If your origin server is an Object Storage Service (OSS) bucket, setting the bucket ACL to private can prevent your resources from unauthorized access. In this case, to allow Dynamic Content Delivery Network (DCDN) to fetch content from the private OSS bucket, you must grant DCDN the corresponding permissions. This topic describes how to enable and disable DCDN access to private OSS buckets.
Background information
After you grant DCDN permissions to access a private OSS bucket, you can use features such as hotlink protection and URL signing that are provided by DCDN to protect your resources. For more information, see Configure a Referer whitelist or blacklist to enable hotlink protection and Configure URL signing.
The first time you use this feature, you need to grant DCDN read-only permissions on all OSS buckets in your account. By default, this feature uses temporary Security Token Service (STS) tokens to access OSS buckets. You cannot use this feature to write or delete objects in OSS buckets by using PUT requests.
If you configure a permanent security token, you need to restrict the token from being used to write or delete objects in OSS buckets by using PUT requests when you apply for the token. For information about how to access OSS by using a RAM user, see Access OSS by using a RAM user.
After you grant read-only permissions to DCDN and enable the private bucket access feature for an accelerated domain name, you can access all resources in your private buckets by using the accelerated domain name. Proceed with caution when you use this feature. If the private OSS bucket stores content other than what is intended for the visitors of the website, do not grant DCDN permissions on your private OSS bucket or enable the private bucket access feature.
If your website is vulnerable to attacks, purchase an Anti-DDoS service. In addition, proceed with caution when you grant DCDN permissions on private OSS buckets or enable access to private OSS buckets.
After you enable the private bucket access feature, points of presence (POPs) add the Authorization header to origin requests. The value of the header is the authentication signature for accessing private OSS buckets. An origin request that retrieves resources from an OSS bucket cannot include a signature in both the Authorization header and URL parameters. If an origin request includes the Authorization header and URL parameters that are used for signature authentication, which are usually generated by the client, such as
Expires,Signature, andOSSAccessKeyId, OSS authentication fails.
Enable access to private OSS buckets
Log on to the DCDN console.
In the left-side navigation pane, click Domain Names.
On the Domain Names page, find the domain name that you want to manage and click Configure.
In the left-side navigation tree of the domain name, click Origin Fetch.
Optional. In the Private Bucket Origin section, click Authorize, and then click Confirm Authorization Policy. This step is required only if this is your first time authorizing DCDN to access private OSS buckets.
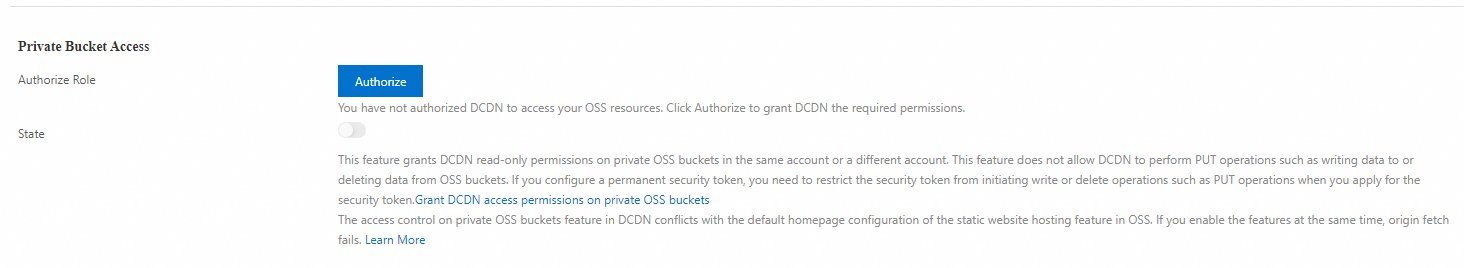
In the Private Bucket Origin section, turn on the Private Bucket Origin switch.
NoteYou only need to perform the preceding steps if you want to authorize DCDN to access unencrypted objects in a private OSS bucket. If you want DCDN to access OSS objects that are encrypted by using Key Management Service (KMS), you need to first attach the AliyunKMSCryptoUserAccess policy to the AliyunCDNAccessingPrivateOSSRole RAM role.
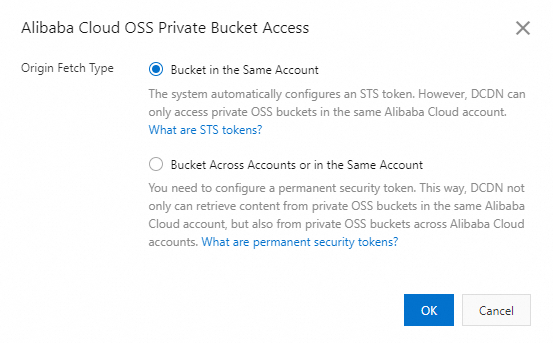
In the Alibaba Cloud OSS Private Bucket Access dialog box that appears, select a type and click OK.
Parameter
Description
Origin Fetch Type
Bucket in the Same Account: A security token is automatically issued by Security Token Service (STS). This option allows DCDN to fetch content from private OSS buckets only in the same Alibaba Cloud account.
Bucket Across Accounts or in the Same Account: You need to configure an AccessKey pair. This option allows DCDN to fetch content from private OSS buckets both in the same account and across different accounts.
AccessKey ID
The AccessKey ID of the Alibaba Cloud account to which the private OSS bucket belongs. For more information, see Create an AccessKey.
AccessKey Secret
The AccessKey secret of the Alibaba Cloud account to which the private OSS bucket belongs.
Attach the AliyunKMSCryptoUserAccess policy to the AliyunCDNAccessingPrivateOSSRole RAM role.
Log on to the RAM console.
In the left-side navigation pane, choose .
In the Role Name column, find and select the AliyunCDNAccessingPrivateOSSRole RAM role.
Click Grant Permission. In the Grant Permission panel, the Principal field is automatically filled in.
In the Policy section, search for the AliyunKMSCryptoUserAccess system policy. Click the policy to add it to the Selected Policy list.
Click Grant permissions.
Click Close.
Disable access to private OSS buckets
If you no longer want DCDN to access your private OSS buckets, you can log on to the RAM console and revoke the access permissions that are granted to DCDN.
Log on to the RAM console.
In the left-side navigation pane, choose .
On the Roles page, find and click AliyunCDNAccessingPrivateOSSRole.
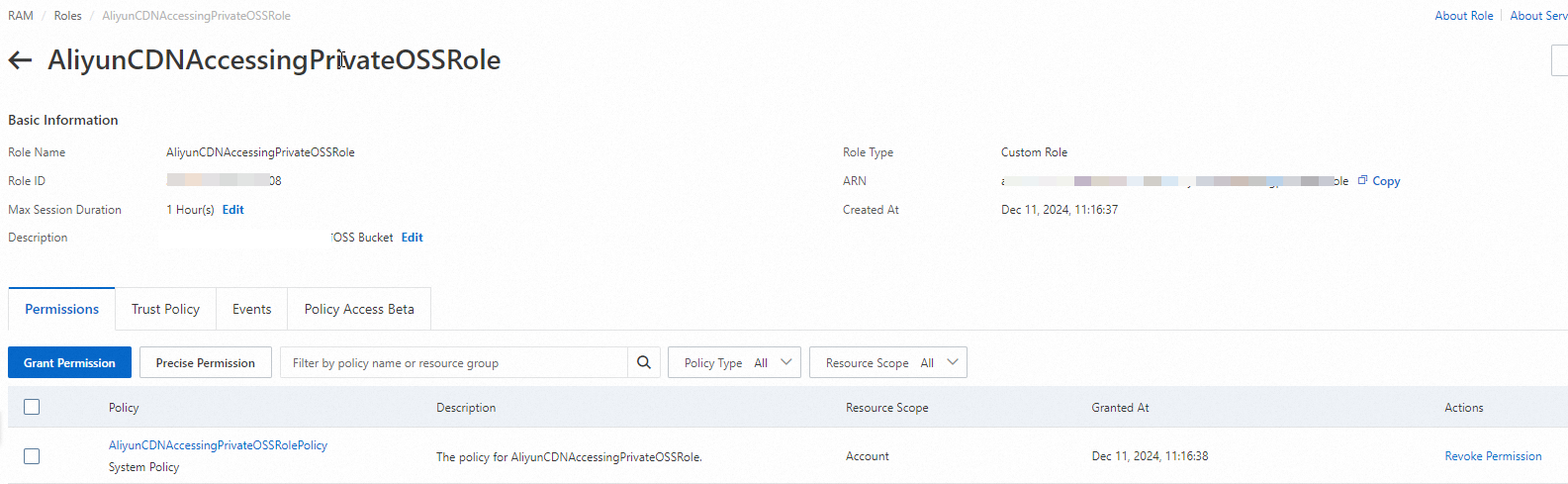
Revoke all permissions from the role AliyunCDNAccessingPrivateOSSRole.
Find the policy that you want to manage and click Revoke Permission in the Actions column.
In the Revoke Permission message, click Revoke Permission.
In the left-side navigation pane, choose .
Find AliyunCDNAccessingPrivateOSSRole and click Delete Role in the Actions column.
In the Delete Role dialog box, enter the name of the role you want to delete and click Delete Role.