Once you follow the Security-as-Code concept, you can also apply the Test Pyramid (Mike Cohn, 2005) to security testing. In this document, you will have a quick introduction to a security tool of each level of the pyramid:
The Test Pyramid (Mike Cohn, 2005) can help to organize and structure security testing.
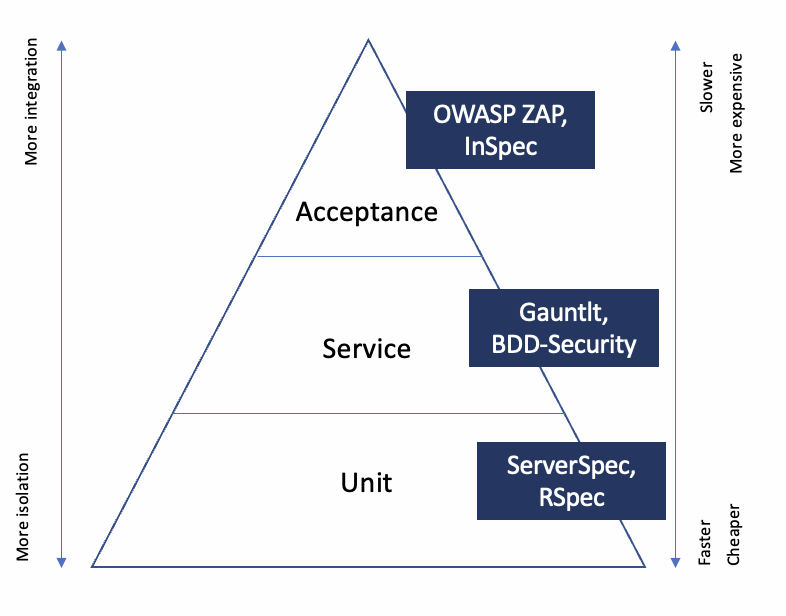
It has 3 levels of tests. The main principle is to prefer the layer layers, faster and cheaper.
So when a Service or an Acceptance Test fails, create an Unit Test and so on.
The correction of defects will be earlier and less costly.
In this presentation, focus on:
OWASP ZAP (Open Web Application Security Project ZAP) is an open source tool provided by OWASP for penetration tests of a web application in order to find vulnerabilities. It does a passive scan.
It can:
zap-baseline.py,zap-full-scan.py,zap-api-scan.py.The ZAP Baseline is ideal for CI/CD pipelines. With Docker, it's very easy to integrate it in a pipeline:
docker run --rm \
--it \
--name owasp-zap-scan-dvws \
--network host \
-v $PWD/data:/zap/wrk:rw \
owasp/zap2docker-weekly \
sh -c "zap-baseline.py -t http://0.0.0.0:80 -r zap-baseline-scan-report.html"For more information: https://github.com/zaproxy/zaproxy/wiki/ZAP-Baseline-Scan
Gauntlt ("Be Mean to Your Code") is based on the Cucumber BDD (Behavior-Driven Development) testing framework. It includes several attack tools:
sslyze: verifies the SSL configuration,nmap: verifies the network configuration,sqlmap: tests SQL injection vulnerabilities,curl: performs simple web application attacks,arachni, dirb, and garmr: searches common vulnerabilities,hartbleed: checks specific vulnerabilities.Source: http://gauntlt.org
Example (nmap.attack file):
Feature: nmap attacks for scanme.nmap.org and to use this for your tests, change the value in the profile
Background:
Given "nmap" is installed
And the following profile:
| name | value |
| hostname | scanme.nmap.org |
| host | scanme.nmap.org |
| tcp_ping_ports | 22,25,80,443 |
Scenario: Verify server is open on expected set of ports using the nmap-fast attack step
When I launch a "nmap-fast" attack
Then the output should match /80.tcp\s+open/Run (via a Docker image):
docker run -t - rm=true -v $PWD:/working -w /working gauntlt nmap.attackGauntlt can be integrated in CI/CD pipelines:
@slow are executed in the CD pipeline,For more information: http://gauntlt.org/
ServerSpec allows you to check that the servers are correctly configured using an SSH connection (resources, port, packages, HTTP status code, ...) or locally.
ServerSpec run tests on specifications you create. For example, to verify that a Docker image is present and that the port 80 is listening:
docker run -d \
- name nginx \
-p 80:80 \
devopstestlab/nginx-helloworldserver1_spec.rb specifications,require 'spec_helper'
describe docker_image('devopstestlab/nginx-helloworld') do
it { should exist }
end
describe port(80) do
it { should be_listening }
enddocker run --rm \
--network host \
-v $PWD:/serverspec \
devopstestlab/serverspec \
rake specBy Bruno Delb

8 posts | 1 followers
FollowCherish Wang - September 16, 2019
Alibaba Cloud Native - July 22, 2022
Alibaba Cloud Community - February 15, 2022
Alibaba Cloud Indonesia - September 13, 2023
Alibaba Container Service - July 29, 2019
Alibaba Clouder - February 21, 2019

8 posts | 1 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Database Security Solutions
Database Security Solutions
Protect, backup, and restore your data assets on the cloud with Alibaba Cloud database services.
Learn MoreMore Posts by Bruno Delb