By default, Resource Access Management (RAM) users lack access to cloud service APIs. To use Distributed Cloud Container Platform for Kubernetes (ACK One) through RAM users or RAM roles, operational permissions must be granted for specific actions, such as Fleet instance creation, cluster association, and workflow cluster provisioning. ACK One provides default system permission policies to control global read and write permissions. This topic describes how to attach system permission policies to RAM users or RAM roles.
Usage notes
You need to grant permissions to a RAM user or RAM role by using an Alibaba Cloud account or RAM administrator account. You cannot grant permissions by using a RAM user.
System permission policies supported by ACK One
RAM system policy | Permission | Cluster involved | ||
Registered clusters | Fleet instances | Workflow clusters | ||
AliyunAdcpFullAccess | Provides read and write permissions on all ACK One resources. | Yes | Yes | Yes |
AliyunAdcpReadOnlyAccess | Provides read-only permissions on all ACK One resources. | Yes | Yes | Yes |
AliyunCSFullAccess | Provides read and write permissions on all Container Service for Kubernetes (ACK) resources. | Yes | Yes | No |
AliyunCSReadOnlyAccess | Provides read-only permissions on all ACK resources. | Yes | Yes | No |
AliyunVPCReadOnlyAccess | Provides permissions to specify a virtual private cloud (VPC) for an ACK cluster to be created. | Yes | Yes | Yes |
AliyunECIReadOnlyAccess | Provides permissions to schedule pods to elastic container instances. | Yes | Yes | Yes |
AliyunLogReadOnlyAccess | Provides permissions to select an existing log project to store logs for an ACK cluster to be created or view the configuration inspection information of an ACK cluster. | Yes | Yes | Yes |
AliyunARMSReadOnlyAccess | Provides permissions to view the monitoring data of the Managed Service for Prometheus plug-in in an ACK cluster. | Yes | Yes | Yes |
AliyunRAMReadOnlyAccess | Provide permissions to view existing RAM policies. | Yes | Yes | Yes |
AliyunECSReadOnlyAccess | Provides permissions to add existing nodes in the cloud to an ACK cluster or view node details. | Yes | No | No |
AliyunContainerRegistryReadOnlyAccess | Provides permissions to view application images within an Alibaba Cloud account. | Yes | No | No |
AliyunAHASReadOnlyAccess | Provides permissions to use the cluster topology feature. | Yes | No | No |
AliyunYundunSASReadOnlyAccess | Provides permissions to view the runtime monitoring data of an ACK cluster. | Yes | No | No |
AliyunKMSReadOnlyAccess | Provides permissions to enable the Secret encryption feature when you create an ACK cluster. | Yes | No | No |
AliyunESSReadOnlyAccess | Provides permissions to perform node pool-related operations in the cloud, such as the permissions to view, modify, and scale node pools. | Yes | No | No |
Grant permissions to a RAM user or RAM role
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
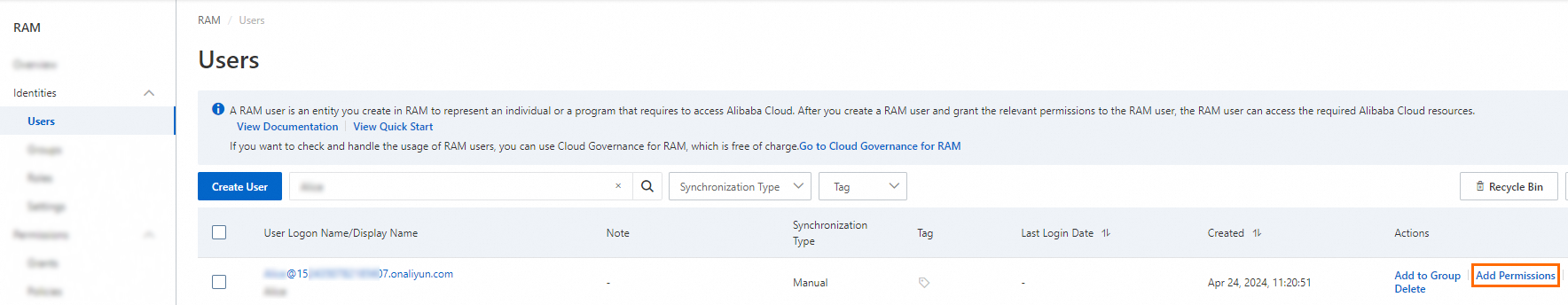
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Grant Permission panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. The current RAM user is automatically selected.
Configure the Policy parameter.
A policy contains a set of permissions. Policies can be classified into system policies and custom policies. You can select multiple policies at a time.
System policies: policies that are created by Alibaba Cloud. You can use but cannot modify these policies. Version updates of the policies are maintained by Alibaba Cloud. For more information, see Services that work with RAM.
NoteThe system automatically identifies high-risk system policies, such as AdministratorAccess and AliyunRAMFullAccess. We recommend that you do not grant unnecessary permissions by attaching high-risk policies.
Custom policies: You can manage and update custom policies based on your business requirements. You can create, update, and delete custom policies. For more information, see Create a custom policy.
Click Grant permissions.
References
RAM system permission policies can be used to control permissions only on ACK One resources. If a RAM user or RAM role needs to manage Kubernetes resources in the specified cluster, such as creating GitOps applications and workflows, you must grant the RAM user or RAM role Role-Based Access Control (RBAC) permissions on the ACK One Fleet instance, workflow cluster, and their namespaces. For more information, see Grant RBAC permissions to a RAM user or RAM role.