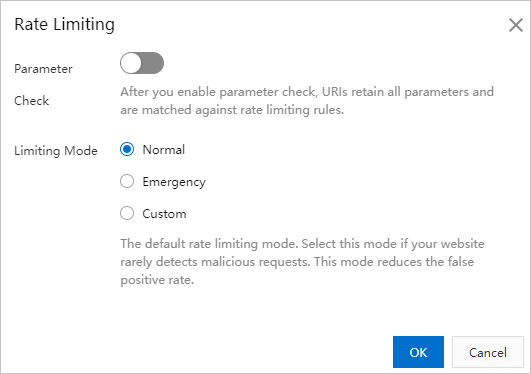
If your website is flooded by HTTP requests and its responses become sluggish as a result, you can enable the rate limiting feature. When rate limiting is enabled, Dynamic Route for CDN (DCDN) identifies IP addresses that send abnormal amounts of requests and limit the requests coming from the identified IP addresses. This improves website security.
Notice The rate limiting feature is suspended. We recommend that you use DCDN WAF (new edition).
This topic consists of the following sections:
Enable the rate limiting feature
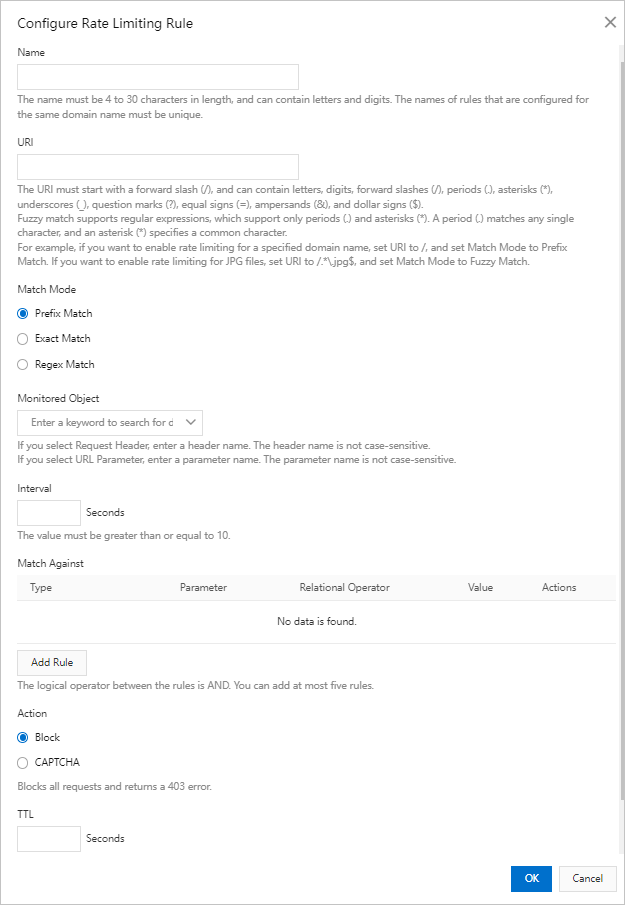
Create a custom rate limiting rule
Notice
- If you set Limiting Mode to Custom, you must create a custom rate limiting rule. Other limiting modes do not require custom rate limiting rules.
- You can create a maximum of five custom rate limiting rules.
Examples
The following table provides examples of how to create a custom rule.
| Scenario | Monitored object | Interval | Matching against | Action | TTL | Expected result |
|---|---|---|---|---|---|---|
| 4xx or 5xx errors | IP | 10 seconds | "status_ratio|404">60%&&"count">50 |
Block | 10 minutes | If the percentage of the HTTP 404 status code among all HTTP status codes returned to an IP address reaches 60%, and at least 50 requests are coming from the IP address, the IP address is blocked for 10 minutes. All requests from the IP address receive the HTTP 403 status code. |
| Queries per second (QPS) errors | Domain name | 10 seconds | "count">NNote Specify a value for N based on your business requirements.
|
CAPTCHA | 10 minutes | If the number of requests that are sent to a domain name reaches the value of N, CAPTCHA is triggered. Within the next 10 minutes, all requests sent to the domain name are presented with a verification challenge. Requests are allowed to access the domain name only if the requests pass the verification challenge. |