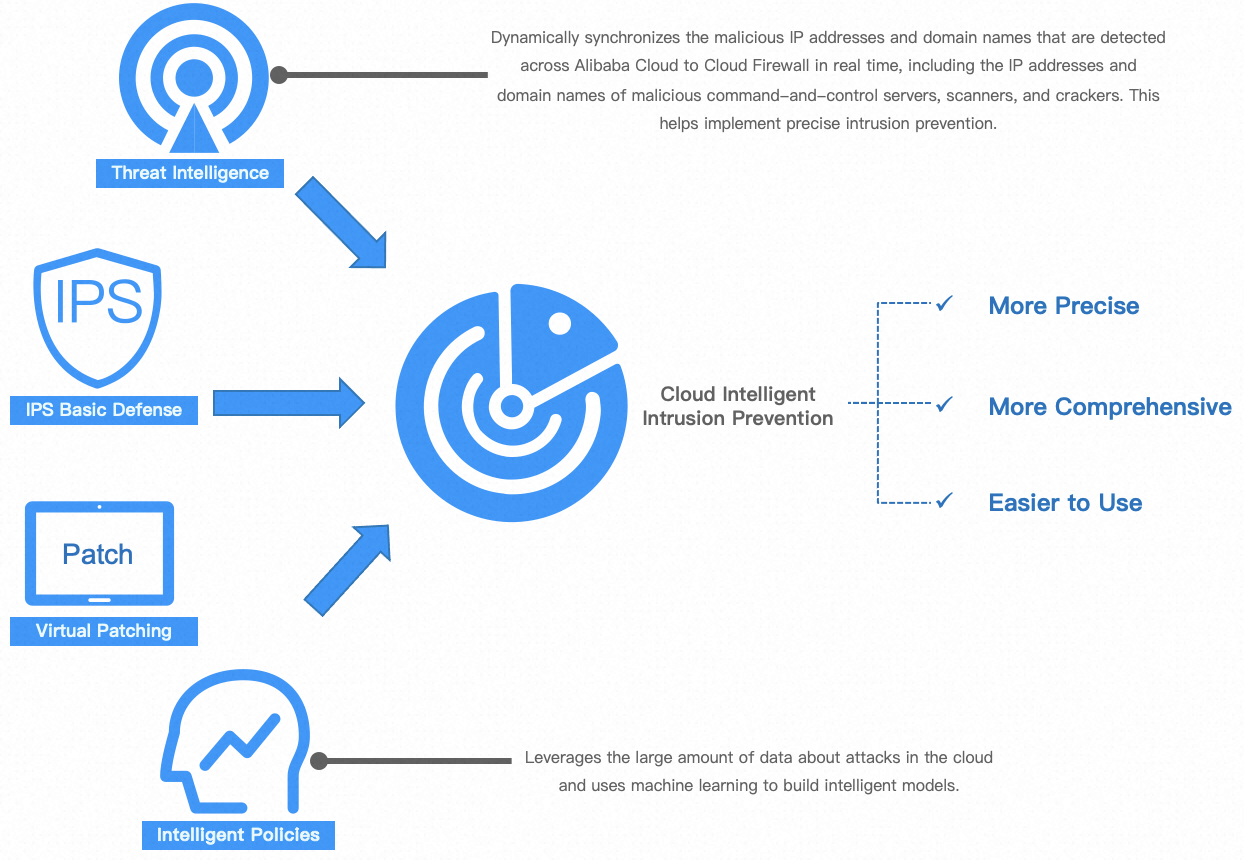
The default intrusion prevention system (IPS) of Cloud Firewall proactively detects and blocks malicious traffic that is generated by attacks, vulnerability exploits, brute-force attacks, worms, mining programs, trojans, and DoS attacks in real time. This protects enterprise information systems and network architectures on the cloud against attacks, prevents unauthorized access or data leaks, and prevents damage or failures of your business systems and applications.
Why IPS?
Common cyber attacks on the cloud
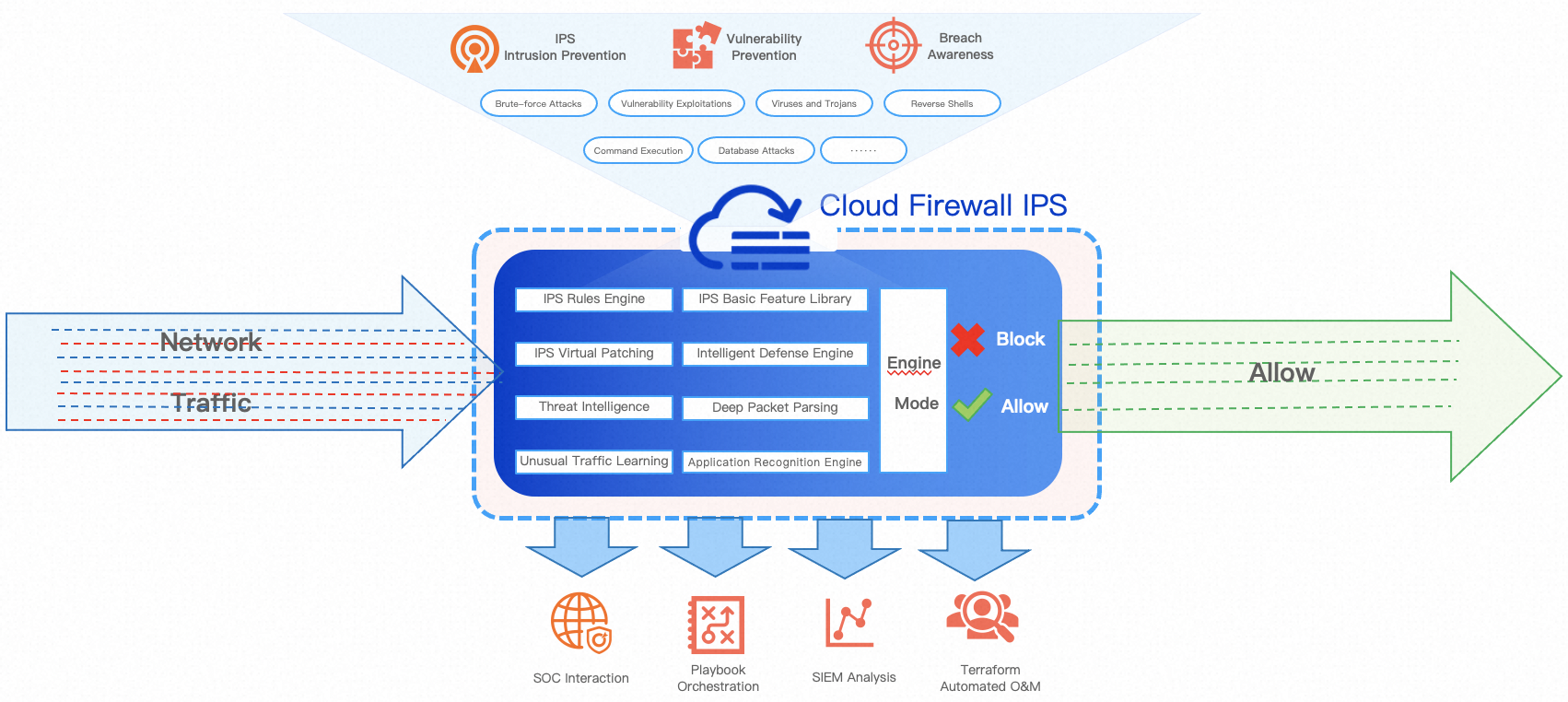
IPS of Cloud Firewall
Implementation of the Cloud Firewall IPS
Cloud Firewall is deployed in the cloud network in series mode. It protects the traffic from and to the Internet, the traffic passing through NAT gateways, the traffic between virtual private clouds (VPCs) in internal networks, and the traffic between the cloud and on-premises data centers. The following figure shows the network architecture.

Cloud Firewall monitors all network traffic that passes through Cloud Firewall, filters the traffic by using the IPS engine and ACL engine of Cloud Firewall, and then forwards normal traffic.
Cloud Firewall uses the Deep Packet Inspection (DPI) engine to detect and identify network traffic. It can identify protocols of network traffic and parse packets. Cloud Firewall also filters traffic and packets to identify IPS attacks and threat intelligence. If the rules of the threat detection engine in different modes, such as Monitor Mode, Block Mode - Loose, Block Mode - Medium, or Block Mode - Strict and IPS rules are hit, the attack packets are discarded or allowed. This way, alerts are generated and attacks are blocked in real time.
Types of attacks supported by Cloud Firewall
For more information about how to configure the mode of the threat detection engine, see IPS configuration.
Attack type | Attack hazard | Suggestion |
Suspicious connection | Attackers may use scanners to scan open ports on a server. If the server has unauthorized database ports or services that have weak passwords, data loss or data leaks may occur. For example, unauthorized access to Redis is a common risk. If the security settings of a Redis database are not properly configured, attackers can obtain sensitive data or damage the database by implementing unauthorized access. | If you have a number of non-web applications, such as MySQL and SQL Server applications for which ports 80, 443, or 8080 are enabled, take note of whether the rules for behaviors such as shellcode and sensitive operations are hit. The rules are also the attack methods that are intended for non-web applications. If you do not have the preceding non-web applications, we recommend that you enable Block Mode - Strict. |
Command execution | If an attacker executes malicious commands, serious consequences may occur. For example, the control permissions of a server may be obtained, sensitive data may be leaked, and other systems may be attacked. For example, attackers may exploit the Log4j vulnerability to execute malicious commands, which poses security threats. | You can use the Block Mode - Loose mode to protect most web applications against common and non-common RCE attacks. This mode also meets your daily protection requirements. RCE attacks are the most harmful among various attacks. If you use the Block Mode - Medium mode to protect against RCE attacks, you must take note of the hit details of rules for each module. If your business is complex and involves a number of non-web applications, we recommend that you enable Block Mode - Strict. |
Scanning | If machines or network devices are overloaded by network scanning, service interruptions or stability issues may occur. As a result, the system may stop responding or the service may become unavailable. | We recommend that you check whether Server Message Block (SMB) named pipes are enabled in your business. SMB named pipes are used for features such as file sharing. If you do not need to use SMB named pipes in your business, we recommend that you disable SMB named pipes to reduce potential security risks. If you need to use SMB named pipes, we recommend that you enable Block Mode - Medium or Block Mode - Strict. |
Information leakage | Information leakage may lead to the violation of personal privacy rights, and unauthorized use of sensitive information, such as ID card numbers, contact information, and financial information. | The definition of information leakage may vary based on your business. Take note of the hit details of rules in Block Mode - Medium and Block Mode - Strict. We recommend that you enable Monitor Mode to monitor the hit details of rules and check whether false positives are reported within a business cycle, such as 24 hours, a week, or a month. If no false positives is reported in Monitor Mode, normal traffic is not identified as a threat. In this case, you can enable Block Mode - Medium or Block Mode - Strict. |
DoS attack | If machines or network devices are overloaded by DoS attacks, service interruptions or stability issues may occur. As a result, the system may stop responding or the service may become unavailable. | DoS attacks are less harmful. You can check whether your service is interrupted or suspended due to unknown causes. If your service is not affected, you can retain the Block Mode - Loose setting. If your business requires a high level of service uptime, you can select Block Mode - Medium or Block Mode - Strict. |
Overflow attack | If machines or network devices are overloaded by overflow attacks, service interruptions or stability issues may occur. As a result, the system may stop responding or the service may become unavailable. | Overflow attacks occur when input points in the binary representation are not strictly controlled. In this case, out-of-bounds access occurs during parameter configuration, and other attacks such as command execution and information leakage are initiated. When you protect against overflow attacks, take note of the hit details of non-web application attacks. If your business mainly involves web applications, you can select Block Mode - Loose. If your business involves a number of non-web applications, we recommend that you select Block Mode - Medium or Block Mode - Strict. |
Web attack | Web attacks are serious security threats. Attackers can obtain control permissions on specific servers and steal sensitive data by initiating web attacks. This may cause service interruptions. | Common web attacks include SQL injections, XSS attacks, and arbitrary files that are listed in Open Web Application Security Project (OWASP) Top 10. To prevent these attacks, we recommend that you perform strict testing during the canary release and official release of the rules. We also recommend that you enable Block Mode - Medium or Block Mode - Strict during routine O&M. |
Trojan | A trojan is a type of malware that can provide continuous unauthorized access to a victim machine. Attackers may access the system again even if system vulnerabilities are fixed. Attackers can monitor the compromised system for a long period of time and steal sensitive data by using a trojan. Systems that are compromised by trojans may lead to legal liabilities, lawsuits, fines, and reputation damage. | In most cases, encryption, obfuscation, and encoding are used in trojan communication to bypass protection measures. In Block Mode - Strict mode, weak features are usually used for detection and blocking. In daily operations, we recommend that you enable the Block Mode - Medium mode. In most cases, encryption, obfuscation, and encoding are used in trojan communication to bypass protection measures. In Block Mode - Strict mode, weak features are usually used for detection and blocking. We recommend that you enable Block Mode - Medium or Block Mode - Strict during routine O&M. |
Worm | A worm is a type of persistent malware that provides continuous unauthorized access to a victim machine. Attackers may access the system again even if system vulnerabilities are fixed. Attackers can monitor the compromised system for a long period of time and steal sensitive data by using a worm. At the same time, systems that are compromised by worms may lead to legal liabilities, lawsuits, fines, and reputation damage. | In most cases, this type of attack compromises hosts. If a rule is hit in Monitor Mode, you must use the traceability analysis feature to identify the source of the attack and take appropriate countermeasures. If no rules are hit, the host is securely running. In this case, we recommend that you enable Block Mode - Medium. |
Mining | Mining is a malicious behavior that occupies bandwidth resources and computing power of machines, which causes system stuttering and affects the system performance. As a result, issues occur, such as slow application running and response latency, which adversely affect efficiency and experience. | In most cases, this type of attack compromises hosts. If a rule is hit in Monitor Mode, you must use the traceability analysis feature to identify the source of the attack and take appropriate countermeasures. If no rules are hit, the host is securely running. In this case, we recommend that you enable Block Mode - Medium. |
Reverse shell | Reverse shells are attack tools that provide continuous unauthorized access to a victim machine. Attackers may access the system again even if system vulnerabilities are fixed. Attackers can monitor the compromised system for a long period of time and steal sensitive data by using a reverse shell. At the same time, systems that are compromised by reverse shells may lead to legal liabilities, lawsuits, fines, and reputation damage. | In most cases, this type of attack compromises hosts. If a rule is hit in Monitor Mode, you must use the traceability analysis feature to identify the source of the attack and take appropriate countermeasures. If no rules are hit, the host is securely running. In this case, we recommend that you enable Block Mode - Medium. |
Others | Attacks that are used for illegal outbound connections and attacks that are caused by outbound connections are included. Attacks that cannot be classified are also included. |
|
Modes of the threat detection engine
The modes of the threat detection engine are the Monitor mode and Block mode. The action of basic protection policies and virtual patching policies varies based on the mode of the threat detection engine. For example, if you set the threat detection engine to the Block - Strict mode, the action of basic protection policies and virtual patching policies is Block. The following list describes the modes of the threat detection engine.
Category | Scenario | Description | Example | |
Monitor | Protection is not supported. | In Monitor mode, the system only records attacks and generates alerts for the attacks. However, the system intercepts attacks in Block mode. | Remote DoS vulnerability in Apache Tomcat (CVE-2014-0075), Atlassian Jira SSRF vulnerability (CVE-2019-16097), and Godlua backdoor software communication | |
Block | Loose | The system blocks attacks in a loose manner by using rules that prevent a high rate of false positives. This level is suitable for business that requires the rate of false positives to be minimized. | In this level, the system detects keywords and key parameters of vulnerability exploits in attack packets and behavior. No false positives can be generated. | RCE vulnerability in Apache Struts 2 (CVE-2018-11776), unauthorized access to Spark REST API (CVE-2018-11770), and Jenkins RCE vulnerability (CVE-2018-1000861) |
Medium | The system blocks attacks in a standard manner. This level is suitable for daily O&M. | In this level, the system uses common rules to detect various types of attacks in a comprehensive manner based on different types of detection methods for vulnerability exploits. This level provides a lower rate of false positives than the Loose level. | RCE vulnerability in Oracle WebLogic Server (CVE-2020-2551), RCE vulnerability in Microsoft WindowsRDP Client (CVE-2020-1374), and SMBv1 DoS attack (CVE-2020-1301) | |
Strict | The system blocks attacks in a strict manner by using all rules. This level is suitable for business that requires the rate of false negatives to be minimized. This level may cause a higher rate of false positives than the Medium level. | In this level, the system detects high-risk vulnerabilities, such as stack overflow and buffer overflow, most of which are Layer-4 protocol vulnerabilities. The system identifies attacks based on various methods such as protocol analysis, keyword matching, multiple redirects, and keyword offset. | Buffer overflow in Squid Proxy HTTP Request Processing (CVE-2020-8450), DoS attack in NGINX 0-Length Headers Leak (CVE-2019-9516), and command injection in Oracle WebLogic | |