By default, if you do not configure an access control policy after you enable a firewall, Cloud Firewall allows all traffic. To better manage unauthorized access to your assets, you can configure Allow or Deny policies based on your business requirements. This topic describes access control policies of Cloud Firewall, including how access control policies work and the billing rules.
Feature description
Cloud Firewall allows you to configure access control policies for the Internet firewall, NAT firewalls, virtual private cloud (VPC) firewalls, and internal firewalls to block unauthorized access and implement multi-directional isolation and control on traffic. The access control policies that are described in this topic apply only to the Internet firewall, NAT firewalls, and VPC firewalls.
For more information about how to configure an access control policy for an internal firewall, see Create an access control policy for an internal firewall.
Items in access control policies
You can specify different items in access control policies to allow or deny related traffic.
Item | Description | Type | Supported type by policy |
Source | The initiator of the network connection. |
|
|
Destination | The receiver of the network connection. | IP address, IP address book, domain name, and region.
|
|
Protocol type | The transport layer protocol. | TCP, UDP, ICMP, and ANY. If you do not know the protocol for the policy, select ANY. The value ANY specifies all protocol types. | The types are supported by all access control policies for firewalls. |
Port | The destination port. | The access control policy controls traffic that passes through specific ports. The types are port and address book. |
|
Application | The application layer protocol. | The types include HTTP, HTTPS, SMTP, SMTPS, SSL, FTP, IMAPS, and POP3. If you do not know the application type, select ANY. The value ANY specifies all application types. Note Cloud Firewall identifies the application of SSL or TLS traffic based on the port.
| The types supported by access control policies vary based on the selected protocol types. |
Implementation
By default, if no access control policy is configured, Cloud Firewall allows all traffic during the matching process of access control policies.
After you configure an access control policy, Cloud Firewall splits the policy into one or more matching rules based on specific logic and sends the policy to an engine. When traffic passes through Cloud Firewall, Cloud Firewall matches traffic packets in sequence based on the priorities of the configured access control policies. If a traffic packet hits a policy, the action that is specified in the policy is performed, and the subsequent policies are not matched. Otherwise, the system continues to match the traffic packet against the policy that has a lower priority until a policy is hit or all configured policies are matched. By default, if traffic does not hit a policy after all configured policies are matched, the traffic is allowed.
After you create, modify, or delete an access control policy, Cloud Firewall requires approximately 3 minutes to send the policy to the engine.
A small priority value indicates a higher priority. To ensure that the capabilities of access control can be maximized, we recommend that you specify high priorities for frequently matched policies and refined policies.
The following figure shows how an access control policy works.

Policy actions
The following actions are supported in access control policies: Allow, Monitor, and Deny. When the elements of traffic packets match an access control policy, Cloud Firewall performs the action specified in the policy.
If the action of a policy is set to Monitor, traffic is allowed when the policy is hit. You can observe traffic for a period of time and change the policy action to Allow or Deny based on your business requirements.
You can view the traffic data on the Traffic Logs page. For more information, see Log audit.
Quota consumed by access control policies
After you configure an access control policy, Cloud Firewall calculates the quota that is consumed by the policy based on the numbers of items that are specified in the policy, such as source addresses, destination addresses, protocol types, ports, and applications.
Calculation method
The quotas that are consumed by access control policies are calculated by using the following formulas:
Quota consumed by an access control policy = Number of source addresses (number of CIDR blocks or regions) × Number of destination addresses (number of CIDR blocks, regions, or domain names) × Number of port ranges × Number of applications.
ImportantYou can configure access control policies whose Destination Type is Domain Name for the Internet firewall, VPC firewalls, and NAT firewalls. The quota consumed by such access control policies in which Domain Name Identification Mode is set to DNS-based Dynamic Resolution or set to FQDN and DNS-based Dynamic Resolution is calculated by tier on each firewall boundary.
If the total quota consumed by such access control policies on a firewall boundary is less than or equal to 200, the actual consumed quota is the total quota. If the total quota consumed by such access control policies on a firewall boundary is greater than 200, the actual consumed quota is calculated based on the following formula: Actual consumed quota = 200 + (Excess quota × 10).
For example, you configured an access control policy on the Internet boundary. The destination address of the policy is aliyun.com, the domain name identification mode of the policy is DNS-based dynamic resolution, and the quota that is consumed by the policy is 185. In this case, if you want to create an access control policy whose domain name identification mode is DNS-based dynamic resolution and the quota that is consumed by the policy is 16, the total quota consumed by the two policies is calculated based on the following formula: 200 + (185 + 16 - 200) × 10 = 210.
You can view the quota that is consumed by an access control policy in the Consumed Quota column of the policy in the access control policy list.
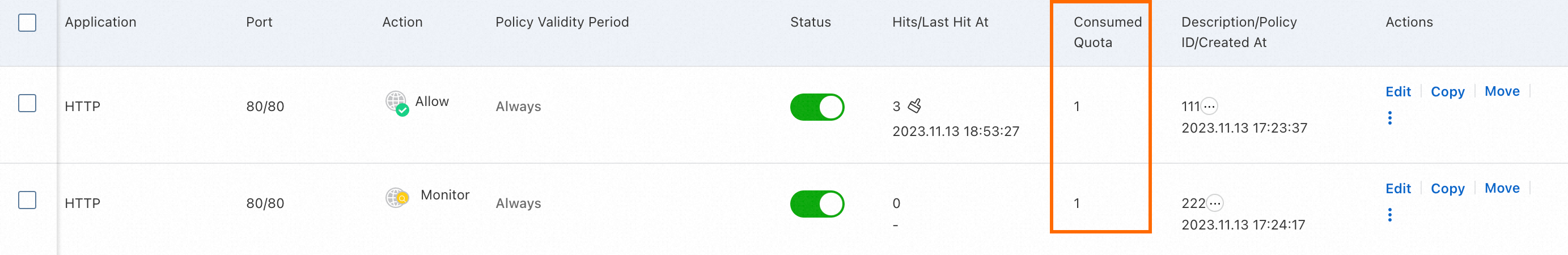
Total quota consumed by access control policies = Quota consumed by outbound access control policies + Quota consumed by inbound access control policies.
You can view the total quota that is consumed by the access control policies for a type of firewall in the upper part of the page of the firewall. The following figure shows the quota that is consumed by access control policies that are created for the Internet firewall.
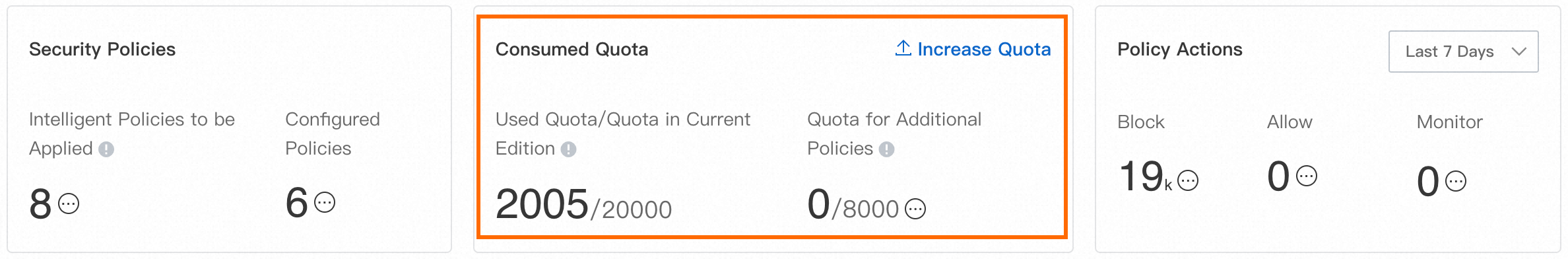
Billing
By default, the basic price of Premium Edition, Enterprise Edition, and Ultimate Edition of Cloud Firewall that uses the subscription billing method covers a specific quota for access control policies. If the specific quota cannot meet your business requirements, you can purchase an additional quota.
The additional quota on access control policies can be used for access control policies for the Internet firewall, NAT firewalls, and VPC firewalls. For more information, see Subscription.
Cloud Firewall that uses the pay-as-you-go billing method allows you to create a maximum of 2,000 access control policies for the Internet firewall, 2,000 access control policies for NAT firewalls, and 10,000 access control policies for VPC firewalls. The numbers cannot be increased. For more information, see Pay-as-you-go.
Examples on how to calculate the quota consumed by access control policies
References
For more information about how to manage the traffic between Internet-facing assets and the Internet, see Create access control policies for the Internet firewall.
For more information about how to manage the traffic from internal-facing assets to the Internet, see Create an access control policy for a NAT firewall.
For more information about how to manage traffic between VPCs and between VPCs and data centers, see Create an access control policy for a VPC firewall.
For more information about how to manage traffic between ECS instances, see Create an access control policy for an internal firewall between ECS instances.
For more information about how to configure access control policies and the usage scenarios of access control policies, see Configure access control policies.
If you deploy Cloud Firewall together with Bastionhost, you must configure access control policies to prevent the traffic of your Bastionhost from being blocked by Cloud Firewall. For more information, see Configure access control policies in scenarios in which Cloud Firewall is deployed together with Bastionhost.