实例标识,包括实例标识文档和实例标识签名,可用于快速辨识并区分ECS实例,为应用程序权限控制和软件激活等提供重要的信任基础。本文主要介绍实例标识的定义、应用场景、获取方式以及使用示例。
什么是实例标识
实例标识由动态生成的实例标识文档(document)和实例标识签名(signature)组成。
实例标识文档
用于提供实例的身份信息,包括实例ID、IP地址等,包含的属性如下表所示。
属性
描述
owner-account-id
实例所属用户账号ID
instance-id
实例ID
mac
实例主网卡MAC地址
region-id
实例所属的地域ID
serial-number
实例的序列号
zone-id
实例所属可用区ID
instance-type
实例规格
image-id
实例使用的镜像ID
private-ipv4
实例的私网IPv4地址
实例标识签名
供第三方验证实例标识文档的真实性和内容。实例标识签名采用PKCS#7格式加密,纯数字化,安全可靠。
实例标识签名支持传入自定义
audience参数,用于防止签名被非法冒用。audience参数可以是随机字符串、时间戳、规律性变化的信息或者根据算法生成的数据。传入audience参数后,即使他人获取了标识文档和标识签名的部分信息,也很难猜测到audience参数的取值。通过audience参数实现鉴权。具体使用,请参见使用实例标识。
应用场景
在以下场景中,您可以借助实例标识实现鉴权、授权或者判断运行环境等:
传统的线下手动激活的软件授权是一码单用,但由于云上软件的使用时间及场景多变,您可以在云市场上架应用软件时使用实例标识灵活地完成用户授权。
当您在ECS实例中写入敏感数据时,您可以使用实例标识来确保当前所写入的位置是您的ECS实例而不是其他环境。
其他需要确认目标服务器来源的场景。
获取实例标识文档/签名
(推荐)加固模式下获取
Linux实例
# 获取服务器访问凭证,需设置有效期,不可包含标头X-Forwarded-For TOKEN=`curl -X PUT "http://100.100.100.200/latest/api/token" -H "X-aliyun-ecs-metadata-token-ttl-seconds:<服务器访问凭证有效期>"` # 获取实例标识 curl -H "X-aliyun-ecs-metadata-token: $TOKEN" http://100.100.100.200/latest/<dynamic data>Windows实例
# 获取服务器访问凭证,需设置有效期,不可包含标头X-Forwarded-For $token = Invoke-RestMethod -Headers @{"X-aliyun-ecs-metadata-token-ttl-seconds" = "<服务器访问凭证有效期>"} -Method PUT -Uri http://100.100.100.200/latest/api/token # 获取实例标识 Invoke-RestMethod -Headers @{"X-aliyun-ecs-metadata-token" = $token} -Method GET -Uri http://100.100.100.200/latest/<dynamic data><服务器访问凭证有效期>:访问凭证用于鉴权以加强数据安全。有效期取值范围为1~21600,单位为秒。在有效期内可重复使用实例标识获取命令获取数据;超过有效期后,凭证失效需重新获取。
访问凭证仅适用于一台实例,如果将凭证复制到其他实例使用,将会被拒绝访问。
<dynamic data>:需替换为具体的实例标识文档/签名。实例标识文档:dynamic/instance-identity/document
实例标识签名:dynamic/instance-identity/pkcs7?audience=XXXX
重要?audience=XXXX非必填,具体说明,请参见实例标识签名。
普通模式下获取
Linux实例
curl http://100.100.100.200/latest/<dynamic data>Windows实例(PowerShell)
Invoke-RestMethod http://100.100.100.200/latest/<dynamic data><dynamic data>:需替换为具体的实例标识文档或签名。实例标识文档:dynamic/instance-identity/document
实例标识签名:dynamic/instance-identity/pkcs7?audience=XXXX
重要?audience=XXXX非必填,具体说明,请参见实例标识签名。
使用实例标识
以下操作以Alibaba Cloud Linux 3系统为例,介绍在加固模式下如何使用实例标识。
认证和使用实例标识需要OpenSSL支持,从而确保实例标识的安全性。如果您没有配置OpenSSL服务,请前往OpenSSL官网下载并安装OpenSSL服务。
远程连接Linux实例。
具体操作,请参见使用Workbench登录Linux实例。
(可选)执行以下命令,查看实例标识文档和实例标识签名。
# 获取服务器访问凭证,设置有效期为3600秒 TOKEN=`curl -X PUT "http://100.100.100.200/latest/api/token" -H "X-aliyun-ecs-metadata-token-ttl-seconds:3600"` # 获取实例标识文档 curl -H "X-aliyun-ecs-metadata-token: $TOKEN" http://100.100.100.200/latest/dynamic/instance-identity/document # 获取实例标识签名 curl -H "X-aliyun-ecs-metadata-token: $TOKEN" http://100.100.100.200/latest/dynamic/instance-identity/pkcs7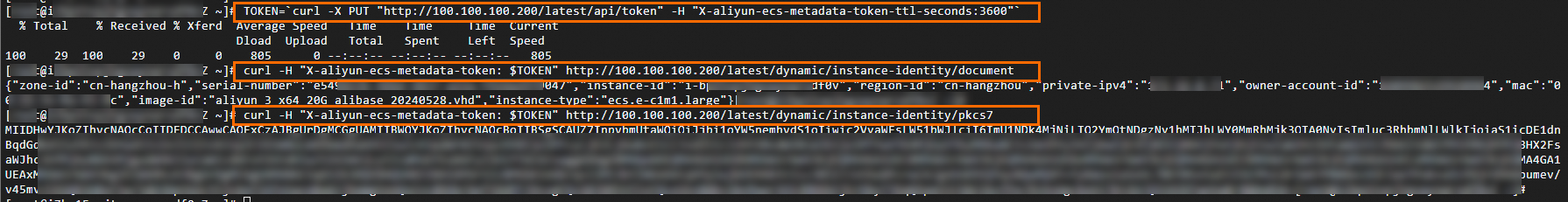
将实例标识文档、实例标识签名及阿里云公有证书内容保存至文件。
执行以下命令,将实例文档信息保存至document文件。
curl 100.100.100.200/latest/dynamic/instance-identity/document > document执行以下命令,将实例签名信息保存至signature文件。
echo "-----BEGIN CERTIFICATE-----" > signature curl 100.100.100.200/latest/dynamic/instance-identity/pkcs7 >> signature echo "" >> signature echo "-----END CERTIFICATE-----" >> signature执行以下命令,将阿里云公有证书保存至cert.cer文件。
cat <<EOF > cert.cer -----BEGIN CERTIFICATE----- MIIDdzCCAl+gAwIBAgIEZmbRhzANBgkqhkiG9w0BAQsFADBsMRAwDgYDVQQGEwdV bmtub3duMRAwDgYDVQQIEwdVbmtub3duMRAwDgYDVQQHEwdVbmtub3duMRAwDgYD VQQKEwdVbmtub3duMRAwDgYDVQQLEwdVbmtub3duMRAwDgYDVQQDEwdVbmtub3du MB4XDTE4MDIyMzAxMjkzOFoXDTM4MDIxODAxMjkzOFowbDEQMA4GA1UEBhMHVW5r bm93bjEQMA4GA1UECBMHVW5rbm93bjEQMA4GA1UEBxMHVW5rbm93bjEQMA4GA1UE ChMHVW5rbm93bjEQMA4GA1UECxMHVW5rbm93bjEQMA4GA1UEAxMHVW5rbm93bjCC ASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAIJwy5sbZDiNyX4mvdP32pqM YMK4k7+5lRnVR2Fky/5uwyGSPbddNXaXzwEm+u4wIsJiaAN3OZgJpYIoCGik+9lG 5gVAIr0+/3rZ61IbeVE+vDenDd8g/m/YIdYBfC2IbzgS9EVGAf/gJdtDODXrDfQj Fk2rQsvpftVOUs3Vpl9O+jeCQLoRbZYm0c5v7jP/L2lK0MjhiywPF2kpDeisMtnD /ArkSPIlg1qVYm3F19v3pa6ZioM2hnwXg5DibYlgVvsIBGhvYqdQ1KosNVcVGGQa HCUuVGdS7vHJYp3byH0vQYYygzxUJT2TqvK7pD57eYMN5drc7e19oyRQvbPQ3kkC AwEAAaMhMB8wHQYDVR0OBBYEFAwwrnHlRgFvPGo+UD5zS1xAkC91MA0GCSqGSIb3 DQEBCwUAA4IBAQBBLhDRgezd/OOppuYEVNB9+XiJ9dNmcuHUhjNTnjiKQWVk/YDA v+T2V3t9yl8L8o61tRIVKQ++lDhjlVmur/mbBN25/UNRpJllfpUH6oOaqvQAze4a nRgyTnBwVBZkdJ0d1sivL9NZ4pKelJF3Ylw6rp0YMqV+cwkt/vRtzRJ31ZEeBhs7 vKh7F6BiGCHL5ZAwEUYe8O3akQwjgrMUcfuiFs4/sAeDMnmgN6Uq8DFEBXDpAxVN sV/6Hockdfinx85RV2AUwJGfClcVcu4hMhOvKROpcH27xu9bBIeMuY0vvzP2VyOm DoJeqU7qZjyCaUBkPimsz/1eRod6d4P5qxTj -----END CERTIFICATE----- EOF
执行以下命令,使用OpenSSL服务验证实例标识。
openssl smime -verify -in signature -inform PEM -content document -certfile cert.cer -noverify > /dev/null若标识返回结果为
Verification successful,表示实例身份验证成功。上述命令中相关参数说明如下:
document:包含您获取的标识文档内容的文件。
signature:包含您获取的标识签名内容的文件。
说明如果您在实例标识签名时传入了audience参数,则需要手动将该参数信息添加至实例标识文档的末尾,格式为"audience":"audience参数取值",各参数之间使用半角逗号(,)进行连接。
cert.cer:包含阿里云公有证书的文件。
相关文档
如果您需要通过实例元数据,在实例内部获取其他实例信息,请参见实例元数据。
如果您需要使用实例自定义数据在实例启动时自动执行命令或脚本,请参见自定义实例初始化配置。