Target Audience : Retail, e-Commerce, Logistics, Manufacturing
Successful Use Case Sharing
Industry : One of the leading international e-Commerce operation in Southeast Asia
Background Information
Client is one of the largest Southeast Asia e-commerce provider. There are many offices and branches around the globe. Most of the existing connectivity between the branches to the respective Private Cloud (Datacenters) and Public Cloud (Alibaba Cloud) were still going through a very traditional setup with WAN dependencies to the entire network. However, with the growth of users in the branches and data/workloads on Alibaba Cloud, there’s a strict requirement for the network performance to optimize with minimum latency and packet loss.
Customer Challenges
As client is still leveraging on a traditional WAN, MPLS and IP-Sec setup for the branches and offices, there are a lot of concerns due to the network performance as the data transfer can be slow whenever it comes to cross-region connectivity. Any transactions from one to another should be as quick as possible thus even a slight downtime ( few seconds ) can result in business interruption especially when there is an ongoing Live transaction.
Furthermore, as every countries have their own Logistics (Production) and Office (Corporate) which the dependency is relying on a single WAN, it can be risky if WAN goes down or under attack. Client's intention is to segregate both the logistics and office networks and build a robust, secured and reliable network solution to tackle this issue, at the same time providing the end users a good customer experience.
Proposed Solution
New Architecture Design for 2 Branches(Thailand & Vietnam) to Singapore & Indonesia Region’s Hub
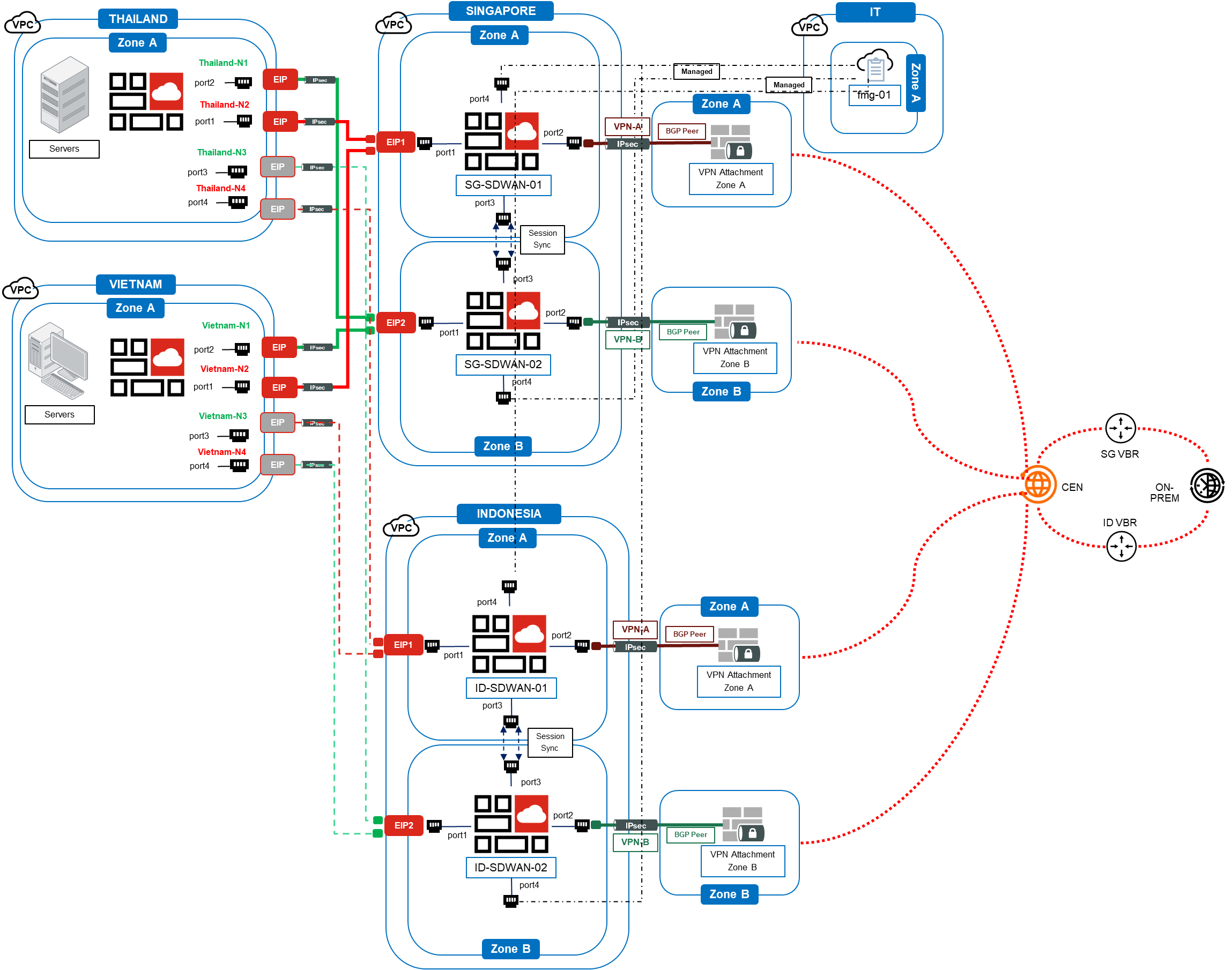
Solution Brief
In consideration of both technical and commercial aspect, the above new solution design has been successfully adopted and proven to be one of the best approach to minimizing any unnecessary downtime during failover and at the same time maximizing the network performance. Singapore Hub will act as the primary while Indonesia Hub will be the Secondary.
Let’s break this into a 5 phases to better understand the solution in details. To comprehend this in a more detail way, let us take Singapore Hub as one of the example as shown below. Indonesia Hub will be exactly the same concept.
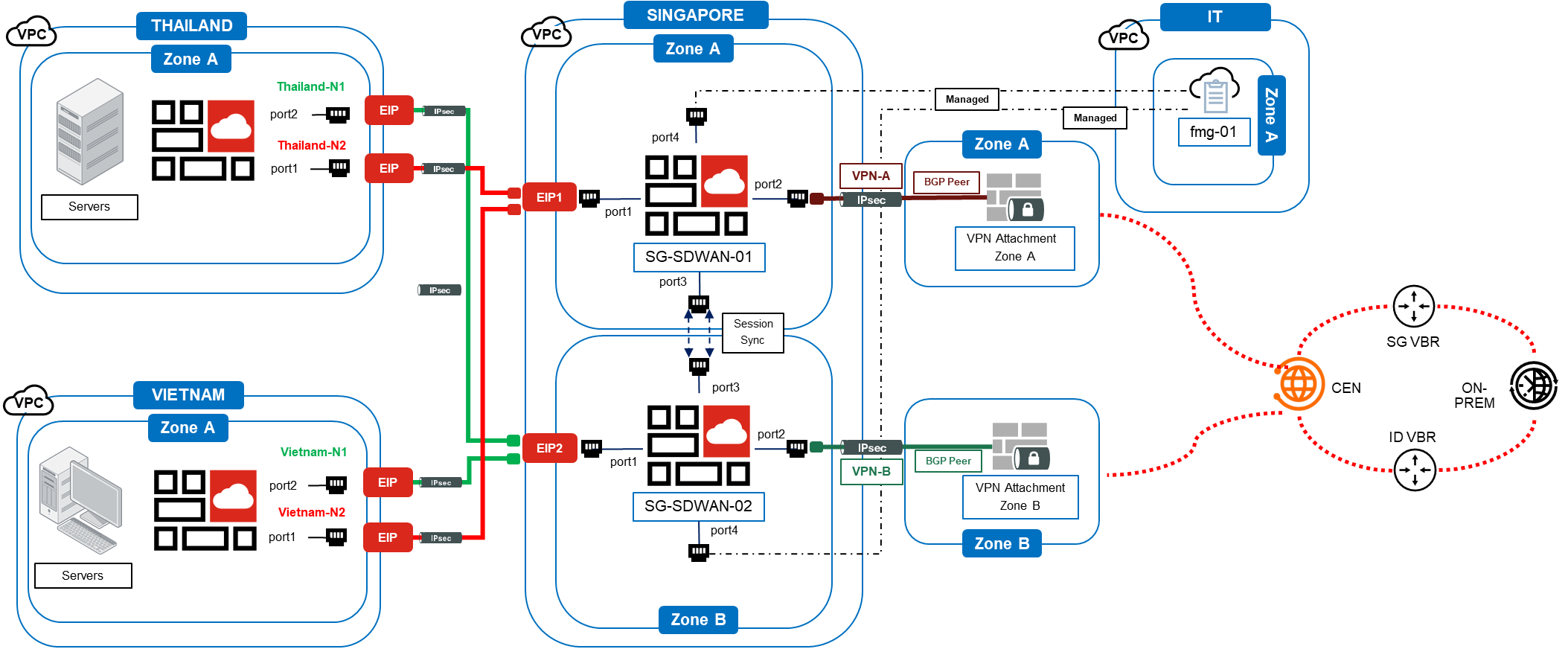
Phase 1
Branch Perspective (VPC - Spoke)
i. Overview
From the left, we can clearly see that there’s a FortiGate Firewall deployed in the Vietnam and Thailand branches with a pair of Internet Service Providers (ISPs) in each branch. Each of these ISPs will establish a connectivity to the Singapore Hub which a pair of FortiGate Firewall is deployed. The connectivity between both sides is configured based on eBGP over IP-Sec connectivity with SDWAN configured based on the jitter characteristics for the best link selection during any failover. In terms of the total number of network interface, there will be 2 Public IP (EIP) that will be assigned for the IP-Sec Tunnel for IP-Sec Tunnel to Hub. More interfaces can be created for other purposes such as FortiGate Internal or Management Ports.
ii. Technical Aspect (Hands-On)
Ref: https://docs.fortinet.com/document/fortigate/6.4.0/administration-guide/453982/branch-configuration
Phase 2
Cloud Perspective (VPC - Hub)
i. Overview
In the middle, we can see that there’s a pair of FortiGate Firewall deployed in the Singapore Hub. These firewalls are configured with Active / Active setup in 2 different zones for high availability. Session Sync (ECMP) is also enabled for both sessions to be synced to avoid any session loss especially for the return traffic. In terms of the number of interfaces, there will be 4 interfaces in total, 2 of which will be bound with respective Public IP (EIP) for IP-Sec Tunnel to Branch.
ii. Technical Aspect (Hands-On)
Ref: https://docs.fortinet.com/document/fortigate/6.2.9/cookbook/543607/datacenter-configuration
Phase 3
Alibaba Cloud VPN Gateway + CEN Perspective
i. Overview
In the middle, we can clearly see that there’s a VPN Gateway in Zone A and Zone B. The objective of this VPN Gateway is to establish to the Singapore Hub’s FortiGate Firewall. Each of these VPN Gateway will be connected to the same Zone’s Firewall as a dedicated tunnel. For e.g. Zone A VPN Gateway will be attached to Zone A SG Hub FGT Firewall via IP-Sec VPN, likewise for Zone B. As the plan is also to allow VPN gateway to automatically learn routes, BGP will be configured on top of the VPN Gateway. After which, because the VPN Gateway is required to communicate to on-premise ( on the right ), it is also mandatory that this VPN gateway will be attached to Alibaba Cloud Cloud Enterprise Network (CEN).
ii. Technical Aspect (Hands-On)
IP-Sec + BGP : https://www.alibabacloud.com/help/en/vpn-gateway/latest/connect-a-data-center-to-a-vpc-and-enable-bgp-dynamic-routing
CEN : https://www.alibabacloud.com/help/en/cloud-enterprise-network/latest/create-an-cloud-enterprise-network-instance
Phase 4
Alibaba Cloud VBR + CEN Perspective
i. Overview
On the right, we can clearly see that the Singapore & Indonesia Virtual Border Router (VBR) are created at it is required to connect to the on-premise Offices. The objective of this VBR is to establish to the Leased Line connectivity from On-premise to the VPCs. However, to achieve that, on-premise office will require a leased line to be connected to the VBR and attach to the Alibaba Cloud CEN. After the VBR is attached to the CEN, the CEN will also be able to communicate to the attached VPN Gateway and subsequently routing the traffic to the respective regions’ VPCs.
ii. Technical Aspect (Hands-On)
Express Connect : https://www.alibabacloud.com/help/en/express-connect/latest/what-is-a-connection-over-an-express-connect-circuit
VBR : https://www.alibabacloud.com/help/en/cloud-enterprise-network/latest/h57c4t
Phase 5
Management Perspective
i. Overview
On the top right, we can clearly see that FortiManager is added into this solution design as it provides centralised policy-based provisioning, device configuration, and update management for FortiGate, FortiWiFi, and FortiMail appliances, FortiClient end-point security agents, as well as end-to-end network monitoring and device control. However, the objective for this FortiManager is to manage all the Branches and Hubs FortiGate devices so as to reduce any management cost, simplify configurations, and automate device provisioning.
ii. Technical Aspect (Hands-On)
Ref : https://docs.fortinet.com/document/fortimanager/6.2.0/cookbook/585894/adding-fort igate-devices-to-fortimanager
Conclusion / Testing
After these 5 steps are completed, we are ready to test the connection. You can create a FTP server in respective branches to test the connection. For e.g. Shutdown either one of the FortiGate Firewall to stimulate the failover test and try to constantly ping from the branches endpoint to the on-premise endpoints which is all the way at the right side of the diagram. The result should be smooth with only very minimal downtime/spike.
Redspan - September 30, 2022
Rupal_Click2Cloud - August 30, 2021
Alibaba Clouder - February 11, 2019
Alibaba Clouder - July 10, 2020
vincentsiu - September 5, 2023
Alibaba Cloud Industry Solutions - January 12, 2022
 Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn More Accelerated Global Networking Solution for Distance Learning
Accelerated Global Networking Solution for Distance Learning
Alibaba Cloud offers an accelerated global networking solution that makes distance learning just the same as in-class teaching.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Architecture and Structure Design
Architecture and Structure Design
Customized infrastructure to ensure high availability, scalability and high-performance
Learn More