API Gateway is a mature cloud service that can be integrated with various architectures. API Gateway allows the access to Kubernetes (K8s) application clusters. This significantly improves the service capabilities of the Kubernetes application clusters. This architecture serves as a standard architecture for large-scale Internet applications. This topic describes how to use API Gateway as the access layer of a K8s cluster.
Overview
K8s clusters
K8s is a widely used automated container platform that is highly praised for its openness. K8s leverages container-based technologies to schedule and scale nodes in clusters. This allows you to easily create an enterprise-level containerized application cluster. This cluster provides the following capabilities:
Automates container deployment and replication.
Scales containers as required.
Groups containers and supports load balancing among the containers.
Easily upgrades containerized applications.
Replaces containers if they fail to work.
Architecture with API Gateway that serves as the access layer
K8s clusters can be used as application services. However, the clusters do not have sufficient access processing capabilities, especially in large-scale applications, in which case the clusters cannot directly provide services due to high security risks. API Gateway serves as the access service to K8s application clusters. This architecture can be used as a standard architecture for large-scale Internet applications. The following figure shows an architecture with Alibaba Cloud API Gateway deployed:
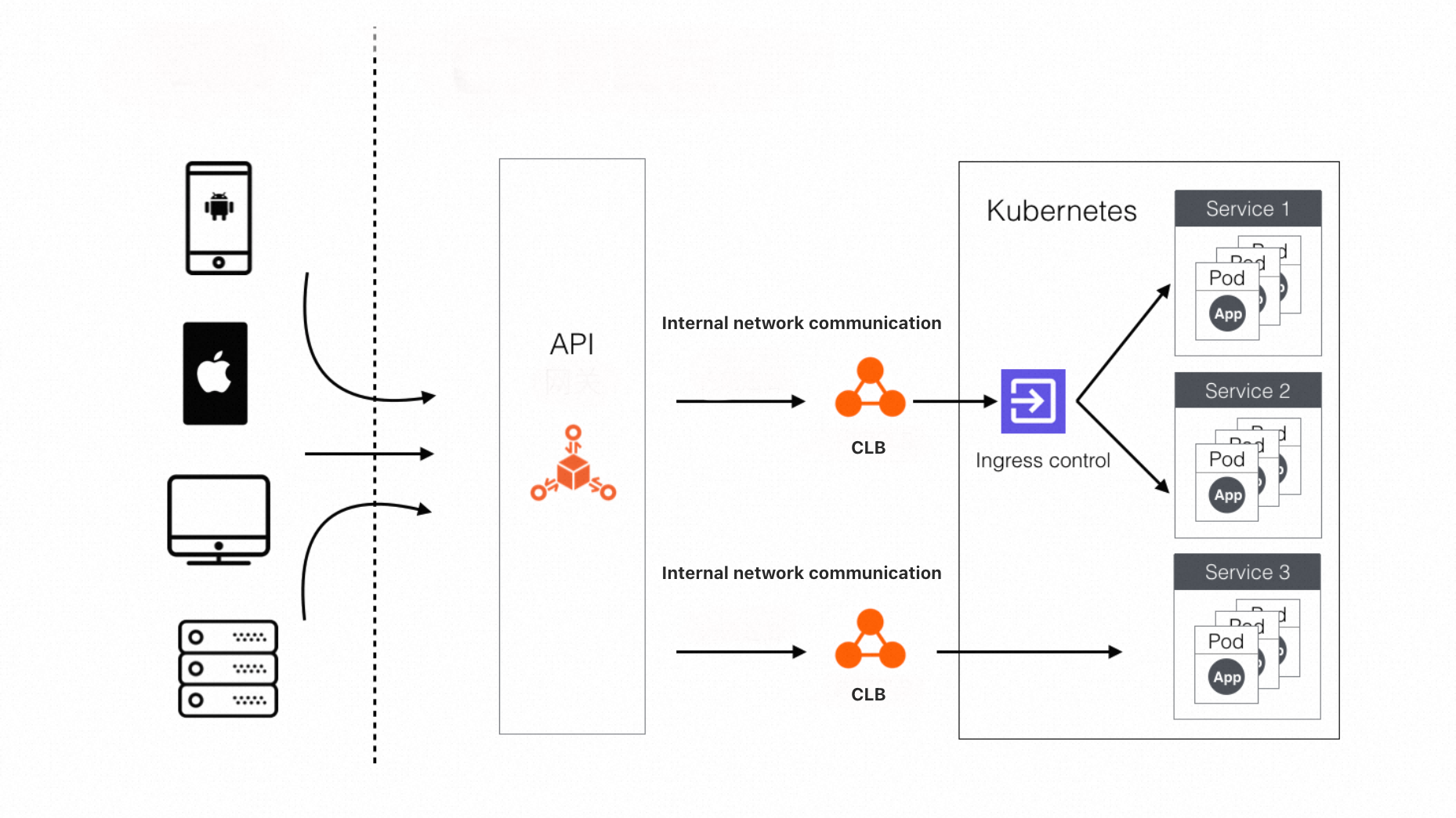
When to use an ingress controller
As shown in the architecture diagram, API Gateway processes client requests for and safeguards a K8s cluster as its bridgehead. API Gateway communicates with the internal Classic Load Balancer (CLB) instance of an ingress controller or that of a service in the K8s cluster. When to use an ingress controller? If the cluster has only one service, API Gateway communicates directly with the internal CLB instance associated with this service. If the cluster has multiple services, API Gateway cannot communicate with the internal CLB instances associated with the services because too many CLB instances complicate resource management. Instead, API Gateway communicates with the CLB instance associated with the ingress controller of the cluster. In this case, the ingress controller helps discover services and forward requests to containers in the cluster. Therefore, only one internal CLB instance is required to provide all services in the cluster.
API Gateway access capabilities
API Gateway brings the following benefits to the entire architecture:
API Gateway communicates with clients in compliance with a variety of protocols. These protocols include:
* HTTP * HTTP2API Gateway uses various methods to secure communications with clients.
* Defines an authorization relationship between APIs and apps. Only the authorized apps are allowed to call APIs. * Provides a full-link signature authentication mechanism for the communication between clients and API Gateway, and between API Gateway and backend services. This mechanism prevents data tampering during the transmission of requests. * Allows you to use your SSL certificates for HTTPS communication. * Supports the OpenID Connect security certification method.API Gateway automatically generates SDKs for iOS, SDKs for Android, and SDKs for Java. It also automatically generates API calling documents.
API Gateway supports mapping between frontend and backend parameters. Parameters in a request can be mapped to any parameter location in a backend request.
API Gateway supports parameter cleansing. When you define an API, you can specify rules such as the parameter type and regular expression. API Gateway helps you determine whether the parameters in a request to be transmitted to backend services conform to the rules.
API Gateway supports throttling by user, app, or API.
API Gateway supports monitoring and alerting based on the number of requests, the number of errors, response timeout, and traffic. All alerts are sent by using text messages or emails within one minute after an error occurs.
API Gateway is integrated with Alibaba Cloud Simple Log Service. All request logs can be automatically uploaded to your Simple Log Service resources for statistical analysis.
API Gateway supports the Mock mode, which is efficient at joint debugging between different departments.
API Gateway allows you to configure IP address whitelists and blacklists for callers.
API Gateway allows API providers to charge API callers for API calls in Alibaba Cloud Marketplace.
Alibaba Cloud API Gateway is a mature cloud service that has been released for years. Its stability and performance have been refined over the years by Alibaba Cloud engineers. API Gateway can meet your high performance requirements.
Quickly configure K8s clusters and API Gateway in Alibaba Cloud
Alibaba Cloud allows you to quickly create K8s clusters. API Gateway can be easily integrated with K8s clusters in the same region. The following sections describe how to build the architecture described in Section 2 Architecture with API Gateway that serves as the access layer in Alibaba Cloud.
Method 1: API Gateway sends requests to the CLB instance preceding the ingress controller, which routes the requests to the corresponding node in the K8s cluster. This method requires only one CLB instance that precedes the ingress controller. The ingress controller discovers services and routes requests.
Method 2: API Gateway directly sends requests to the CLB instances preceding services in K8s. K8s directly forwards the requests to the corresponding node in the K8s cluster. This method requires a CLB instance to precede each service and is suitable for high-concurrency scenarios.
Configuration in method 1
Create a K8s cluster and install an Ingress
When you create an ACK managed or Serverless cluster, select ALB Ingress for Ingress in the Component Configurations step. For more information, see Create an ACK managed cluster and Create an ACK Serverless cluster.

Create a multi-container service in a cluster
Perform the following operations to create a service that consists of two containers in the K8s cluster. Each container is generated by using an Nginx image. The container port is 80. The service port of the ingress controller is 80.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Deployments page, click Create from YAML. Enter the following Resource Orchestration Service text and click Create.
apiVersion: apps/v1 kind: Deployment metadata: name: nginx-demo labels: app: nginx spec: replicas: 2 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: anolis-registry.cn-zhangjiakou.cr.aliyuncs.com/openanolis/nginx:1.14.1-8.6 ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginx-service spec: ports: - port: 80 protocol: TCP targetPort: 80 selector: app: nginx sessionAffinity: None type: NodePortNoteDescription:
Two containers are created based on an Nginx image, and the container service port is 80. A service named nginx-service is created, and the service port is 80, which maps to the 80 port of the container service.
An Nginx service is running in each of the containers. The two containers form a stateless application and support a service named nginx-service. You can go to the details page of the stateless application and view its running status. Currently, API Gateway cannot access this service. You need to create an ingress on the ingress controller that routes requests to this service for end-to-end communication.
Create an ingress on the ingress controller that routes requests to a service
Deploy a service for the stateless application and create an ingress for this service on the ingress controller. This way, when API Gateway sends requests to K8s services, the ingress controller forwards the requests to appropriate K8s services based on configured ingress information. Follow these steps to create an ingress:
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
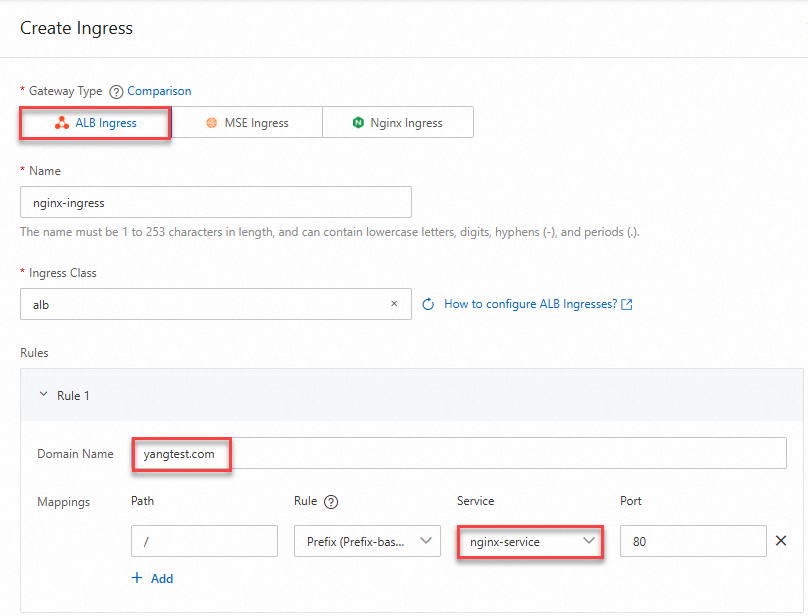
Click Create Ingress. In the Rules section, configure the domain name and path mapping and click OK.
Create an access authorization for the VPC of the internal CLB instance
If you want API Gateway to access the internal CLB instance of the ingress controller, you must configure a VPC access authorization in the API Gateway console.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
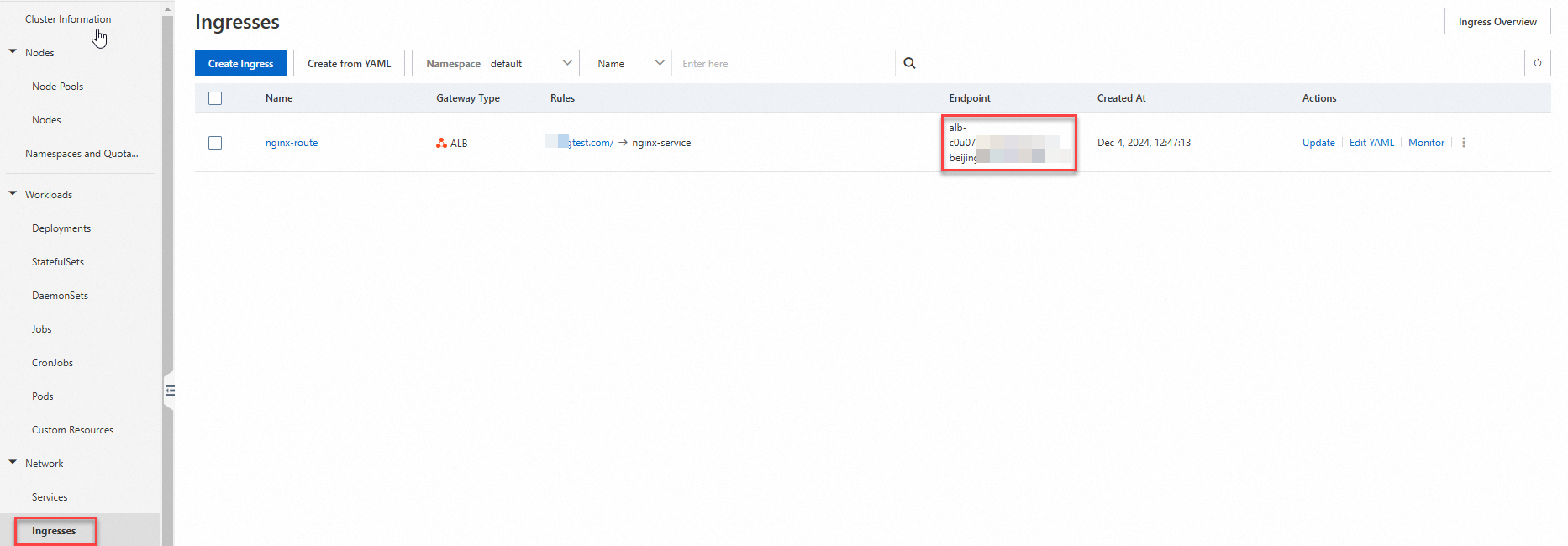
On the Ingresses page, copy the endpoint.
- Log on to the ALB console.
In the left-side navigation pane, click Overview. In the Resources section, paste the copied endpoint and click the retrieved ALB instance.
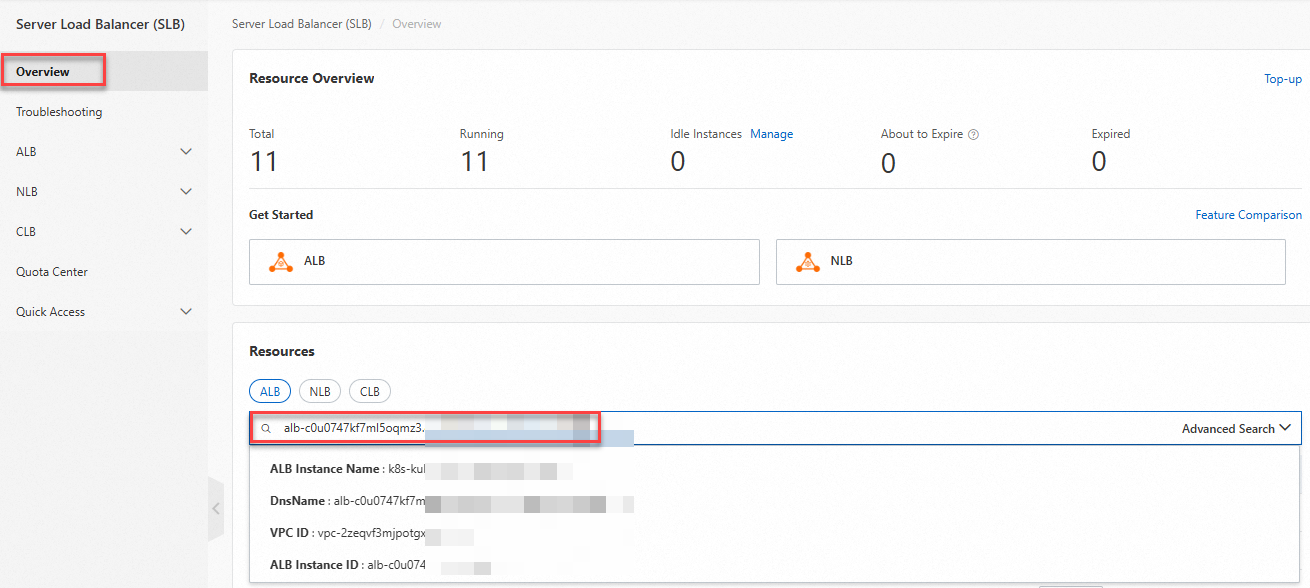
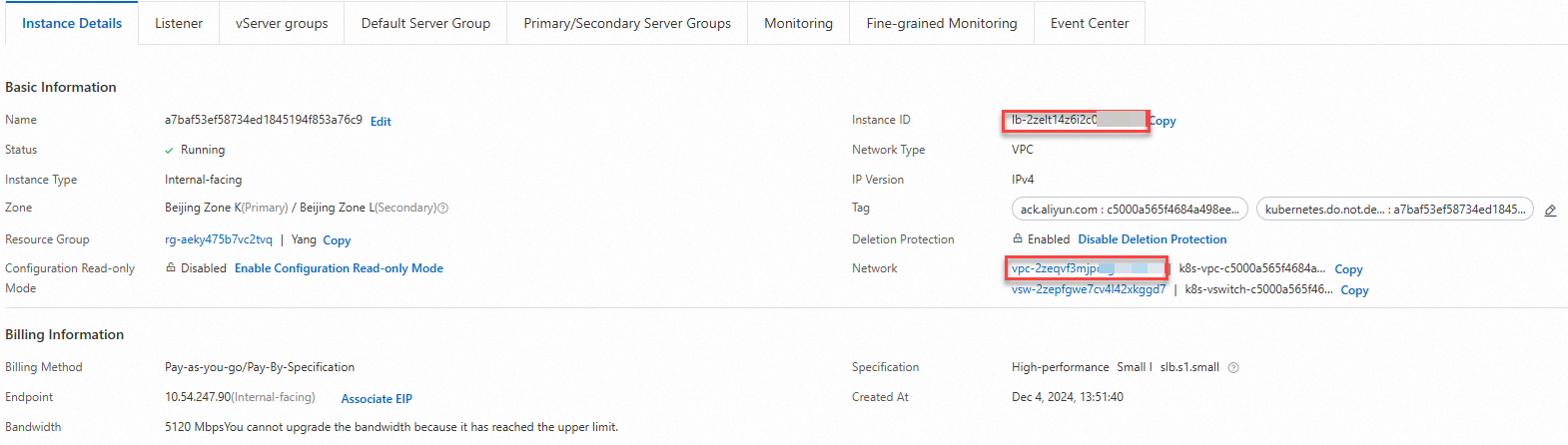
On the Instance Details tab, copy the VPC ID and the domain name of the ALB instance.
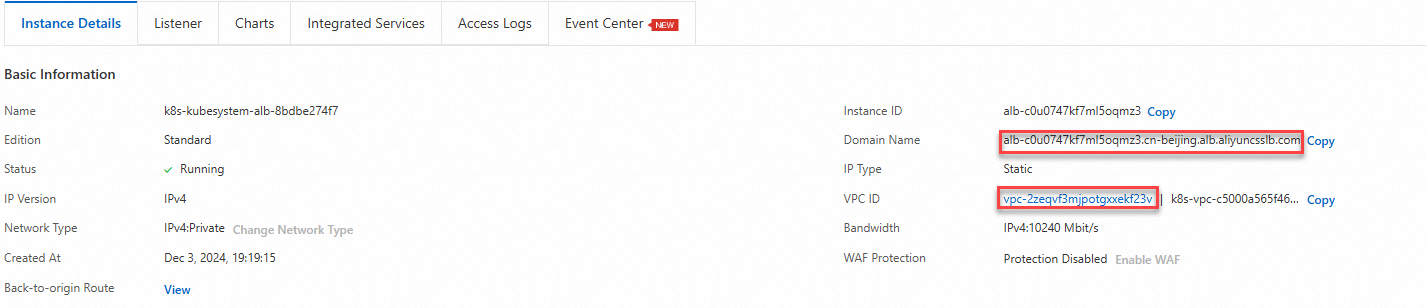
Log on to the API Gateway console. In the top navigation bar, select a region. In the left-side navigation pane, choose Manage APIs > VPCs.
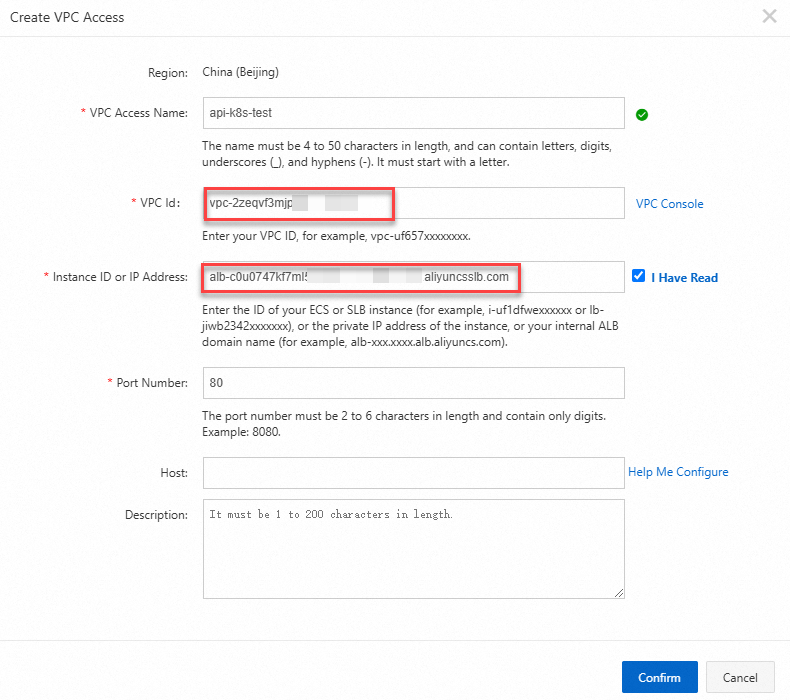
On the VPC Access Authorizations page, click Create Authorization in the upper-right corner.
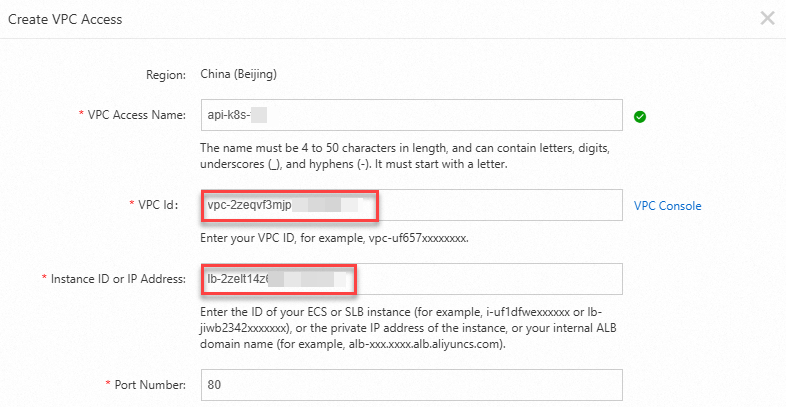
In the Create VPC Access dialog box, specify the VPC Access Name, VPC Id, Instance ID or IP Address, and Port Number parameters. Then, click Confirm.
Create an API
Log on to the API Gateway console. In the left-side navigation pane, choose Manage APIs > API Groups.
On the API Groups page, find the created group and click Manage APIs in the Actions column.
On the APIs page, click Create API in the upper-right corner.
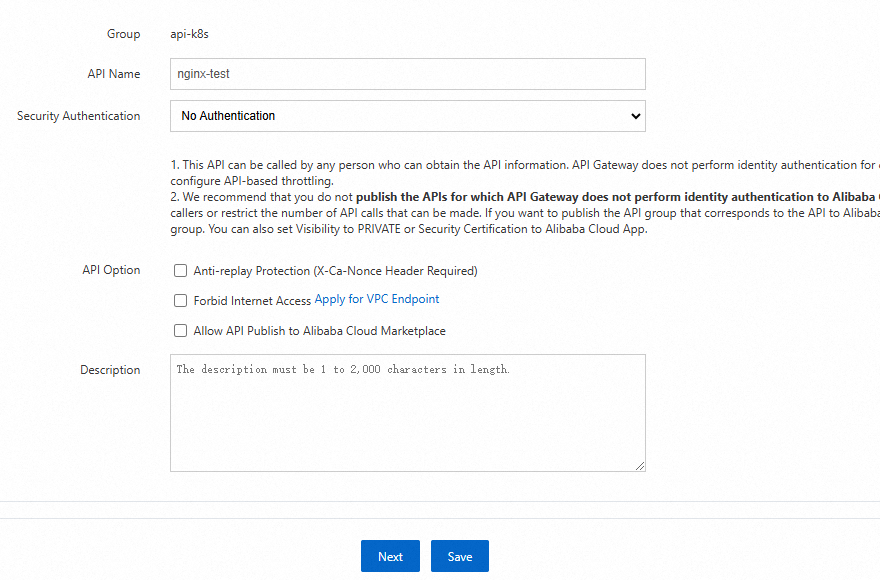
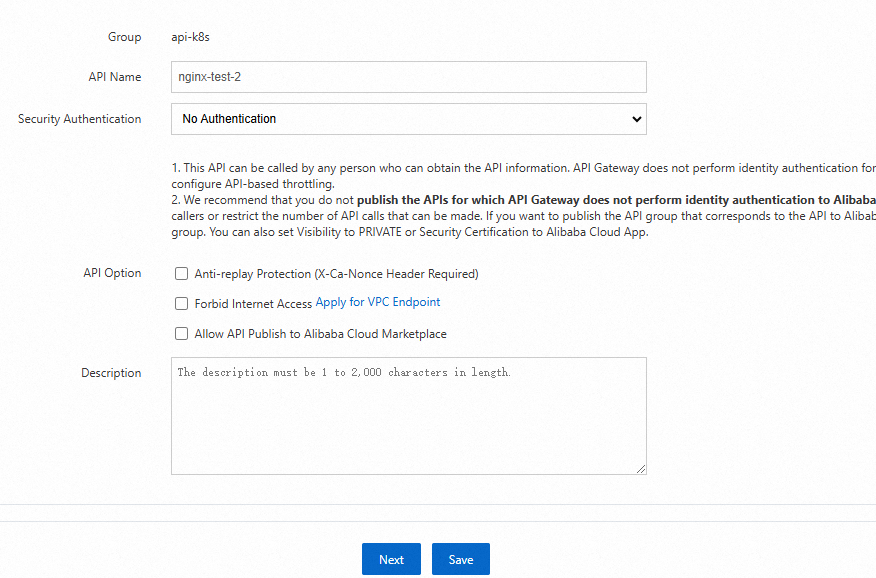
In the Basic Information step of the Create API wizard, configure the following parameters and click Next.
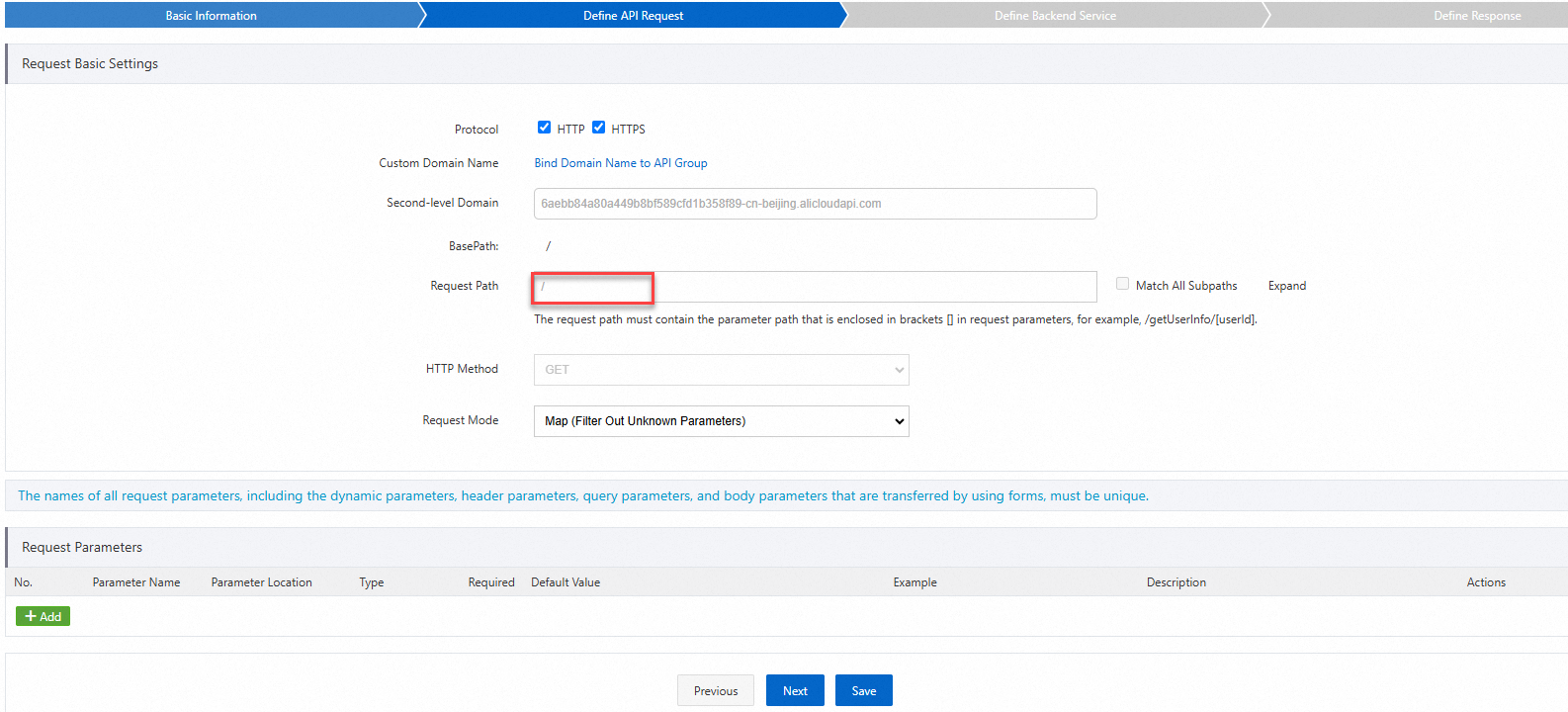
In the Define API Request step, configure the following parameters and click Next.
In the Define Backend Service step, configure the following parameters and click Next.
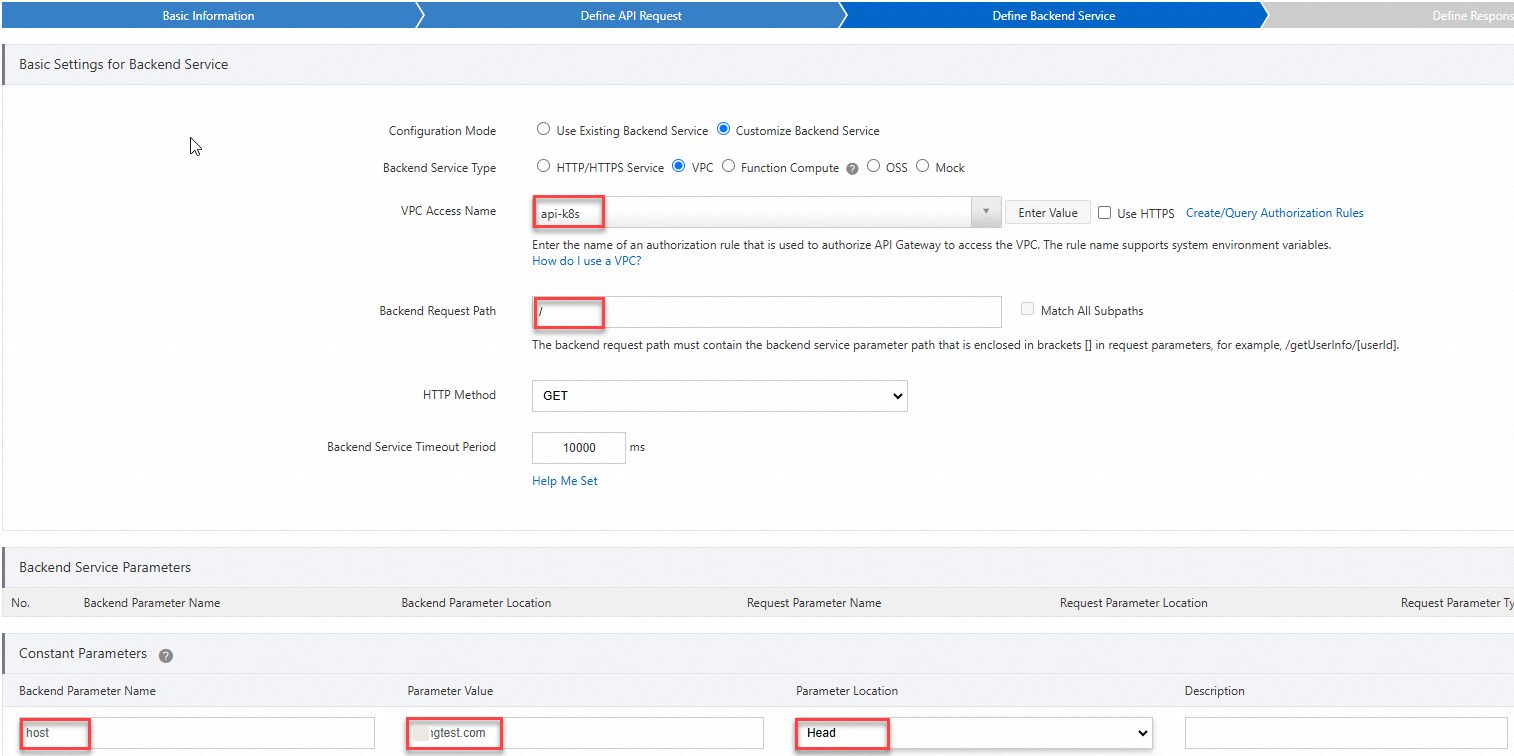 Important
ImportantWhen you create an API, you can add a constant parameter whose name is host, location is header, and value is the domain name of the ingress configured for the service in the ingress controller.
In the Define Response step, configure the parameters on the page based on your business requirements and then click Create.
In the message that appears, click Publish.
In the Publish API dialog box that appears, set Environment to Release, enter remarks in the Remarks section, and then click Publish.
Debug the API
After an API is created and published, you can test whether requests can be sent to the created K8s cluster in the API Gateway console.
Log on to the API Gateway console. In the left-side navigation pane, choose Call APIs > Debug.
On the Debug API page, select the
nginx-testAPI that you created and then click Send Request. The following information indicates that the configuration is successful.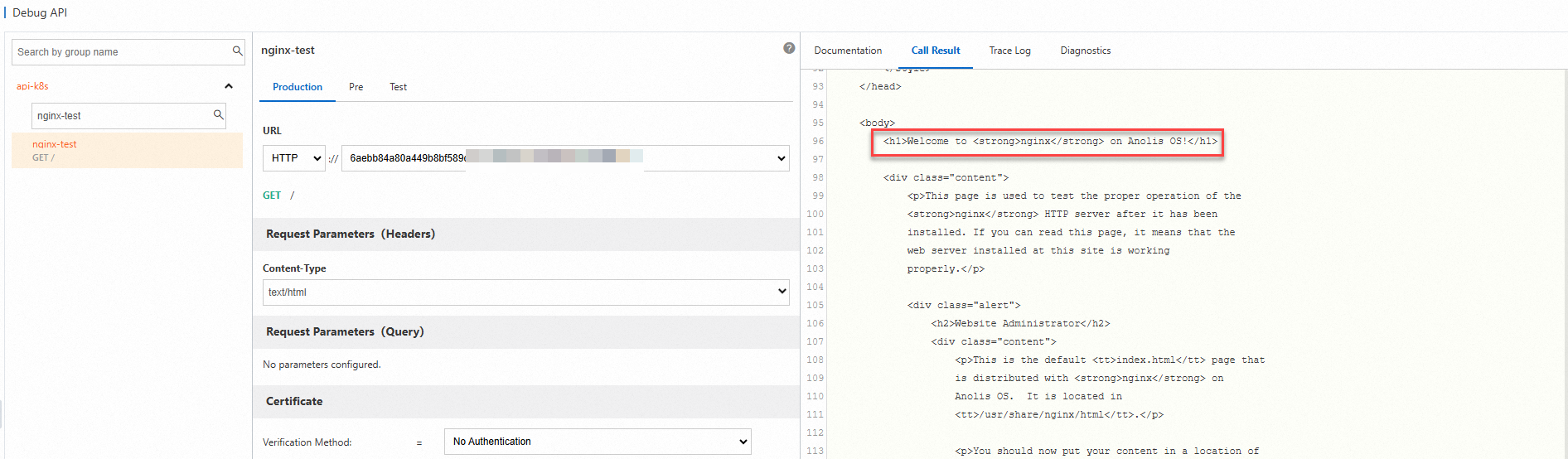
Configuration in method 2
This section describes how to create a K8s service that has an internal CLB instance.
Create an ACK cluster
For more information, see Create an ACK managed cluster or Create an ACK Serverless cluster.
Create a multi-container service in a cluster
You can use the following template to create a service that has an internal CLB instance in this cluster. Take note that the following code is different from the sample code in Configuration in method 1, in the last line of which Type is set to LoadBalancer and the CLB instance is specified as an internal instance.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Deployments page, click Create from YAML. Enter the following Resource Orchestration Service text and click Create.
apiVersion: apps/v1 kind: Deployment metadata: name: nginx-demo labels: app: nginx spec: replicas: 2 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: anolis-registry.cn-zhangjiakou.cr.aliyuncs.com/openanolis/nginx:1.14.1-8.6 ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginx-service annotations: service.beta.kubernetes.io/alicloud-loadbalancer-address-type: intranet spec: ports: - port: 80 targetPort: 80 protocol: TCP selector: app: nginx type: LoadBalancerNoteTwo containers are created based on an Nginx image, and the container service port is 80. A service named nginx-service is created, and an internal CLB instance precedes the service. The service port of the CLB instance is 80, which maps to the 80 port of the container service.
Grant permissions on the CLB instance
On the details page of your cluster, choose Network > Services. On the Services page that appears, find the endpoint of the internal CLB instance that precedes the created service.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Services page, copy the IP address in the External IP column.
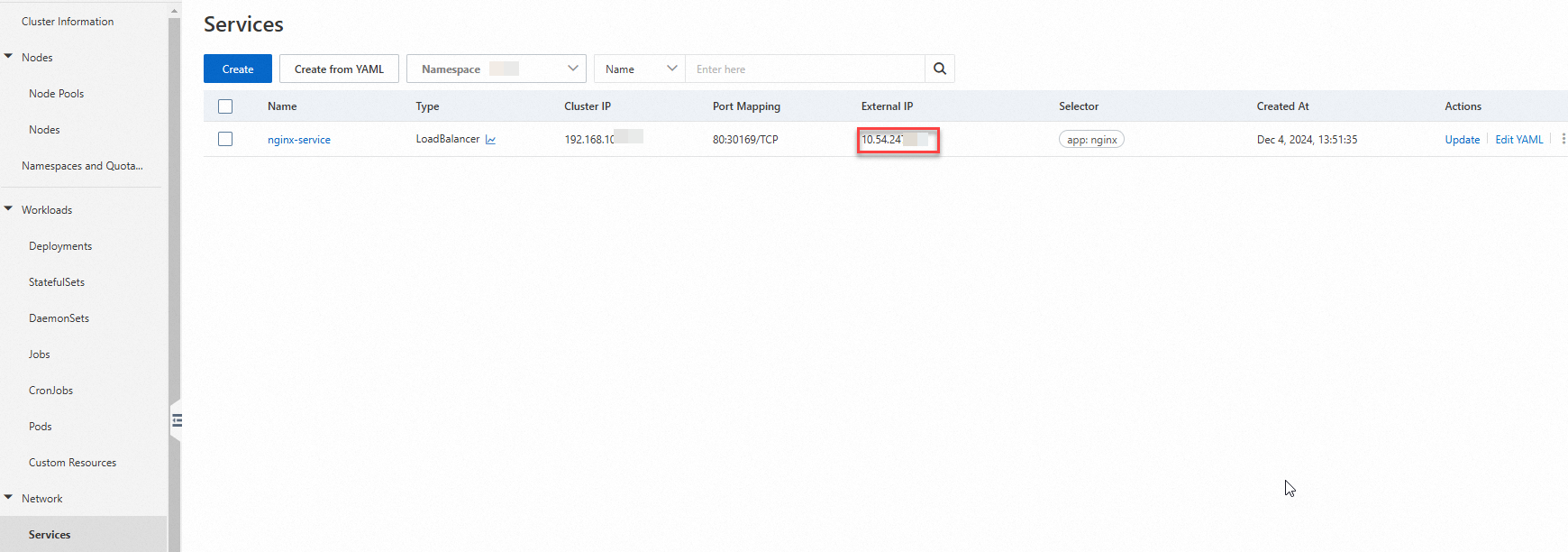
- Log on to the ALB console.
In the left-side navigation pane, click Overview. In the Resources section, paste the copied IP address and click the retrieved CLB instance.
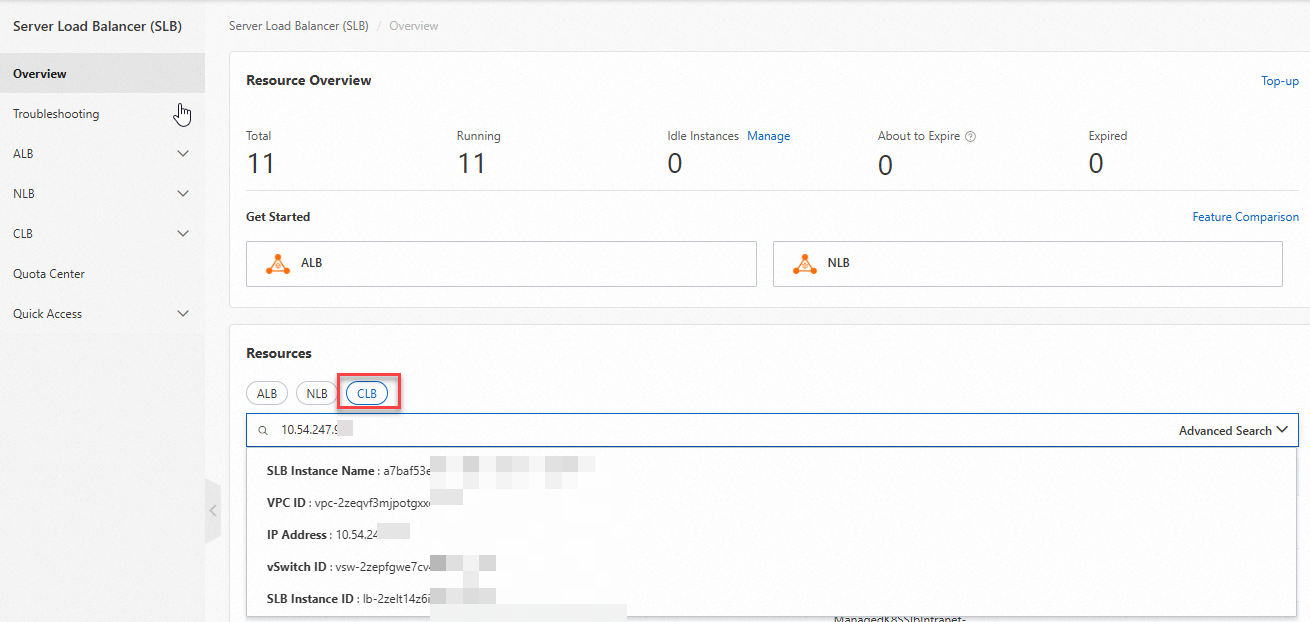
On the Instance Details tab, copy the VPC ID and the domain name of the CLB instance.
Log on to the API Gateway console. In the top navigation bar, select a region. In the left-side navigation pane, choose Manage APIs > VPCs.
On the VPC Access Authorizations page, click Create Authorization in the upper-right corner.
In the Create VPC Access dialog box, specify the VPC Access Name, VPC Id, Instance ID or IP Address, and Port Number parameters. Then, click Confirm.
Create an API
Log on to the API Gateway console. In the left-side navigation pane, choose Manage APIs > API Groups.
On the API Groups page, find the created group and click Manage APIs in the Actions column.
On the APIs page, click Create API in the upper-right corner.
In the Basic Information step of the Create API wizard, configure the following parameters and click Next.
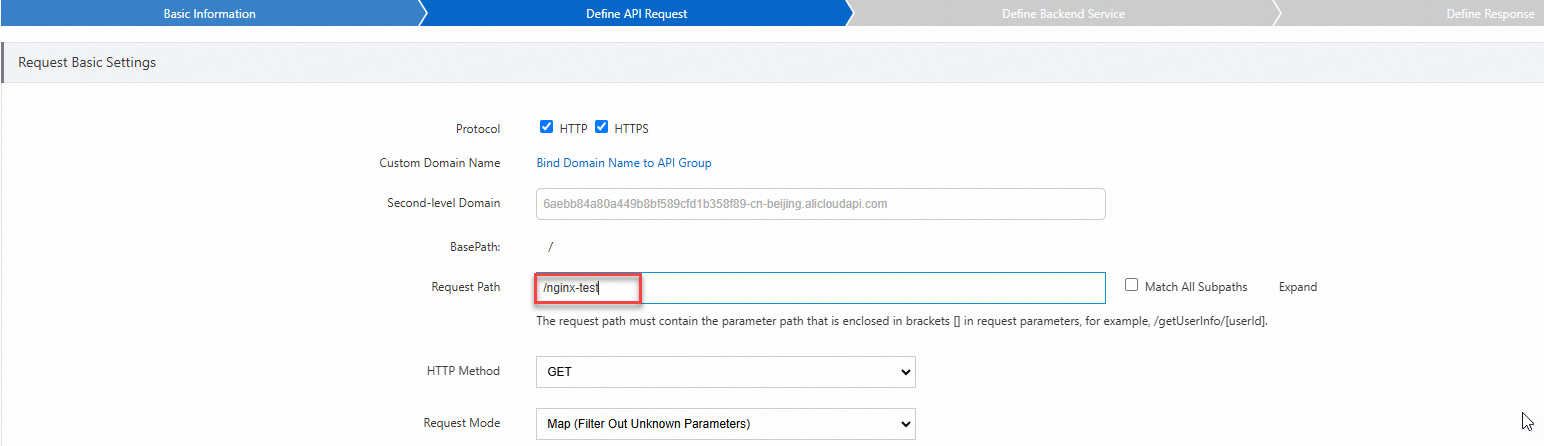
In the Define API Request step, configure the following parameters and click Next.
In the Define Backend Service step, configure the following parameters and click Next.
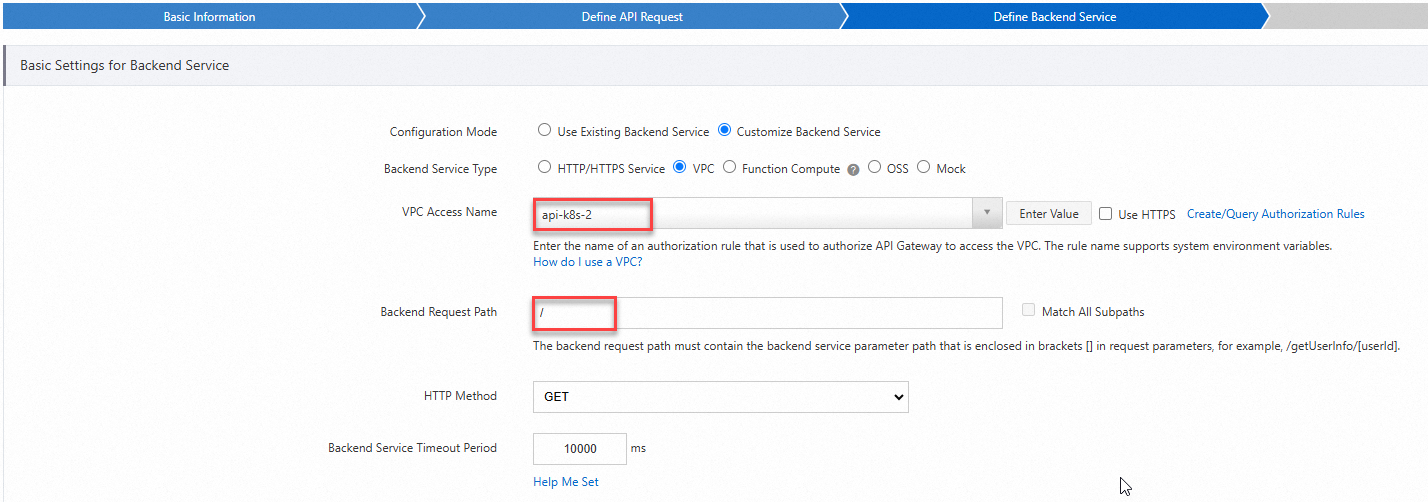
In the Define Response step, configure the parameters on the page based on your business requirements and then click Create.
In the message that appears, click Publish.
In the Publish API dialog box that appears, set Environment to Release, enter remarks in the Remarks section, and then click Publish.
Debug the API
After an API is created and published, you can test whether requests can be sent to the created K8s cluster in the API Gateway console.
Log on to the API Gateway console. In the left-side navigation pane, choose Call APIs > Debug.
On the Debug API page, select the
nginx-test-2API that you created and then click Send Request. The following information indicates that the configuration is successful.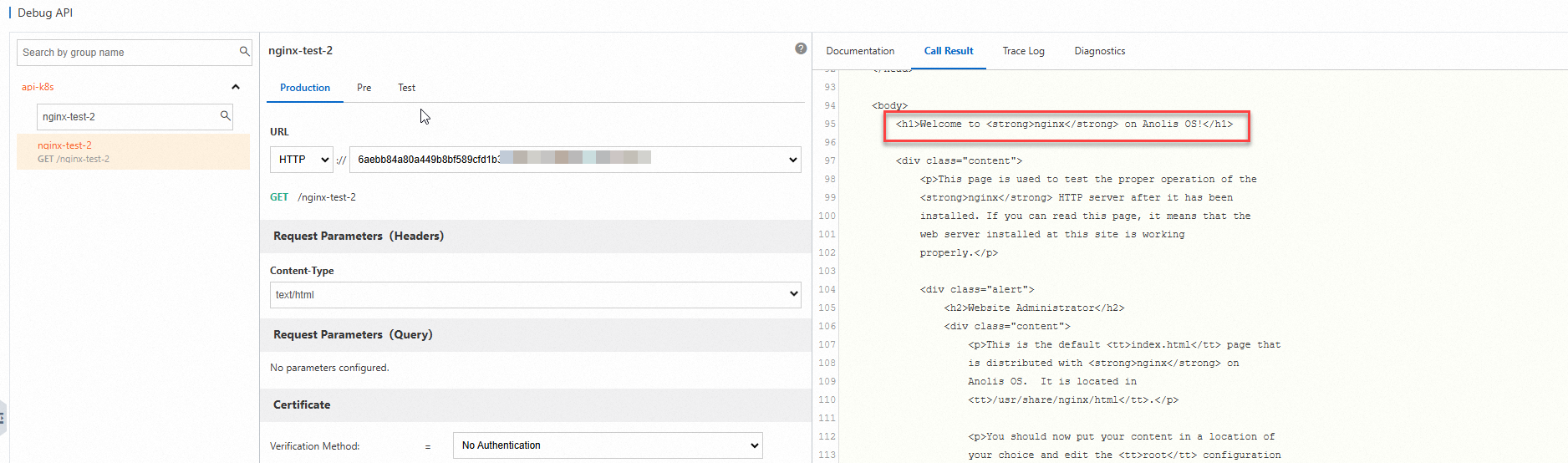
Summary
This topic describes how to use API Gateway in K8s clusters. The key lies in the use of an ingress controller to discover services and the use of a VPC access authorization to route requests to CLB instances. Configuration procedure in method 1:
Create a K8s cluster with an ingress controller installed.
Execute resource orchestration code to create two containers on which Nginx runs and create a service supported by these containers.
Create an ingress that routes requests to the service on the ingress controller.
Obtain the IDs of your VPC and the CLB instance associated with the ingress controller and create a VPC access authorization in API Gateway.
Create an API in the API Gateway console. Remember to use the created VPC access authorization for the backend service and add a constant parameter named host whose value must be set to the domain name of the ingress. This way, API requests are sent to the CLB instance associated with the ingress controller, and the ingress controller routes the requests to the Nginx service in containers.
For high-concurrency or single-service scenarios, you can directly associate a CLB instance with the service and authorize API Gateway to access the CLB instance.
Comparison between the two methods
CLB + ingress controller: An ingress controller can be used for service discovery and application-layer proxy for K8s clusters. If a K8s cluster contains multiple services, an ingress controller can be used to route requests by using only one internal CLB instance. This facilitates O&M and K8s cluster service addition. This method is recommended.
CLB only: If a service has heavy loads in a cluster, you can create a separate CLB instance for the service and connect API Gateway directly to this CLB instance for higher communication efficiency. However, if you configure a CLB instance for each of multiple services in a cluster, O&M and management become complicated.
Conclusion
This topic describes the capabilities provided by K8s clusters and API Gateway and also an architecture in which K8s clusters and API Gateway are integrated as backend application services. This architecture achieves higher availability, reliability, and flexibility. The system supports dynamic scaling, dynamic routing, multi-protocol access, and automatic SDK generation.