This topic describes how to connect to an ApsaraDB for MongoDB instance in a virtual private cloud (VPC) by using an SSL-VPN tunnel. The SSL-VPN tunnel allows you to manage the instance from a local client with ease.
Scenarios
The public IP address of the local client dynamically changes. As a result, you must frequently update the IP address whitelist that contains the public IP address of the local client in the ApsaraDB for MongoDB console. If you do not delete expired IP addresses at your earliest opportunity, security risks may arise.
A high level of security is required when you connect to an ApsaraDB for MongoDB instance over the Internet.
You must log on to the ApsaraDB for MongoDB instance from an Elastic Compute Service (ECS) instance over the Internet. This may cause security risks. In this case, you must separate ECS management permissions from ApsaraDB for MongoDB database permissions.
Billing
You are charged fees when you create a VPN gateway. For more information, see Billing.
Prerequisites
The network type of the ApsaraDB for MongoDB instance is VPC. If the network type of the instance is classic network, switch the network type of the instance from classic network to VPC. For more information, see Switch the network type of an ApsaraDB for MongoDB instance from classic network to VPC.
The CIDR block of the local client is different from that of the ApsaraDB for MongoDB instance.
The local client can access the Internet.
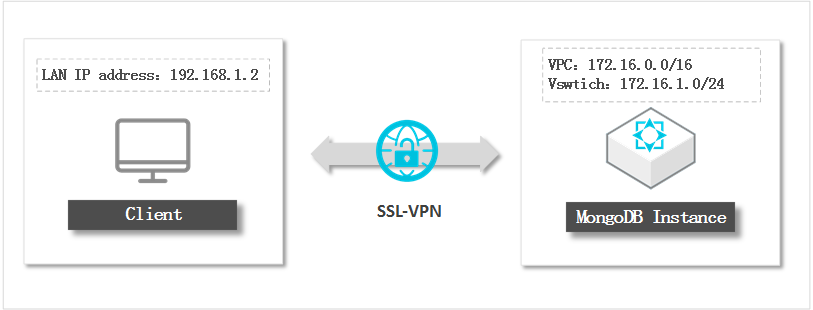
Networking
Step 1: Create a VPN gateway
For more information, see Create and manage a VPN gateway.
When you create a VPN gateway, take note of the parameters described in the following table.
Parameter | Description |
Region | The region where the VPN gateway resides. Select the same region as the ApsaraDB for MongoDB instance. |
VPC | The VPC to which the VPC gateway belongs. Select the same VPC as the ApsaraDB for MongoDB instance. |
IPsec-VPN | Specifies whether to enable the IPsec-VPN feature. In this example, the local client is used to access the VPC. In this case, set the IPsec-VPN parameter to Disable. The IPsec-VPN feature provides site-to-site connections. You can create an IPsec tunnel to establish a connection between a data center and a VPC or between two VPCs. |
SSL-VPN | Specifies whether to enable the SSL-VPN feature. In this example, the local client is used to access the VPC. In this case, set the SSL-VPN parameter to Enable. The SSL-VPN feature provides site-to-site VPN connections. You can use an SSL-VPN tunnel to establish a connection between the local client and the VPN, You do not need to configure a gateway for the local client. |
Step 2: Create an SSL server
For more information, see Create and manage an SSL server.
When you create an SSL server, take note of the parameters described in the following table.
Parameter | Description |
VPN Gateway | The VPN gateway associated with the ApsaraDB for MongoDB instance. Select the VPC gateway created in Step 1. |
Local Network | The local CIDR block that the local client needs to access by using the SSL-VPN connection. The CIDR block can be the CIDR block of a VPC, a vSwitch, a data center that is connected to a VPC by using a leased line, or an Alibaba Cloud service such as ApsaraDB RDS or Object Storage Service (OSS). In this example, enter the CIDR block of the vSwitch in the VPC to which the ApsaraDB for MongoDB instance belongs: 172.16.1.0/24. Note The subnet mask of the CIDR block must be 16 to 29 bits in length. |
Client CIDR Block | The CIDR block that you want to allocate to the virtual network interface of the local client. Do not enter the CIDR block where the local client resides. When the local client is connected to the ApsaraDB for MongoDB instance by using an SSL-VPN tunnel, the VPN gateway selects an IP address from the specified CIDR block and assigns the IP address to the local client. In this example, enter 192.168.100.0/24. Note Make sure that the value of the Client CIDR Block parameter does not overlap that of the Local Network parameter. |
Step 3: Create an SSL client
For more information about how to create an SSL client, see Create and manage an SSL client certificate.
After the SSL client certificate is created, you must download the certificate and install the certificate on the client. For more information, refer to the following section and topic:
The Connect a client to a VPC by using SSL-VPN section of the "Connect a client to a VPC" topic
Step 4: Establish an SSL-VPN connection
Linux client
Run the following command to install OpenVPN and create the
confdirectory.CentOS
yum install -y openvpn mkdir -p /etc/openvpn/confUbuntu
apt-get update apt-get install -y openvpn mkdir -p /etc/openvpn/confDecompress the SSL client certificate package that you downloaded and copy the SSL client certificate to the /etc/openvpn/conf/ directory.
Go to the /etc/openvpn/conf/ directory and run the following command to establish an SSL-VPN connection:
openvpn --config /etc/openvpn/conf/config.ovpn --daemon
Windows client
Download and install the OpenVPN client for Windows. If you fail to access the page, contact your account manager or Alibaba Cloud engineer.
Decompress the SSL client certificate package that you downloaded and copy the SSL client certificate to the
OpenVPN\configdirectory.In this example, the certificate is copied to
C:\Program Files\OpenVPN\config. You must copy the certificate to the directory where the client is installed.Double-click the OpenVPN GUI icon on your desktop to launch the client. The VPN icon is displayed in the lower-right system tray. Right-click the VPN icon in the system tray and click Connect to create an SSL-VPN connection.
If State displays Connected and IP address is allocated, the connection is created.
Step 5: Log on to the ApsaraDB for MongoDB instance
Add the local client CIDR block specified in Step 2 to all IP address whitelists of the ApsaraDB for MongoDB instance. In this example, add 172.16.1.0/24 to all IP address whitelists of the ApsaraDB for MongoDB instance.
Log on to the ApsaraDB for MongoDB console.
Obtain the internal endpoints of the ApsaraDB for MongoDB instance. For more information, see Connect to a replica set instance.
Use the mongo shell or other management tools to log on to the ApsaraDB for MongoDB instance. For more information about the mongo shell, see Connect to an ApsaraDB for MongoDB replica set instance by using the mongo shell.
NoteLog on to the ApsaraDB for MongoDB instance by using the internal endpoint of the instance.