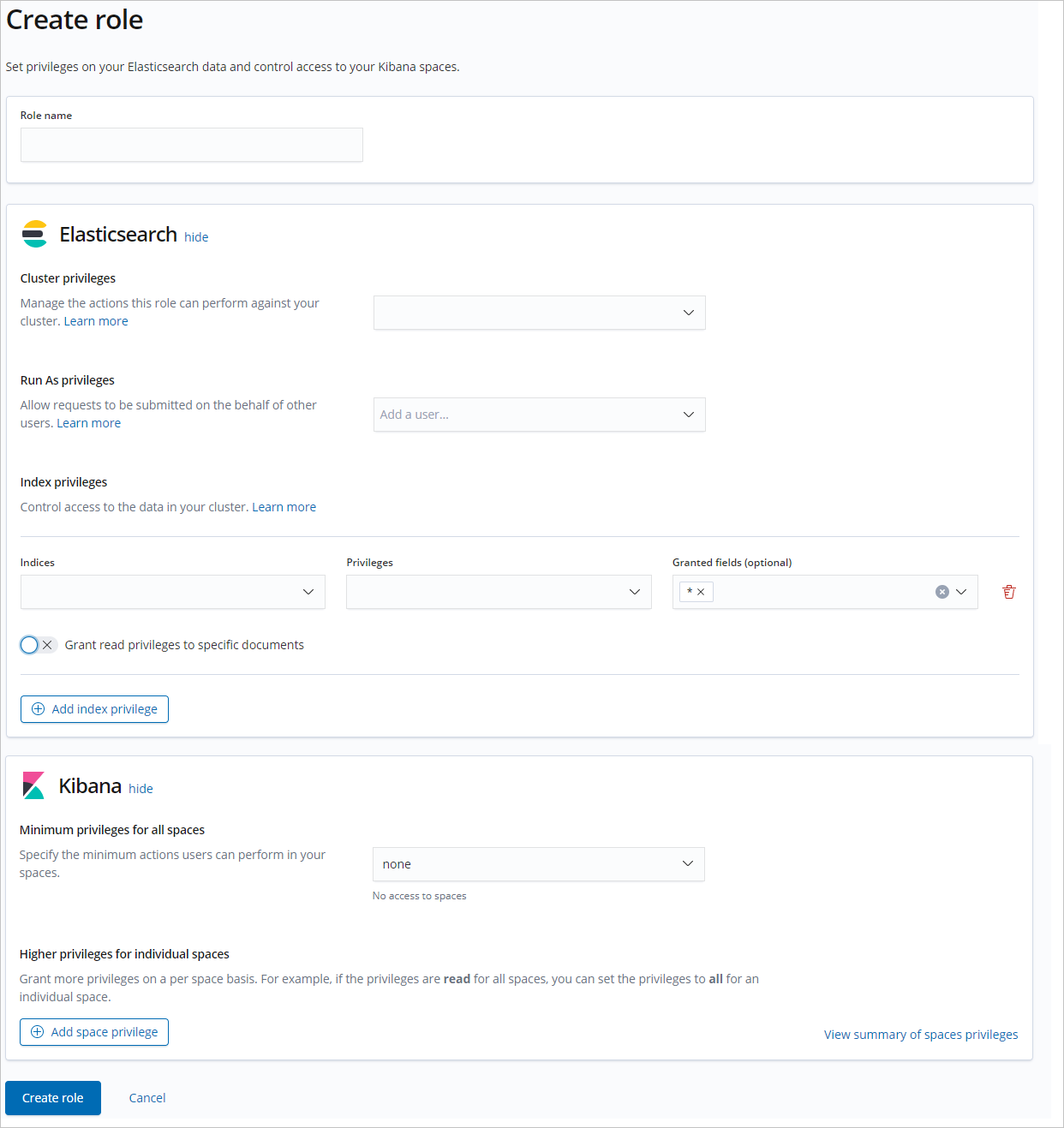
Use the RBAC mechanism provided by the X-Pack plug-in
If you want to grant access permissions on objects such as Elasticsearch clusters, indexes, and fields, you can use the role-based access control (RBAC) mechanism that is provided by the X-Pack plug-in of Elasticsearch. This mechanism allows you to grant permissions to custom roles and assign the roles to users in the Kibana console for access control. For more information, see Use the RBAC mechanism provided by Elasticsearch X-Pack to implement access control.