By: Jeremy Pedersen
Securing servers is tough. Anyone who has tried it has run up against the following questions:
...and lots more.
One of the more common approaches to this problem is to set up a Bastion Host.
This usually involves setting up and configuring yet another server, and that server itself inevitably becomes its own security headache.
But there's a better way.
Alibaba Cloud has a built-in Bastionhost Service which saves you the trouble of setting up your own server to do the job.
Better, Bastionhost provides:
I'll be using the paid version for today's test because I have an Alibaba Cloud test account. However, there is a free trial you can apply for if you'd like to try it out yourself.
Since I want to test Bastionhost's SSH and RDS functionality, my minimum test environment consists of:
Setting up VPC network groups and ECS instances is straightforward, so I'll skip over those details and show the final setup.
I have created a new VPC group in Singapore:
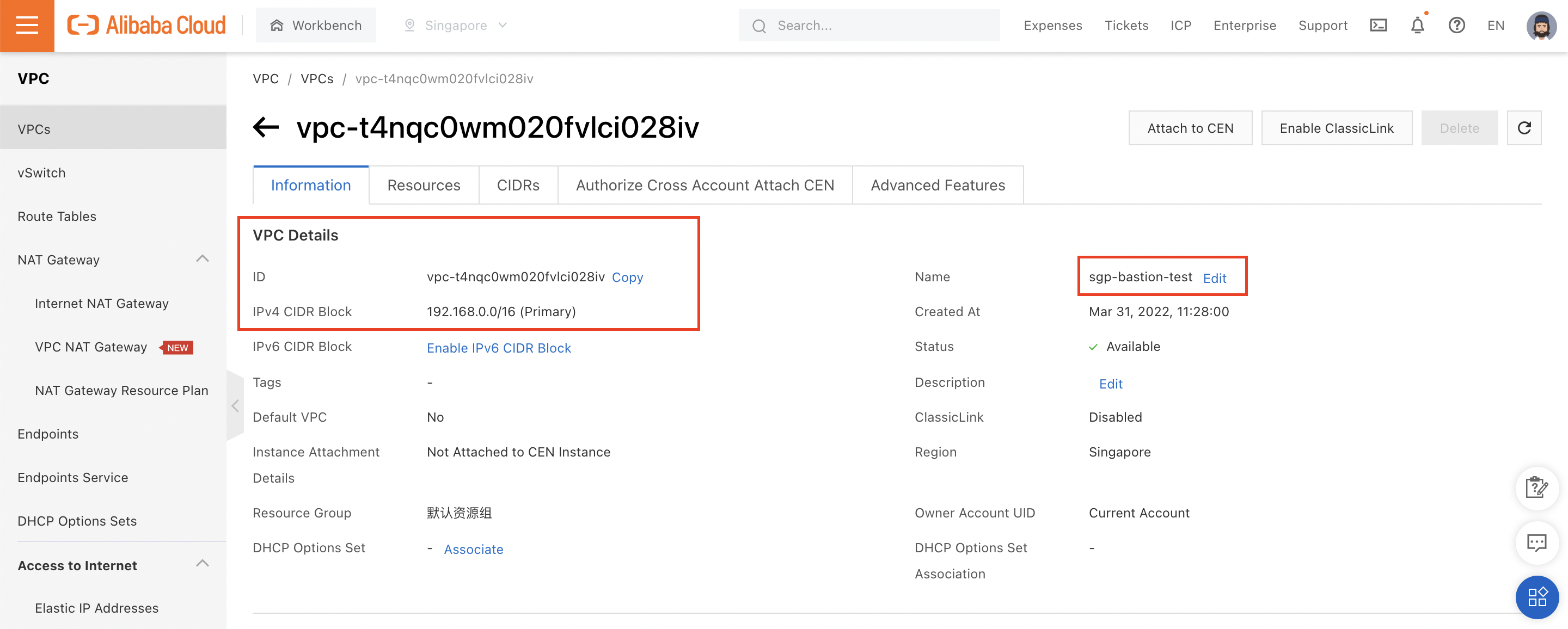
And created two ECS instances (one running Windows, one running Linux) inside that VPC:
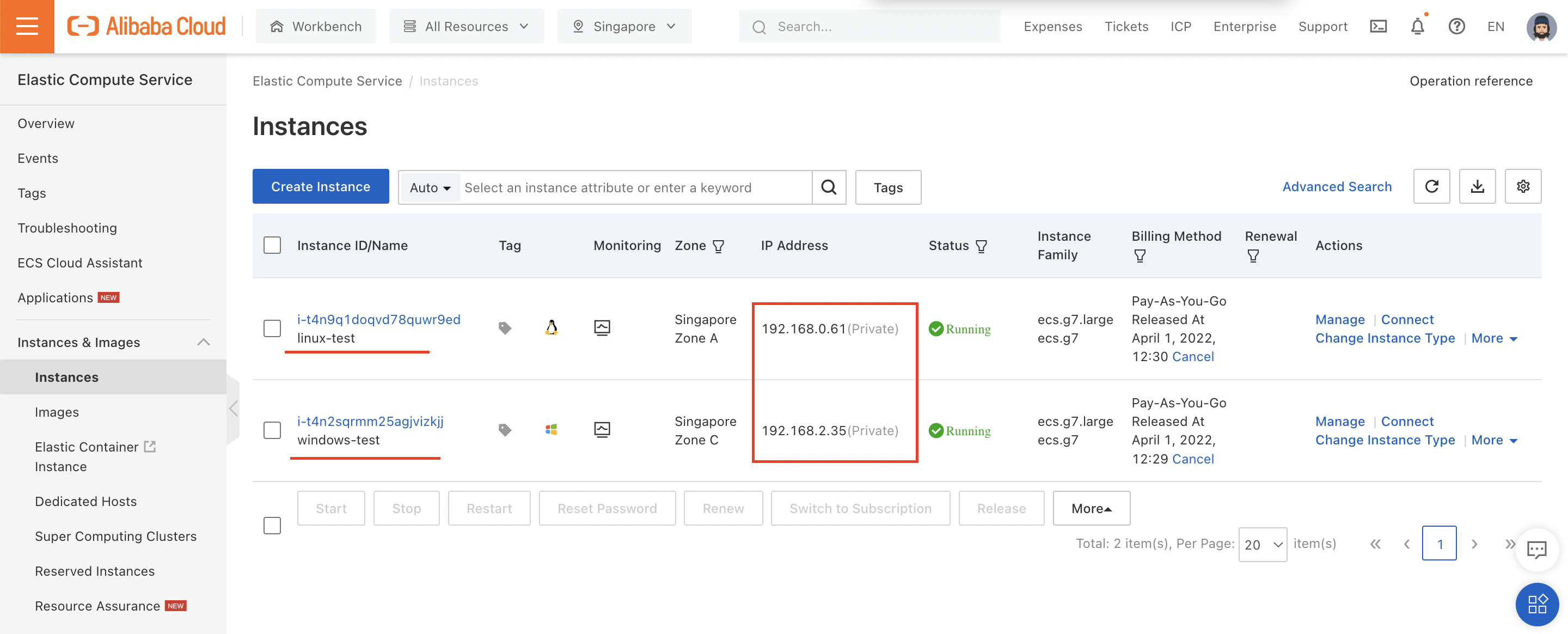
Note that neither ECS instance has a public IP, meaning these instances won't be reachable from the Internet (except indirectly through Bastionhost).
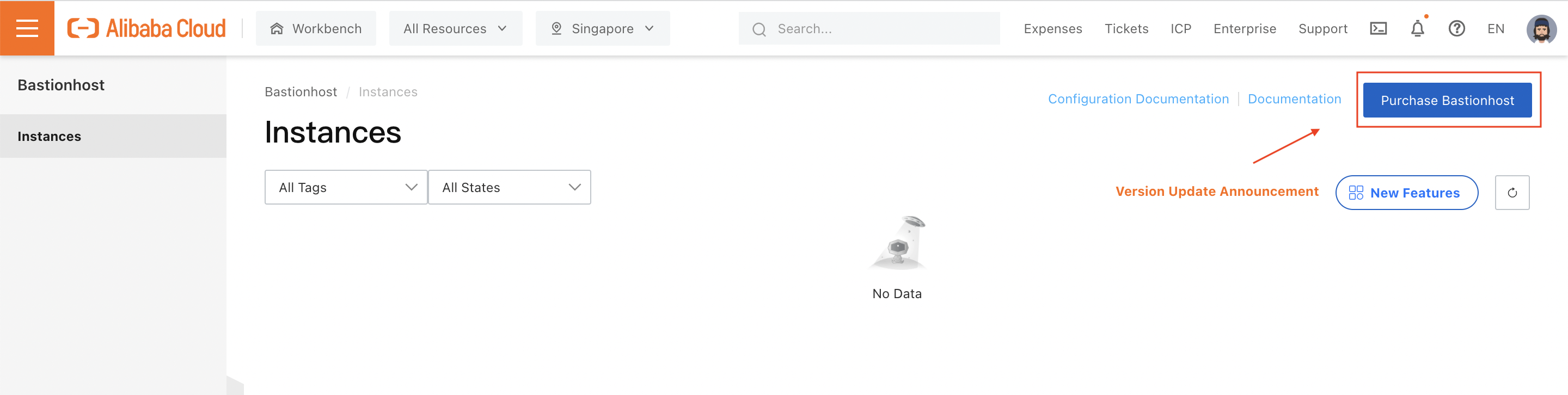
Next, we need to enable Bastionhost. I'll run my tests in Singapore, so I need to purchase a Bastionhost instance in the Singapore region:
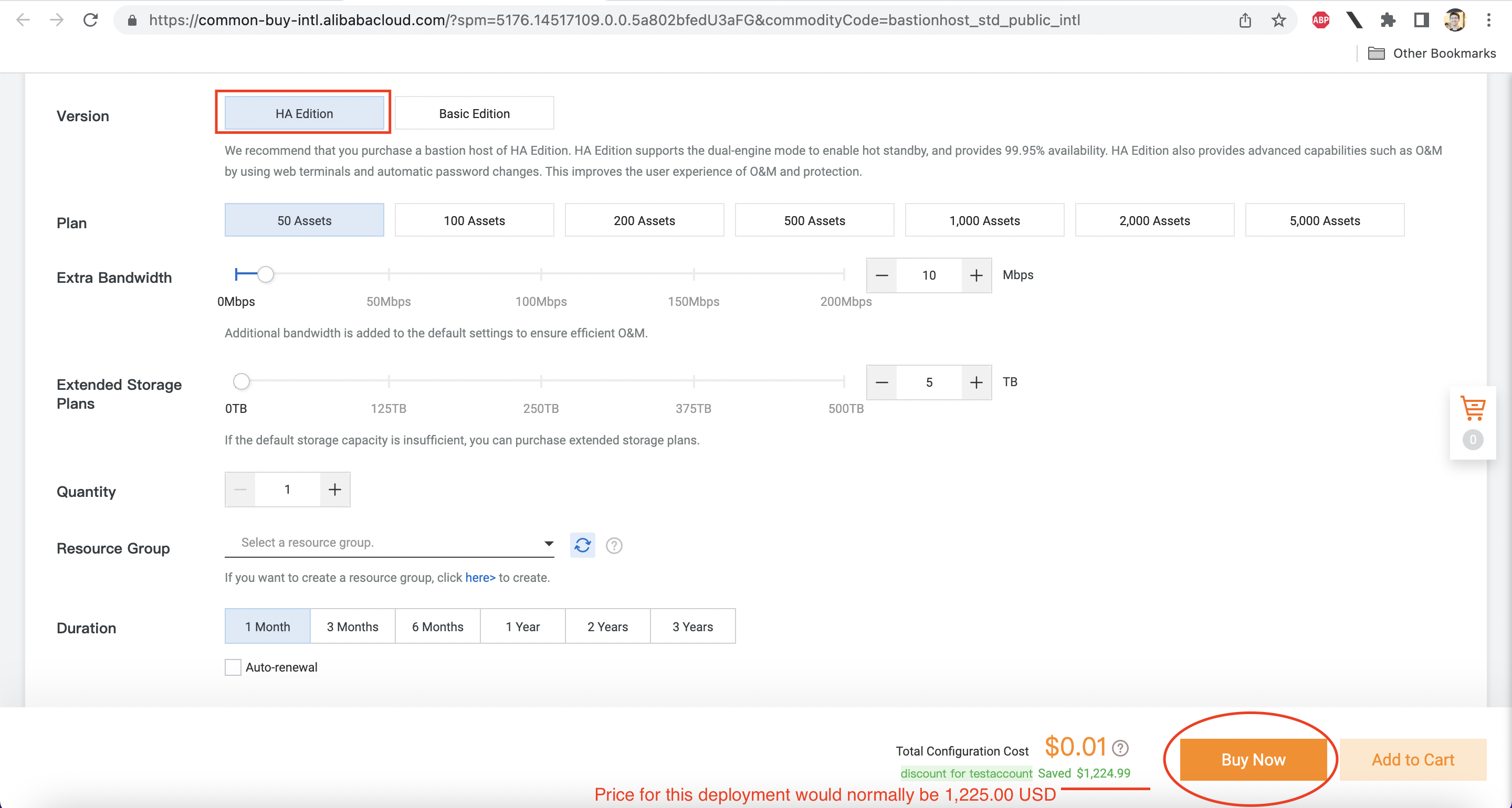
I'm using a test account, so I'll choose the more expensive HA edition, which has built-in redundancy. As configured here, I can use my Bastionhost instance with up to 50 ECS instances, and can store 5 TB of log data:
Before I can start using Bastionhost, I have to start the instance by clicking "Run" from the console:
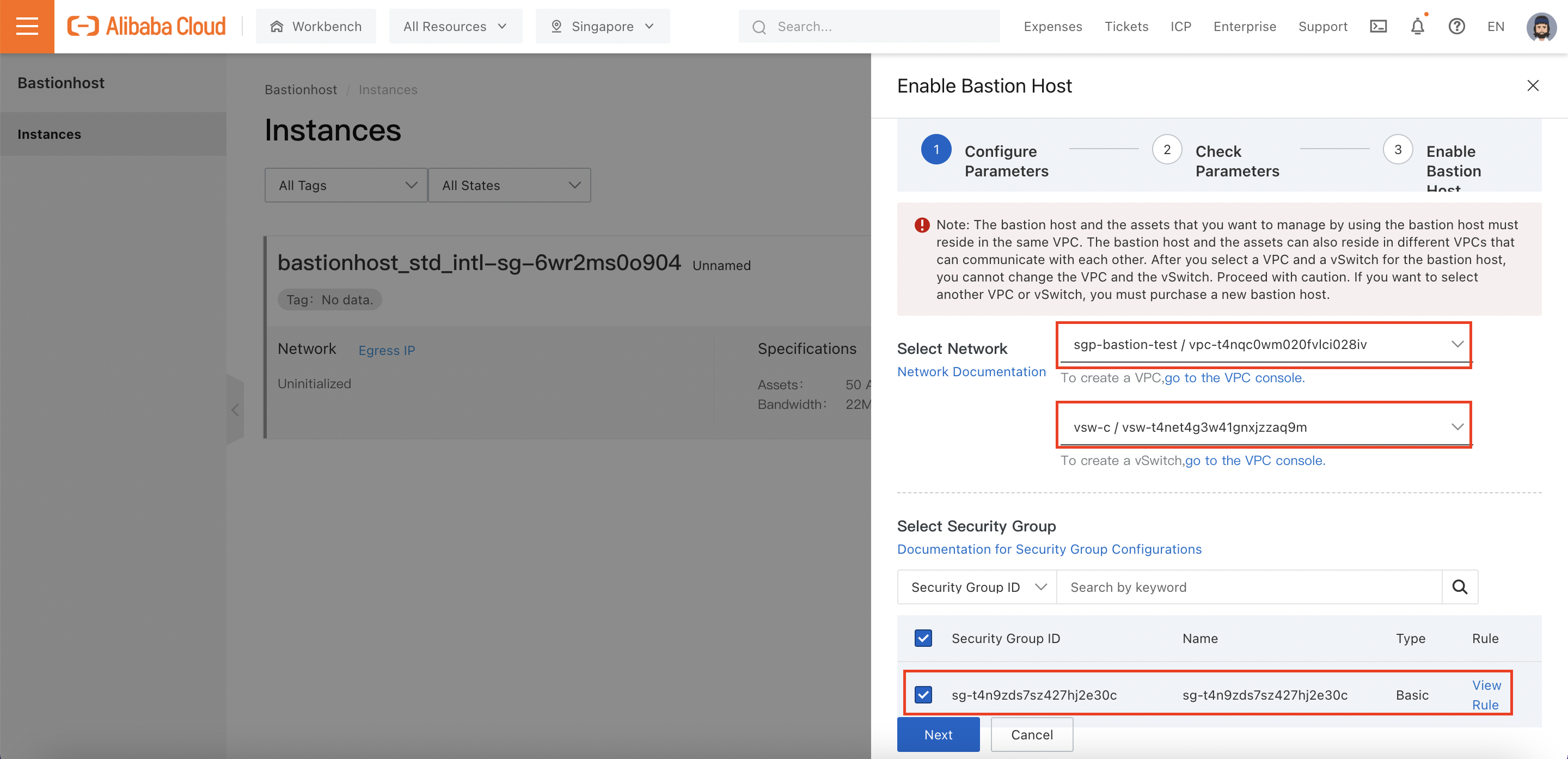
This will open a setup pane, which prompts me to choose the VPC group and VSwitch the Bastionhost instance should attach to, as well as any Security Groups it should have access to:
It may take a few minutes for the Bastionhost instance to boot up:
We can now click on "Manage" to open up the Bastionhost instance's management pane:
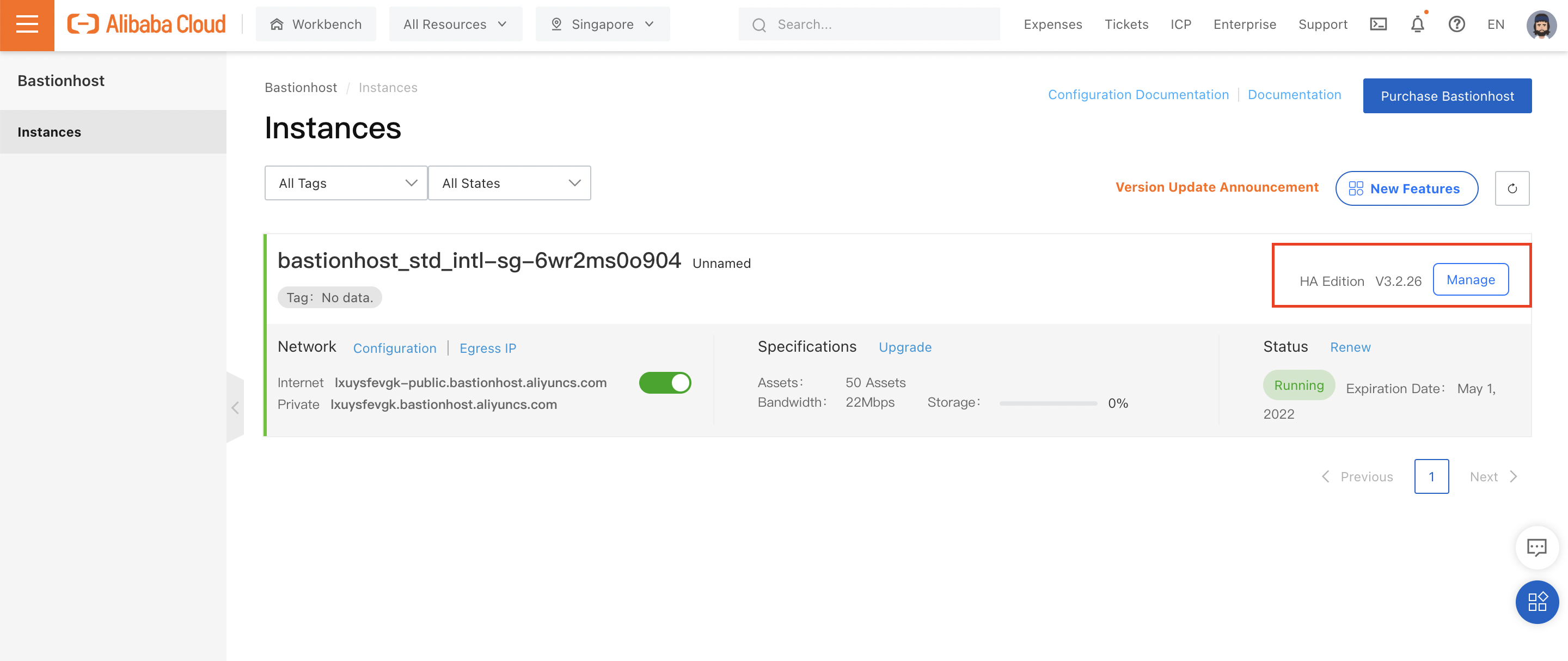
Let's start playing around!
We can start by attaching our ECS instances to Bastionhost. To do this, navigate to "Assets -> Hosts":
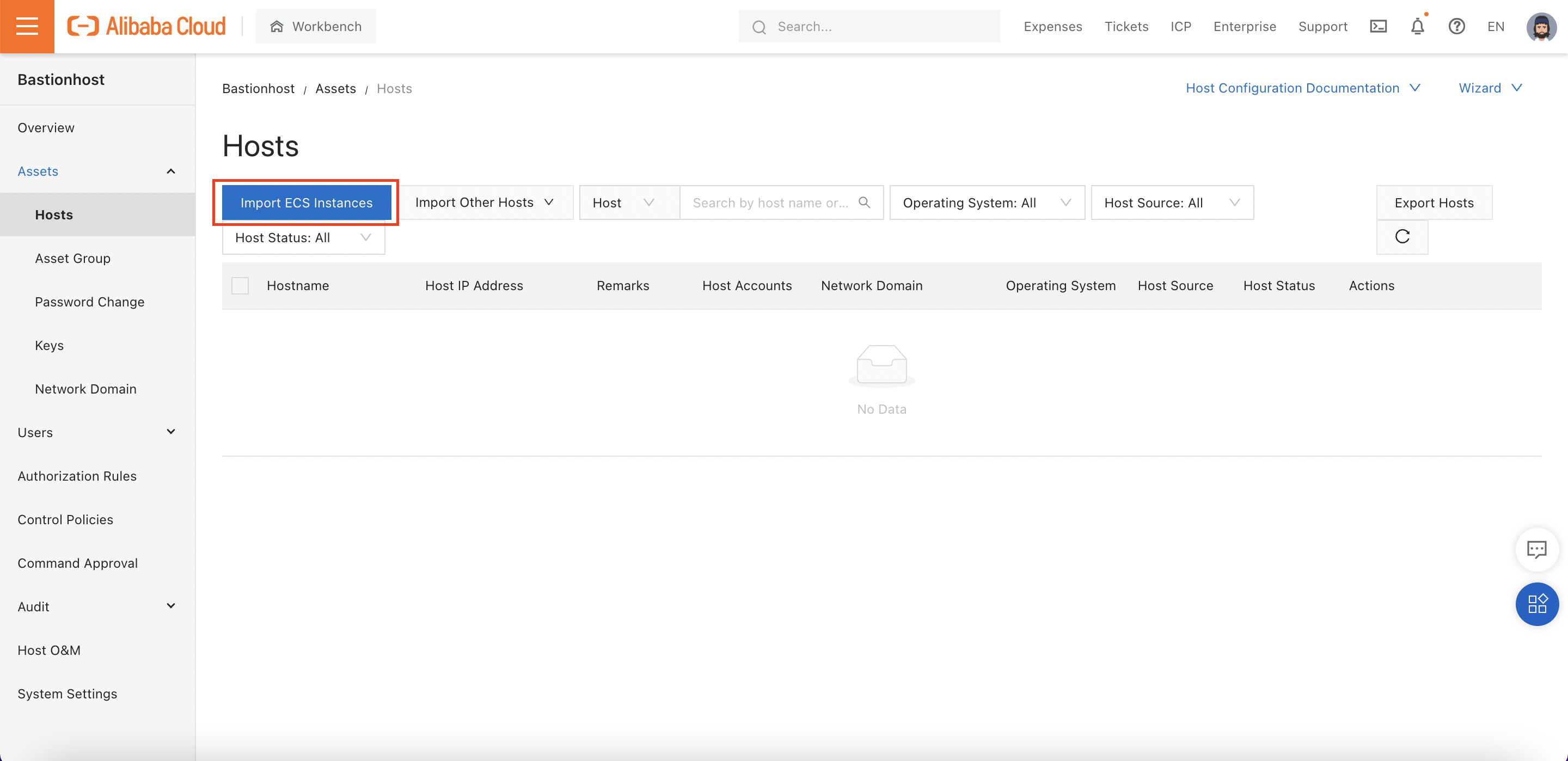
Choose the Singapore region:
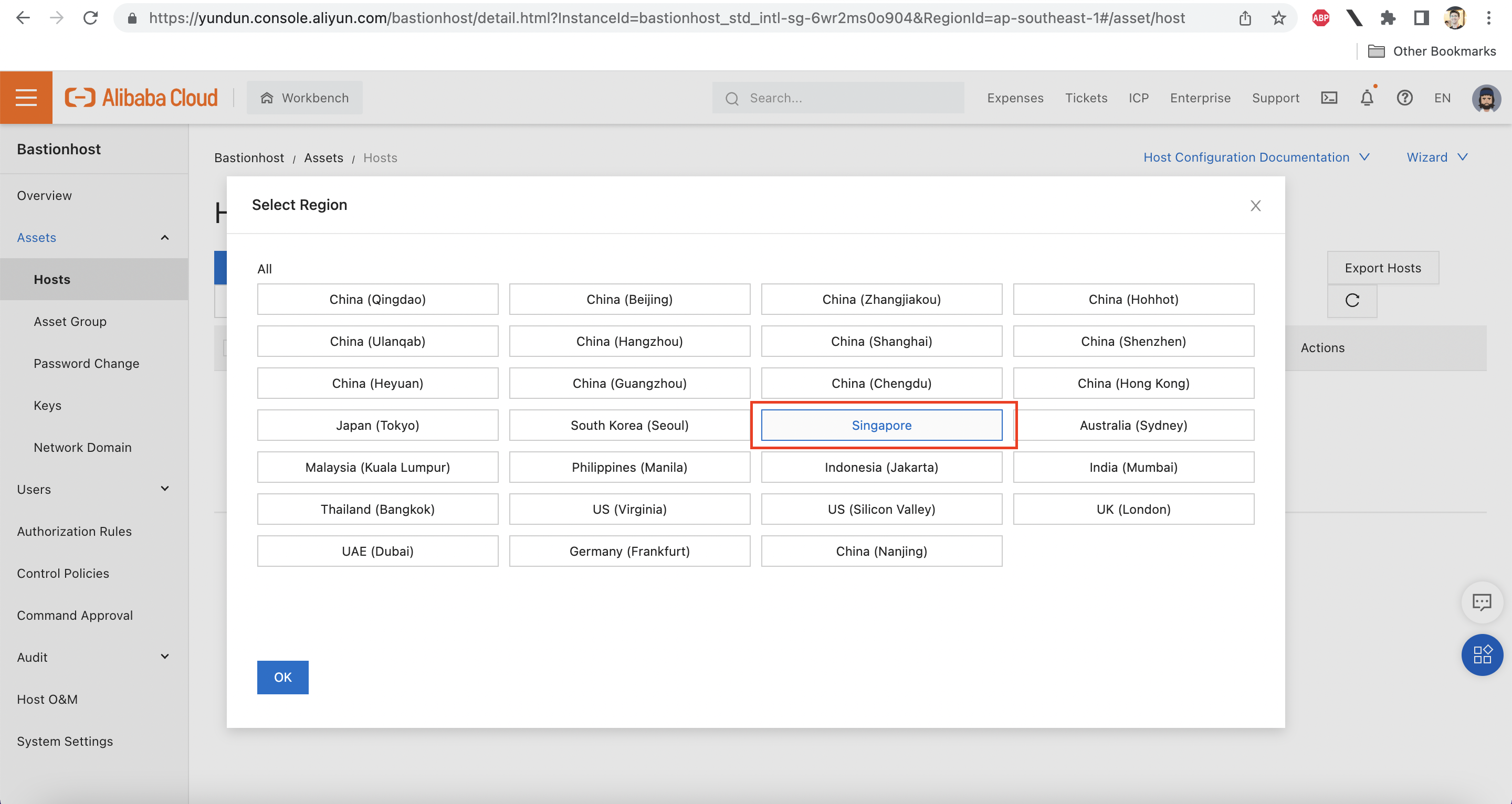
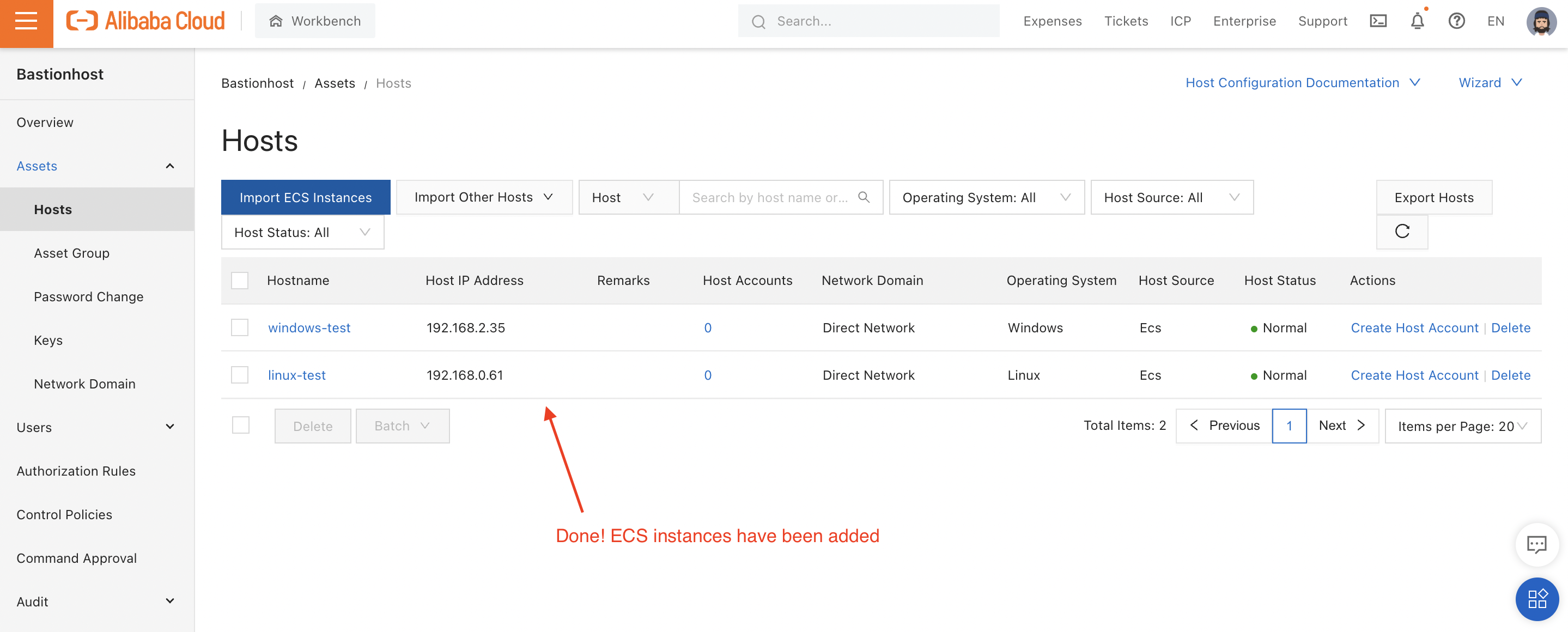
Add both ECS instances:
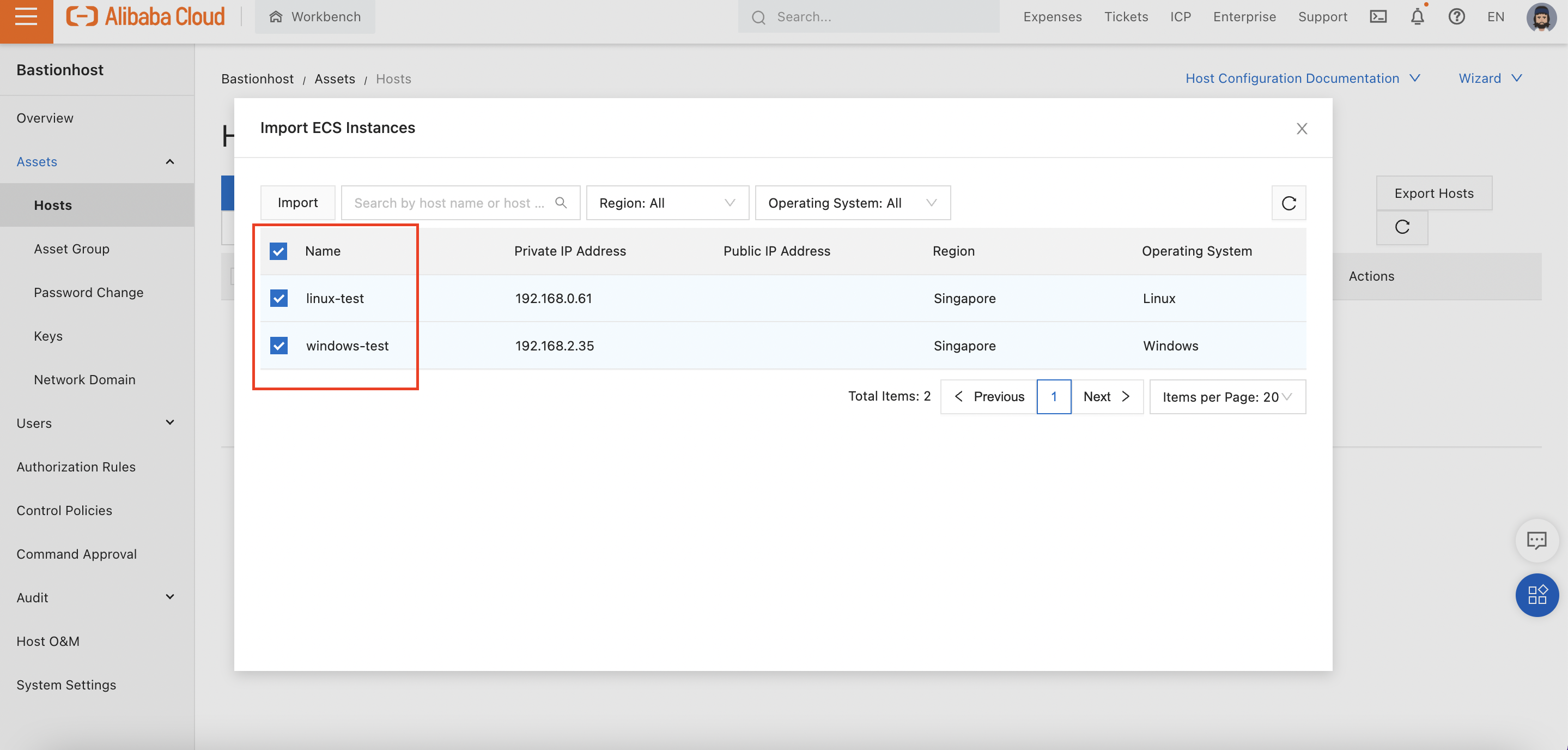
Clicking "Import" at the top of that dialog will attach both ECS instances to Bastionhost and take us back to the Instance list:
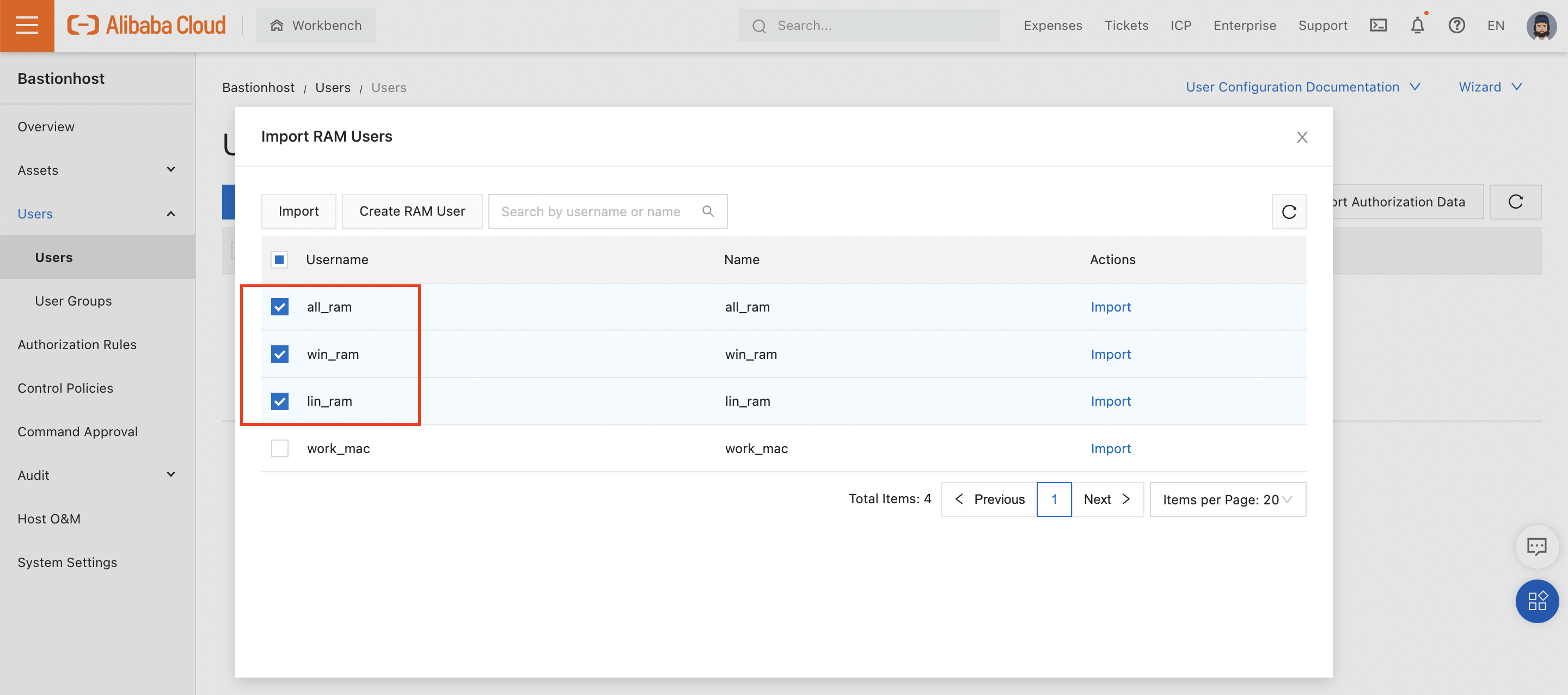
Prerequisite: We need to set up some RAM users via the Alibaba Cloud RAM console. Instructions on creating RAM users can be found here. I have created three:
Note that these three users have not been given any permissions, and have not been given Access Keys.
Why? Because they don't need any. Permissions to access the ECS instances will be granted through Bastionhost itself.
We can add our users from "Identities -> Users":
After clicking "Import", all 3 users now show up in the Bastionhost console:
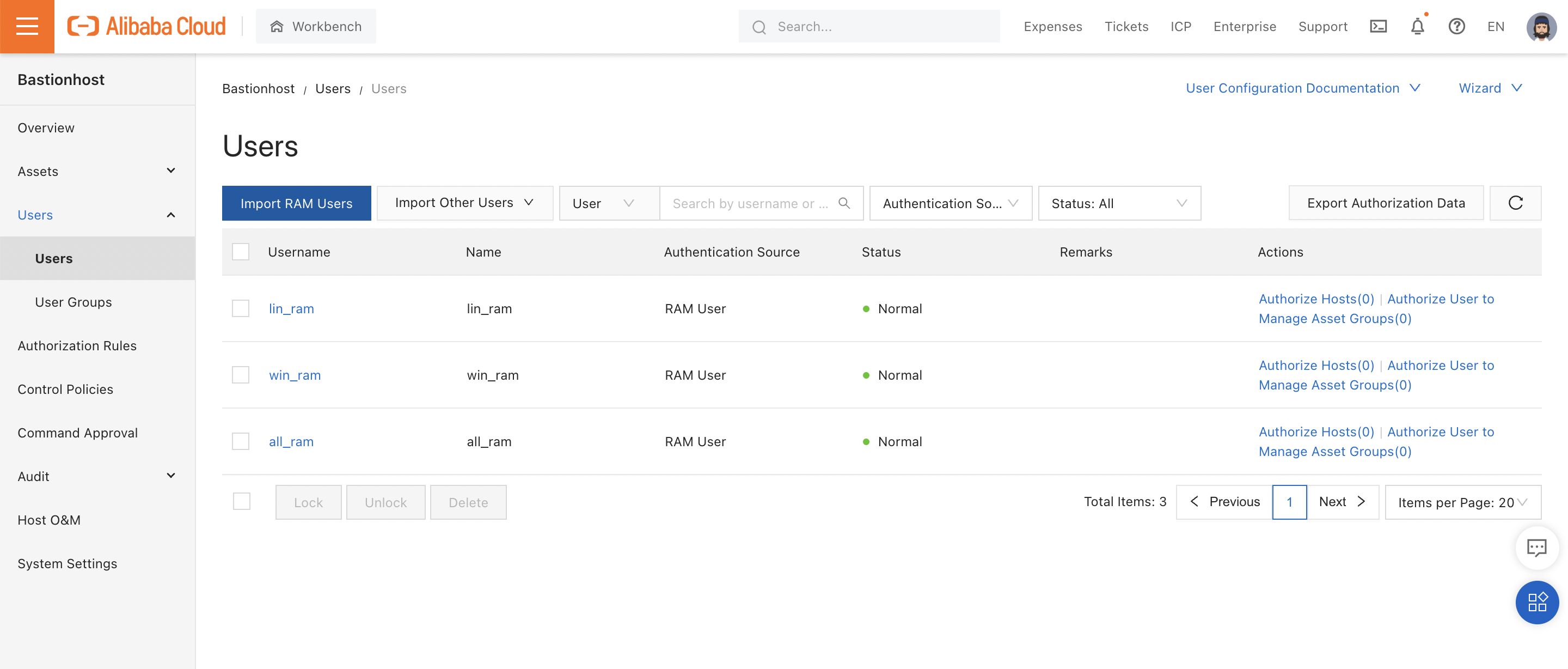
Looking closely at the above screenshot, you'll notice there's a little (0) next to "Authorize Hosts" in the "Actions" column.
This is because none of our RAM users have permission to access any of our ECS instances. Let's fix that.
First, I'll click on "Authorize Hosts" in the first row, for the "lin_ram" user. I'll authorize this user to access the Linux ECS instance I created earlier:
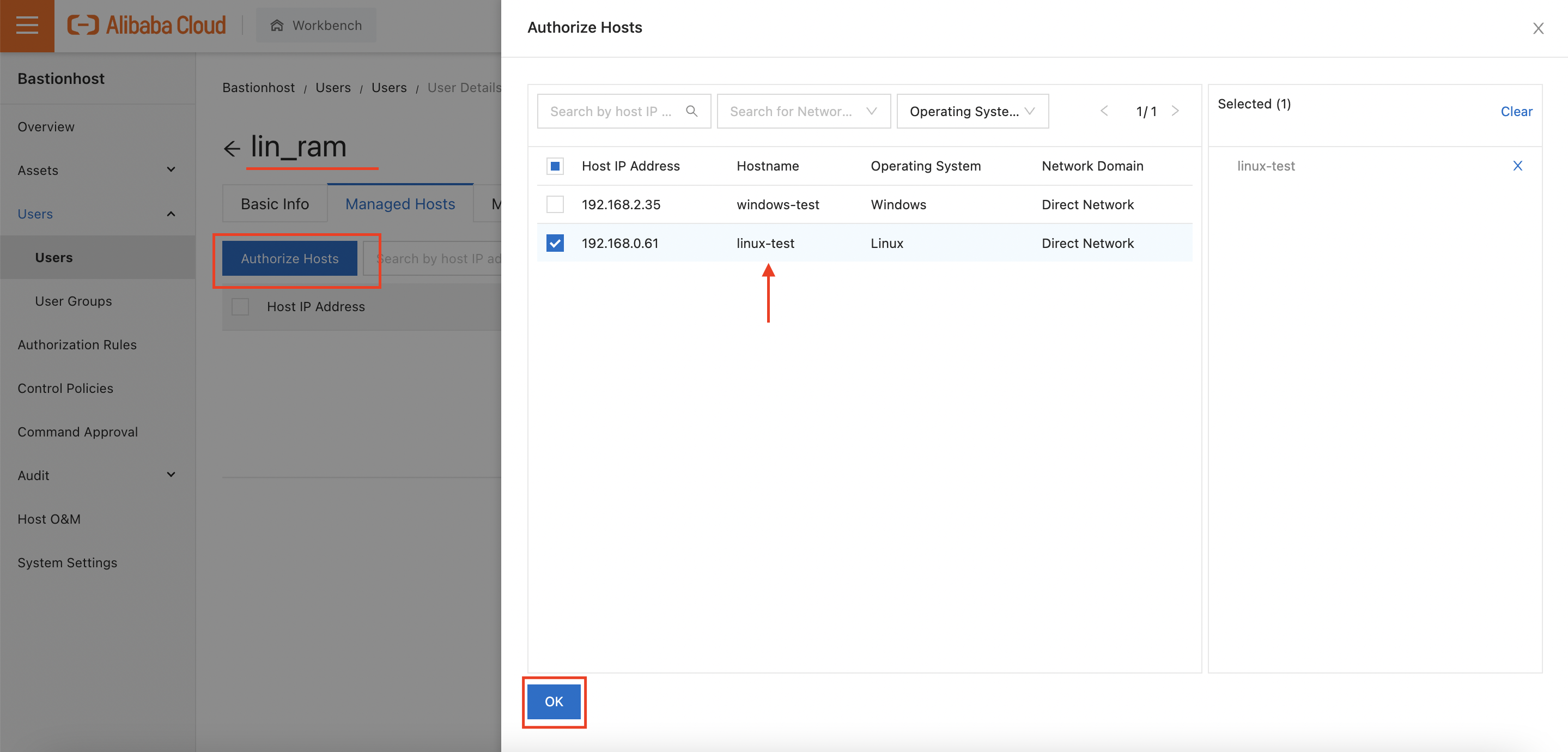
I'll repeat this process for "win_ram" and "all_ram", giving "win_ram" access to the Windows instance only, and "all_ram" access to both instances.
Returning to the user list, I can now see that each RAM user is authorized to access one or more ECS instances:
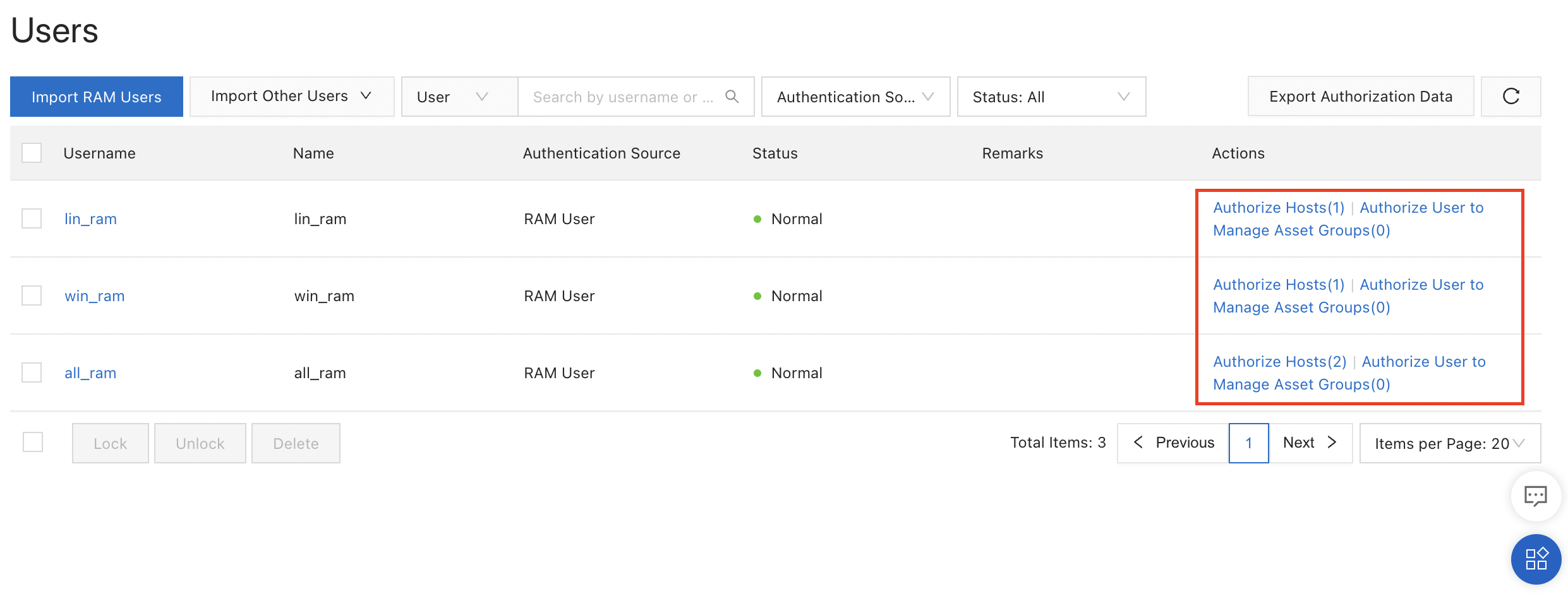
Tip: For working with larger sets of users, I can also create user groups. Users added to a user group will automatically gain access to any ECS instances associated with the group.
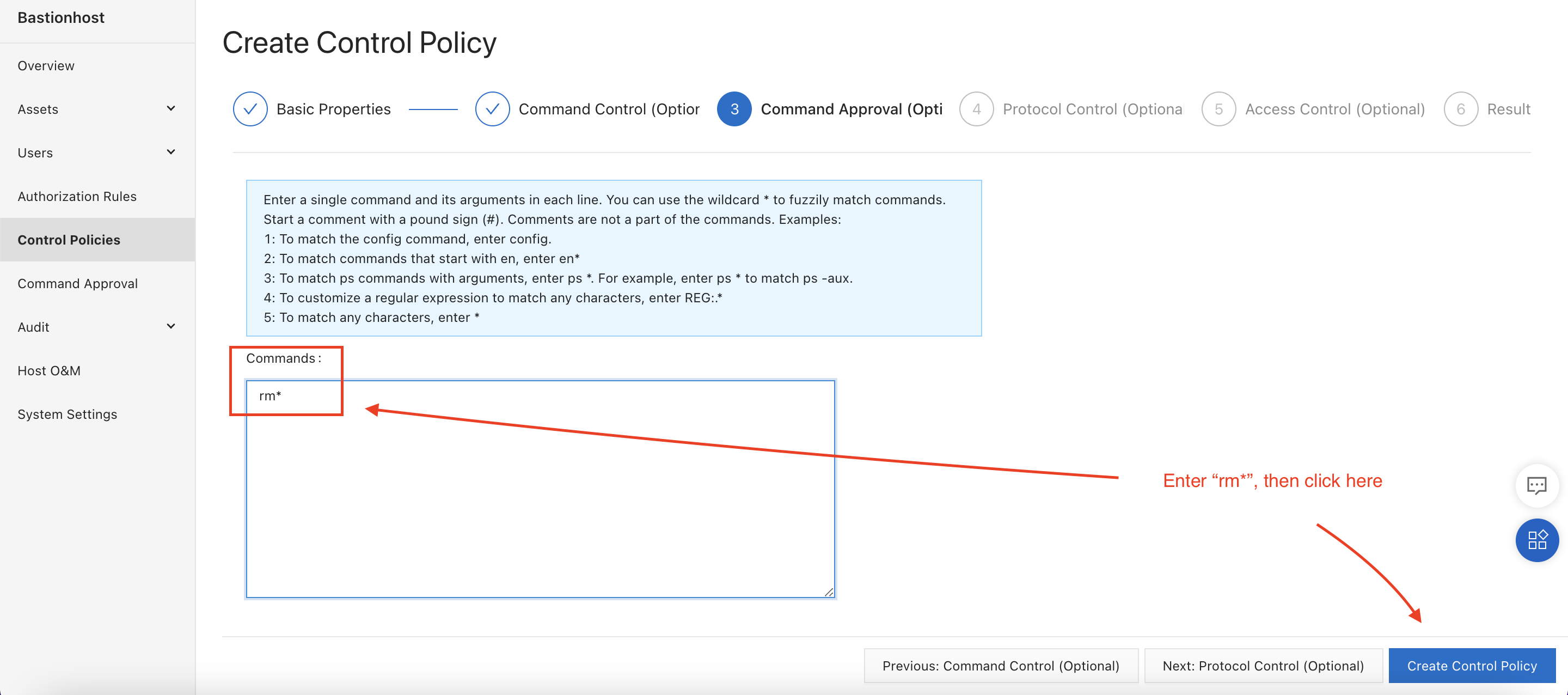
We can also write control policies limiting what actions a user can perform. As an example, let's create a control policy that prevents the "lin_ram" user from executing the rm command. Any time the user enters a command starting with rm, a Bastionhost administrator will be required to approve the command from the Bastionhost console.
First, click "Create Control Policy":
Creating the control policy is a 6-step process:
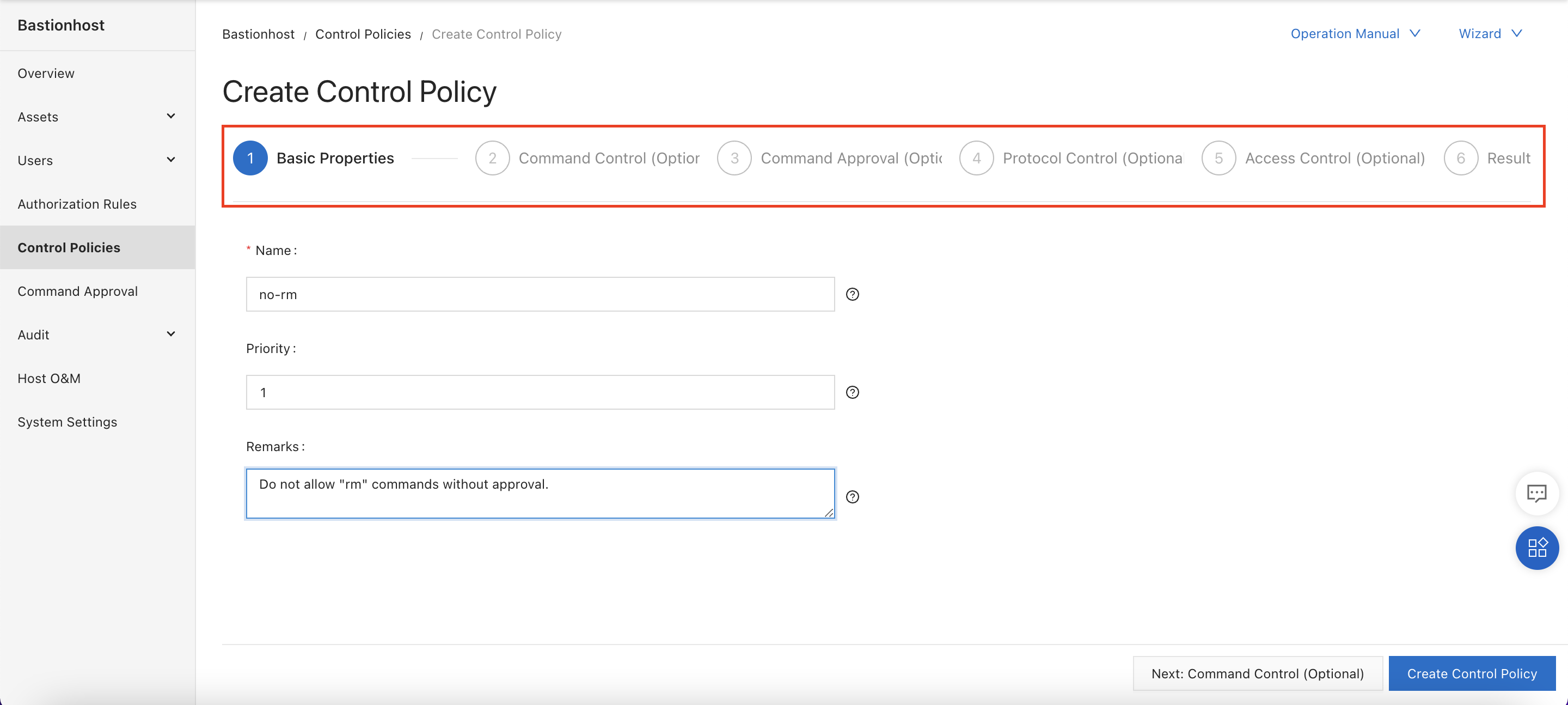
We will skip the "Command Control" step. We want to force approval for rm commands, not disable them entirely:
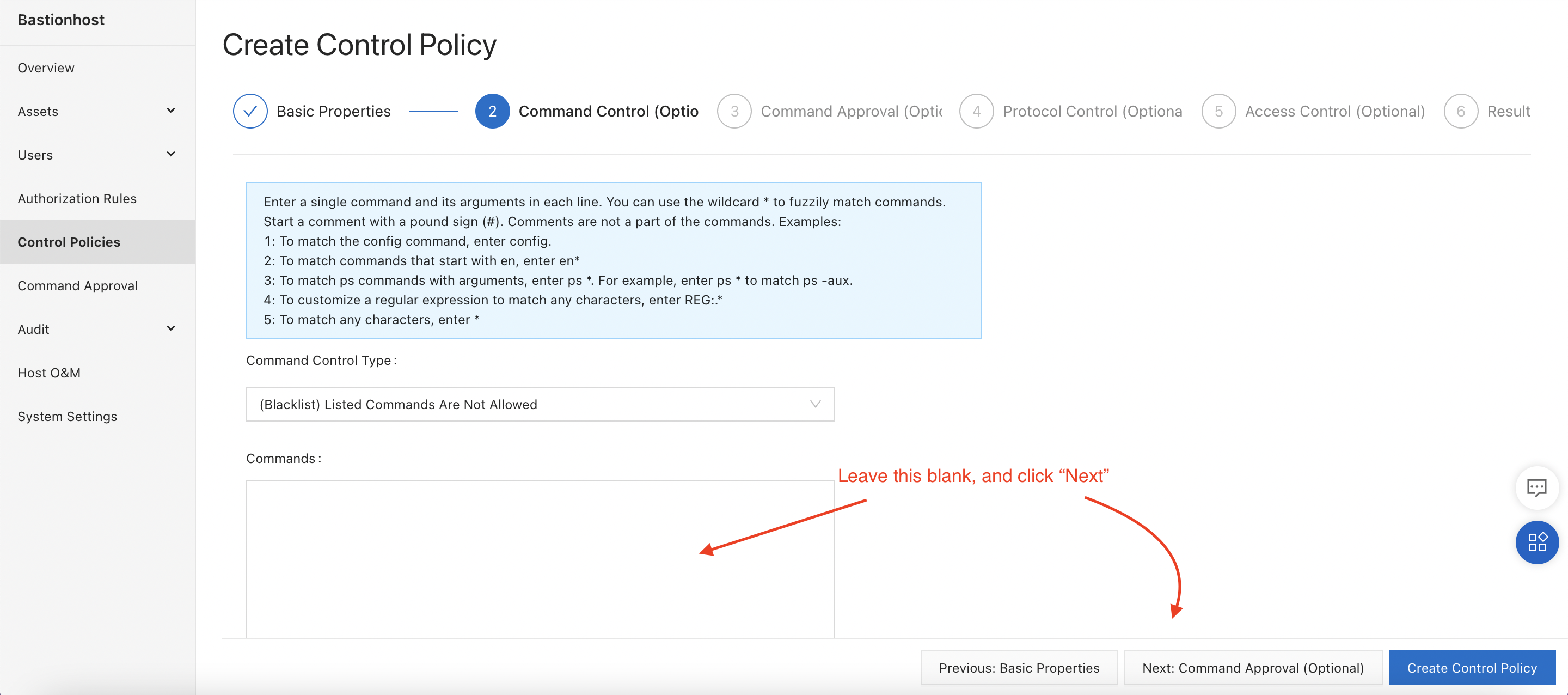
On the next screen, enter rm* to block the execution of any command starting with the prefix "rm":
We don't need to limit the rule to particular protocols or hosts, so we can just click "Create Control Policy", skipping steps 4 and 5. This takes us straight to step 6, where we can associate the policy with one or more users or hosts:
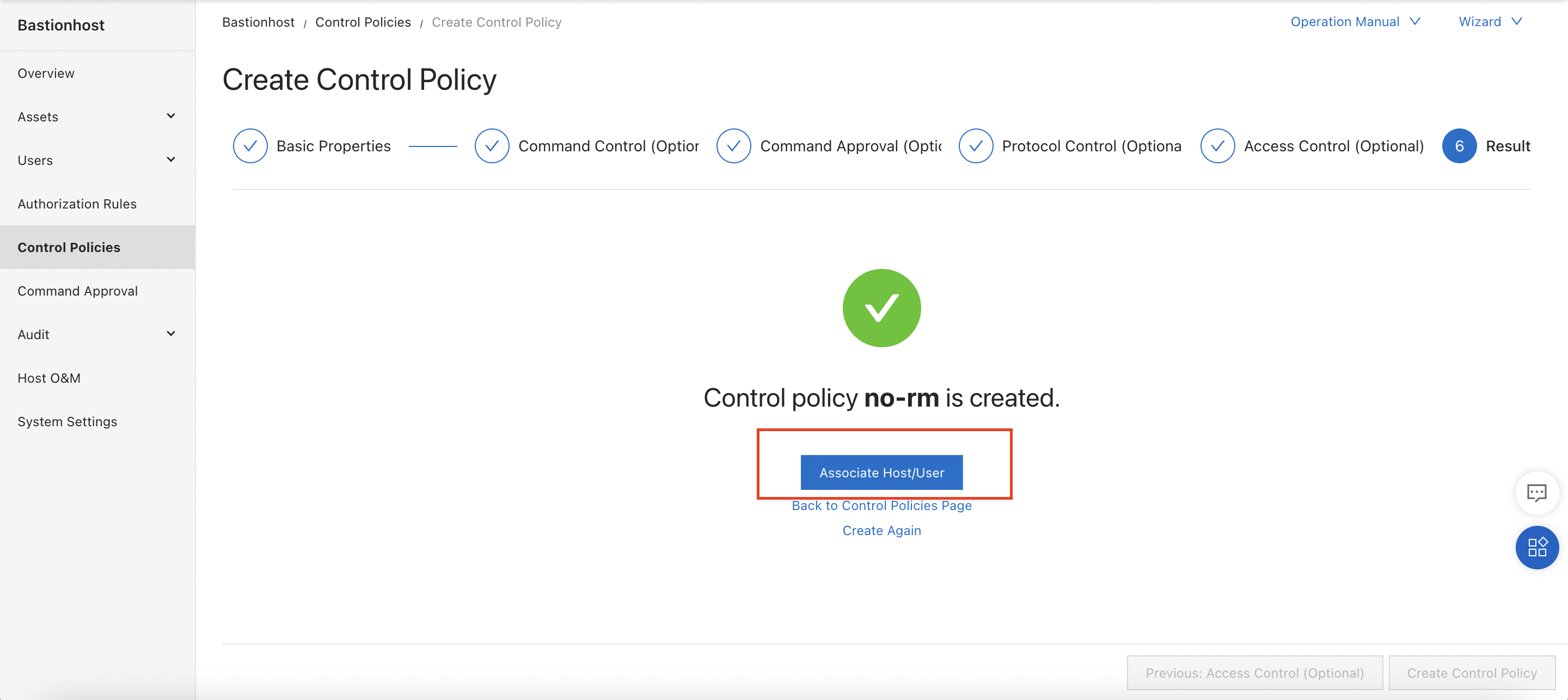
Clicking on "Associate Host/User" gives us the option to apply the police to one or more hosts and/or one or more users.
We'll associate the policy with the "lin_ram" user:
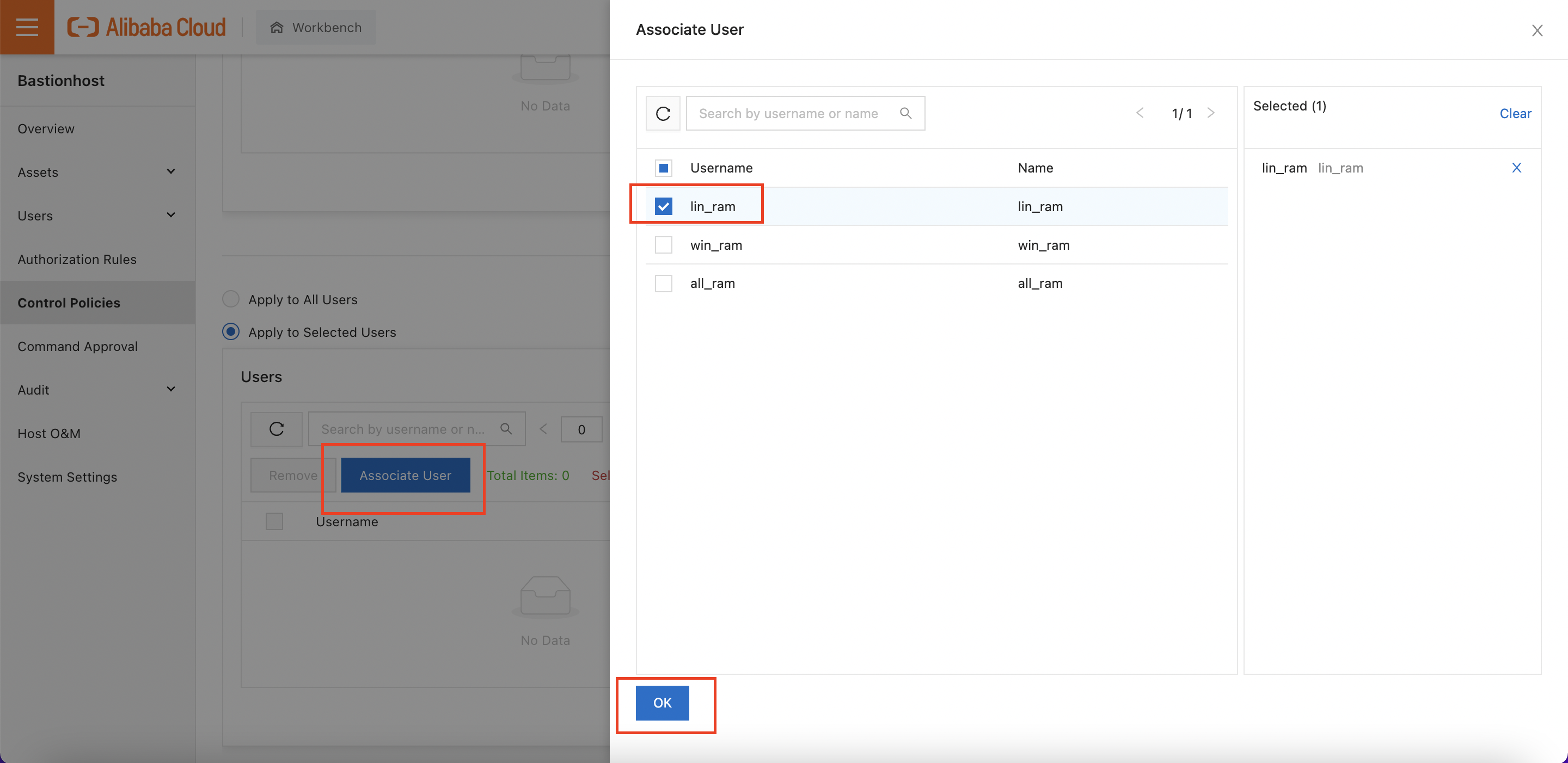
I also scroll up and make sure the policy is attached to the "linux-test" host, as well.
We've configured our hosts and users. Now let's try logging in, and seeing what happens!
Returning to the "overview" page, we see the login information for the Bastionhost instance:
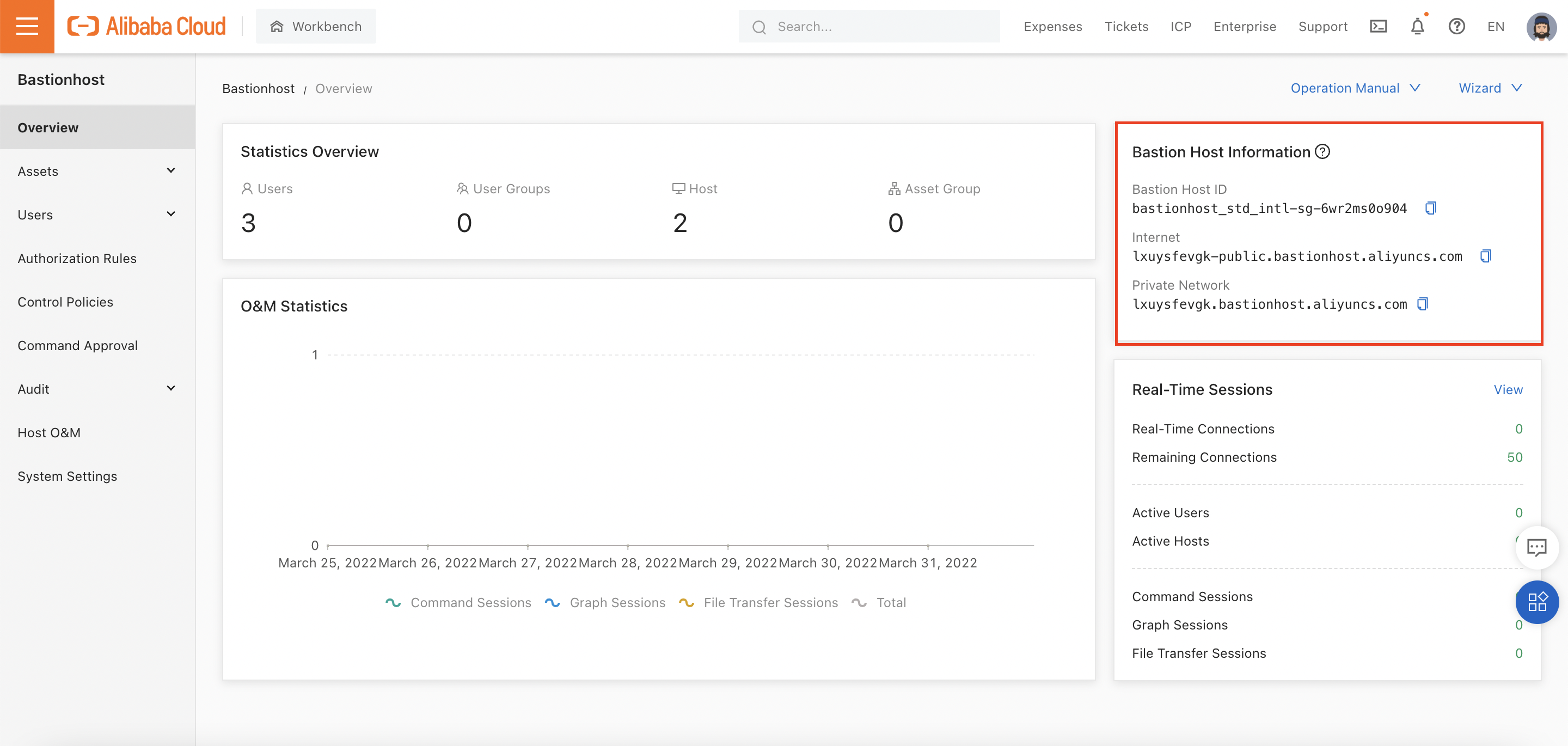
Important Note*: First-time users of Bastionhost are often surprised that access via the default SSH and RDP ports (22 and 3389) doesn't work. This is because Bastionhost uses non-standard port numbers. Specifically:
When logging on, you need to make sure you are using these port numbers, rather than the default ones! This is documented here.
Let's test SSH login for the user "lin_ram", first. I'll use the Internet endpoint for my Bastionhost, which is lxuysfevgk-public.bastionhost.aliyuncs.com:
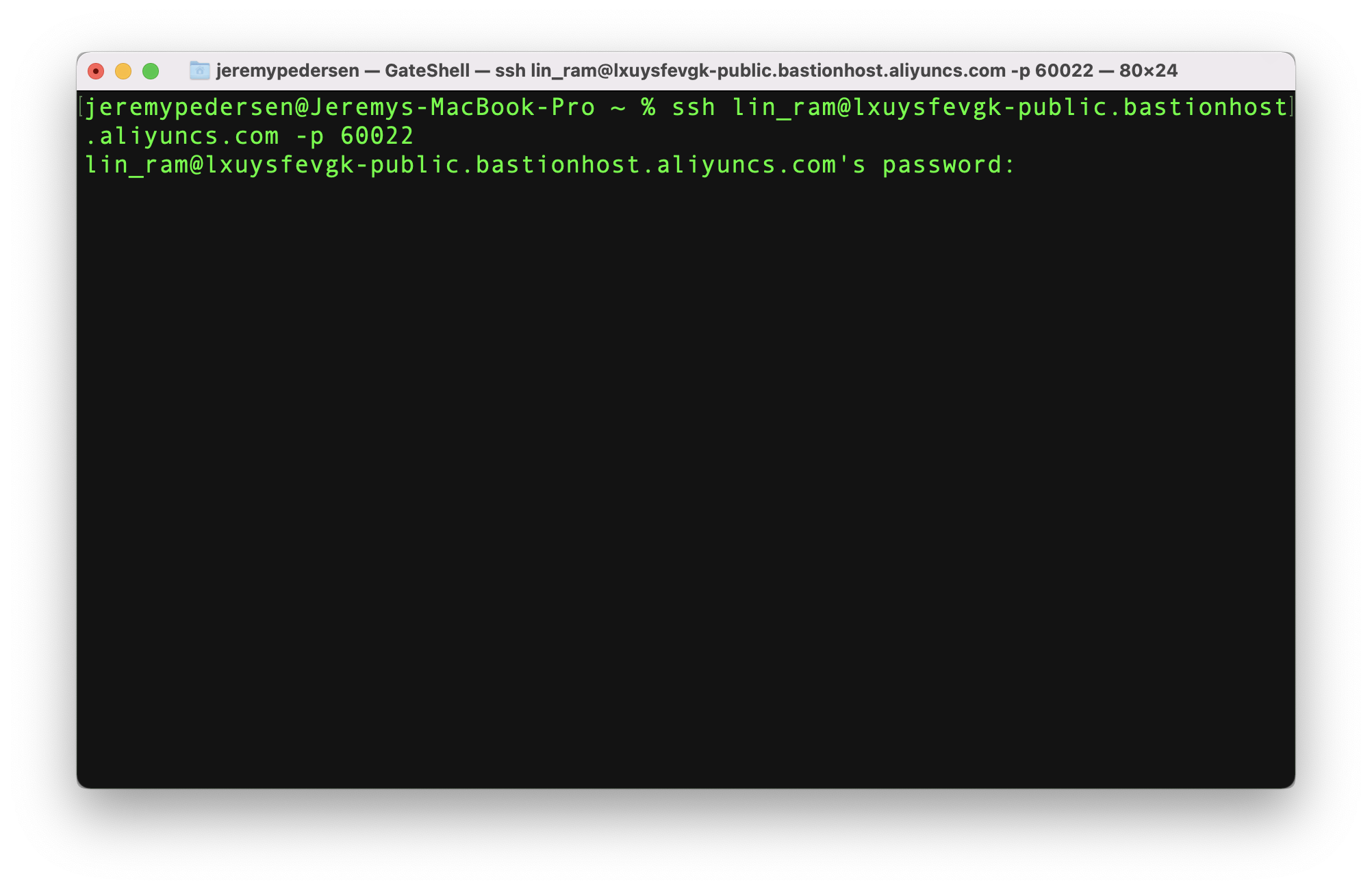
Note that my logon password is my RAM user password. You can enable key-based login or MFA for extra security if needed.
Once logged on, I can see a list of all hosts I have access rights for (in this case, only one):
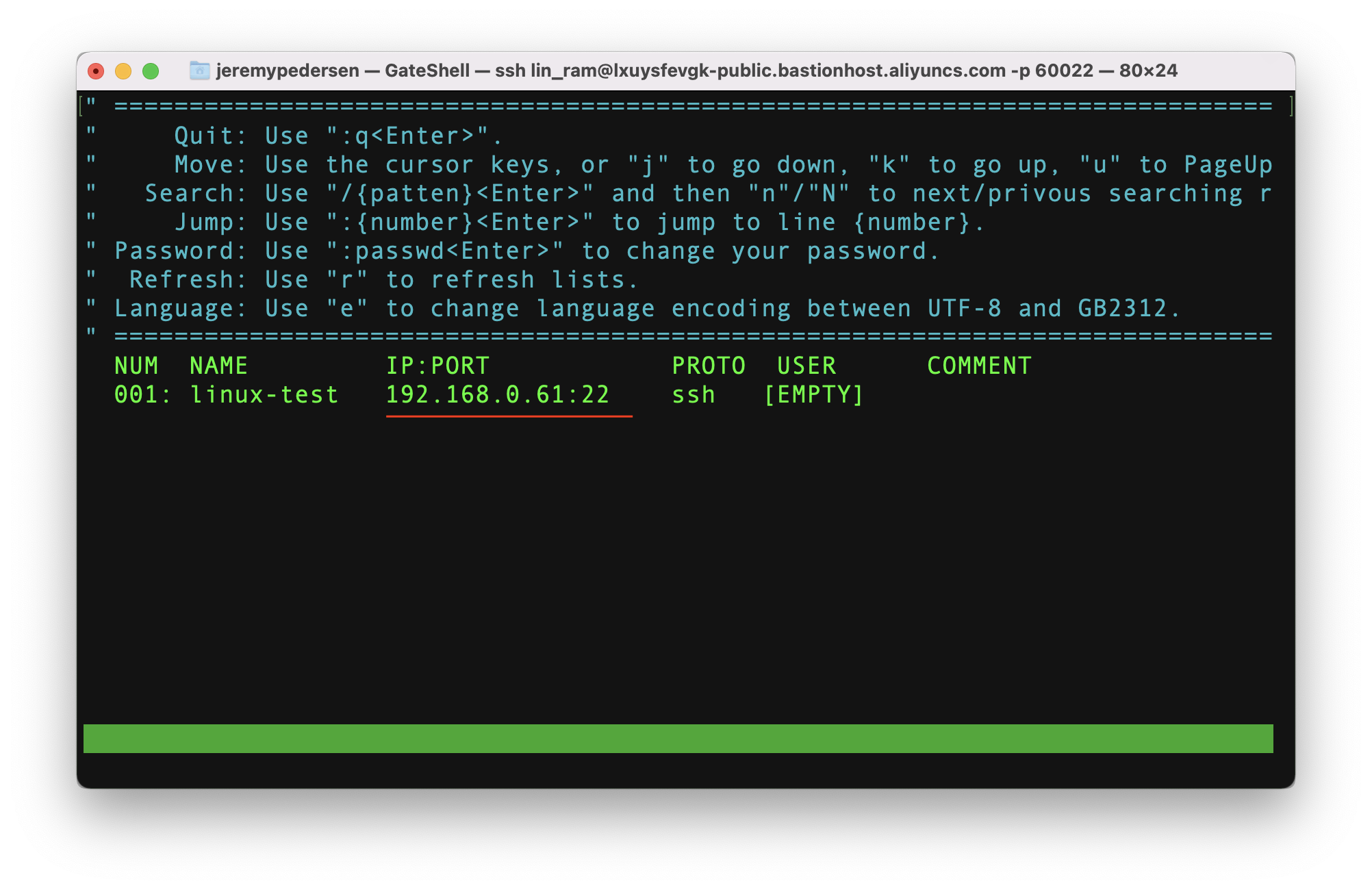
If there were more than one host available, hitting the arrow keys would allow me to move up and down the list. Hitting the enter key while a host is highlighted will initiate a logon, like this:
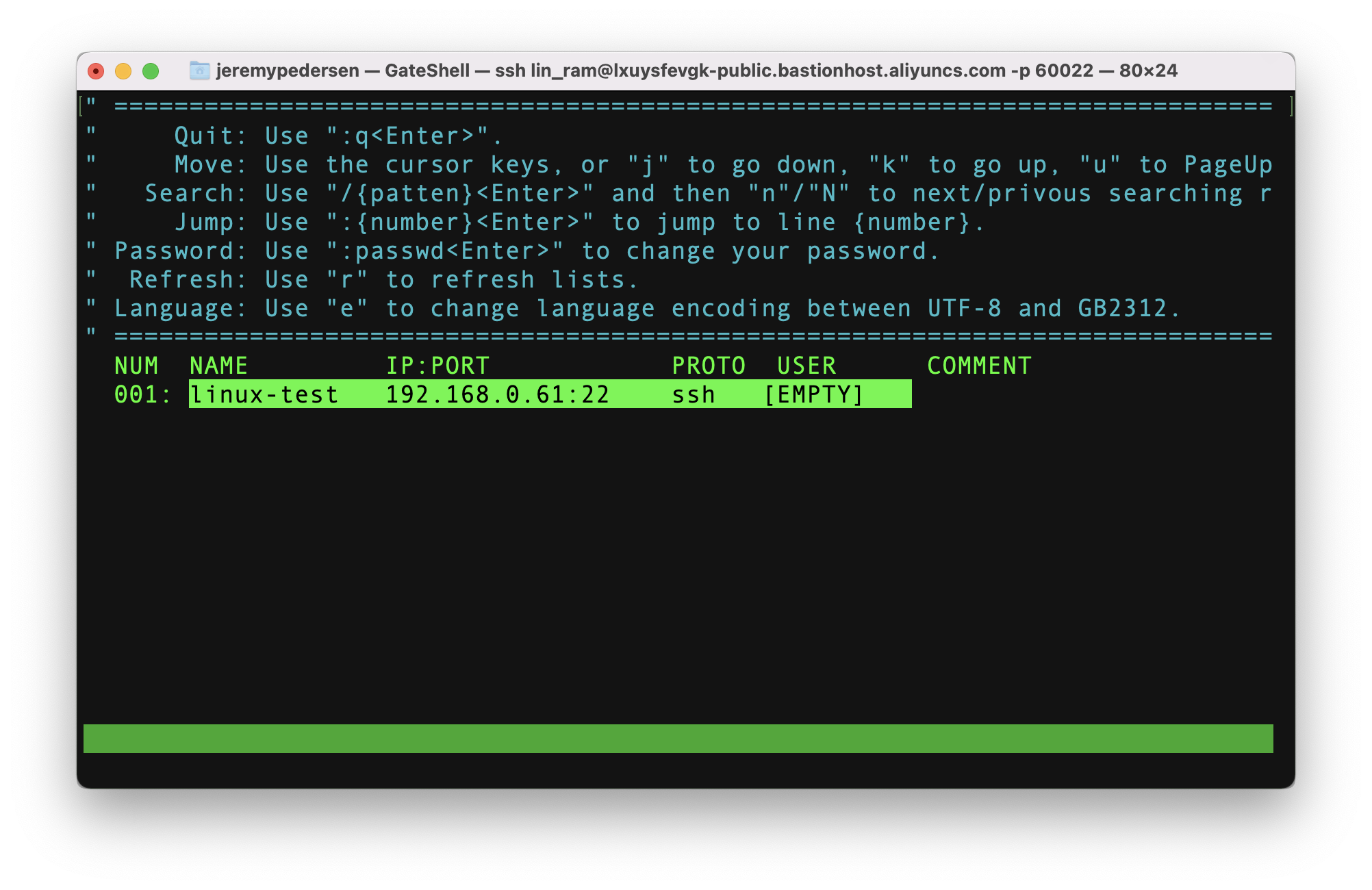
Of course, I then need to specify a valid username and password on the ECS instance itself!
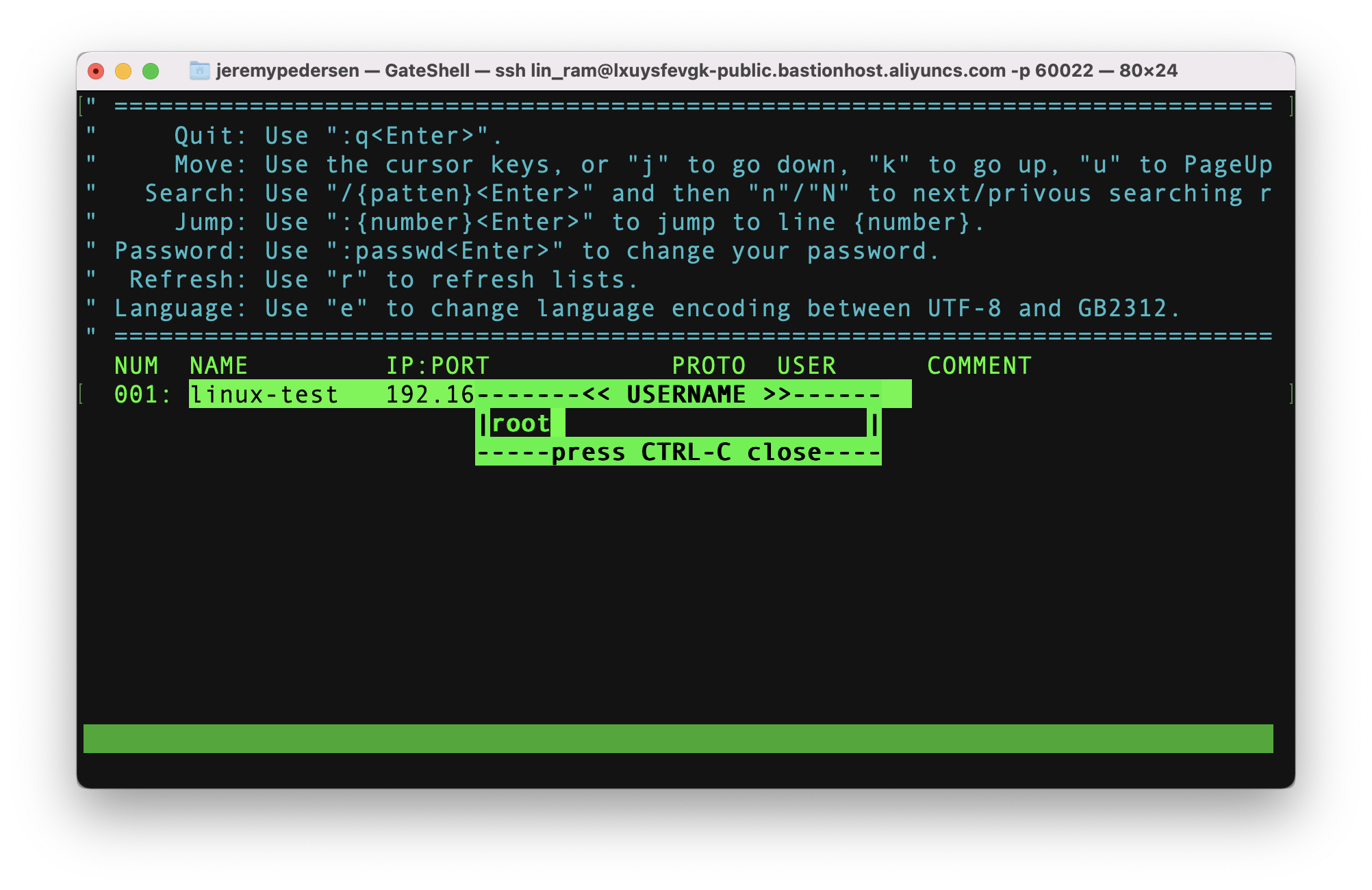
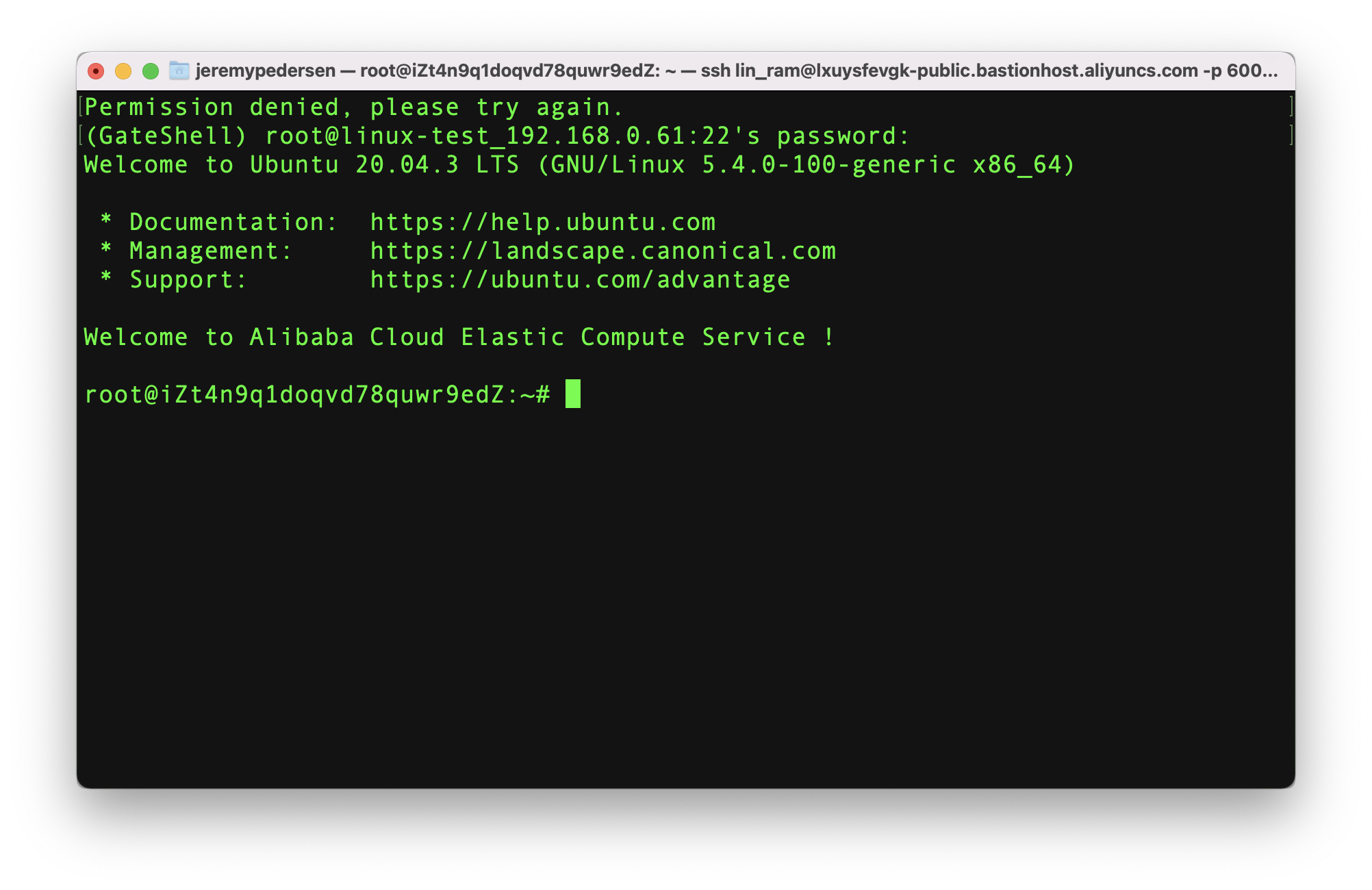
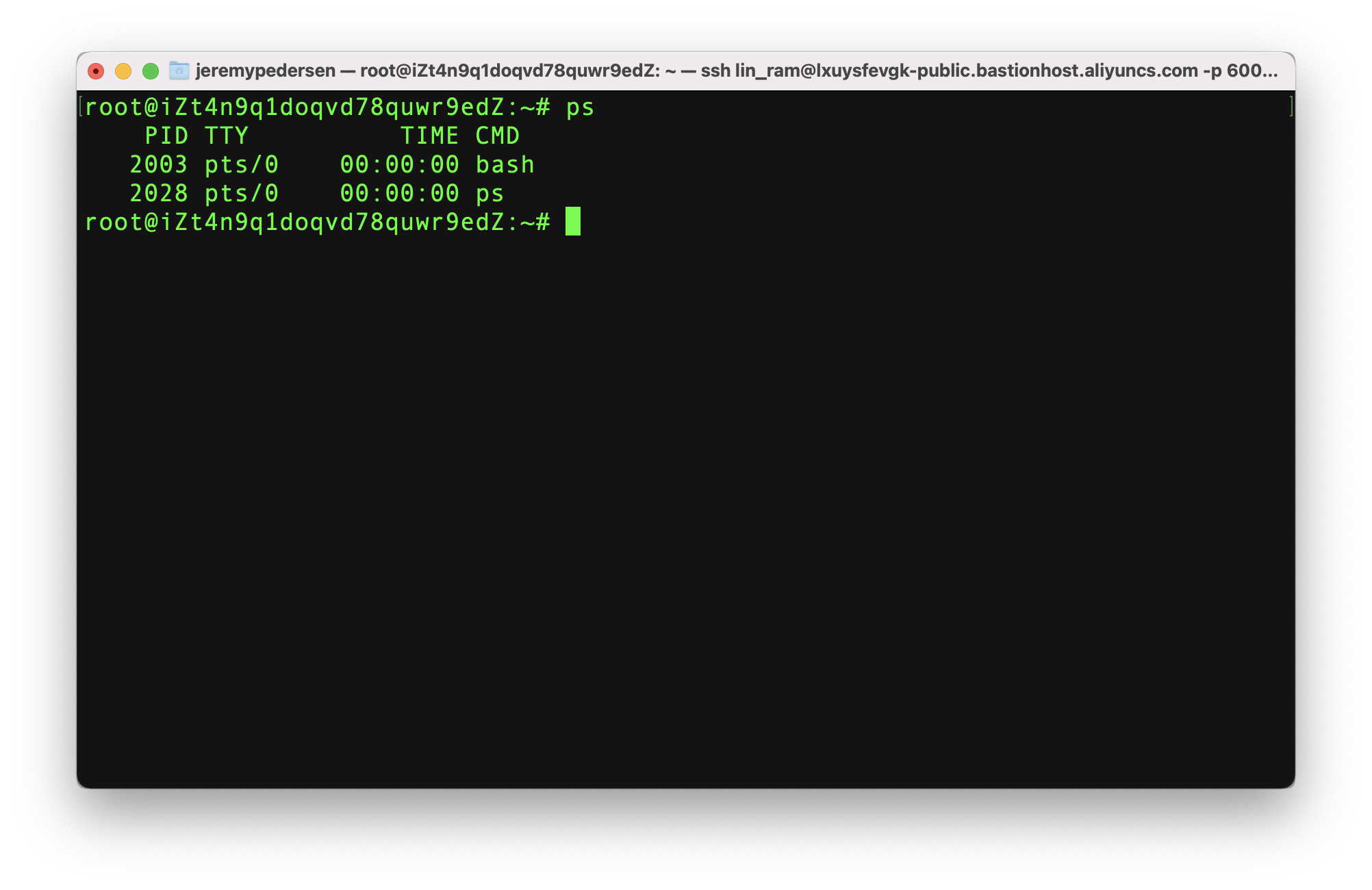
We are now logged in and can execute commands:
We set up a policy for the "lin_ram" user which should block access to commands starting with rm unless they are approved by an admin. Let's try this out!
First, I'll try and remove a text file I have just created:
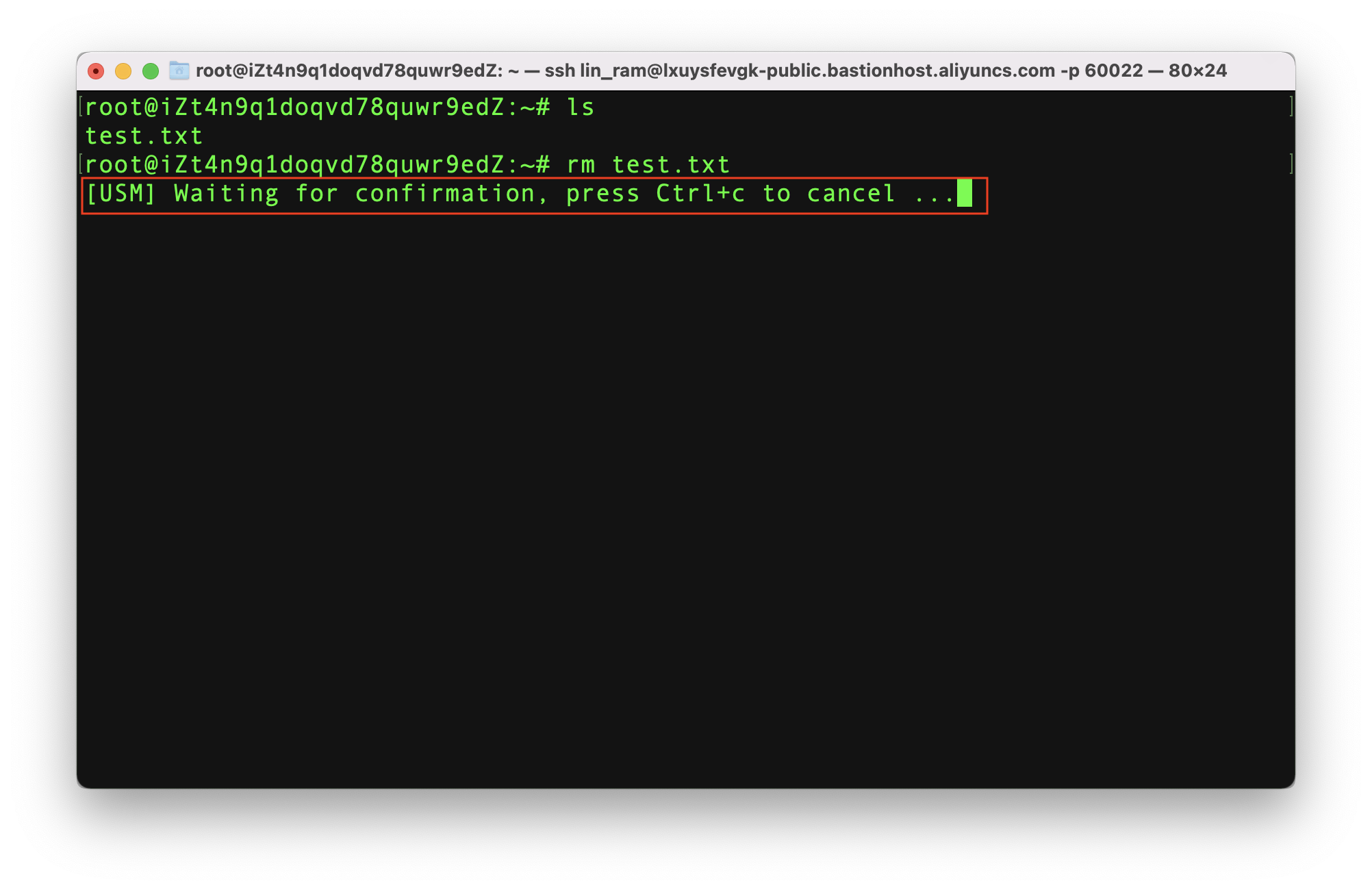
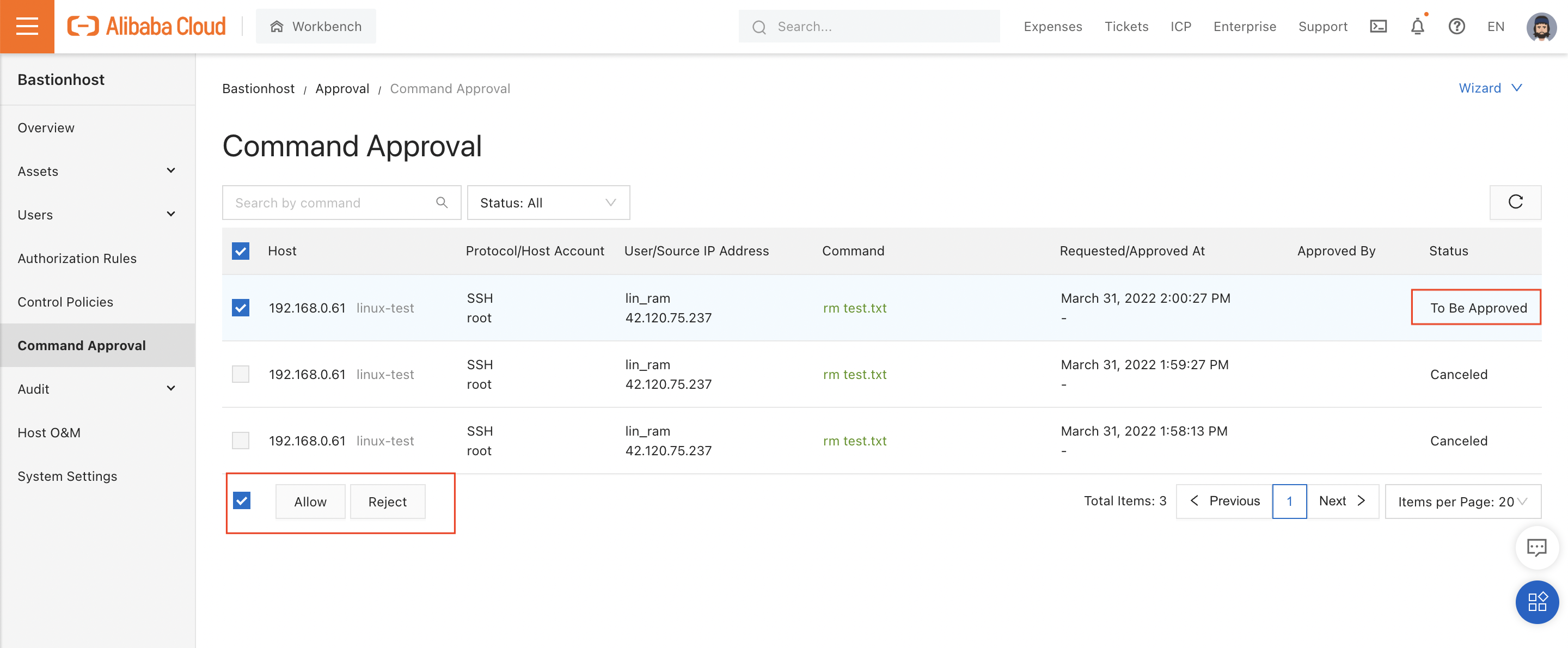
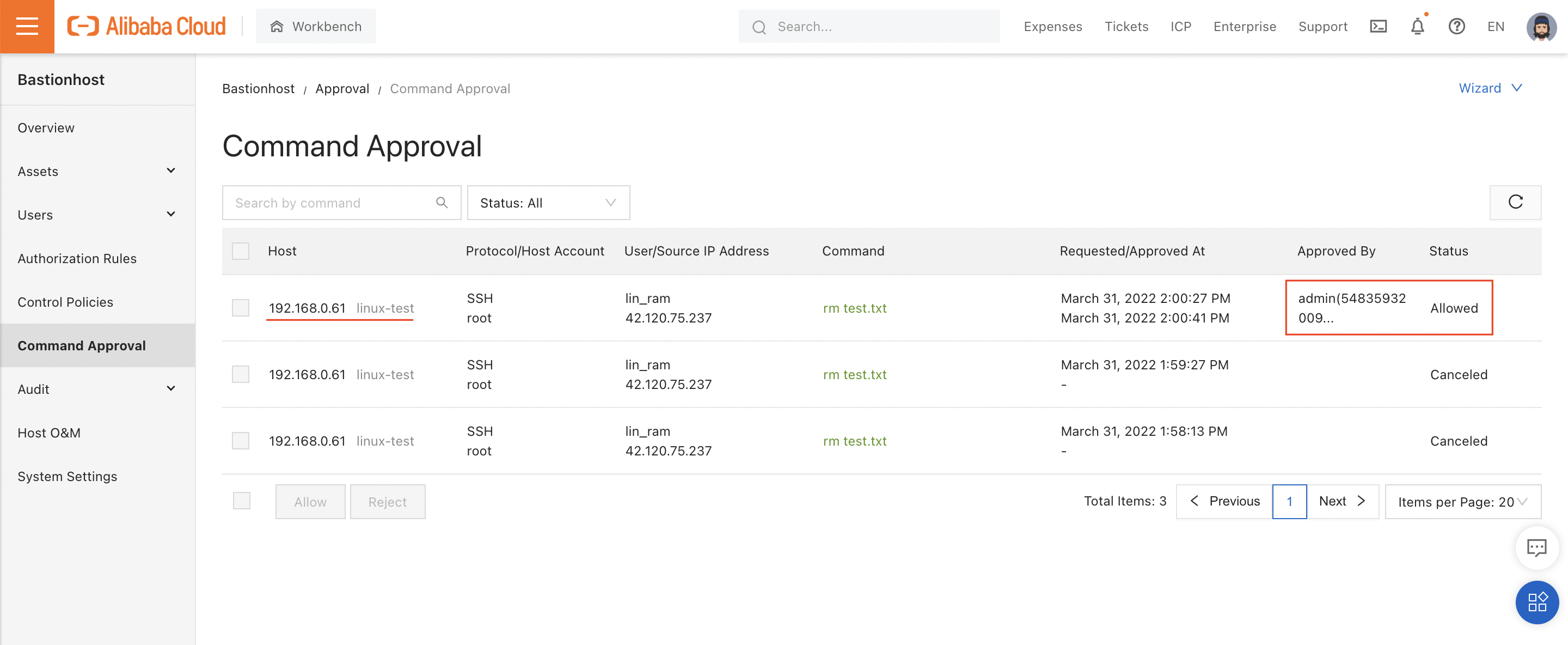
The system tells me that the command is "waiting for confirmation". If I open "Command Approval" in the console, I can see that - as a Bastionhost administrator - I have the ability to accept or reject the command. In this case, I accept:
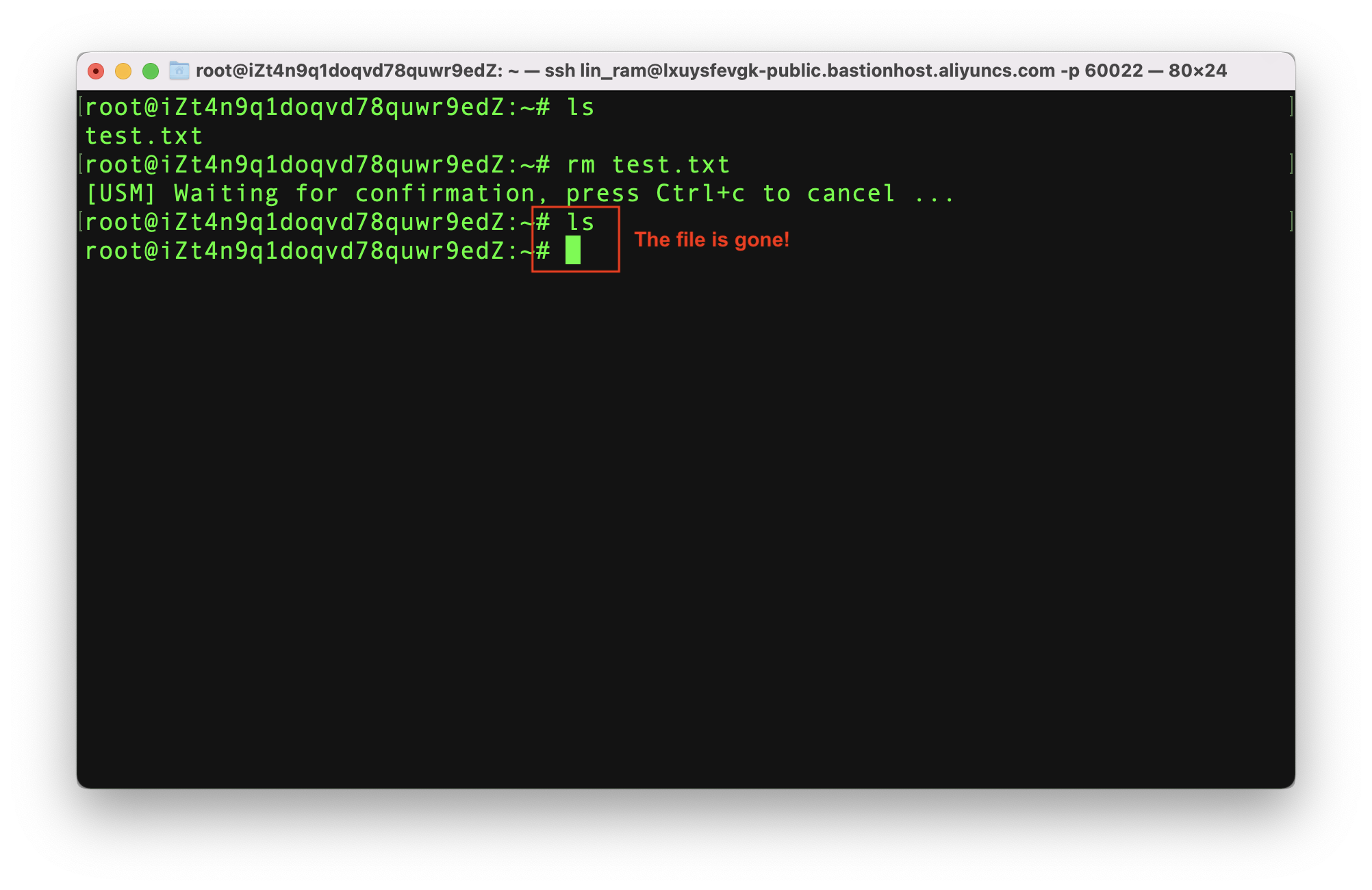
Going back to the terminal, I see the command has been run and my text file is gone!
Bastionhost can only prohibit commands it can recognize, meaning clever users can always find another way. You'll need to use other security best practices like limiting the permissions of your users from Windows or Linux, to achieve a truly secure environment.
Just to demonstrate this, here's one way I could remove that text file without Bastionhost noticing...
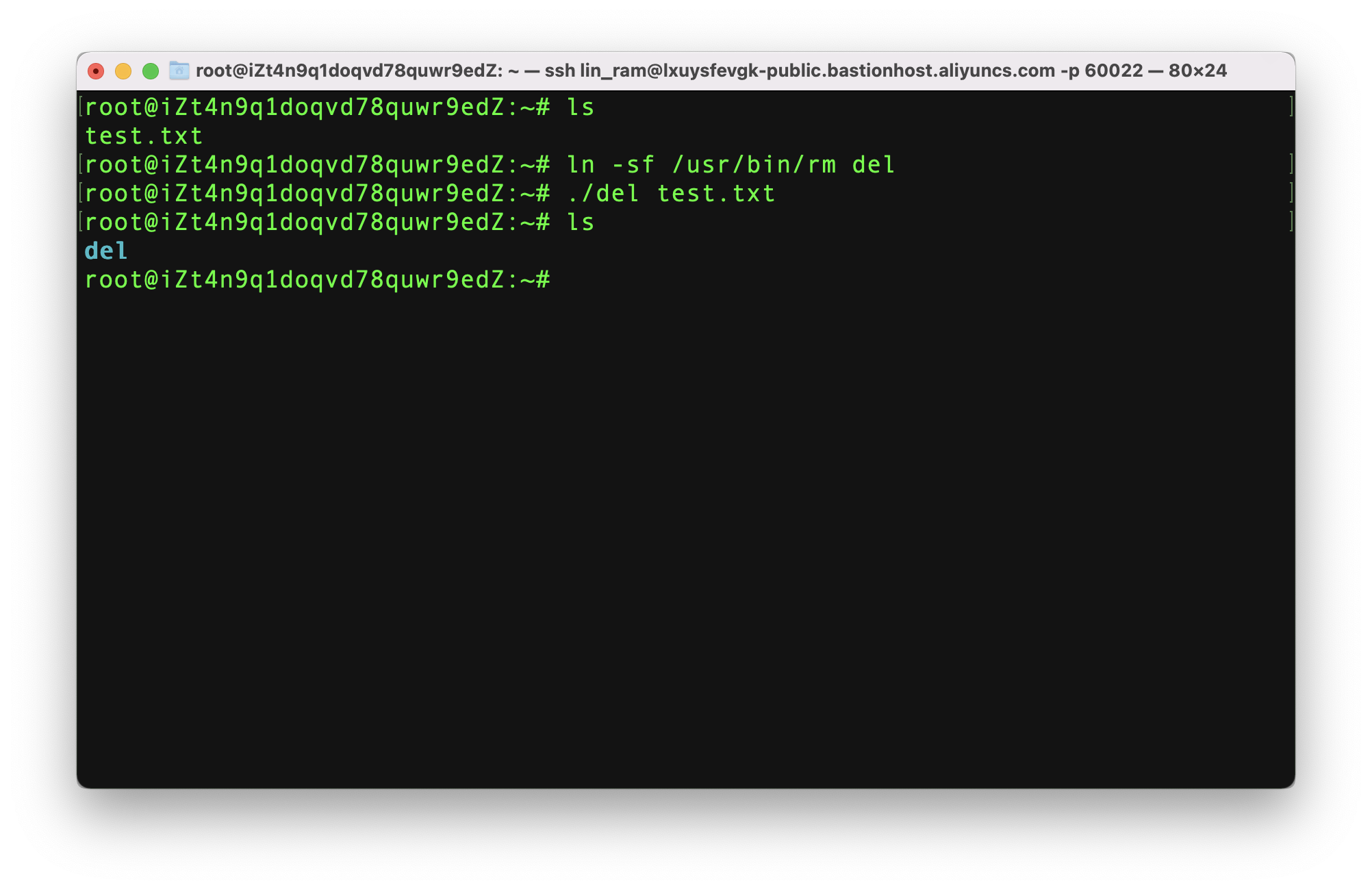
See what I did there?
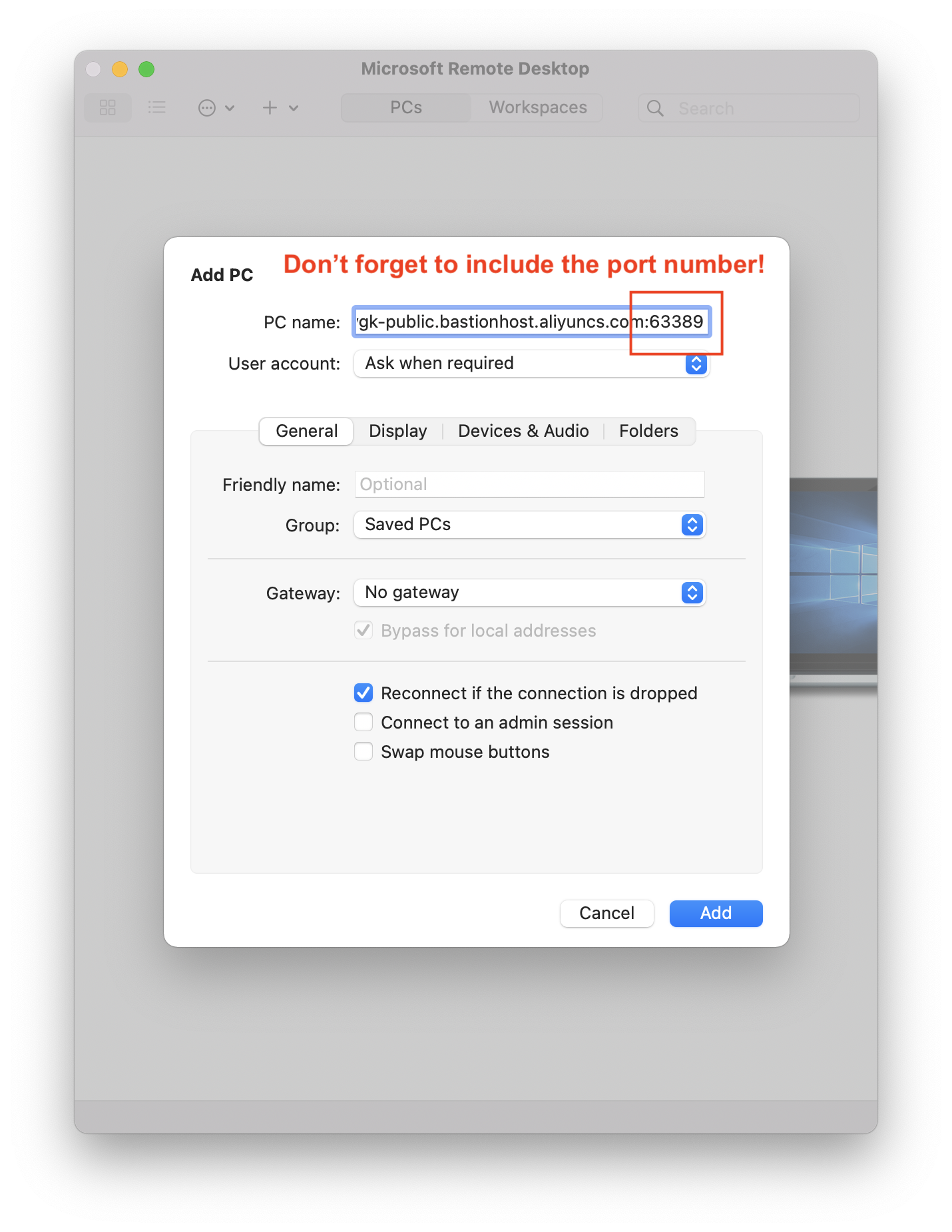
Let's try an RDP logon, from the "all_ram" account, and see what happens. I'll use Microsoft's Remote Desktop tool for macOS:
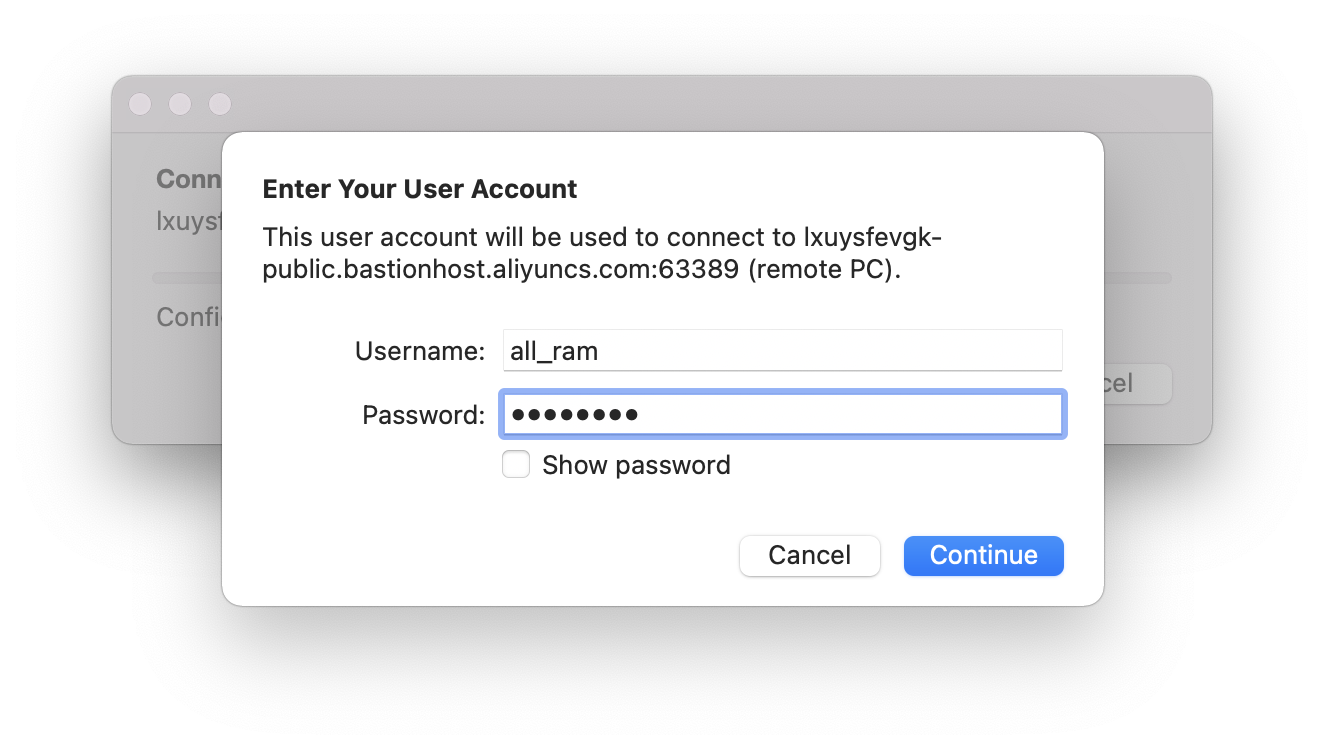
During logon, you'll need to enter your RAM user's username and password:
After logging on, Bastionhost will give you a list of (Windows) hosts you are authorized to log into:
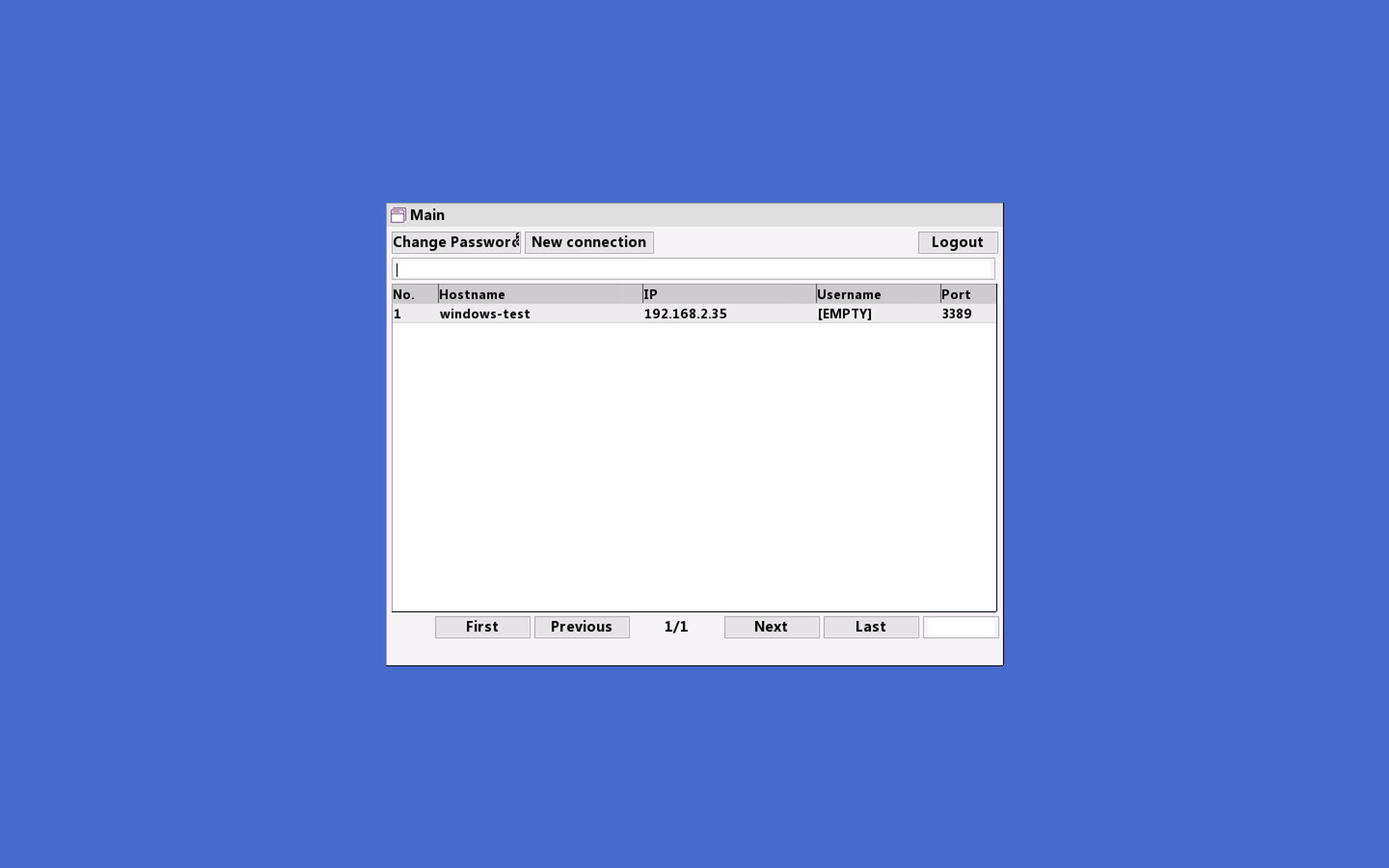
Let's try logging into our Windows ECS instance:
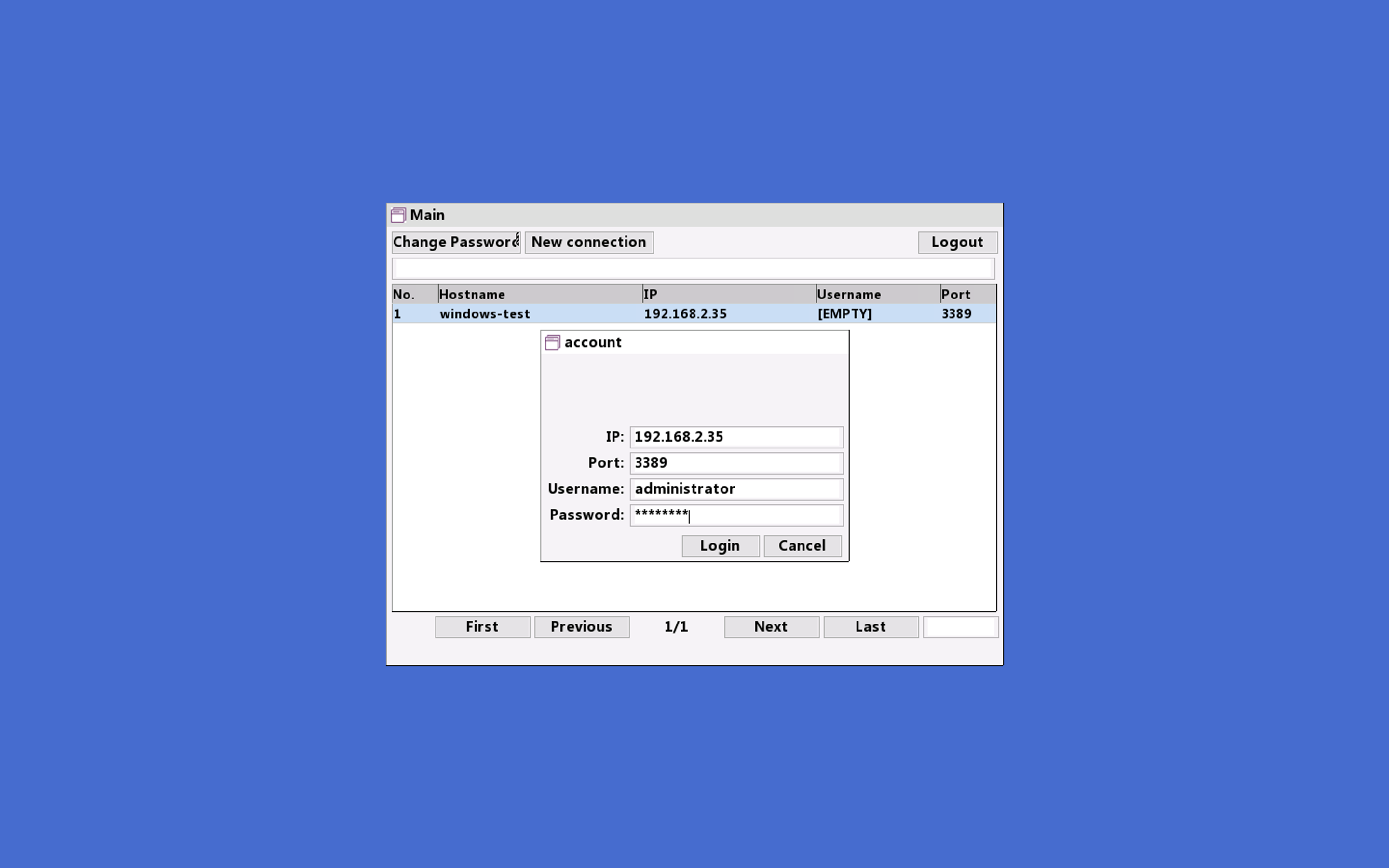
And that's it! We're logged in:
Now we're getting to the cool bit!
From the console, we can see a video replay of every RDP or SSH session, for every user. We can also see - at least for SSH logins - a chronological listing of all commands executed.
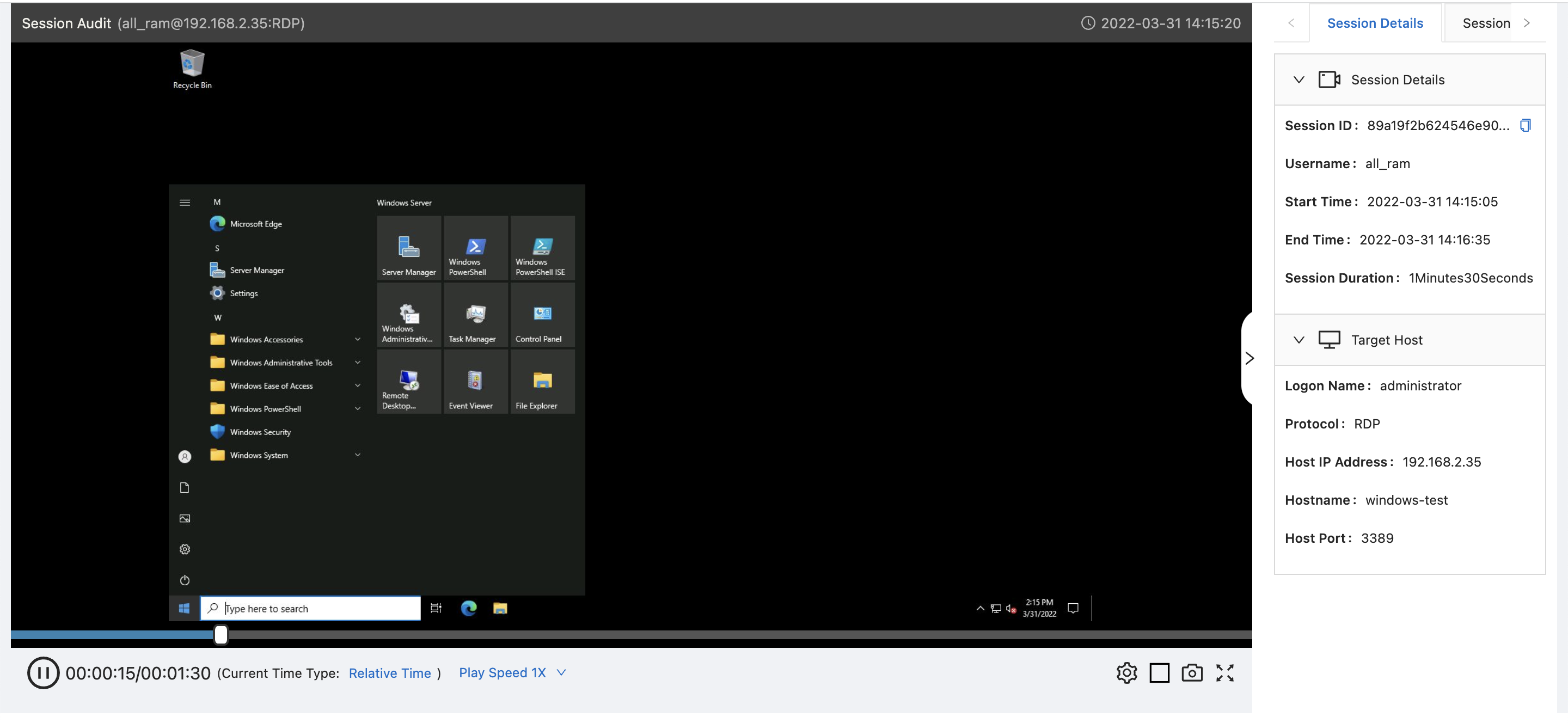
Here are examples of the video replays for Linux and Windows, respectively:
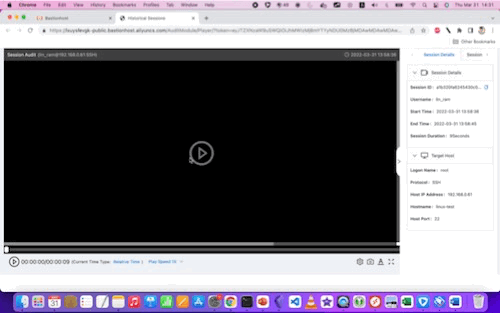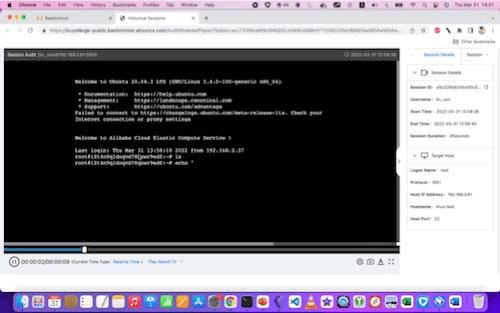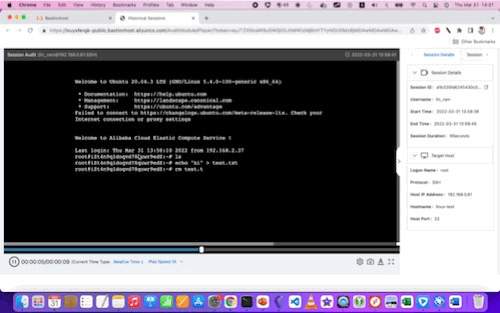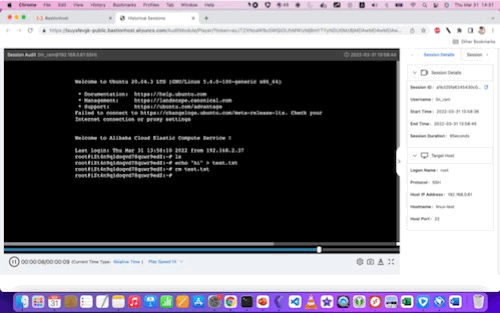
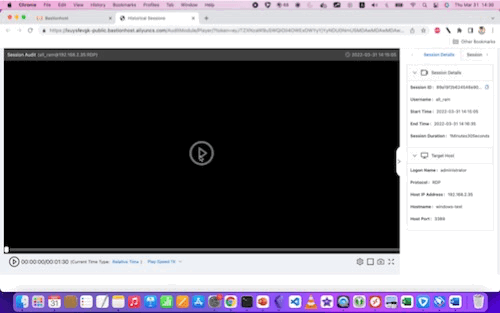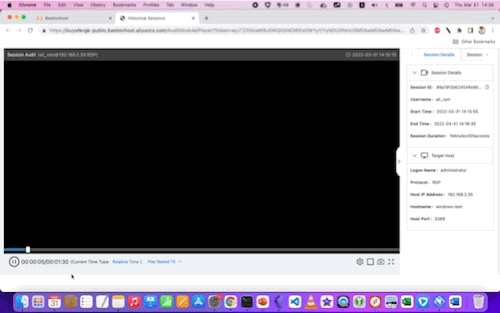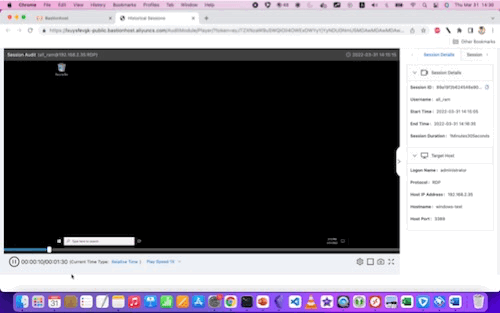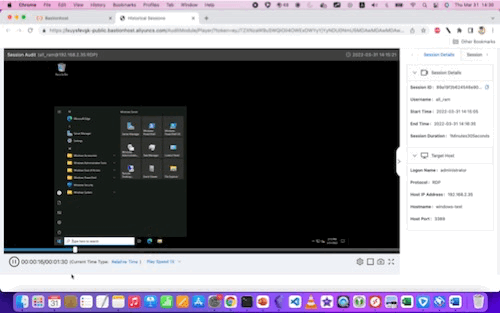
With some larger (still) screenshots for reference:
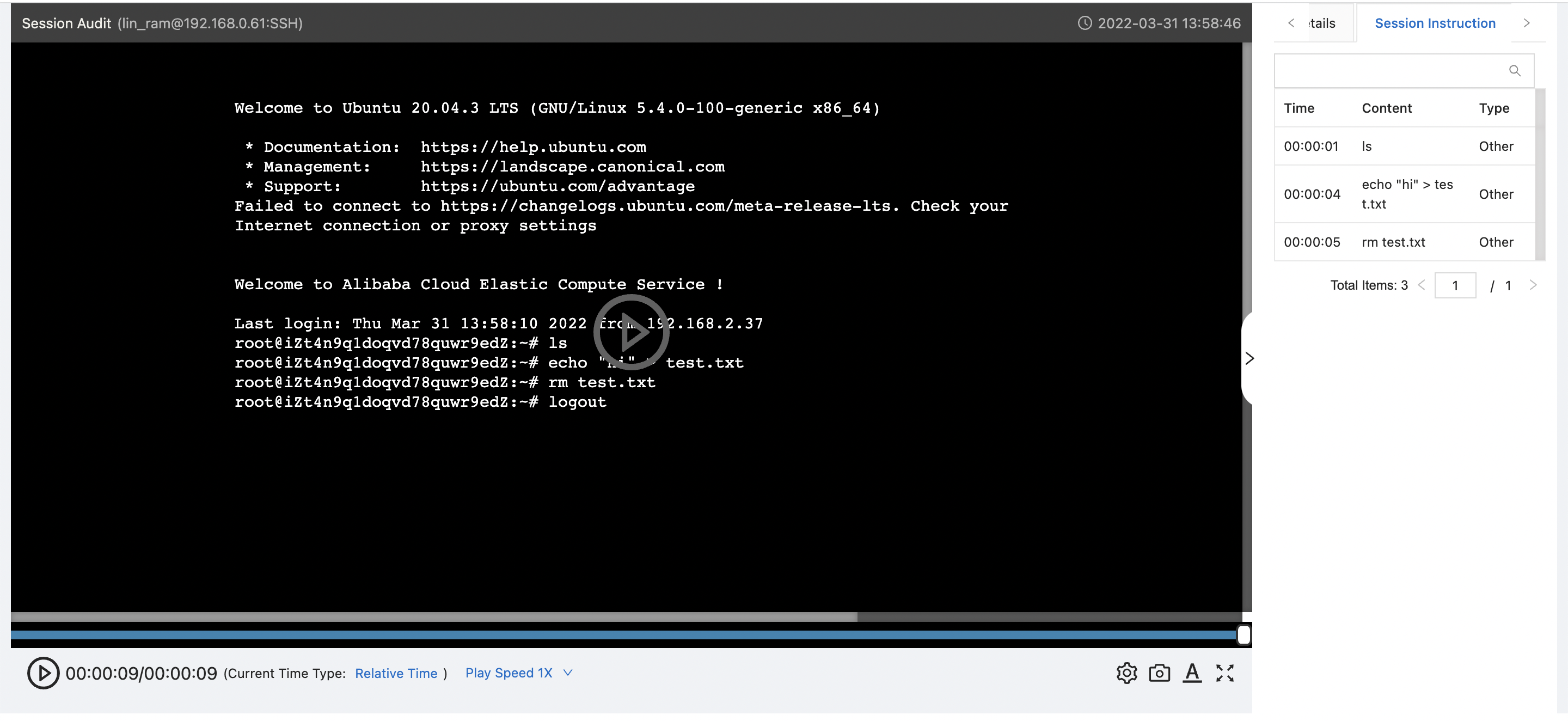
We've just scratched the surface here: Bastionhost can do a lot more, including support federated login via LDAP and other logon services.
If you want to try it out for yourself, take a look at this page, which explains how to apply for a free trial.
That's all for this week: happy administrating!
Great! Reach out to me at jierui.pjr@alibabacloud.com and I'll do my best to answer in a future Friday Q&A blog.
You can also follow the Alibaba Cloud Academy LinkedIn Page. We'll re-post these blogs there each Friday.
What You See Is What You Get: Implementing Image Search - Friday Blog, Week 55
JDP - May 27, 2022
Alibaba Cloud Community - April 8, 2022
JDP - November 5, 2021
JDP - August 5, 2021
JDP - July 30, 2021
JDP - September 15, 2021
 Bastionhost
Bastionhost
A unified, efficient, and secure platform that provides cloud-based O&M, access control, and operation audit.
Learn More Managed Service for Grafana
Managed Service for Grafana
Managed Service for Grafana displays a large amount of data in real time to provide an overview of business and O&M monitoring.
Learn More Dedicated Host
Dedicated Host
A dedicated resource pool that offers flexible and compliant deployment options to grant enterprise users more control over their cloud infrastructure.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by JDP